The Top 5 Web Security Issues and Solutions
According to Kaspersky’s Security Bulletin 2021, the company blocked 687,861,449 online attacks globally between November 2020 and October 2021. Knowing this, if you conduct any business online, whether you run a website or just do some occasional shopping, you need to know about the top five website security issues.
The security of your website should always be a priority, regardless of the industry or size of your organization. But protecting websites from cybercriminals is easier said than done. The best way to begin to secure your website or application is to understand the issues you’re facing. So, let’s look at the top five web security issues and solutions you should know to help keep your website secure.
5 of the Most Common Web Security Issues and Solutions
The security risks affecting websites are numerous. We’ll study five of the most concerning issues and present some suggested solutions here. The topics we’ll cover in this list aren’t in any particular order, but it’s vital to take each threat seriously and take steps to prevent all of them.
Web Security Issue 1: SQL Injections
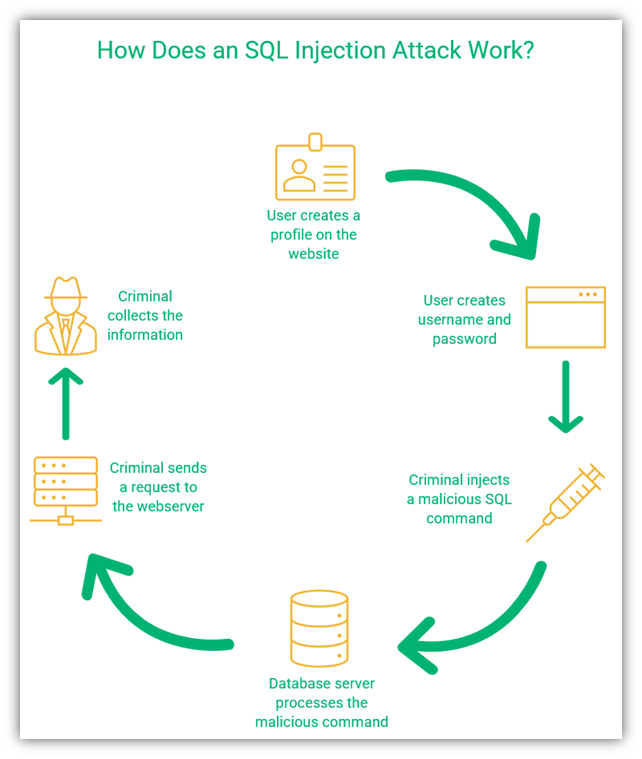
SQL, which stands for “structured query language,” is a standardized language used to speak to databases where you store, retrieve, and use data. This includes everything from customers’ names and email addresses to their usernames and passwords. An SQL injection attack targets an application’s database to exploit any vulnerabilities that allow someone to select, add, or retrieve information from the database (or delete the database altogether).
In an SQL injection attack, a criminal enters code into a site that allows them to gain access to sensitive backend resources of your site. For example, they can enter an SQL query to gain access to users’ passwords; if they do this for an admin account, they get access to the whole database for the website. In addition to access rights, the criminals can also modify and retrieve data from the web servers and do other nasty things for malicious purposes.
Edgescan found that SQL injection was the most critical risk of 2020, occurring in 51.7% of websites tested. With SQL injection, the criminal inserts malicious code into a web app that allows them to access data or execute commands on the victim’s device. These attacks are often carried out by exploiting a server-side vulnerability.
Web Security Solutions for SQL Attacks
We can prevent SQL injection attacks by taking the following measures:
- Restrict searches for users. Avoid allowing blank searches or searches that return too much data. Use date ranges to limit searches and the number of results.
- Don’t allow freeform input by users. For example, disallow numbers or special characters in the name field, make the user select their state and city while entering the address, and only allow a legitimate format for email addresses.
The screenshot below shows an invalid email address and the message in red directing the user to enter a valid one:
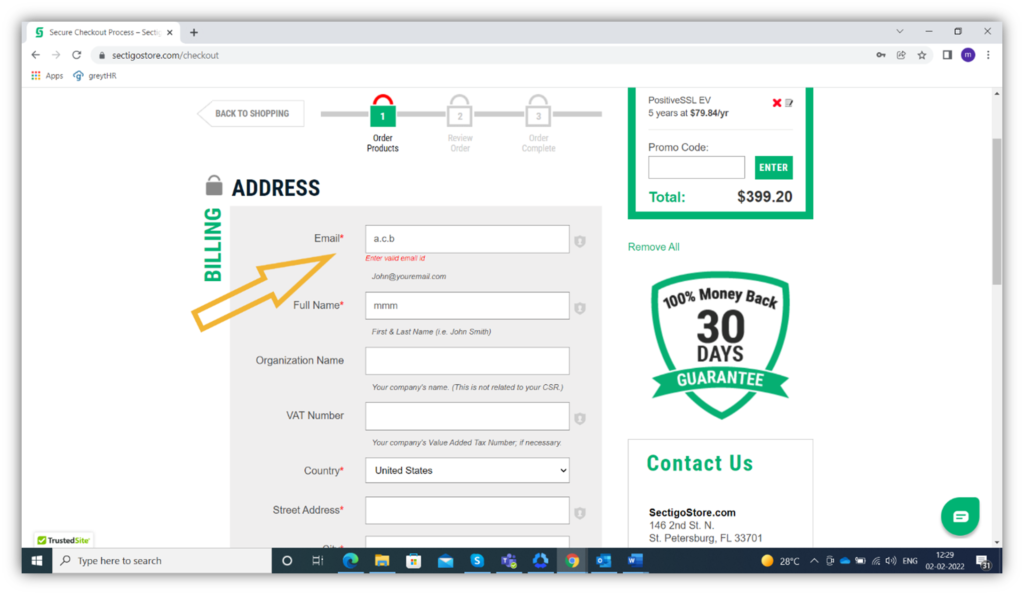
- Validate all data server-side. Before processing any data, validate it to isolate anything that doesn’t belong. This step could protect your website from a hacker who is trying to inject malicious SQL code.
- Clearly define who can and can’t access the data. Assigning clear access permissions for all data helps prevent unauthorized access.
Be sure to check out our other article on 8 tips for how to prevent SQL injection attacks.
Web Security Issue 2: Cross-Site Scripting (XSS) Attacks
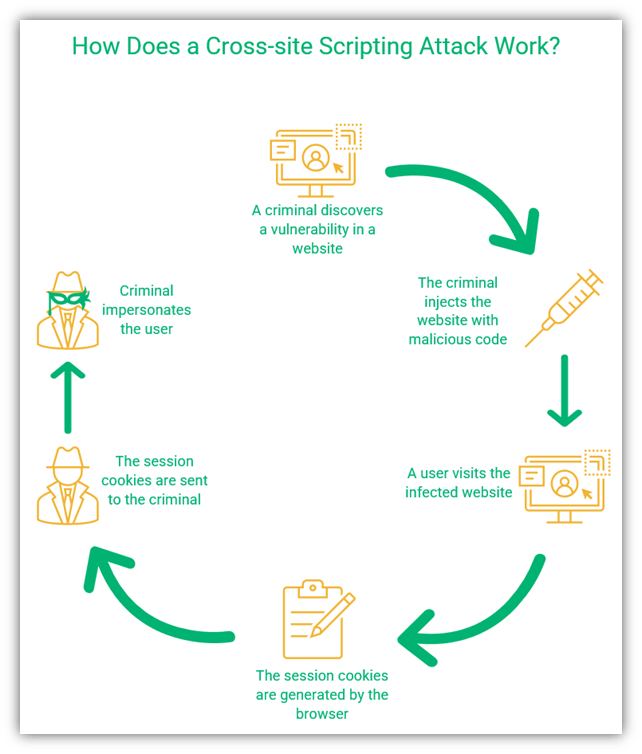
Cross-site scripting (XSS) is an injection attack that exploits a client-side vulnerability in a website or web app. The goal is to use legitimate websites or web applications to spread malicious code to other users.
Unlike an SQL injection, the goal of many XSS attacks is often to target other web users by using legitimate or trusted websites as proxies. A cross-site scripting attack allows the criminal to impersonate the user they have victimized and carry out all the actions that the user can do. When a user visits a legitimate but compromised web page, the malicious code executes in their browser. The bad guy then gets access to the victim’s web session.
A session begins when a user logs in to their account on a website; it ends when the user logs out or is inactive for a certain amount of time. Each session generates session cookies (i.e., temporary data) to make the execution faster. Once the session ends, the cookies are deleted automatically.
In this type of attack, bad guys inject code that’s designed to steal users’ session cookies. These cookies contain sensitive information about the user and allow the bad guys to log in as the user on that website or web app. Here’s a quick overview of how this works:
Web Security Solutions for XSS Attacks
Since an XSS attack is another form of injection, there’s some overlap in terms of the solutions you can use to prevent XSS and SQL injection attacks. Let’s look at some quick examples:
- Validate all client-side inputs. One of the most important steps you can take to prevent an injection attack is to check and recheck everything that goes on your servers. As criminals tend to inject the malicious code from outside, you’ll reduce their chances of success by validating all user inputs.
- Use properly configured firewalls. Firewalls help to protect your network and devices from malicious code executions. If the firewall detects any suspicious activity, it will filter out the content.
- Update your software and anti-malware. If you use top-notch software and anti-malware but don’t keep them updated, they can do more harm than good. Developers release patches when they discover vulnerabilities in their software. Updating the software will ensure that all the known vulnerabilities are patched.
- Use a strong content security policy. A content security policy (CSP) specifies the commands a website is allowed to perform. Stringent CSPs limit what external resources websites load, thereby helping to prevent malicious executions (which help prevent XSS attacks).
Check out our other article on cross site scripting attacks to learn more about what they are and how to prevent them.
Web Security Issue 3: Secure Authentication Issues
To understand broken or insecure authentication in web security, we must first understand authentication. In the context of web security, authentication means verifying a user’s identity before allowing them access to sensitive information on your server. You want to verify someone is who they claim to be before you let them walk in your home’s front door, right? The same concept applies here.
Broken authentication typically is the result of one of two things:
- A breach in your site’s authentication methods
- Poor session management
Bad guys use phishing techniques or bots to extract passwords or one-time passwords (OTPs) from unsuspecting victims. Although platforms regularly warn users not to share their passwords and OTPs, phishing can be so convincing that many people fall for it.
Poor session management can also lead to broken authentication. Using predictable session IDs or session IDs that don’t expire after a certain period of inactivity leads to broken authentication. Sharing session IDs, passwords, or OTPs over an insecure network can also result in a security breach.
So, how does broken authentication pose a threat? Broken authentication issues can lead to cyberattacks such as:
- Session hijacking — where the criminal takes over a legitimate user’s session so the attacker can do everything the valid user can do during a session.
- Session fixation — where a criminal sends a phishing email containing a malicious link that allows them to hijack the user’s session before the user is logged in using the user’s authentic session ID.
- Credential stuffing or brute force — where the criminal runs a script that either repeatedly tries known username/password combinations or tries their hand at guessing them.
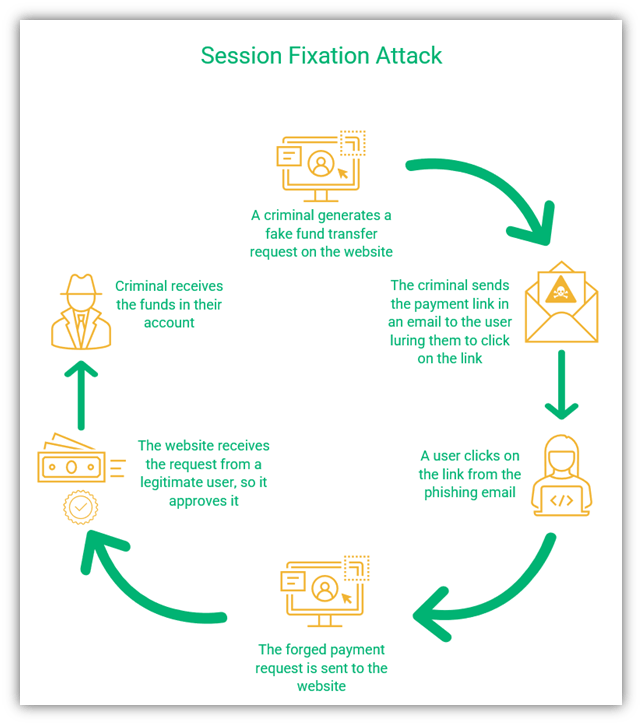
A figure showing the steps in session fixation attack
Web Security Solutions for Authentication Issues
As broken authentication is typically a result of poor password or session management practices, it can often be prevented by fortifying accounts. You should take the following steps to prevent these authentication-related issues from occurring as a user or an admin:
- Require use of strong passwords (which should never be shared). It is very easy to guess your password if you use predictable words and numbers (e.g., your name and birth date). Use longer, stronger passwords to prevent the bad guys from accessing your accounts. Also, never, ever share your password, period. Make this requirement part of your organization’s password policy.
- Use passwordless authentication. For resources you want only select users to access, do away with passwords altogether and implement certificate-based authentication instead. This method requires the users to have authentication certificates installed on their devices that authenticate them without typing in tricky passwords.
- Don’t open links from unknown sources. If you want to visit a site, go through your browser. Don’t click on links sent to you via email or messages. Although it seems easier to click rather than type the address in your browser, it is much riskier.
- Implement stringent session management. Always log out of your session once your work on a particular website or device is over. Implement automatic logouts for other users as well after set periods of inactivity.
- Set unique session keys. Don’t use predictable session keys for your website.
- Don’t use session IDs in URLs. Some websites include session keys in URLs. This is an open invitation to criminals to hack the session. Don’t do this.
- Limit login attempts. This is a good general practice as it helps to prevent bot-based automated attacks such as credential stuffing and brute force attacks. If a user tries to log in too many times in a period, set it to lock the account for a specific amount of time automatically.
Web Security Issue 4: Sensitive Data Exposure
Sensitive data exposure is one of the most important web security issues and solutions topics we can address. Why? Because data security is everything. The sensitive data you need to protect includes but is not limited to:
- Personally identifiable information (PII) of employees, customers, and partners
- Financial information of the organization or customers
- Trade secrets, intellectual property, and other sensitive company documents
- Customer and supplier lists
Sensitive data exposure can happen for many reasons, including human error, technical glitches, or criminal activity. But if sensitive data falls into the wrong hands, it can cause significant damage to the organization.
Data exposure has serious consequences, from loss of reputation to hefty fines. IBM Security reported that the global average cost for an organization suffering a data breach was $4.24 million in 2021. Sensitive data exposure can result in the following situations:
- Sensitive data is published on the web. Criminals might publish the PII or other sensitive data online for others to view and use, often in other cyberattacks.
- Sensitive data is used for ransom. Criminals might threaten to make the sensitive information public via publication or encrypt the data to restrict access if the victim doesn’t pay a ransom.
- Sensitive data is used by competitors. Trade secrets or product information can be used by competitors for their own benefit causing losses to the organization.
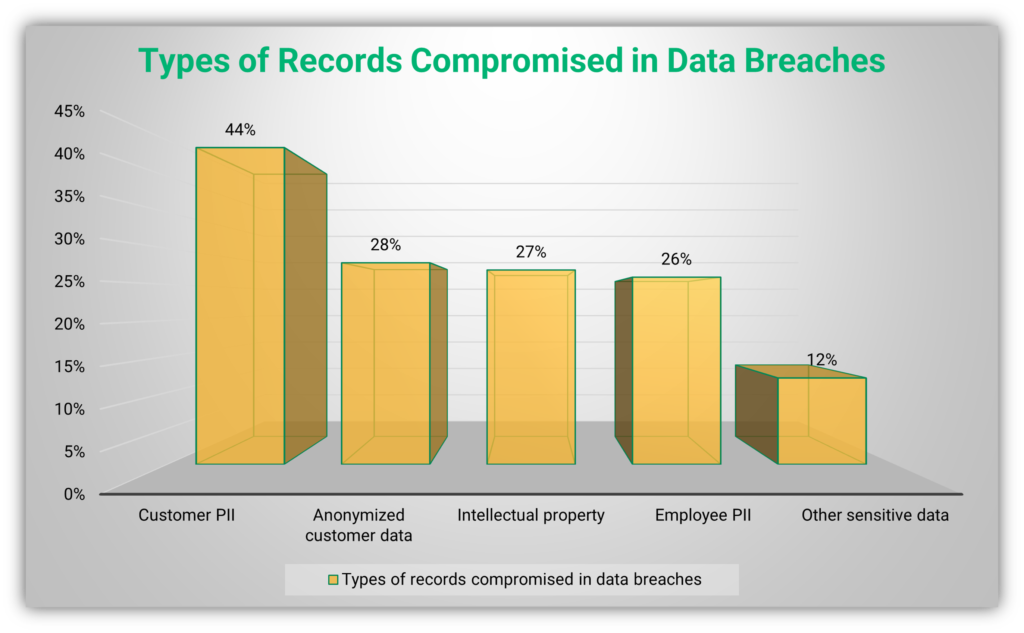
Moreover, governments also regulate the privacy of their residents with regulations such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA). A data breach can lead to violations of these regulations, resulting in fines and penalties for the organization involved. The following figure shows the types of records compromised in data breaches according to the IBM Security report:
Web Security Solutions That Help Protect Sensitive Data
Protecting sensitive data is crucial because of data breaches’ high financial costs and legal repercussions. So, let’s look at some of the ways you can secure your organization’s sensitive data:
- Use strong TLS certificates for data in motion. When you transfer data from one place to another, criminals can use man-in-the-middle attacks to gain access to it. TLS certificates ensure the integrity and security of the data as it travels.
- Protect data at rest. Use strong database passwords, multi-factor (or passwordless) authentication methods, and hardware security tools to protect data at rest.
- Secure your network. Firewalls and anti-malware secure the network from unwanted visitors, reducing the chances of a data breach.
- Implement a zero-trust model for information sharing. Limiting the amount of data shared can work wonders for the security of the organization’s network. Share data with employees, contractors, and other stakeholders only when necessary.
- Use security automation. In the report we mentioned earlier, IBM observed that when organizations use full AI and automation for security, the average cost of a data breach falls from $6.71 million to $2.90 million ($3.85 for partially deployed security AI and automation). The company’s researchers also noted that it takes less time to detect and contain breaches when these security automation tools and processes are fully deployed — just 247 days (compared to the 324 days when no automation was used).
Web Security Issue 5: Security Misconfiguration
Last but certainly not least on our list of web security issues and solutions is security misconfigurations. If you have a security misconfiguration come to light, it’s often the result of poorly defined and implemented security procedures and settings. These vulnerabilities arise when a developer or administrator makes mistakes when configuring an application, network, or server.
Verizon research found that misconfiguration issues were involved in more than 50% of data breaches that fall in their ‘Miscellaneous Errors’ category. Criminals can exploit misconfiguration vulnerabilities with all kinds of attacks, including everything from brute force attacks to buffer overflows.
Principle Reasons for Security Misconfiguration
Some of the major reasons for misconfiguration include:
- Mistakes by developers and administrators. Sometimes developers or admins make changes to security procedures or software for testing purposes but forget to revert the changes when they’re finished.
- Not updating software and anti-malware. Running outdated software gives criminals free rein. Additionally, if upgrades are not installed and configured properly, the system could still be vulnerable.
- Using default usernames and passwords. Whether you are the administrator or a user, changing the default settings and passwords is crucial. An administrator using “admin” as their username is asking for trouble.
- Unresolved problems in the cloud. IBM Security reported that cloud misconfiguration was an initial vector in 15% of data breaches. With an increasing number of people shifting to cloud storage, the importance of cloud security should not be taken lightly.
- Not carrying out regular audits. Sometimes even when everything is configured properly, vulnerabilities appear due to additional devices, changes in system, and software updates. Regular audits help mitigate this threat.
- Not having properly documented procedures. Having documented procedures and processes is critical to the security of all businesses because these documents help your IT admin or team ensure that all T’s are crossed and I’s are dotted.
Web Security Solutions That Help to Prevent Misconfiguration-Related Issues
Okay, now that we know some of the biggest website security issues regarding configuration problems, what are some solutions? To avoid issues associated with misconfiguration:
- Check security procedures before execution. Developers should meticulously check all code before it goes live.
- Keep software and hardware up to date. Known vulnerabilities should be patched by installing updates as soon as they become available.
- Change login information from defaults. Users should change usernames and passwords as soon as they get access to their accounts and change them regularly.
- Use stringent cloud management policies. Cloud storage should be managed by following well-designed policies. Unnecessary information should be deleted from the cloud as soon as possible.
- Audit and update security regularly. Regular audits can reveal gaping security holes. Any unknown devices, outdated software, or unwarranted user access can cause a breach, so audits should always be conducted regularly to help you keep an eye on things.
- Maintain current procedural documents and enforce their usage. Creating these valuable resources won’t do you any good if the people who need them don’t use them. Regularly review and update those documents when applicable to ensure they remain current and useful.
Final Thoughts on the Top Five Web Security Issues and Their Solutions
As you can see from this list of web security issues and solutions, security is not a one-time job. This article has explored the five big issues that commonly lead to cyberattacks and some of the solutions to prevent them from affecting your organization. A cyber security breach can result in devastating damage to your organization, and it’s far better to invest in robust security measures than to fall prey to cybercriminals and have to deal with the consequences.
You need to continuously assess the threat landscape and make alterations to your security program to keep your network and web apps safe. Although there is no sure-fire way to completely secure your networks from cyber threats, understanding the issues will help you stay as secure as possible. The Center for Internet Security (CIS) issues benchmarks for different software vendors and product families that you can use to help secure your systems.







![The TLS Handshake Explained [A Layman’s Guide]](https://sectigostore.com/blog/wp-content/uploads/2023/01/tls-handshake-feature-150x150.jpg)










2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security