What Is a Certificate Authority? Certification Authorities Explained
Certificate Authority – Regardless of whether you them certification authorities, certificate authorities, or CAs, we’re here to answer your top questions about these third-party entities and how they work
What is a certificate authority? Well, before I can answer that, let’s back up a second and let me ask you something. Would you hand over your banking information, banking information, or social security number to a stranger on the street? Probably not. But people do the digital equivalent of this all the time through their favorite websites. They enter their personal details on ecommerce, banking, and credit bureau websites without knowing whether they’re secure, safe, or trustworthy. Moreover, they do this without having any real understanding of what makes them secure, safe, or trustworthy.
But how do you know whether a website is any of these things? For example, how do you know whether you’re shopping on a legitimate ecommerce website or banking on the legitimate banking website? And how do you know that your info is transmitting securely? This is where something known as a certificate authority comes into play.
We’ve put together a list of the top questions people ask about certification authorities to help you better understand their role in internet security. You can either choose to read through all of the content or you can simply pick and choose which questions you want answers to from the table of contents below.
Don't make the same mistakes
Yahoo, Equifax, Home Depot,
LinkedIn, and Ericsson did!
Get our free 15-point checklist and
avoid the same costly pitfalls.
Contact details collected on InfoSec Insights may be used to send you requested information, blog update notices, and for marketing purposes. Learn more...
Table of contents
- Certificate Authority – Regardless of whether you them certification authorities, certificate authorities, or CAs, we’re here to answer your top questions about these third-party entities and how they work
- What Is a Certification Authority (Certificate Authority)?
- What Does a Certificate Authority Do?
- A Real-World Example of How a Public CA Works
- Certificate Authority Validation Levels
- Why Do We Need Certification Authorities?
- What Is an Example of a Certification Authority?
- What Is the Role of a Certificate Authority in Public Key Infrastructure?
- What Is a Digital Certificate and What Does It Do?
- How Certificate Authorities Issue Digital Certificates for Websites
- TLDR; A Quick Overview of Certification Authorities
What Is a Certification Authority (Certificate Authority)?
A certificate authority is a third-party entity that’s trusted by web browsers and operating systems to create and issue digital certificates. But their job is to do this for organizations and websites that they vet, which makes CAs integral to digital security (and internet security) as we know it.
A “certification authority” is the original term for what we now commonly refer to as a certificate authority or a CA. So, you’ll sometimes see them referred to by these different names.
What Does a Certificate Authority Do?
Basically, a public certificate authority is a publicly trusted entity that issues digital certificates to individuals, businesses, and other organizations. These certificates are basically small data files that contain vetted identifying information about the organization. So, CAs are a way to prove yourself to people who don’t know you (or your organization) personally by having a reputable third party vouch for you.
But what does all of this mean when it comes to website security?
Before issuing a certificate, the certification authority checks out the requesting organization. They look at documents and records from official sources to make sure that the company is legitimate. After that, the CA issues a digital certificate that the organization can use to secure their websites, software, and email communications using encryption and digital signatures.
So, if you’re someone who requests a certificate for your organization, here’s what a certification authority helps you to achieve:
- Prove your organizational identity. You can run around screaming “I’m me!” all you want — but this is a way for you to prove your identity to the rest of the world.
- Validate that your organization is legit (and that your site isn’t operated by hackers). Hackers are crafty individuals who are always looking for ways to trick users into providing their personal information and clicking on malicious links. What better way to do that than by pretending to be you by creating a fake website that resembles your real one?
In a roundabout way, CAs also help you to create secure, encrypted connections between your web servers and your users’ browsers. By issuing an SSL/TLS certificate for your website, for example, you can then use a secure transport layer security (TLS) protocol to send and receive encrypted data. As a site owner, this helps you to protect the information that travels to and from your servers. This prevents eavesdropping and man-in-the-middle (MitM) attacks that can result in stolen data.
Certificate authorities are also frequently responsible for maintaining certificate revocation lists (CRLs) that tell the world when certificates are invalidated prior to their assigned expiration dates.
Public CAs Are the Identification Card Issuers of the Internet
To put it another way, certificate authorities are the identity verification authorities of the internet. They’re kind of like the identity card issuers for your state or country of residence.
In the United States, each state has its own equivalent of a Department of Motor Vehicles (DMV), which is responsible for issuing driver’s licenses. These licenses are government-issued cards that you can use to prove your identity to drive, buy alcohol, get a job, and perform other business and tasks.
When you apply for your driver’s license, in addition to having to pass a driver’s test, you’re also required to provide different types of official documents that prove your identity. This includes everything from social security cards and birth certificates to green cards and various proofs of residence.
Once you verify your information with a third party (in this case, the DMV), the DMV worker then takes your picture, which displays on the card along with your official signature. They then print the card with holographic markings that indicate your card is real and isn’t a realistic forgery (think of this like a digital signature). You can then use this documentation to prove your identity.
A Real-World Example of How a Public CA Works
Of course, the best way to understand what a certification authority is, is to consider a real-world example of what they do in terms of website security.
Let’s say you’re someone who dabbles in investing and you use vanguard.com for your transactions. How do you know that you’re on the official website for The Vanguard Group, Inc.? After all, the site appears to be legitimate and uses logos and branding that are consistent with the company. But it could be a really well-designed phishing website… this is why it’s important to know what to look for.
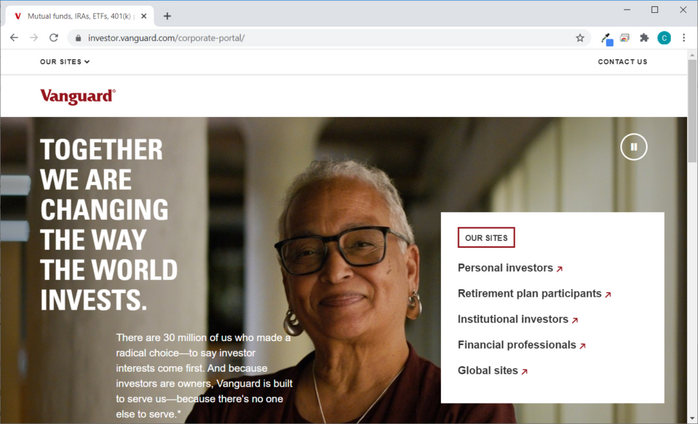
See the padlock symbol in the address bar? That means that your browser is connected to the site’s server using a secure, encrypted connection. Okay, cool. So now you know your info is transmitting via a secure, encrypted channel — but that still doesn’t mean your info is safe. That’s because even phishing websites can get domain validated (DV) SSL/TLS certificates from less-than-stringent CAs. The Anti-Phishing Working Group’s (APWG) Phishing Activity Trends Report for Q1 2020 shows that as of the end of Q1 2020, nearly 75% of phishing websites used SSL/TLS certificates!
This is why it’s crucial that you know whether you’re connecting to a real web server and not a hacker’s imposter website. After all, a cybercriminal can get a free DV certificate and slap it on their website to make the secure padlock icon appear. But this is why it’s important to know the difference between a secure site and a safe site. I say that because you can have a secure site — meaning that it’s communicating using an encrypted communication channel — that isn’t safe because you don’t know who you’re connecting to on the other end of that encrypted connection.
You can verify the site’s legitimate by checking the site’s SSL/TLS certificate organizational information (see the screenshot below):
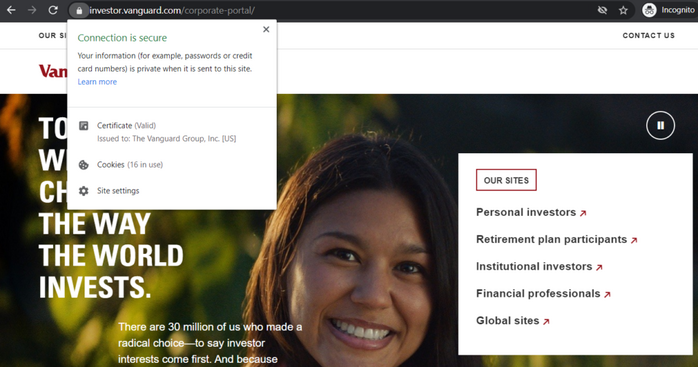
So long as a website is using a website that validates organizational identity (more on that shortly) as a minimum, you can tell that a site is real.
To view more in-depth information, click on the certificate information and open the Details tab. Here, you can select the Subject field to read the organization’s verified information.
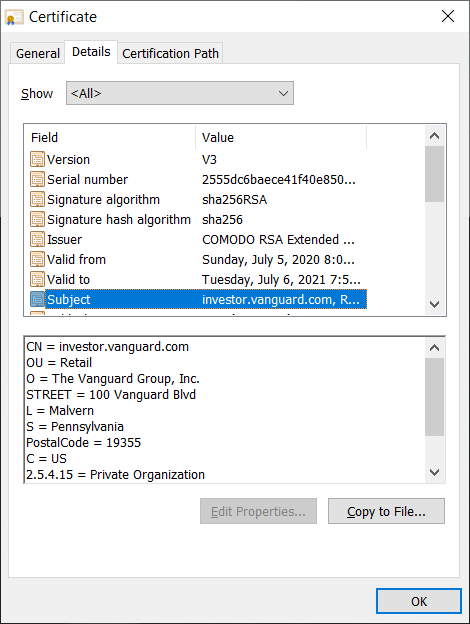
All of this is made possible through public key infrastructure, or what’s known as PKI. (We’ll speak more about PKI shortly.)
Certificate Authority Validation Levels
Certificate authorities are capable of validating organizations and individuals to make sure they’re real and aren’t posers. There are three levels of validation that they use:
Domain Validation
This is the most basic form of validation. It only requires the CA to ensure that the person or organization requesting the certificate has control of the domain or website. This can be done either by them sending a validation link to your registered email address or by sending one or more files that you’d need to upload to specific folders of your domain.
Because this process is so basic, it’s typically completed automatically and results in certificate issuance within minutes. So if you’re looking for more in-depth verification, you’ll want to use the next type of validation as a minimum.
Organization Validation
This is sometimes referred to as a basic business validation certificate and it’s the next step up from domain validation. The reason why is because it offers greater vetting of an organization than a DV certificate does, yet it’s not as extensive as the next type of certificate we’ll cover.
The American Cancer Society’s website is an example of a site that uses an OV certificate.
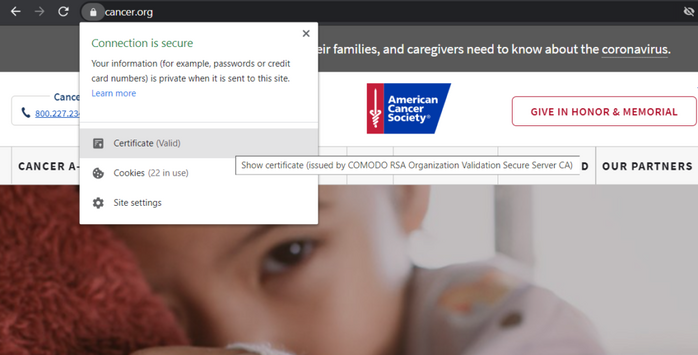
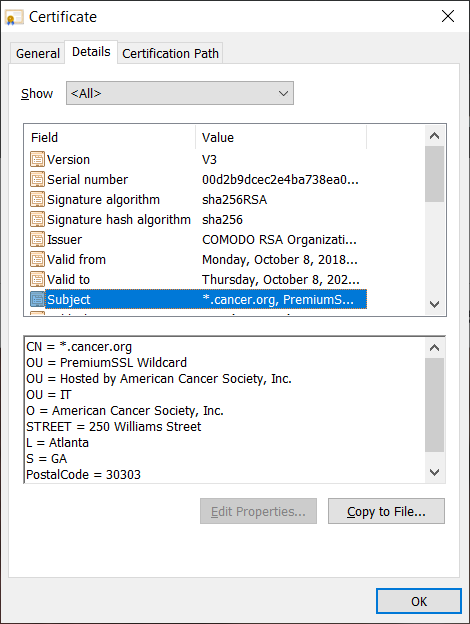
This is why organization validation should be the minimum form of validation for businesses that collect, process or use sensitive or personally identifiable information (PII). Ideally, organizations that collect and process these types of information should be using extended validation. But if they don’t, then OV should be the absolute minimum form of validation.
Extended Validation
Extended validation is the most in-depth form of business validation that certificate authorities offer. This type of certificate requires the most verification about your organization and generally takes up to five days to issue.
The Vanguard site is an example of a site that uses an EV certificate.
Why Do We Need Certification Authorities?
Why do you need a driver’s license or state ID card? Because it helps you prove that you’re you to third parties who wouldn’t know otherwise. A CA helps you to establish trust with others because they’re trusted for issuing valid, reliable certificates — and that trust is integral to public key infrastructure (PKI). (We’ll speak more to PKI later.)
Trust gives you credibility in the eyes of others. To put it simply, public certificate authorities vouch for you — they attest to browsers, email clients and operating systems that you’re you and that you’re trustworthy. They do this by vetting you and issuing digital certificates. Without a trusted third party to stand in and vouch for you, how would anyone know whether you are trustworthy? Again, it’s like having the DMV issuing you an official ID card that proves you’re you.
The same thing basically happens when you request an SSL/TLS certificate for your company’s website. A public CA is responsible for adhering to strict standards and processes when vetting your organization’s information. They do this through a series of set processes and by using official documents and resources. This makes it so that web browsers, email clients, and operating systems trust them to verify that you are who you claim to be.
CAs Provide Verification (and Help You to Establish Trust with Others)
Publicly trusted CAs — and the digital certificates they issue — are central to the public key encryption trust model that’s at the heart of public key infrastructure (PKI). (We’ll talk more about PKI and digital certificates shortly.)
What Makes a Public CA Trustworthy?
Third-party certification authorities are inherently trustworthy for two main reasons:
- Public CAs are autonomous and not controlled by certificate requestors. This is a huge difference between public and private certificate authorities — public CAs are separate from the entities that request certificates.
- Public CAs (and the certificates they issue) have standards to meet as a minimum. For example, the CA/Browser Forum (CA/B Forum) has baseline requirements. Because of the way that the certificates are created, they’re unforgeable, meaning that no one can modify them without you knowing it.
It’s All About Trust…
For the authentication framework that a certificate authority helps create to work, it’s essential for the CA to have the trust of third-party organizations. This is where the X.509 standards come into play — these standards outline the X.509 digital certificates that are central to public key infrastructure (PKI). (We’ll speak more to these certificates shortly.) The latest version of the standards is X.509 (10/19), which was approved in October 2019 but requires payment to access.
The X.509 (10/2016) standards document — the latest free version of the standards — refers to trust in a CA as the:
“Belief that the certification authority (CA) will act reliability and truthfully in the management of its public-key certificates and will comply with its published certification practise statement and relevant legislation.”
Yes, I know there’s a typo in there — it should say reliably instead of reliability, but what can you do? Typos happen. That aside, the main take away here is that the CA is expected to behave a certain way and serve as a reliable — trustworthy — certification entity.
The original X-509 (11/1988) standards document talks about the importance of trust:
“The key role of trust in the authentication framework is to describe the relationship between an authenticating entity and a certification authority; an authenticating entity must be certain that it can trust the certification authority to create only valid and reliable certificates.”
What Is an Example of a Certification Authority?
Sectigo is an example of a publicly trusted certificate authority. In fact, Sectigo ranks among the world’s largest commercial CAs. There are a few hundred CAs, but the truth of the matter is that only around a dozen or so are ones that the majority of organizations and individuals rely upon for issuing their digital certificates.
So far, we’ve only discussed public CAs (and, frankly, that’s going to be what we focus on in this article). But did you know that there’s actually more than one type of CA? There are two types of certificate authorities: public and private CAs.
Private Certificate Authorities
A private CA (or private certification authority) is an internal CA that’s controlled by the organization that it issues certificates for. It’s essentially the equivalent of you signing your own driver’s license to prove your identity. While using something that’s self-signed may work within your own organization, needless to say, that kind of approach just ain’t gonna fly with third parties who don’t know you.
Public Certificate Authorities
Public certificate authorities, on the other hand, are separate entities that aren’t controlled by the organizations they issue certificates to. This is why when people talk about CAs, they typically are talking about public CAs.
What Is the Role of a Certificate Authority in Public Key Infrastructure?
Public key infrastructure is defined by the X.509 standards as the following: “The infrastructure able to support the management of public keys able to support authentication, encryption, integrity or non-repudiation services.” Basically, PKI is the framework — the policies, procedures, and technologies — that the foundation of website security is built upon.
Without PKI, data would only be able to transmit across the internet in plaintext form without the use of encryption to disguise it. And no one would know for certain whether the entities they’re communicating with on the other end of websites or emails are legitimate.
Certification authorities are one of the core components of the overarching public key infrastructure. This infrastructure involves:
- A variety of entities (certificate authorities, web browsers, operating systems, etc.)
- Regulatory standards, processes and procedures (as outlined by the CA/B Forum)
- PKI digital certificates (which securely ties your distinguished organizational name and key to your identity),
- Digital signatures (which sign the digital certificates), and
- Public-private key pairs.
If you’re interested in reading more about PKI specifically, check out our other article that breaks down what PKI is and how it works. But, basically, these PKI certificates are known as X.509 digital certificates or X.509 public key certificates.
What Is a Digital Certificate and What Does It Do?
Remember earlier when we said that a public CA is like the DMV of the internet? Well, a PKI digital certificate is like your government-issued ID card or passport — it’s a form of documentation that shows others who don’t know you that you are who you claim to be. But in this case, instead of your picture and other license information, it’s a digital file that contains the following crucial data:
- Your organization’s name and information — The subject field shows that your organization is legitimate and owns the certificate.
- Your public key — This is the half of your public-private key pair that’s publicly known.
- The certificate issuer’s name — This is the name of the certificate authority (such as Sectigo) that issues the certificate.
- The CA’s digital signature — This shows that the certificate was, in fact, issued by a reputable CA.
- A serial number — This is a code that’s unique to your individual SSL/TLS certificate.
- Your certificate’s issuance and expiration dates — These certificates are only valid for a set amount of time — up to 398 days starting Sept. 1, 2020).
This information helps you to validate your organizational identity to others. For example, you validate to website users’ browsers that your website/server actually belongs to your organization.
The Different Types of X.509 Digital Certificates
Of course, CAs can issue more than just website security certificates (SSL/TLS certificates). They also issue:
- Code signing certificates
- Document signing certificates
- Email signing certificates (also known as S/MIME certificates)
How Certificate Authorities Issue Digital Certificates for Websites
The process of how a third-party certification authority issues SSL/TLS certificates is a bit long. So, we’ve included this graphic to help illustrate the process:
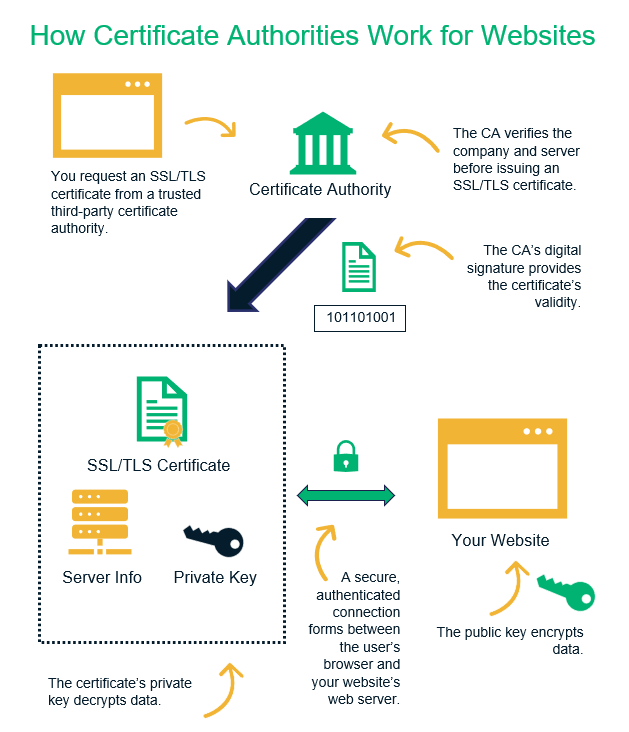
As you can see in the illustration above, it starts with you requesting an SSL/TLS certificate for your domain from a public CA. Before the certificate authority can issue the cert, they first need to verify your identity and that you also control the domain in question. Once they do this, they can then issue your certificate, which they apply their digital signature to prove that they issued it.
Once you have the certificate, you can then install it on your web server. This allows you to verify your identity and to establish secure, encrypted communication channels with site users’ browsers.
TLDR; A Quick Overview of Certification Authorities
Yeah, that was a lot of information to slog through. So, to make this easy for those of you who want to just skim or need a quick recap, here are the big takeaways about public certificate authorities:
- Certificate authorities are the equivalent of an ID card-issuing authority like the Department of Motor Vehicles.
- They enable you (your organization) to authenticate yourself to third parties who don’t know you. They do this by issuing digital certificates that they digitally sign that prove that you’re legitimate.
- Public CAs are integral to public key infrastructure and internet security as a whole. They’re what make it possible to establish trust.
- Sectigo is an example of a publicly trusted CA.
- The X.509 digital certificates that they issue can help you to authenticate yourself or your organization to others via websites, emails, software and documents.
- There are three levels of validation that they can use to verify your information: domain validation, organizational validation and extended validation.














 (14 votes, average: 4.43 out of 5)
(14 votes, average: 4.43 out of 5)







2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security