What Is a Honeypot in Network Security? Definition, Types & Uses
Let’s find out if using honeypots to invite attackers into your network boosts your organization’s security
Ever wonder if there’s a way to outsmart hackers and beat them at their own game? There sure is, and honeypots in network security make the perfect bait. A security honeypot server is something you can deploy to lure cybercriminals into attacking what they think is the organization’s actual network but is just a decoy.
Honeypots in network security are a way to trick attackers into investing time and effort exploiting deliberate vulnerabilities while alerting your internal security team of their compromise attempts. The information you receive from observing a live attack through security honeypots is much more detailed than what you get from some intrusion detection systems. And it also helps to keep cybercriminals from attacking your legitimate targets.
In this article we’ll answer questions like “what is a honeypot server?” and “what are the different types of honeypots?” as well as talk about their benefits.
Honeypot Definition & Explanation: What Is a Honeypot and How Does It Work?
When we talk about security, we often talk about how to keep cybercriminals away from your network. With honeypot traps, security practitioners achieve the opposite. But what is a honeypot? A honeypot is an open or otherwise intentionally vulnerable decoy technology that’s designed to misdirect cyber attacks from critical IT systems. It does this by mimicking those very systems and by providing fabricated files and data.
Moreover, a honeypot is a computer system that helps IT security pros observe and learn from cybercriminals’ attacks by observing them in real time. Basically, it helps organizations detect unauthorized use or access to systems. It also helps them gain crucial information about attackers and how they operate. Of course, all of this occurs with the intruder being none the wiser about what’s really happening. It may comprise of several components such as:
- Network devices,
- Keyloggers,
- Monitoring tools,
- Packet analyzers, and
- Alerting tools.
What Honeypots Do
In a nutshell, honeypots help organizations:
- Assess the latest trends in attacks,
- Understand where cyber attacks arise, and
- Better frame security policies to mitigate future risks.
This deceptive technology can be hardware-based (like an appliance) or software-based virtual honeypots that can scale and be set up to emulate a legitimate network.
How Honeypots Work
Honeypots are a way for organizations and businesses to detect, deflect and fight back against cybercriminals who desire unauthorized access. Honeypot traps lure bad guys into attacking these fake networks, servers, or other devices because they contain applications and data similar to legitimate targets.
Ever watch Shark Week on the Discovery Channel? Marine biologists and other scientists use chum and bait to lure sharks into attacking decoys while they record it with video, pressure sensors, and speed-monitoring technologies. This is part of their research to learn more about sharks by observing their hunting methods and attack tactics as they occur. Honeypots are much the same — just for cyber attacks instead of shark attacks.
But wouldn’t a hacker realize that they’re attacking a fake system? Not necessarily. Honeypots are designed to appear like legitimate systems. In fact, they typically contain a variety of fake data to make them seem legitimate. So, when bad guys attack, their efforts appear successful on their end. This keeps them on your system longer so you can log and record more information about their attack.
What Is a Honeypot vs Honeynet
A network of honeypots (honeynet) can be placed in different positions, for example — outside the external firewall, in the DMZ, or within the internal network. A honeynet has servers, networking devices, and systems that are similar to a legitimate network with fake data. Since the purpose is to lure attackers into exploiting intentionally vulnerable systems to monitor and study their activities, placing a honeynet on the internal network is risky business unless the attack can be trapped within it.
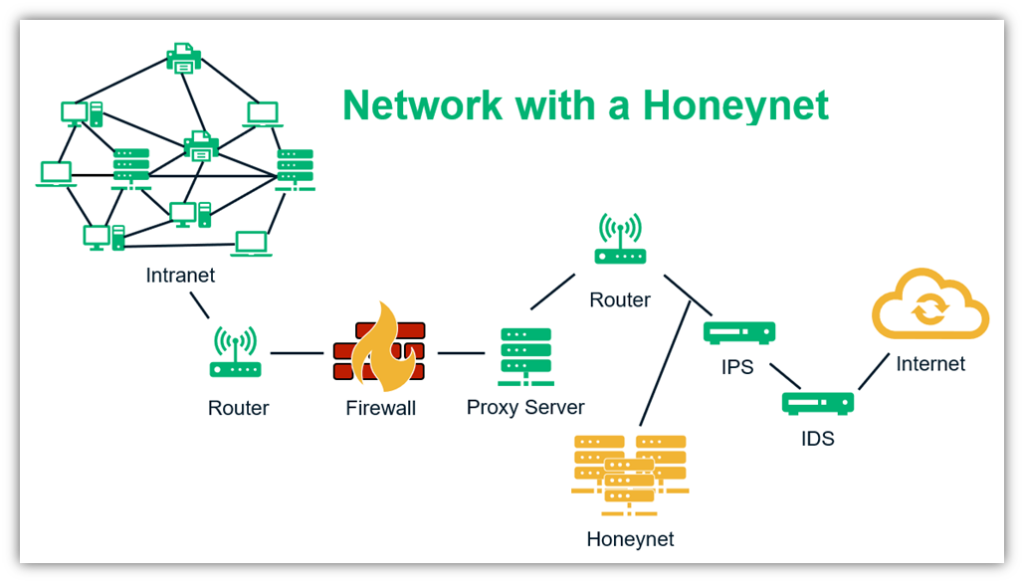
However, since more than 75% of security incidents occur due to insider threats, installing a honeypot with proper configurations to monitor user behavior on the internal network is often worth the risk. A honeypot on the internal network can detect misconfigured firewall settings and be useful in detecting zero-day exploits. All in all, installing honeypots can strengthen your organization’s network security posture significantly.
What Are the Different Types of Honeypots?
Honeypots are typically categorized in one of two ways — either based on their interaction levels or the types of threats they’re able to detect. We’ll first take a quick look at the different types of honeypots based on their interactivity levels before moving on to talk about honeypots based on their purpose.
Types of Honeypots Based on Interaction Level and Complexity
Interaction levels define the hacker’s degree of interactivity with the systems that they’re attempting to infiltrate. “Pure” honeypots mimic the full-scale production environment and run on servers with live, faux “sensitive” data. They’re the most complex honeypot systems to deploy and are challenging to maintain. Some other options include:
High-Interaction Honeypots
These honeypots imitate real-world systems and applications with actual services, functions, and operating systems involving high levels of interactivity (though less than pure honeypots). Setting up high-interaction honeypots is a complex and resource-intensive process. It gives extensive details about how an attack progresses and how payloads execute in a network. However, since there are actual operating systems and services involved, the chance of infection is higher if the hackers are able to compromise the honeypots and use them gain access to your organization’s real production environment.
Medium-Interaction Honeypots
As the name suggests, medium-interaction honeypots fall between high and low interaction honeypots. They come with expanded capabilities compared to low interaction honeypots but reduced implementation complexities than high interaction honeypots. They imitate the application layer but don’t have their own operating system. Organizations typically deploy these types of honeypots to stall attackers to give them time to respond to attacks.
Low-Interaction Honeypots
Low-interaction honeypots allow partial interaction with systems since they run limited emulated services with restricted functionality as would be typically expected from a server. Though these are the easiest to set up and maintain, they run the risk of coming across as inauthentic targets to potential attackers. These types of honeypots serve as an early detection mechanism, and organizations commonly use them in production environments.
Some Other Types of Honeypots
- Malware Honeypots — These types of honeypots detect malware based on known replication techniques and propagation vectors.
- Database Honeypots — Since attacks on databases like SQL injections are fairly common, you can use database honeypots to distract an attacker from your legitimate database servers by setting up decoy databases.
- Client Honeypots — These honeypots typically act as servers, listening in for incoming connections. Client honeypots actively engage with malicious servers that attack clients. They pose as a client to monitor and record any modifications.
- Email Honeypots — Email honeypots are a list of email addresses used by email service providers to detect spammers. Typically, accounts inactive over a long period of time are used for this purpose.
- Spider Honeypots — These honeypots are used to trap web-crawlers by creating fake web pages and links only reachable by crawlers. Detecting these crawlers can be useful in blocking bot activity.
Types of Honeypots Based on Purpose
What drives the need for setting up a honeynet in your environment? There are different types of honeypots that serve different purposes. Do you need insights to study attack methodologies for research purposes or respond efficiently to active internal security threats? Or are you just trying to thwart attackers from attacking their real targets?
Research Honeypots
These honeypots are deployed and used by researchers to gain a better understanding of attack techniques, motivations, information about malware strains in the wild, and security vulnerabilities. This is done to specifically use the knowledge gained to make informed decisions about:
- Defense strategies,
- Patching prioritizations,
- Future security investments, and
- Identifying and developing new security solutions.
Production Honeypots
Production honeypots are placed within your organization’s internal network with other production servers. Though the intention is similar in terms of gaining insights about active attacks, it is typically less complex than research honeypots with lesser data. It is primarily deployed to identify active attacks on the internal network and distract or misdirect hackers from attacking your legitimate servers.
Benefits of Honeypots
Placing a honeypot in your network doesn’t replace or fulfill the needs of other traditional security controls such as intrusion detection systems (IDS), intrusion prevention systems (IPS), firewalls, etc. Instead, it complements the existing systems by providing highly specific information. A honeypot:
- Distracts cybercriminals from targeting legitimate systems. The more time and effort they spend on the honeypot, the less they have to invest in attacking your organization’s real network and systems.
- Gives you greater visibility of attacks as they’re happening. Logs an attacker’s keystrokes during a session and share instant alerts whenever there is an attempted access to the system.
- Monitors an attacker’s behaviors and detect zero-day vulnerabilities. An IDS/IPS, on the other hand, relies on already published signatures to identify an attack.
- Puts your organization’s incident response capabilities to the test. Does your team know how to take appropriate countermeasures to block the attacker’s access to legitimate servers?
- Helps to improve your organization’s overall security. A honeypot shines a light on the types of adversaries and attacks in the wild so that you can formulate appropriate prevention strategies.
Disadvantages of Honeypots
Though there are several benefits of using a honeypot, doing so doesn’t come without risks. Some of them, like high-interaction honeypots, can be resource intensive and difficult to maintain.
- Perhaps one of the primary downsides with using honeypots is that it may introduce additional risks into your environment. A compromised honeypot that’s not isolated effectively may be used launch an attack on the real network.
- Another major drawback of using honeypots is that it can only detect an intrusion when it is attacked directly. However, if an attacker identifies the honeypot for what it is, they can evade the system and infiltrate the network.
- Additionally, attackers may be able to fingerprint a honeypot (i.e. identify honeypots) based on certain specific characteristics such as misspelt error messages and so on. They can launch false attacks to distract administrators and while the organization chases these alerts, the attacker can focus on orchestrating a real attack.
Wrapping Up on Honeypots
Now you know the answer to “what is a honey pot” and why they’re useful tools for both research and an organization’s cyber security defenses. There are several different honeypot tools that can be used based on a particular service or application you’re trying to secure. Honeyd is an open-source tool that can be used as a honeypot, hence the name. It can spin up multiple virtual hosts, which you can configure to mimic different servers.
For organizations that are willing to take a proactive approach towards strengthening their defenses, honeypots can offer enormous benefits. However, to detect attacks that avert the honeypot network (suppose an attacker gets alerted to its presence), other defense mechanisms need to be in place.





















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security