Cyber Attacks 2020! 20 of 2020’s Notable Cyber Attacks
Cloud-based attacks rose 630% between January and April 2020! Let’s explore 20 of the cyber attacks we’ve seen (so far) in 2020…
As if the world isn’t facing enough difficulties in 2020, cybercriminals are contributing to greater anxiety in the collective consciousness. Just like every year, we’ve witnessed a large number of cyber attacks in 2020 so far, exposing millions of data records and executing the most dangerous cybercrimes against individuals and organizations. Out of thousands of cyber attacks that took place so far this year, we’ve handpicked 20 of the most noteworthy 2020 cyber attacks to cover.
In this article, we’ll share examples of cyber attacks that targeted people, businesses, and other entities along with the data breaches that resulted from them. This includes info about attackers using leaked data for financial fraud, identity theft, ransomware attacks, brute-force attacks, and getting unauthorized access to user accounts.
If you’re looking for information specifically relating to COVID-19 scams, we recommend reading this article on Coronavirus Scams.
Table of contents
- Cloud-based attacks rose 630% between January and April 2020! Let’s explore 20 of the cyber attacks we’ve seen (so far) in 2020…
- Cyber Attacks 2020: 20 Attack Examples (So Far)
- 1. Iranian Hackers Attack U.S. Government’s Library Program Website
- 2. Hacker Group Steals 25 Million Students’ Data from Math App’s Database
- 3. Cybercriminal Post Credentials of 3.68 Million MobiFriends Users in Web Forum
- 4. Attackers Launch a Massive DDoS Attack Against Amazon
- 5. A Hacker Accesses GoDaddy’s Servers to Steal Users’ Login Credentials
- 6. Ransomware Attack Steals 800 GB of Sensitive Data from W&T Offshore
- 7. Network Break Leads to Theft of 11 Million Banco BCR Payment Card Credentials
- 8. A Hacker Posts 15 Million Tokopedia Users’ Data on The Dark Web
- 9. Australia’s Home Affairs Department Leaks 774,000 Immigrants’ Data
- 10. A Hacker Tries Selling Unacademy’s 21,909,709 Registered Users’ Data Online
- 11. Phishing Email Leads to Leak of More Than 12,000 Nikkei Employees’ Data
- 12. The Hacker Group ShinyHunters Lists 73 Million User Records for Sale
- 13. A Cyber Attack on EasyJet Affects 9 Million Customers
- 14. A Hacker Publishes 2.3 Million Indonesian Voters’ Data on The Darknet
- 15. Bigfooty.com’s Leaky Database Exposes 132GB of Customer Data
- 16. UCSF Pays $1.14 Million Ransom
- 17. Cloudflare Becomes the Target of a Massive DDoS Attack
- 18. Bitcoin Scammers Hacks 130 Celebrities’ Twitter Accounts
- 19. Avon Leaks 19 Million Document Records
- 20. New Zealand Experiences a Wave of Cyber Attacks
- 1. Iranian Hackers Attack U.S. Government’s Library Program Website
- Wrapping Up on Cyber Attacks 2020
Cyber Attacks 2020: 20 Attack Examples (So Far)
It’s been an only half year passed, and we have witnessed some of the ugliest cyber attacks of 2020. We’ve compiled a list of notable 2020 cyber attacks in chronological order — from January to August — to make it easy to follow.
1. Iranian Hackers Attack U.S. Government’s Library Program Website
We’ll kick off our list of 2020 cyber attacks with an attack on the Federal Depository Library Program website. The site displayed a disturbing image over a map of the Middle East on Jan. 6, 2020. The image consisted of:
- A tribute to Iran’s late major general Qassim Soleimani,
- A declaration of taking revenge for the commander’s death,
- A doctored image of an arm and fist labeled “Iran” that punches U.S. President Donald Trump in the face,
- A message stating that “This is only a small part of Iran’s cyber ability!”
The attackers exploited a misconfigured content management system (CMS) to insert the image and messages. Although this cyber attack didn’t involve a data breach, this incident shines a light on the cyber threats that face government-owned websites. Attackers constantly search for misconfigurations and small vulnerabilities in websites’ security postures that they can exploit.
2. Hacker Group Steals 25 Million Students’ Data from Math App’s Database
In January 2020, a hacker group named Shiny Hunters stole 25 million students’ email addresses and passwords from a math solving app, Mathway. A report by ZDNet shows that the attackers put the data up for sale for $4,000 on the dark web on May 18, 2020.
The passwords were encrypted, and the onus of decrypting them was on the buyers. Even if the buyer of the data can’t decrypt the passwords, having a list of 25 million email addresses is still useful for sending malware-laden phishing or spam emails to the students.
3. Cybercriminal Post Credentials of 3.68 Million MobiFriends Users in Web Forum
According to Risk Based Security’s report, on Jan. 12, 2020, a hacker named “DonJuji” tried to sell the sensitive data about nearly 4 million MobiFriends users on a deep web hacking forum. On Apr. 12, 2020, the same data was posted without restrictions by another person on the same website.
MobiFriends is a Barcelona based popular dating website. The database includes the following information of 3,688,060 users:
- Email addresses,
- Usernames,
- Encrypted passwords,
- Mobile numbers,
- Dates of birth,
- Genders, and
- Website activities.
The data included corporate email addresses of Fortune 1000 companies, including American International Group (AIG), Experian, Walmart, and Virgin Media. If the users are using the same breached passwords to log in to their corporate email addresses, these companies can be at risk of business email compromise (BEC) related cybercrimes. Although Risk Based Security reports that the passwords were encrypted with the MD5 algorithm, it’s not considered a very robust hashing algorithm.
Let’s move on to the next item on our list of 2020 cyber attacks.
4. Attackers Launch a Massive DDoS Attack Against Amazon
In Feb. 2020, Amazon Web Services (AWS) became the target of a massive distributed denial of service (DDoS) attack. The company experienced and mitigated the DDoS attack, which had a magnitude of 2.3 terabits per second (Tbps). It also had a 293.1 Mpps packet forwarding rate and 694,201 request rate per second (rps). The DDoS attack caused three days of elevated threat during a single week and is thought to be one of the biggest DDoS attacks in history.
5. A Hacker Accesses GoDaddy’s Servers to Steal Users’ Login Credentials
GoDaddy, one of the biggest hosting provider company, notified some of its customers about an altered SSH file in GoDaddy’s hosting environment that led to a data breach incident on Apr. 23, 2020. The letter informed the users that an unauthorized individual tried to access users’ hosting accounts using the exposed credentials.
GoDaddy reset the users hosting accounts’ login credentials to prevent further damage. They also provided a one-year subscription of website malware removal tool for free to the affected customers to make up for this incident.
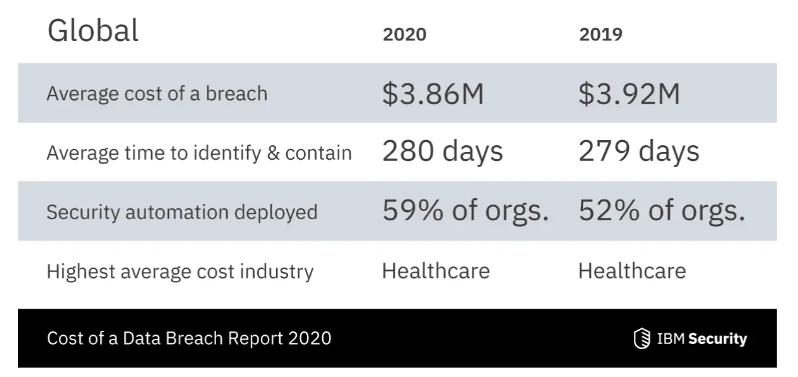
I think the most disturbing thing about this incident is the time gap. Although the incident took place on Oct. 19, 2019, GoDaddy didn’t notice it until Apr. 23, 2020. According to IBM’s Cost of a Data Breach Report 2020, it takes an average of 280 days to identify and contain a data breach in 2020! In that amount of time, an attacker can not only exploit the system but also sell the breached credential on the dark web to other cybercriminals.
6. Ransomware Attack Steals 800 GB of Sensitive Data from W&T Offshore
Security research firm Cyble Inc. published a report on Apr. 28, 2020, about a ransomware attack on W&T Offshore. According to the report, Netfilim ransomware operators stole 800 gigabytes of sensitive data from the Texas-based oil and gas company.
The report further states that the company’s ransom negotiations with the attacker failed, resulting in the cybercriminal releasing 10 GB of the data on the dark web. The leaked data included sensitive financial documents as follows:
- Bank reconciliation statements,
- Journal entries,
- Company’s risk analytics model, and
- Long-term debt reports.
7. Network Break Leads to Theft of 11 Million Banco BCR Payment Card Credentials
BleepingComputer published an article on May 1, 2020, about Maze ransomware operators who are claiming responsibility for stealing 11 million credit card credentials from Banco de Costa Rica’s (BCR) network.
Banco BCR is a government-owned commercial bank. The report shares that the bank’s network was accessed in August 2019 and again in February 2020, but the attackers claim to have stolen “a few years of data, including 11 million credit cards.”
Of those 11 million records, 4 million are unique, and 140,000 belong to U.S. residents. As proof, hackers posted:
- 240 credit card numbers (without disclosing the last four digits),
- The cards’ expiration dates, and
- The cards’ verification codes (CVV).
The attackers told BleepingComputer that they are unable to contact bank authorities to negotiate the ransom. On May 22, 2020, Cyble Inc posted a report stating the Maze ransomware operators have started to release Banco’s customers’ credit card details on the dark web. The attackers released a 2GB CSV file containing various Mastercard and Visa credit and debit card information because the bank wasn’t taking their leak claims seriously.
8. A Hacker Posts 15 Million Tokopedia Users’ Data on The Dark Web
Next on our list of 2020 cyber attacks comes from the data breach monitoring and prevent service Under the Breach. They posted a tweet on May 2, 2020, that shared that a hacker listed the personal data of 15 million Tokopedia customers for sale on the dark web. The data comes from a hack that occurred back in March. On May 3, the firm released an update that the attacker has 91 million records of the victim, which they are selling for $5,000.
According to ZDnet, the data includes:
- Full names,
- Email addresses,
- Phone numbers,
- Hashed passwords,
- Dates of birth, and
- Tokopedia profile-related details
Thankfully, the passwords were encrypted using the SHA2-384 hashing algorithm, so the hacker could not decrypt the passwords. The company’s spokesperson said they had taken measures to protect their customers’ data but still advised users to change their passwords as the precautionary measure.
9. Australia’s Home Affairs Department Leaks 774,000 Immigrants’ Data
The media outlet The Guardian published a report on May 2, 2020, indicating that Australia’s Home Affairs Department has a leaky database that exposes personal details of 774,000 existing and would-be migrants online.
The database leaked migrants’ information such as:
- 774,326 unique identifiers known as ADUserIDs,
- 189,426 completed expressions of interests,
- The outcome of the applications, and
- Applicants’ birth countries, ages, qualifications, and marital statuses.
After The Guardian’s report, the Australian government took the information offline.
10. A Hacker Tries Selling Unacademy’s 21,909,709 Registered Users’ Data Online
Unacademy comes in next on our list of 2020 cyber attacks. Unfortunately, India’s largest educational platform was schooled in an unfortunate lesson in cybersecurity on 8 May when a hacker began selling nearly 22 million Unacademy users’ data on the dark web. The security firm Cyble reports that the hackers were selling the entire Unacademy database for $2,000.
Cyber Inc.’s report says the data contained:
- First names,
- Last names,
- Usernames,
- Encrypted passwords, and
- Email addresses.
It also included details related to Unacademy’s user profiles and their roles and statuses. The leaked database also contains corporate email addresses that belonged to reputed organizations such as Wipro, Reliance Industries, TCS, Google, and Facebook. If users are using the same password for their corporate email account, the attackers can break into these corporation’s email network as well.
When questioned about the security measures taken to secure data by Mint, Unacademy’s co-founder Hemesh Singh responded that misusing the leaked data to access passwords is “highly implausible.” That’s because they use the SHA256 algorithm to protect their passwords and a one-time password (OTP) based login system to provide two-factor authentication (2FA).
11. Phishing Email Leads to Leak of More Than 12,000 Nikkei Employees’ Data
Nikkei Inc., a prominent Japanese newspaper publisher, announced a data leak relating to the personal data of 12,514 contract employees. The cause of the attack? A phishing email that appeared to be coming from Nikkei’s internal network itself had a virus in it.
The virus infected a portion of Nikkei’s internal email system and stole 12,514 contract employees’ details, including names, affiliations, and email addresses. The data was leaked on May 8, 2020.
12. The Hacker Group ShinyHunters Lists 73 Million User Records for Sale
A hacker group ShinyHunters listed individual databases containing a total of 73.2 million user records from 10 different companies for sale on the dark web for $18,000. ZDnet’s report from May 9, 2020 shares that ShinyHunters is the same group that was responsible for the Tokopedia data breach back in March.
According to the report, the list of the 10 companies with breached data includes:
| Company name | Number of breached user records |
| Zoosk | 30 million |
| ChatBooks | 15 million |
| SocialShare | 6 million |
| Home Chef | 8 million |
| Minted | 5 million |
| Chronicle of Higher Education | 3 million |
| Ggumim | 2 million |
| Mindful | 2 million |
| StarTribune | 1 million |
| Bhinneka | 1.2 million |
13. A Cyber Attack on EasyJet Affects 9 Million Customers
BBC reported that the budget airline EasyJet had been the victim of a highly sophisticated cyber attack in which nine million customers’ email addresses and travel details were stolen. The report states that attackers were also able to access 2,208 customers’ credit card/debit card numbers along with CVV.
Although EasyJet was aware of the data breach since January, it didn’t disclose this matter to the general public until May 19. However, the airline did inform the customers whose payment card details have been stolen in April. EasyJet has informed UK’s Information Commissioner’s Office (ICO) about the breach to help them further investigate it.
14. A Hacker Publishes 2.3 Million Indonesian Voters’ Data on The Darknet
According to a report published on Reuters on May 22, a hacker released 2.3 million Indonesian voters data on the hacking forum Raidforums on May 20, 2020. The data included sensitive details such as home addresses and national identification number of the voters. The attacker had also given a threat to release the other 200 million voters’ data. Indonesia’s General Election Commission confirmed the authenticity of the voters’ data.
15. Bigfooty.com’s Leaky Database Exposes 132GB of Customer Data
Security researcher Anurag Sen and his team atof Safety Detectives found a leaky database of bigfooty.com on Bigfooty’s parent company Big Interest Group LLC’s server on May 29, 2020. Bigfooty.com is a famous Australian football fan forum with more than 100,000 members.
The leaky Elasticsearch database had 132 GB of data containing approximately 70 million user records. Up to 100,000 users were affected by this leak, which included data such as:
- Usernames
- Passwords
- Email addresses
- Mobile phone numbers
- Personal messages and data relating to behaviors and activities
In Bigfooty, users get an option to be anonymous. However, with the above details, it becomes possible to track down the anonymous users’ identities, including those who were sending personal threats and racist material in private messages. Comments posted by high-profile users such as Australian police officers and government employees can also be tracked down. Attackers can easily use such details for ransomware attacks, blackmailing, personal revenge, and ruining the image or reputation of a person and organization.
The leaked data also included the website’s internal technical information related to IP addresses and GPS locations, operating system and server data, access and error logs, etc. Such information can be used by hackers to execute other serious crimes against the website.
16. UCSF Pays $1.14 Million Ransom
The University of California San Francisco (UCSF) hit by a ransomware attack on Jun. 1, 2020. The Netwalker ransomware operators encrypted some important servers from the university’s medical-research institution, which was working on a cure for COVID-19.
Although the university’s staff isolated the malware-infected servers from the core UCSF network, they didn’t have any plans to get back to unlock the hacked servers and decrypt the data. Hence, UCSF negotiated with the hackers and paid $1.14 million (116.4 bitcoins) to Netwalker operators on Jun. 26, 2020. In return, hackers sent the decryption key to UCSF, which they used to get back access to the servers and the lost data.
17. Cloudflare Becomes the Target of a Massive DDoS Attack
An attacker launched a massive DDoS attack against Cloudflare, a leading U.S. web infrastructure and security company, on Jun. 18, 2020. The attack continued for four days before ending on Jun. 21. These are the details that Cloudflare shared about the severity of the attack:
- The June 2020 DDoS cyber attacks lasted for multiple hours at rates exceeding 400-600 million packets per second (pps). It peaked multiple times above 700 million packets per second.
- At the peak of the attack, 754 million pps were sent out from more than 316,000 different IP addresses.
- A combination of three types of TCP attack vectors was used: SYN floods, SYN-ACK floods, and ACK floods.
The attackers targeted one particular Cloudflare IP address that was mostly used for websites on the free subscription plan.
Fortunately, the attack was detected and handled by Cloudflare’s own DDoS detection and mitigation tool named Gatebot. The customers experienced no downtime and service discrepancies. While Cloudflare was able to mitigate the DDoS attack successfully, not all companies can say the same. For other companies, especially for startups and small companies, escaping such a massive DDoS attack virtually unscathed is an enormous feat.
18. Bitcoin Scammers Hacks 130 Celebrities’ Twitter Accounts
Several attackers hacked 130 high-profile Twitter accounts and posted cryptocurrency scam message from their profiles on Jul. 15, 2020. According to Twitter, the posts were the result of a social engineering attack that resulted in tweets from 45 accounts, accessing the direct message inboxes of 36, and downloading the Twitter data of seven others.
For example, the fraudulent message posted using Joe Biden’s account was as follows:
“I am giving back to the community. All Bitcoins sent to the address below will be sent back doubled! If you send $1,000, I will send back $2,000. Only doing this for 30 minutes.”
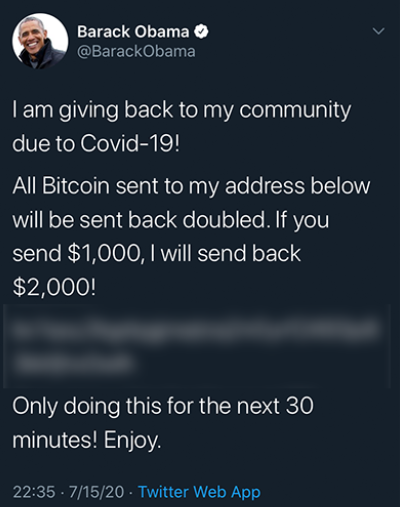
The list of celebrities included Barack Obama, Joe Biden, Elon Musk, Kanye West, and Bill Gates — all of who have millions of followers. Hackers gained access to Twitter’s own internal administration tool through the social engineering attack. Twitter immediately put a temporary hold on all the verified users to post anything from their accounts. However, the attackers were able to trick some people into falling for this scam and received more than $100,000 worth of Bitcoin.
19. Avon Leaks 19 Million Document Records
The Safety Detectives team published a report on Jul. 28, 2020, revealing some major vulnerabilities in the cosmetic giant Avon’s servers. They discovered that a leaky database containing 7 GB of customer and employee data. The data, which could be accessed by anyone with the server’s IP address, included everything from their names and GPS coordinates to their email addresses and phone numbers. Such details can be used for phishing attacks and identity theft-related crimes.
The database also included details about Avon’s internal technical components such as:
- Security tokens, SMS verification service logs,
- OAuth tokens,
- 3 million technical log entries,
- Account settings information,
- 11,000+ entries marked as “salesLeadMap,” and
- Technical server information.
An attacker can easily use these details to execute massive cyber attacks against the website or sell the data to competitors or marketers.
The Safety Detectives team discovered the leaky database on Jun. 3, 2020, itself. But, fortunately, before releasing the information to the public, they contacted Avon, and the company took steps to secure it.
20. New Zealand Experiences a Wave of Cyber Attacks
Alright, we’ve reached the last item on our list of 2020 cyber attacks. New Zealand’s various services and websites found themselves the targets of various 2020 cyber attacks during the month of August. For example, entities such as Westpac Bank, MetService weather news website, Kiwibank, and TSB bank experienced service outages and issues due to cyber attacks.
Among the biggest targets, however, was the New Zealand Stock Market (NZX). The NZX had to halt trading due to a severe DDoS attack that lasted for five consecutive days, Aug. 24-Aug. 28. The magnitude of the attack was more than one terabit a second (Tbps) at its peak. Prior to the attack, a hacker (or group of hackers) sent an email to NZX and warned about the potential cyber attack. According to Stuff.co.nz, the attackers might have been seeking to extort ransom payments in Bitcoin to halt the attacks.
Wrapping Up on Cyber Attacks 2020
As you can see from the above 2020 cyber attack incidents, your data is not secured even with the big reputed organizations and government institutions. Cybersecurity is a continuous process, and that’s why all the big organizations keep a cybersecurity team that is dedicated to data protection and preventing various types of cyberattacks. But startups, small businesses, and SMBs generally have tight budgets and can’t necessarily afford to hire cybersecurity experts. But there are some DIY cybersecurity tricks you can follow to strengthen your company’s cybersecurity posture.
We’ve compiled a list of eight articles to help you mitigate cyber risks. Check out these simple yet powerful cybersecurity tips to help prevent your business from making headlines as the target of any 2020 cyber attacks:
- Top 25 Recommendations for Small Business Cyber Security
- How to Prevent Malware Risks in 9 Ways
- 5 Best Ransomware Protection Tips to Protect Your Organization
- 8 Data Leakage Prevention Tips for Your Organization
- 10 IoT Security Tips You Can Use to Secure Your IoT Devices
- 10 Steps for How to Secure Your Email Communication
- 12 Network Security Best Practices to Secure Your Business
- 8 Crucial Tips to Secure Your WordPress Website














 (21 votes, average: 4.43 out of 5)
(21 votes, average: 4.43 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security