What Is Ransomware and How Does It Work?
Ransomware isn’t a threat to just large corporations. Datto reports that 85% of MSPs regarded ransomware as the most prominent malware threat to SMBs in 2019
Ransomware is a threat to governments, businesses, and other organizations. It can do everything from halting a major city’s operations to resulting in a business closing its doors permanently. But what is ransomware and how does ransomware work? In this article, we’re going to give you a ransomware definition and explore what ransomware does and how it creates chaos for businesses and users alike.
What Is Ransomware? A Ransomware Definition
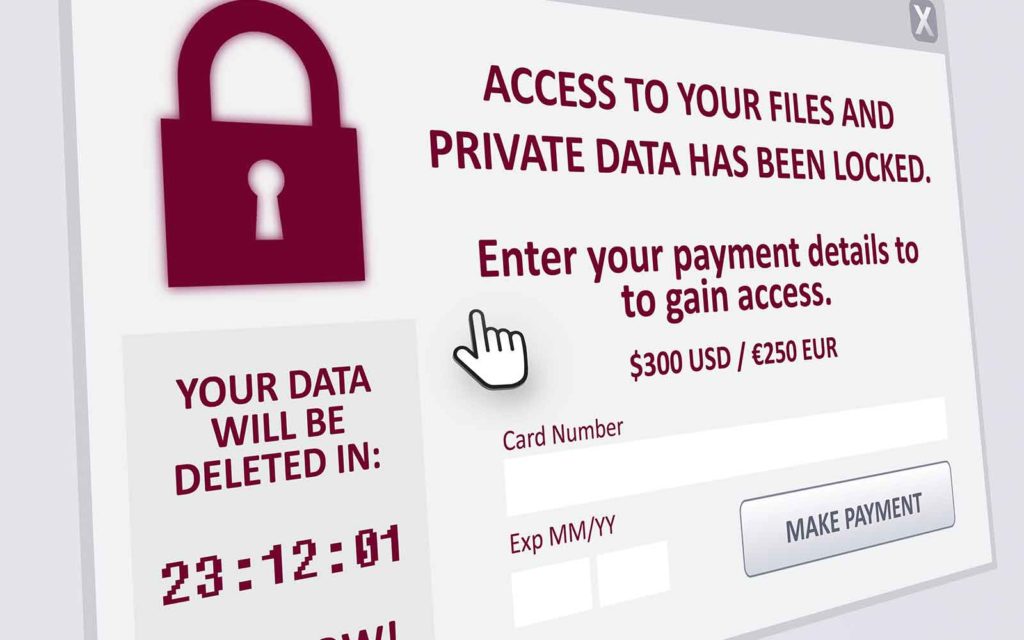
My simple ransomware definition is that it’s a type of malicious software (malware) that cybercriminals use to attack businesses where it hurts the most: access to their systems and data. Ransomware is a type of malware that blocks access to devices and/or their data. It’s named such because cybercriminals use this malware to demand payment in exchange for access to said devices and data that they hold ransom. If the victim doesn’t comply — or doesn’t do so quickly enough — the attacker may choose to delete or otherwise destroy the data so that there’s no chance of recovery.
And while ransomware isn’t a new threat, it’s certainly a growing one. We’ve seen multiple articles stating that VMware Carbon Black reported that ransomware attacks increasing 900% year-over-year in 2020, but I wasn’t able to find the original source of that information. However, data from Check Point shows that the average daily number of ransomware attacks jumped 50% in Q3 2020 in comparison to their Q2 2020 data.
To answer a question like “what is ransomware?” you need to think in terms of how some abductors operate. I say that because ransomware is similar to how criminals abduct children to extort payment — but instead of controlling children and their parents, it’s about controlling companies (or individuals, governments, organizations, or any other targets they choose) to demand payment in exchange for access to their data or devices.
Some big examples of debilitating and costly ransomware attacks include:
- WannaCry ransomware attacks (2017). This ransomware attack affected 230,000 computers in approximately 150 countries by exploiting a known vulnerability in Microsoft Windows operating systems known as EternalBlue. Although Microsoft issued a security patch for it, many neglected to apply it and were vulnerable to attack as a result.
- City of Atlanta, Georgia ransomware attack (2018). This massive ransomware attack virtually crippled this proud U.S. city’s municipal operations. The Atlanta Journal-Constitution and Channel 2 Action News reports that the attack “could cost taxpayers as much as $17 million […] roughly $6 million in existing contracts along with an additional $11 million in potential costs associated with the March 22 attack.”
- City of Baltimore, Maryland ransomware attack (2019). This eastern U.S. city found itself facing a heft price tag of more than $18 million after undergoing a ransomware attack that targeted multiple departments and agencies. The attack resulted in more than two months’ worth of mitigation efforts when all was said and done, according to a detailed timeline by Heimdal Security.
- ISS World ransomware attack (2020). This attack, which targeted the Demark-based company, represents one of the biggest ransomware attacks in terms of the overall cost. The company had to regain control of its IT systems and other critical business systems at a cringe-worthy cost of $74 million when all was said and done, Cybersecurity Insiders reports.
What Does Ransomware Do?
In a nutshell, what ransomware does is infect your device to block you from accessing your device and/or data. Sometimes, this involves encrypting the device’s data. Other times, it’s as simple as taking control of the device or locking its screen, essentially turning those devices into glorified paperweights.
Ultimately, the purpose is to interfere with an organization’s ability to operate until they cough up money to pay the cybercriminal. It’s a method of extortion, pure and simple.
The Time & Financial Implications of Ransomware
Coveware reports in its Q4 2019 Ransomware Marketplace report that ransomware attacks last an average of 16.2 days. As you can imagine, having an average of more than two weeks of downtime causes significant issues for businesses and their customers.
But ransomware doesn’t just target large corporations and governments. In fact, Coveware’s Q3 2020 data shows that 70% of ransomware attacks targeted small and medium-size businesses (companies with <$50 million in revenue and <1,000 employees). The most heavily attacked sector was professional service firms.
But just how big of an issue is ransomware? The FBI Internet Crime Complaint Center (IC3) reports that they received 2,047 ransomware-related complaints with adjusted losses of over $8.9 million in 2019 alone. (Note: those numbers only reflect the minority of incidents that somebody reports to the FBI.) However, their report is careful to note that “this number does not include estimates of lost business, time, wages, files, or equipment, or any third party remediation services acquired by a victim.”
And to make matters worse, it appears that some ransomware groups may be collaborating. Sophos analysts report in their Sophos 2021 Threat Report that they discovered ransomware code that appears to have been “shared across families.” Their report also shares that the average ransom payouts increase significantly from Q4 2019 to Q3 2020, jumping from $84,116.00 to $233,817.30. But the good news for SMBs is that the higher ransom demands are typically limited to larger organizations.
How Does Ransomware Work?

Ransomware works by infecting one or more devices to gain access to a network. The reality is that all ransomware attackers typically need is just one avenue of access to carry out their malicious activities.
There are a few different ways that ransomware works — and part of the differences depend on the type of platforms they’re targeting. For example, Android ransomware, which targets Android mobile devices, operates a bit differently than traditional ransomware that target desktop and laptop devices. Why? Because they do different things a little differently.
Android Ransomware
ESET says that there are two main categories of ransomware for Android devices: lock-screen and crypto-ransomware.
- Lock-Screen Ransomware: This type of malware controls or restricts access to the compromised device
- Crypto Ransomware: This type of malware controls the target’s files through the use of encryption.
The way that Android ransomware works varies from one type of malware to the next. However, Microsoft 365’s Defender Research Team says that, historically, this type of threat would hijack the SYSTEM_ALERT_WINDOW in Android devices. Why? Because it was a notification window that users couldn’t simply dismiss.
To learn more about Android ransomware, be sure to check out our article that goes more in-depth on that particular topic. But keep reading to learn how traditional ransomware infiltrates organizations’ networks.
Common Ransomware Infection Methods
There are many ways that cybercriminals can infect computers and networks with ransomware. Some of the most common methods include:
- Sending phishing emails that contain malicious links or attachments.
- Using social engineering tactics to trick or manipulate users into downloading malicious files or visiting malicious sites.
- Using stolen remote desktop protocol (RDP) credentials, which hackers can purchase at little cost on the dark web. Sophos reports in their 2021 Threat Report that RDP is the leading attack vector for ransomware.
- Infecting removable devices that their targets then plug into network-connected computers and devices.
- Using “malvertisements” on websites their targets visit that auto-download malware onto their devices.
- Exploiting security vulnerabilities of network-connected devices to gain access to the network (and any servers connected to it).
Let’s consider an example. Say, a cybercriminal sends an email to a company’s HR employee that contains malware. The malicious attachment is disguised as a resume, and the email is written in a way so that it looks like it comes from an applicant. The HR employee sees the email and, thinking the attachment is legitimate, downloads it to their device.
The next thing they know, their stomach is in knots as they see a terrifying message take over their screen. The message informs them that they no longer have access to their device or data because it’s now infected with ransomware. The only way that they’re going to regain access is by paying X amount worth of Bitcoin or another cryptocurrency.
Targeting Data Backups
Historically, the recommendations for dealing with ransomware that officials often give companies is to resort to using their data backups to bring their systems back online. This is all well and good if you have a backup in place… but what if you don’t? Or, worse, what if you do but the ransomware attackers have also targeted those backup systems as well? Yeah, that really happens.
Research from the data recovery firm Databarracks also shows that not only are ransomware-wielding cybercriminals directly targeting backups directly, but in some cases, they’re waiting to encrypt files to outlast their targets’ backups as well.
Well, my friend, the reality is if the former happens, you’re up a certain creek without a boat let alone a paddle. Our recommendation would be to have redundant copies of your current backups stored in multiple locations (in both secure cloud and physical storage). Ever heard of the 3-2-1 backup rule? Yeah, that concept definitely applies here.
Ransomware Attacks Are on the Rise — And Even One Attack Costs an Arm & Leg
Unfortunately for the targets of these types of attacks, ransomware is a growing market for cybercriminals. The State of Ransomware in the U.S.: Report and Statistics 2020 from Emsisoft shows that the 113 ransomware attacks that targeted federal, state, and municipal governments and agencies alone cost big bucks. Their estimate? Potentially $915 million but perhaps as much as “multiple billions.”
Why such a broad estimate? Because there’s a lot of missing data and variance that prevents them from giving a more specific estimate.
Ransomware Attacks Don’t Just Encrypt Data
Emsisoft’s state of ransomware article also shows a new trend that’s been gaining traction: attackers exfiltrating data from their targets. This is different from traditional attacks that involve hackers encrypting data but not necessarily moving it. According to their blog post:
“At the beginning of 2020, only the Maze group used this tactic. By the end of the year, at least 17 others had adopted it and were publishing stolen data on so-called leak sites.”
Attackers use this data as extra leverage to extort and ransom payment — pay up or we’ll sell your customers’ data on the dark web and publish all of your confidential emails!
The Effects of Ransomware Reach Beyond the Initial Target
Ransomware is bad news, and not only for the businesses they target. It can also be a nightmare for other businesses that are linked to them. For example, in May 2020, a cloud software solutions company known as Blackbaud was the victim of a ransomware attack. Fortunately, Blackbaud reports that they were able to detect and ultimately halt the attack. However, they weren’t able to prevent the attackers from stealing data first.
The impact of that attack could be felt by businesses, non-profits, healthcare organizations and educational institutions the world over. According to data from Emsisoft, more than 170 organizations were affected and records of more than 2.5 million people were exposed in the ransomware attack.
Should You Pay the Ransom? Not Unless You Want to Face Penalties
This is a question that has a lot of varying answers depending on the source. For example, Forrester research shows that paying a ransom can be a “valid recovery option based on business need and circumstances.” But this is a business decision that involves a lot of different considerations.
Historically, ransom demands are less than the costs affected organizations pay in terms of recovery costs and losses. For example, in the Atlanta attack, the demanded payment was approximately $50,000 in Bitcoin (although there’s not a more specific number since the cryptocurrency’s value is so volatile), whereas the attack overall was thought to cost $17 million.
However, the FBI doesn’t advocate paying ransom demands in ransomware attacks. Their reasoning is twofold:
“Paying the ransom doesn’t guarantee you or your organization will get any data back. It also encourages perpetrators to target more victims and offers an incentive for others to get involved in this type of illegal activity.”
However, there’s an even more pressing reason to think twice before paying in a ransomware attack. In October, the U.S. Treasury’s Office of Foreign Assets Control (OFAC) released an advisory warning that companies that make or facilitate ransom payments to sanctioned hackers may face punishment. According to Reuters, this is true regardless of whether the facilitators or ransomware victims are aware that the hackers demanding payment are subject to U.S. sanctions.
How to Protect Yourself & Your Organization from Ransomware
So, what can you do to protect yourself from the threat of ransomware? The U.S. Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) shares a few suggestions with their CISA Insights tip sheet:
- Back up all of your data and configurations. Be sure to use offline backups in addition to cloud backups.
- Keep your systems and security solutions patched and up to date — always.
- Maintain a current incident response plan and practice it!
- Keep an eye on the industry to learn from other ransomware events.
Their CISA Insights sheet also has information about what actions to take if you find yourself facing a ransomware attack.
TL;DR on Ransomware
If you’re looking for a quick-hits summary that answers your questions of “what is ransomware?” and “how does ransomware work?” then look no further.
- Ransomware is malicious software that infects devices to block access and encrypt data.
- It’s a type of cyber attack that aims to force a target to pay extortion in exchange for access to their device(s) and/or data.
- Ransomware for desktop computers often varies from those targeting Android devices in terms of how they work.
- Remote desktop protocol (RDP) is the leading attack vector for ransomware attacks.
- A growing trend in ransomware attacks is data exfiltration instead of “just” data encryption.
- Some cybercriminals are now targeting data backups directly as part of their ransomware campaigns. This is why it’s important to keep current offline data backups in addition to cloud backups.
- Some ransomware victims choose to pay the ransoms, but their payments don’t guarantee access to the affected systems and/or data. However, the FBI doesn’t recommend ponying up in general because there’s no guarantee the cybercriminals will honor their agreements or won’t be encouraged to attack again because you paid the first time.
- Organizations that choose to pay ransoms — or facilitate those payments — may face punishment from OFAC.













 (23 votes, average: 4.78 out of 5)
(23 votes, average: 4.78 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security