What is Malvertising? Explore 6 Real-Life Examples & Protection Tips
Explore how to recognize a malvertisement and protect yourself from getting hacked
Malvertising = malicious advertising. Basically, it’s a way for cybercriminals to spread malware (malicious software) through ad displays on websites and apps. Malware means any codes, scripts, commands, and software that are made to carry out a cybercrime or another malicious activity. And when malware is hidden in an advertisement, it becomes a malvertisement.
In this article, we’ll discuss what malvertising is, how it works, and what you can do to protect yourself from them.
What Makes Malvertising a Cyberthreat?
Malvertising refers to malicious advertisements that look real. These ads spread malware through legitimate websites. What makes malvertising particularly tricky is that users might not be able to differentiate between real ads and fake ones. After all, if an ad is displayed on a website that users trust, why would they question whether it’s real?
If malware gets inside your device, it can:
- Gain unauthorized access to your device,
- Crash your system,
- Monitor your actions and capture sensitive information (such as passwords),
- Encrypt and steal your data via a ransomware attack,
- Use your device as part of larger botnet attacks against others, and
- Engage in other harmful activities.
Scammers officially rent ad space on the reputed websites, insert the malicious codes in the advertisements, and publish them. The ads look genuine, tempting, and coming from a trusted source. The host website owner may or may not be aware that their website is displaying malvertising.
So, if you see an ad on a reputable website that promises “25% off iPhones for Amazon Prime users,” it might be a malvertisement. If you click on such an ad, you won’t be redirected to the official Amazon website. Instead, it may take you to a malicious website or download malware onto your device. Either way, this is bad news for you.
These are some of the popular websites that have been the victims of malvertising in the past:
- Yahoo.com,
- Spotify,
- London Stock Exchange,
- MySpace,
- The New York Times,
- Hindustan Times
6 Types of Malvertising
Malvertisements come in all shapes and sizes. Hackers can even make invisible malvertisements using iframes (which we’ll discuss shortly)!
1. Content/Text-Based Malvertisements
Attackers insert malicious codes in simple text-based advertisements on host websites, typically in the sidebars or in the main content body. Hackers might also embed malvertising as part of sponsored article content.
2. Banners
Attackers make advertisement banners in a way that they lure the website visitors into clicking on them. Banner ads often display:
- Fake deals and coupon codes,
- Fake virus infection-related messages to incite panic, or
- Some other sort of tempting messages to indulge people in clicking on the banners.
Attackers can also impersonate reputable companies and organizations, using their logos and product pictures to gain people’s trust.
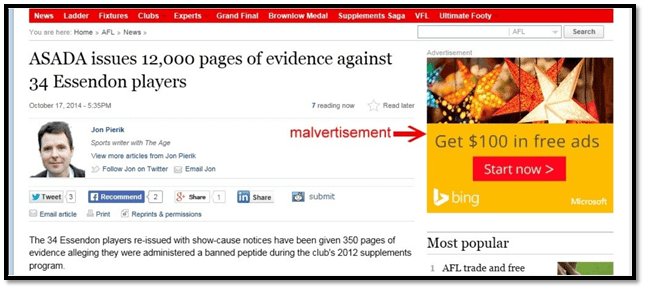
For example, look at the banner below. It looked like a genuine Bing ad offering a free advertisement credit. But it could be a malvertisement, and when you click on it, you might be redirected to a spammy site, or malware gets downloaded on your system.
3. Video Ads
Attackers make catchy video ads to grab users’ attention. These malware-laden videos look like legit product/services ads, or they might even have clips of video games, popular sports, celebrity interviews, breaking news, etc.
4. Animated Ads
Attackers misuse Java scripts or flash player while making animated/motion ads and insert malicious codes in them.
5. Inline Frames (iFrames)
An iframe is one of the HTML features that developers use to showcase one platform’s content to another. But attackers exploit the iframe mechanism by keeping its dimensions set to 0 x 0 pixels. That means the website visitors can’t see any content, but the host website still carries it. Malware automatically downloads after website visitors spend a couple of seconds on the website or accidentally click on the iframe-inserted part.
6. Popup Ads
Popups are the small windows that suddenly open up when you are browsing a webpage. Attackers use popups for malvertising. Fake virus infection and free virus removal tools’ popups are quite popular. Sometimes attackers show popups for a survey, polls, coupon codes, lightning deals for a limited period of time, free products, free subscriptions, etc.
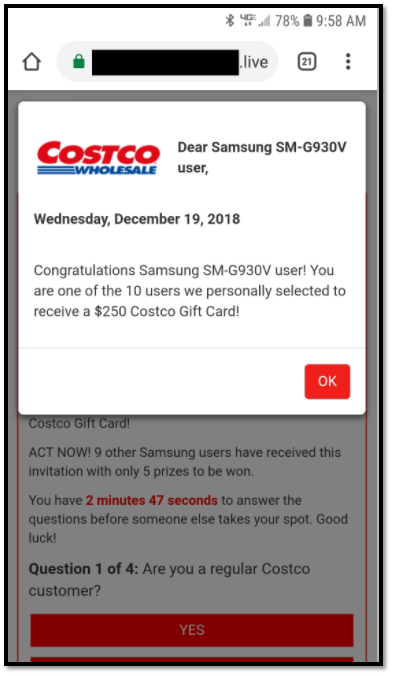
Check out the example below. The popup makes you think that you think you are lucky to win a Costco gift card, but it can just be a malvertisement.
How Attackers Publish Malvertisements On Legit Websites?
You might be thinking, why would any reputable platform allow scammers to publish compromised advertisements on their site? After all, this could ruin their reputation! The thing is, there are many layers and complexity involved in online advertising — lots of sites, networks, and servers. Let’s explore how attackers get their malicious ads on legitimate websites.
1. Use Third-Party Ad Distributors to Extend Their Reach
Scammers use third-party ad distributors such as Google Ads (AdWords), AdPlugg, Propeller Ads, etc. to display their ads on legitimate sites. These third-party advertising platforms have huge networks of companies that want to publish advertisements and website owners (publishers) that want to earn income from displaying ads. VentureBeat reports that Google delivers 30 billion ads every day, and no one is going to scrutinize each code in those ads.
Just like any other advertiser, the perpetrator also makes a free account on such sites, creates some malware-loaded advertisements, bids for the keywords, and specifies the daily budget and the target audience. The ad distributors display the ads as per web visitors’ browsing behavior on their large pool of network websites (including highly reputed ones). This is how the attackers manage to post their ads on the reputed sites.
In some cases, cybercriminals will steal legitimate advertisements from big name companies. But instead of linking back to those legitimate organizations, they’ll instead link to their malicious websites.
2. Rent Space Directly to Display Malvertising
Some website owners (social media platforms, popular blogs, video streaming platforms, etc.) offer spaces on their websites directly to advertisers as rentals. They may opt to do this instead of being part of third-party ad distributor networks to generate extra income.
Advertisers display many of the following on rented spaces:
- Ad banners,
- Videos,
- In-line text ads, or
- Even sponsored articles.
Some discussion forums like Quora and Reddit allow advertisements to post in Q&A format. They charge fees as per the impression counts, the number of clicks, percentage of the sale, or as per the time slot like weekly, bi-weekly, or monthly.
Attackers generally put benign ads in the initial phase, and after gaining the trust of the host platform, they start adding malware in the ads.
3. Take Advantage of Vulnerabilities on Host Platforms
Some hackers exploit websites with weak security postures by manipulating them to display their malvertisements. In this method, the affected website owners have no clue that their websites are showing such ads, and they don’t receive any money for such ads.
Examples of How Malvertising Works
You might be wondering, what exactly is going to happen if you click on a malvertisement? Let’s explore how attackers can defraud you with malvertising examples and hypothetical examples.
Hackers Use Malvertising as a Malware Delivery System
The common types of malware that can be spread through malvertisements include viruses, worms, trojans, and root-kits. The infected advertisements insert these malicious codes or software onto website visitors’ devices to execute various cyber-attacks against them.
Example 1: Malvertising Causes Users to Unknowingly Download Computer Viruses
Bob wants to buy a new cell phone and is browsing online for a good online deal. He sees an ad stating, “40% discount on any Samsung phone!” on a deal-sharing website. He gets excited and clicks on the ad, which takes him to a genuine-looking ecommerce site. When the page loads, it displays a message saying, “Sorry, we are out of stock.”
Disappointed, Bob closes the tab and continues searching for a good mobile discount. But what Bob doesn’t know is that he isn’t returning entirely empty-handed. When he clicked on the advertisement, he inadvertently downloaded a dangerous virus on his device. This nasty little number soon crashes his entire system and steals all of his personal data!
Example 2: Hackers Trick Users into Downloading Trojans via Malvertising
Alice is scrolling her social media profile when she sees an ad with clips of an interesting computer game. Since she’s bored, she clicks on the ad to play it. She sees an error message stating that the game will run only on the latest Flash Media Player. The message also includes a link to install the latest Flash player. So, Alice clicks on the given link and follows all the steps to install it on her PC.
What Alice doesn’t know is that it was a trojan impersonating the media player. A trojan is a type of malicious software that cybercriminals disguise to look like a legitimate computer program, application, or file to trick the users into downloading it. Unknowingly, she has just installed and activated a trojan malware that can steal all her data, lock the files, and hijack the entire system.
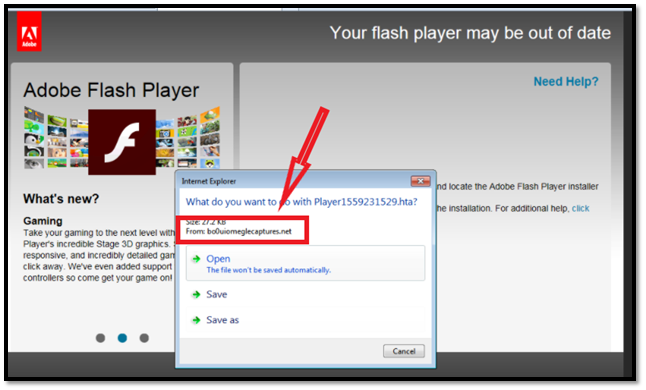
See how a trojan looks like in real life in the below screenshot. You think you are downloading a Flash player, but when you check the developer/publisher’s name, you can see that it’s not coming from Adobe but some scam artist.
Malvertising Leads Users to Phishing Sites
In the phishing attacks, the attacker impersonates a legit entity or the person to defraud the users. Phishing can be done via emails, phone calls, SMS, Wi-Fi routers, websites, etc. Malvertisements redirect the users to phishing websites that look like replicas of well-known, legitimate sites. These phishing websites can make users download and install malicious applications or steal users’ personal/financial information.
Example of How Malvertisements Make Users Victims of Phishing Attacks
John was reading an interesting article online when he sees an advertisement mentioning that Macy’s has introduced a new store-credit card which will give a 20% discount on all the shopping done from their outlets. John is Macy’s regular customer, so he obviously wants to take advantage of this deal. He clicks on the ad, lands on what he believes to be the Macy’s website, and fills out a form to replace his current store credit card.
After submitting the form, John also receives the message that Macy’s will send his new card soon to his residence. What John doesn’t know is that website he filled out the form was a phishing website that looked exactly like Macy’s original site. And instead of Macy’s, the hackers have received all the information he has filled out (name, email address, phone number, physical address, existing credit card details), and they will make him a victim of identity theft or financial fraud pretty soon!
Mavertisements Spread “Drive-by” Malware
Some types of malvertisements automatically download the malware onto website visitors’ devices, even if they haven’t click on anything or press the download button. This type of malware is known as drive-by malware because it doesn’t require any actions from the users and auto downloads. Drive-by malware can spread in many ways, and malvertising is one of them.
It is quite difficult to insert the drive-by malware into a clean and reputed site. So, the attackers rent advertisement space and insert the drive-by malware in the ads.
Example of How Malvertisements Deliver Drive-by Malware
Todd runs a successful traveling blog, which attracts more than a million website visitors every year. Todd was shocked to receive an angry email stating, “STOP SPREADING VIRUSES!” But it didn’t stop with one email. Within 24 hours, he received more than 30 such furious emails complaining about “suspicious software downloads” when people visited his website.
He anxiously thought, “How come I spread malware when I don’t know a single line of coding or anything about hacking? I just write my blog content on a simple WordPress platform.”
What Todd doesn’t know is that the person who is paying him a $100 a month to publish a hotel’s advertisement on his blog is a hacker and the real culprit behind all this mess. He has inserted the drive-by malware in the blog via advertisements. Whenever a website visitor visits Todd’s blog, they inadvertently download the drive-by malware in their devices.
The people who are complaining are the lucky ones whose security software could alert them about such malware insertion. But the rest of the unfortunate website visitors are not even aware of such download and have become victims of the drive-by malware attack.
Hackers Use Malvertising to Distribute Exploit Kits
An exploit kit is an instrument to exploit the vulnerabilities of a software or application. Software vulnerability means errors or bugs in the software, which hackers can use as loopholes to insert malware into victims’ systems. Exploit kits contain special codes that can scan the connected host’s systems, find the vulnerabilities, and deliver the payload as per the vulnerability type. Sometimes attackers use malvertisements to distribute exploit kits.
Example of How Malware Trick Victims into Downloading Exploit Kits
Eva was watching a video online when an ad caught her attention, stating, “Is your device is getting slow? It might be due to virus infection! Scan your device for FREE today!” Eva immediately clicked on that ad because she was frustrated with her painstakingly slow laptop. As the ad promised, the free antivirus program started to scan her laptop right away without charging a single penny!
What Eva doesn’t know is that the security software is an exploit kit that is also scanning all the applications she has installed and finding vulnerabilities in them. After finding various vulnerabilities, the exploit kit inserts malware into some of her applications, browsers, and software!
7 Malvertising Protection Tips
By now, you likely have a better idea of what malvertising is and how dangerous it can be. Now, let’s explore some basic ways to protect your device from malvertisements.
Malvertising Protection Tips for Website Visitors
1. Use cybersecurity software to help identify threats: Antivirus, antimalware, and anti-spyware software are going to be the first line of defense against malvertising. Some programs are signature-based, while others are behavior-based. If anything downloads to your device, these programs will alert you. Plus, they will scan all the downloads and installations and remove the malware loaded stuff from your device.
2. Manually check your systems to identify suspicious programs and files: Manually check your download folder, C:/Program File, C:/Program Files (x86), and C:/Windows/Temp folders for any unknown or suspicious programs, files, and software. If you find an application that you didn’t download, you should do some research about it and its manufacturer/developer online. This way, you cano ensure the program is legitimate.
3. Put ad-blocking software to use: There are some adblocking software and browser extensions available in the market that successfully block the ads. They block all types of advertisements, whether they are harmless or malicious.
4. Keep your system patched with updated software: Keep all your software components, applications, browsers, and operating system patched and updated to the latest version. The old versions generally have security bugs that attackers can exploit to insert malware into your devices and IT systems.
5. Be vigilant while surfing online: If you are redirected to a website, carefully inspect the URL, and make sure you have arrived on the company’s official website. If you’re unsure whether the company’s web address is real or find product prices, discounts, or other information suspicious or “too good to be true,” conduct a separate Google search about it.
You can also click on the padlock sign in the address bar to check the website and organization’s information in its SSL/TLS certificate. Of course, if the site isn’t using one of these certificates, that should already be a red flag.
6. Use official resources and websites (avoid downloading from third-party sites): Be sure to only download browser extensions, media players, or updated versions of any applications from their official websites. For example, if the game you’re trying to play online shows the message that it will run only on the latest version of Chrome, download the latest version of your browser only from google.com/chrome.
If you see a popup showing that your system is suffering from virus infection, instead of clicking on that ad, scan your device with your trusted antivirus or anti-malware software only.
Malvertising Protecetion Tips for Website Owners
7. Use website scanners: Use legitimate website scanners that continuously monitor, scan, detect, and remove the malicious codes on your website. So, if someone has inserted malware-laden advertisements, these types of scanners can quickly detect it before it’s too late.
Another good idea is to use a website vulnerability scanner tool such as HackerProof Trust Mark. It’s a site seal that also runs daily vulnerability scans of your site and provides recommendations for remediation. So, in addition to offering visual assurances of security to your customers and users, it also gives you actionable intelligence for how to improve the security of your site.
8. Restrict ad file types: Restrict ads to allow only specific files types to display. Also be sure to disallow the use of any code, including Javascript.
9. Install the updates as soon as they are available: Keep all plugins, themes, and applications updated to their latest versions so that no one can break into your website and insert the malvertisements.
The Difference Between Malvertising and Adware
People use the terms “malvertising” and “adware” interchangeably, but both words have different meanings. Malvertising refers to ads that deliver malware, whereas adware is malware that pushes ads that are often harmless (albeit annoying). Basically, adware is an advertisement-generating software that keeps showing you unwanted advertisements that link to spammy websites. It is important to note, however, that these ads can sometimes be dangerous in that they may link to malicious websites.
Did you know that publishing software that bundles adware with it can actually legal in some cases (though not all)? This allows organizations to track users’ geographical locations and display ads accordingly based on that data. This is a way to generate pay-per-click (PPC) or pay-per-view (PPV) revenue for software developers. However, adware becomes illegal when it crosses certain lines, such as:
- Displaying popup ads in windows you can’t close or exit,
- Delivering malware,
- Tracking your actions or behaviors, and
- Stealing data such as users’ personal information or login credentials.
Of course, if you’re not sure whether any adware you wish to use is legal or illegal, it’s best to consult a legal professional who specializes in these matters. (We don’t offer legal advice here.)
While users encounter malvertisments only while visiting affected websites, adware is stored inside the user’s browser or the device itself. Hence, adware shows you unsolicited advertisements on your device’s home screen, even if you aren’t visiting any website.
It becomes difficult for anti-malware software to spot malvertisements because they are on legit sites. But security software can easily detect and remove adware, which is sometimes detected under the name of the potentially unwanted program (PUP).
In short, malvertisements are way more dangerous and harmful than adware.
Wrapping Up on Malvertising
In general, we tell people to avoid malicious websites and not download anything that looks fishy. But in malvertising, the host websites are trustworthy, and the ad content frequently appears harmless. Hence why even the vigilant people become prey to such attacks. That’s why robust security software is the best way to alert you when you are downloading any infected material from online.
Updating all of your software components and using ad-blocking software can also be quite helpful. If you receive any malware-related complaints from your website visitors, take their concerns seriously, and scan all of your ads. If you’re using third-party ad platforms, contact them immediately to report the issue.














 (11 votes, average: 4.64 out of 5)
(11 votes, average: 4.64 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security