Hacker Motivation: Why Do Hackers Hack?
Bromium reports that high-end cybercriminals make $166,000+ per year and the middle-income range for hackers is $75,000 a year! But is money the only hacker motivation? Let’s find out!
Hacking is a highly risky game. Most countries have robust security laws and cybersecurity departments working hand-in-hand with local law enforcement officials to catch cybercriminals. To be a successful hacker, apart from having expertise in technology, people also need to know how to monetize their hacking skills without getting caught. You also need to have a strong hacker motivation.
But why would a talented person with vast knowledge in information technology and financial channels choose to take the risk of hacking? What are their hacker motivations? Let’s explore seven hacker motivation factors in this article to understand why do hackers do what they do.
Motivation of Hackers: Why Do Hackers Do What They Do?
Hacker Motivation 1: Achieving Financial Gains

Now this one is a pretty obvious hacker motivation. Money is a huge motivation for many types of criminals — and cybercriminals are no different. In fact, Verizon’s 2020 Data Breach Investigations Report (DBIR) shares that 86% of the data breaches they analyzed were financially motivated.
When hackers profit financially at the cost of others by doing illegal activities, they typically fall within the black hat hacker camp. But hackers can earn money legally, too. They are called white hat hackers, or ethical hackers. (We’ll talk about them towards the end of this article.)
These are several common methods by which hackers (black hat hackers, especially) get financial gains.
Misusing Data
Hackers steal victims’ financial or personally identifiable information (PII) through a variety of different tactics, including using malware, phishing attacks, and brute-force attacks. They can then use the data to carry out financial fraud by making fraudulent purchases or transferring money to their (hackers’) bank account.
Hackers might also execute the following identity theft-related crimes using your PII:
- Apply for a loan in your name.
- Make fake passport/immigration documents.
- Open a bank account or apply for a credit card in your name and use the overdraft/credit limit.
- Send phishing emails, SMS phishing messages, and voice call impersonating you.
- Create a fake social media account in your name (which they can use to scam other targets).
- File for state/federal benefit schemes like unemployment benefits impersonating you.
Selling Data on the Dark Web
Some hackers sell the data they steal on the dark web. Basically, this is an underground marketplace where hackers and other cybercriminals can engage in legal and illegal activities. Other hackers buy personal and sensitive data to execute financial fraud and other PII-related crimes. Even unscrupulous online advertisers and marketers are interested in such data. They can use it to craft targeted advertising or send spam emails.
Either way, it’s a lose-lose situation if your information becomes compromised as a result of this hacker motivation.
Blackmailing Victims
Blackmail is a very powerful tool in any cybercriminal’s arsenal, including hackers. For example, hackers can steal confidential data or intercept personal media files (images, videos, etc.) and demand money to not release the information publicly. They also can encrypt important data or lock users out of their own devices, then demand the ransom in exchange for access.
Hackers use special types of malware such as ransomware and spyware to steal data and lock compromised devices. Sometimes, hackers breach companies or government agencies’ databases to gain access to their data. They then demand extortion money for not revealing their trade secrets or other sensitive information in the public domain.
Selling Malware
Some hackers are programmers who write the code for various types of malware, including worms, trojans, viruses, scareware, and rootkits, etc. They can either use these malware programs or sell them to other cybercriminals.
Using Psychological Manipulation and Social Engineering
Phishing is one of the most commonly used tactics by cybercriminals. Hackers send phishing messages to victims impersonating any person or company they (victims) trust. They psychologically manipulate victims into sending them money by:
- Claiming to be experiencing a fake emergency and needing their help.
- Blaming the victims for breaking a law and demanding they pay a penalty.
- Asking for a donation while impersonating a legitimate charity or non-profit organization.
- Fraudulently claiming the victim’s computer has a virus infection and offering phony malware removal service (which may result in the target’s computer getting infected or otherwise compromised).
- Tricking or manipulating them into buying fake software/products/educational materials.
These are just some techniques hackers use to make money. As you can see, their methods involve lying, manipulating, threatening, and blackmailing victims and other targets.
Hacker Motivation 2: Carrying Out Political Agendas

Some countries’ governments hire hackers for political espionage. In these cases, the hackers who engage in state-sponsored cyber attacks become known as nation-state actors. In this type of role, hackers are assigned duties such as:
- Stealing sensitive, confidential, or classified data (research, trade secrets, or even personal information on specific targets).
- Manipulating or otherwise interfering with elections.
- Stealing or leaking government or military documents.
- Interfering with the economy.
- Interfering or affecting relationships or treaties with other nations.
The hiring governments often release the compromised or breached data to the public to cause political unrest in the enemy country. Hackers also hack or deploy cyber attacks like DDoS attacks on the rival county’s government websites and servers to cause functional or operational disruptions. These types of attacks are also known as state-sponsored cyber attacks. Countries like Iran, China, North Korea, and Russia are notorious for using these types of tactics.
Hacker Motivation 3: Performing Corporate Espionage
Some companies hire hackers for stealing confidential information from rival firms. In these situations, hackers are assigned to find leaky or vulnerable databases or launch attacks on the target organization’s servers or websites. They can attack in multiple ways, including using brute force attacks, SQL injections, cross-site scripting, and DDoS attacks.
But just what types of information are the hackers looking for? The target data can be virtually anything but often falls within the following categories:
- Trade secrets,
- Key customers, suppliers, vendors,
- Pricing information,
- Data regarding future financial and marking planning,
- Technical schematics or sensitive product information.
Some companies hire hackers to slow down or crash a competitor’s website by deploying DDoS attacks. This type of attack essentially overwhelms the organization’s web servers, making them unavailable for the customers. They may also choose to leak confidential customer data to ruin the rival’s reputation.
Hacker Motivation 4: Proving a Point (Hacktivist)
Some hackers don’t care about money. Instead, they hack to prove their social, ethical, religious, or political views or to force their views upon others.
For example 1: To show their protest and anger against the death of Iran’s late major general Qassim Soleimani, Iranian hackers attacked the U.S. Federal Depository Library Program’s website in January 2020 to display an image of President Donald Trump over a map of the Middle East.
Example 2: In July 2015, a hacktivist group calling themselves the “Impact Team” hacked the online cheating website Ashley Madison. The result? The personal data of 32 million members was published publicly. They released the members’ data to teach the members a lesson and make the owner shut down the site.
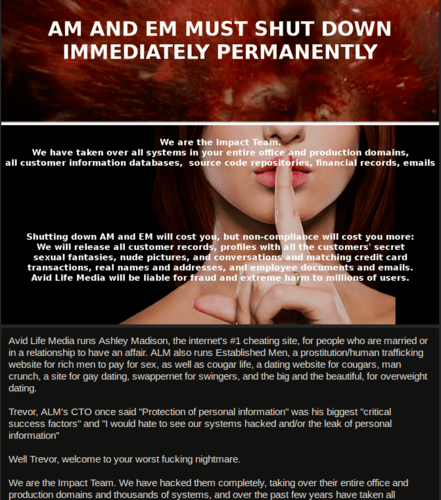
Hacker Motivation 5: Taking Personal Revenge
Some hackers use their hacking skills to take personal revenge on a person or company for a real or perceived injustice. The hackers harass their nemesis in many ways, such as by:
- Locking their targets’ devices.
- Encrypting or deleting their data.
- Publishing the confidential data/personal media files to the public (called doxxing).
- Sending them numerous spam and phishing emails.
- Hacking their social media profiles and posting false or inappropriate content.
- Hacking their email accounts and sending phishing emails to their contacts.
Hacker Motivation 6: Causing Harm for Personal Enjoyment
Some black hat hackers hack just to create chaos or to cause harm or panic. They relish ruining the reputation of a person or company, interrupting governments’ activities, or destroying important data. They might be addicted to hacking and feel a sense of achievement when they hack a system or defraud someone.
Hacker Motivation 7: Mitigating Cyber Threats
This is the last hacker motivation that we’re going to talk about in this article. Hackers sometimes hack to attack or stop other hackers from doing bad things. These types of hackers typically either fall in the white hat or red hat categories.
White hat hackers, or ethical hackers, hack to protect websites, servers, and databases from black hat hackers who want to cause harm. White hat hackers employ the same hacking techniques as black hat hackers, but they do it with the system owner’s permission and stick to legal methods. Companies and government agencies hire them as information security analysts, cybersecurity researchers, security specialists, penetration testers, etc. They work as independent consultants or freelancers as well.
White hat hackers’ intentions are typically to:
- Find and fix vulnerabilities in the system before black hat hackers exploit them.
- Develop security software that detects and removes malware.
- Educate users about various cyber threats and ways to prevent them.
- Make contingency plans in the event of a cyber attack.
- Strengthen the overall security posture of the software and hardware components.
But there is also a different type of hacker that also likes to target the bad guys: red hat hackers. Red hats are like black hats in that they don’t typically stick to legal routes with their attacks and will hack without authorization. However, instead of targeting businesses and other legitimate users, they’ll instead attack other hackers.
Other Hacker Motivations
Of course, there are also other types of hacker motivations that we haven’t yet talked about. Two of the most basic ones are human curiosity and a desire to learn. There are some hackers who are new or inexperienced who just want to expand their knowledge and skills and “flex their muscles” as the phrase goes.
Of course, there are also hackers who do what they do because they want to achieve notoriety and make a name for themselves. But regardless of their reason for hacking, there’s a lot we can learn from hackers and their motivations.
Final Words on Hacker Motivation
As you read above, not all hackers have evil motivations. Security professionals that work to protect our data and systems are also called hackers, but these are the white hat hackers with good intentions. Now that you know the motivation of hackers, you should check also check out the six different types of hackers to see how they differ. Also, check out this black hat hacker vs white-hat hacker article to know which type of activities both the hackers are involved in.














 (19 votes, average: 4.47 out of 5)
(19 votes, average: 4.47 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security