What Is a Trojan Horse in Computer Terms?
Explore what trojan horses are — their invasion techniques, the most common types, the damage they cause, and how can you protect your device & organization from trojan attacks
Ever found yourself wondering “what is a trojan horse?” or “what does ‘trojan horse’ mean when it comes to computers?” That’s probably because there seems to be a lot of confusion in terms of classifying trojans as malware or a type of virus and people often lump viruses, trojans, and other types of malware together in articles.
But don’t worry. We’re here to pull back to the cloak of uncertainty and reveal everything you need to know about trojan malware, trojan bug, and trojan horse attacks. This includes going over:
- What a trojan horse is in computer terms (and where the name came from),
- Why bad guys like to use trojans,
- The 10 common types of trojans,
- What to look for to identify whether your device may be infected, and
- How to prevent trojans from infecting your computer.
What Is a Trojan?
The term “trojan horse” (or just “trojan” for short) refers to malicious software (malware) that’s disguised to look like a legitimate computer program, application, or file. The National Institute of Standards and Technology (NIST) defines it as:
“A computer program that appears to have a useful function, but also has a hidden and potentially malicious function that evades security mechanisms, sometimes by exploiting legitimate authorizations of a system entity that invokes the program.”
Basically, a trojan author (hacker) creates software with a misleading name or corrupts a legitimate program with malicious trojan malware. The trojan malware can be hidden in the files, folders, images, videos, slideshows, etc., too.
Using this ruse, cybercriminals trick innocent users into downloading their corrupt software to infect their devices with malware.
Trojans, Worms, and Viruses: What’s the Difference?
Well, let’s first start by saying that these are all separate (but related) threats. These three types of malicious codes use different routes to reach their destructive goals.
Unlike a computer worm, which self-propagates, a traditional trojan typically needs a user’s manual action to get into (and activated on) a host computer. The trojan stays dormant in the compromised program until a user clicks, downloads, or installs it.
Unlike a virus, traditional trojans can’t replicate themselves. They stay local in the same corrupted program in which its author has stored it. That means it can’t corrupt the other software and programs.
However, modern trojans are frequently combined with viruses or worms. These hybrid trojans replicate themselves and transfer their payloads to all other connected IoT devices, software, USB drives, and browsers.
The Origins of “Trojan Horse” in IT Security![]()

The term trojan horse relates to the Greek myth of a massive wooden horse that the Greeks used in the Trojan War.
To summarize: In the Trojan war, the Greeks made a huge wooden horse, hid soldiers in it, and pretended that they left the city of Troy. The people of Troy, Trojans, brought the wooden horse inside the Troy as the symbol of their victory. But in the night, Greek soldiers came out of the wooden horse, opened Troy’s gates to let the remaining Greek army enter and defeat the city.
The computing world’s trojan horse got this name because of the malware’s similarly deceptive nature. The user willingly downloads a program thinking it is a harmless, useful program without having a clue that it is loaded with malicious code.
Why Attackers Use Trojans
Trojan horses damage infected devices in many of the same ways as other types of malware. They’re also instrumental in helping cybercriminals:
- Steal and encrypt the data for ransomware attacks.
- Steal login information such as user IDs, email addresses, passwords, security questions, PINs, etc.
- Access email clients to send phishing emails in your name.
- Steal financial information such as payment card numbers or bank account number for doing financial fraud.
- Get access to the web browsers to execute man-in-the-browser attacks.
- Steal your personally identifiable information (PII) for identity theft.
- Execute man-in-the-middle attacks.
- Commit espionage and steal other types of confidential, sensitive, or classified information (such as political data, proprietary research, trade secrets, and military-related data).
Server-side attacks: Although most trojans target end user devices instead of servers (websites) or networks, the threats they pose don’t end there. Many major types of cyber attacks against websites and servers — such as DDoS attacks, brute force attacks, man-in-the-middle attacks, etc. — take place when trojans comprise user devices to make a botnet army.
Trojan Horse Invasion Techniques
Let’s explore how the attackers manage to install the trojan horse on a device.
Compromised Software and Apps
Hackers infect a legitimate executable (.exe) with trojan malware or develop new corrupted software with a deceptive name. For example:
- Skyp3.exe (instead of Skype.exe),
- $recyble.bin, (instead of Recycle bin)
- Instagrarm, (Instead of Instagram)
- TikTok-online, (Instead of Tik-Tok)
- Nort0n antivirus (Instead of Norton Antivirus)
As you can see, these names are written in a way that causes less vigilant users to think they’re legitimate software, apps, or files and download them. To lure unsuspecting users into downloading their infected items, hackers often make them available to download for free. When users install the malicious items, the trojans can then take control of their devices.
Phishing Emails
Hackers distribute different types of malware via phishing email links and attachments. Phishing emails look like coming from legitimate sources like your bank, an ecommerce company, friends, relatives, the professional circle, or any legit company, but they’re not.
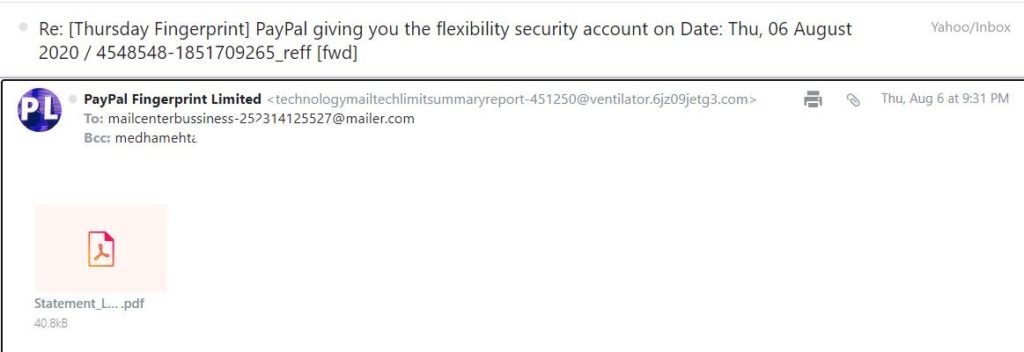
For example, you might think the below email is from PayPal and that the attachment is a benign pdf receipt. However, if you were to download it, the trojan would infiltrate your system.
Pop-Up Messages and Ads
When users visit an infected or spammy website, they get a variety of pop-ups of lucrative advertisements, fake virus infection threats, tempting gossip articles, shocking news, etc. When users click on such pop-ups, the trojan gets installed in their device.
Fake Updates
When users try to access any video or file online, the website denies their access and asks them to download the latest version of a media player, browser, or other types of software with a given link. However, when they install the program from the link provided in the message, a trojan malware-loaded version of the software gets downloaded in the users’ device.
The 10 Common Types of Trojan Horses
The trojan author develops the payload to exploit the host device in a specific manner. Trojans are typically categorized by their functions. Although all trojans are developed differently, these are some common types of trojan malware that we’ve seen in the past on the internet.
1. Botnet Trojans
These trojans are designed to spread their payloads to other connected devices and make them join a bot network. The trojans’ authors are called botmasters, and they control all of the infected devices via C&C servers. Once a large number of infected devices join the same botnet, the botmaster uses them to execute various cyber attacks (DDoS attacks, brute force attacks, etc.).
2. Deceptive Antivirus Trojans
Such trojans send pop ups to users, informing them that their devices are infected with malware. Once the users are convinced that their devices are infected, the attackers sell them fake malware-loaded antivirus software or charge for virus removal services. Check out the following example:
3. Email Corrupting Trojans
These trojans are made to access the hosts’ email clients. They can:
- Intercept email communications,
- Send the victims’ contact lists to the attackers,
- Send phishing emails on behalf of the victims (without the victims’ knowledge) and erase the emails from their sent folders.
4. Backdoor/Remote Access Trojans
These trojans give remote access of the infected devices to cybercriminals. With this comprehensive access, trojan authors can:
- Access, modify and transfer files,
- Send and receive information with other connected IoT devices,
- Reboot the system,
- Install or uninstall software, and
- Get many other such privileges.
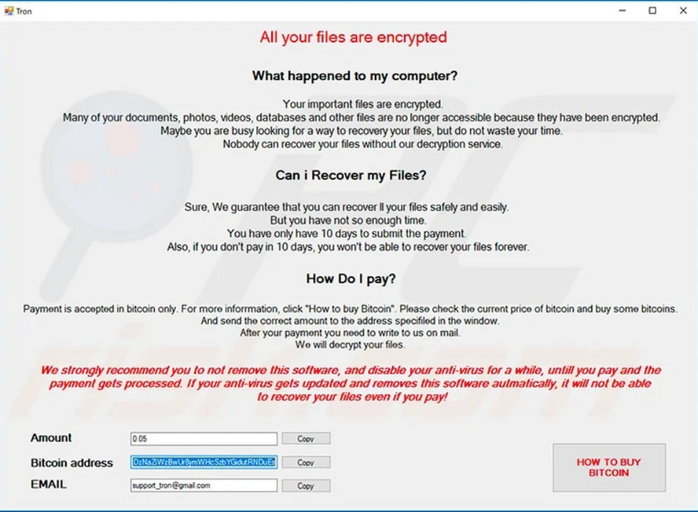
5. Ransomware Trojans
These types of trojans have the ability to encrypt, lock, and delete data. They can lock important programs or even the entire operating system, too. The trojan writers demand extortion money from the victims in exchange for returning access to the data, files, programs, or the entire system. (Although, as you can imagine, even if some victims pay, the bad guys still might not follow through with their promise.) Sometimes, the attackers also threaten to leak the victims’ private data or expose the confidential information if they don’t pay the ransom.
Check out the example below:
6. Vulnerability Finding Trojans
After making their way onto targets’ devices, these trojans seek out the vulnerabilities of the operating systems, apps, and software that are installed on them. The trojans then send the lists of vulnerabilities to the trojan operators. Generally, such vulnerabilities are found in outdated versions of programs. This information helps hackers to make further plans of exploiting the devices (and other devices with the same vulnerabilities) based on the nature of their unpatched bugs.
7. Download Enabler Trojans
Whenever the victim’s device connects to the internet, these types of trojans download the other type of malware in users’ devices without their consent.
8. Spyware Trojans
Spyware trojans (also known as spyware) are covert software that attackers can use to monitor the target users’ actions and behaviors. This includes everything from what the users type on their infected devices to the information they transmit via websites (such as personal information, financial data, login credentials, etc.). The spyware users can then use the information to execute identity theft crimes, financial fraud, or ransomware attacks.
9. File Transfer Protocol Trojans
With these types of trojans, attackers use trojans to open port 21 in the host device to access the files via the file transfer protocol (FTP). Once the attackers get access to the FTP folders, they can upload and download malicious files in the victims’ devices remotely.
10. Security Software Disabler Trojans
These trojans turn off, disable, or uninstall computer security software such as antivirus, antimalware, or firewalls without the users’ knowledge. So, before the antivirus programs can detect the trojan and its payloads, the attackers turn such security software off. The users think that their devices are still protected by the security software and they trust the infected programs without being suspicious.
8 Common Signs That You May Have a Trojan Horse in Your Computer or Device
So, how do you know if your device is infected with a trojan horse? Of course, the immediate answer is that you can use an anti-malware scanner (and some antivirus programs) to check. The symptoms are often going to be the same, whether your device is infected with a trojan or any other type of malware:
- Antivirus and Anti-Malware Tools Are Disabled: You might notice that your antivirus program is suddenly disabled or even uninstalled.
- High Latency and Load Speeds: Your device suddenly becomes slow and sluggish. You may notice warning messages about your device lacking sufficient memory to complete tasks or run programs.
- Freezing Screen: You might even experience your screen freezing up completely or getting the dreaded “blue screen of death.”
- Unusual Cursor Movements: The mouse cursor starts acting up. This may involve moving automatically, moves in the different directions or at inconsistent speeds. In some cases, you might not be able to move or control it at all. Sometimes, the cursor disappears, and you can still notice some activities on your screen such as programs or browsers automatically open up (as if someone is operating your device from a remote place)
- Unsolicited Pop-ups: You start seeing unwanted pop-ups on your screen. This includes everything from frequent virus and software update alerts to advertisements and messages telling you to download unknown software programs.
- Automatic Website Opening: As soon as you connect to the internet or open a browser, some unknown websites open automatically in your browser. In some cases, you may be redirected to some unknown spammy website while surfing online.
- Unknown Extensions Appear In Your Browser: You will find some unknown extensions installed in your web browser. To check the extensions you have installed in your browsers, type chrome://extensions/ in Chrome’s address bar or about:addons in Firefox’s address bar. For Internet Explorer, go to the main menu and click on Manage Add-ons.
- Unknown Programs in Task Manager: If you open your task manager window (which you can do by pressing Ctrl+Alt+Delete), you will notice some unknown programs and apps running.
How to Protect Your Device from Trojan Horses
1) Beware of Phishing Emails
Attackers commonly use phishing email to distribute their trojan horse malware. To avoid accidentally downloading or installing a trojan:
- Educate yourself and your employees to recognize a phishing email. Check out these two easy-to-follow articles: How to know if an email is fake and phishing email scams.
- Don’t download an email attachment from unknown senders. Furthermore, always be sure to scan all email attachments with anti-malware software (even from senders you know) before downloading anything.
- Hover over your cursor to the links given in the email to know where it actually redirects to. You can also right-click on the links and hit Inspect. The link you will see after <a href=” is the webpage where the given link will bring you to.
2) Regularly Scan Your Devices with Anti-Malware Software
Security software and firewalls can detect and remove the majority of trojan malware. They can also alert you when you visit a spammy or malicious website, or if you download a corrupted file from the internet.
3) Be Careful When Downloading Anything from Internet
By now, you already know that trojan horses mimic legitimate software to lure users into downloading them. Hence why you must be extra vigilant in downloading anything from the internet. Scan everything that you download from the internet.
Apps: Beware of installing unknown apps. When you search for an app and see many other apps with a little variation in names, do an internet search to find the official name of the app you want to install.
Let’s say you want to install Zoom for conference calls. You might come across apps like Zoon-online, ZoomMeeting, GetZoom, Zoom Calling, Zoom Video Calling, etc. However, you’re not sure which of these is legitimate. To figure out which one actually belongs to the Zoom platform, visit the app’s official website and check the app publisher’s name in the app store before installing it on your device.
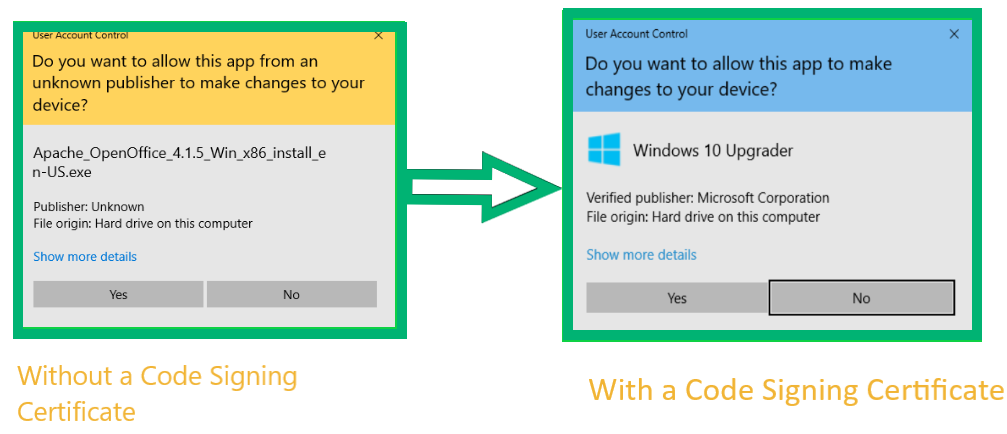
Software: If you’re downloading software, check out the publisher’s name in the security window and conduct a quick search about the publisher and read the reviews. If you see the publisher’s name as Unknown, avoid installing that software. When the software publisher’s name is written as Unknown, it indicates that they are not using a code signing certificate. Hence, such software shouldn’t automatically be trusted in terms of their integrity and authenticity.
Legitimate devs and publishers use code signing certificates to protect their software from being tampered with. The certificate authority (CA) who issues the certificate conducts a rigorous vetting process to verify the software publisher’s identity and issue the certificate only to a legit publisher.
4) Always Store Backups on Third-Party Cloud Platforms:
Always store your backups on a third-party cloud platform such as Google Drive, Dropbox, etc. This will help you to recover your data in the event of a crash or a cyber attack. If a trojan corrupts, encrypts, or removes your data, you can restore everything if you have a current data backup available. Backups are the best solution for the ransomware attacks. Always scan the files with anti-malware software before uploading them to the backup folder.
5) Keep Your Systems Patched and Up to Date
The best protection against many types of malware, including the vulnerability finding trojan, is to keep your operating system and all the software patched. Updates are not only for tweaking the appearance and functionality of the software. The publishers fix the security vulnerabilities in the old versions and publish the patched version. The hackers develop malware that can exploit the vulnerabilities of the old version. Hence why it’s always important to install the updated version of the operating system, software, and apps as soon as they are available.
Wrapping Up on Answering “What Is a Trojan Horse?”
A trojan horse can’t get into your system until you manually download it. So, be vigilant whenever you download anything from the internet. Whenever you find any software, program, application, free stuff, or advertisements online that look too good to be true, follow your instincts, and refrain from downloading them.
If you receive an unsolicited communication for some type of benefit (lottery winning, grand prize, free products, etc.), ask yourself why you’re selected. How many people do you know who are making millions just by playing some online games or casino? If you get a notice that you must use some software (like a flash player or any media player) to access content, do a quick search about that software and read the customer reviews. Also, even if it is a well-known software or browser extension, install them from their official website only instead of clicking on link given in the pop-ups.
We hope this article has helped you to answer questions like “what is a trojan horse?” and how to protect your device from this type of threat.







![The TLS Handshake Explained [A Layman’s Guide]](https://sectigostore.com/blog/wp-content/uploads/2023/01/tls-handshake-feature-150x150.jpg)






 (21 votes, average: 4.43 out of 5)
(21 votes, average: 4.43 out of 5)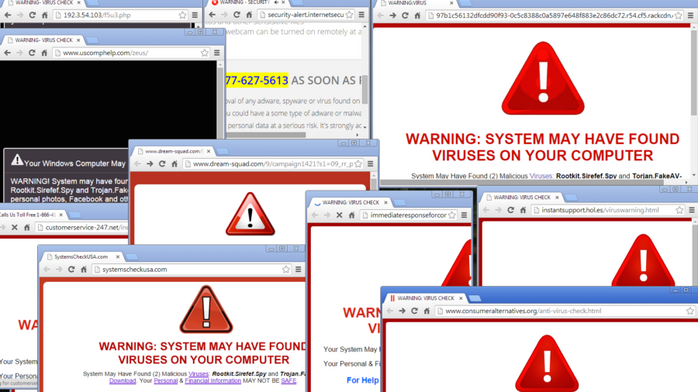







2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security