A Look Under the Hood: The White Hat Hacker (Ethical Hacker)
From information security analysts and pentesters to cybersecurity researchers and consultants — white hat hackers are everywhere and dedicate their skills to making the digital world a safer and more secure place
Note: This blog post on the topic of the white hat hacker (ethical hacker) is the first in a series of articles on the different types of hackers.
As a lifelong Lord of the Rings fan, the term “white hat hacker” always conjures up images of Gandalf the White in my mind. Gandalf stands for everything good in the face of evil or maliciousness. He always tries to do good and serves as a guiding light (in some cases, quite literally with aid of his trusty staff) to shine the way for others.
White hat hackers — or what are known as ethical hackers or white hats — are much the same. They’re the equivalent of Gandalf in the digital world (although likely without the epic beard). But what does it mean to be a white hat hacker (and what’s the definition of one)? What do these individuals try to accomplish? And what skills or training do you need to become one?
What Is a White Hat Hacker (Ethical Hacker)? White Hats Defined
In a world where the cost of cybercrime topped $3.5 billion in 2019 alone, white hat hackers are the good guys who fight to keep the bad guys at bay.
But if you’re looking for an official white hat hacker definition, there really isn’t a universal one. Basically, white hat hackers are those who hack systems with the permission of the owner. They do it to help the owner secure or improve their system. Black hat hackers, on the other hand, hack without permission — usually to cause damage for their own nefarious purposes.
So, in a nutshell, white hat hackers are defined as the “good guys.” They’re a community of hackers, computer experts and penetration experts who protect businesses and individuals by finding and fixing exploitable security vulnerabilities (such as zero day attacks) before the bad guys do.
White hats often work to find exploits in:
- Operating systems
- Software and hardware
- Websites and web applications
- Networks
- Physical defenses
- Human assets (employees and other authorized users)
They’re Not Who You Think They Are…
When people think of the term “hacker,” they often picture a stereotypical shadowy figure; the person whose face is hidden by a hoodie as they type feverishly on a computer in their mom’s basement. And while this may be the case for the obscure hacker, that’s not the reality for most people who call themselves by that moniker.
Basically, white hat hackers are virtual superheroes. They use their computer knowledge and expertise to help make the world (wide web) a better place for businesses and users alike. But instead of wearing spandex and a cape, you’ll find them working in IT and cybersecurity teams or consulting for businesses across the globe. Heck, they might even be someone you know — like that Jim guy who works in your IT department.
When Bad Guys Become the Good Guys…
Some white hat hackers are actually reformed black hat hackers and cybercriminals. Many white hat hackers use the same techniques as other less ethical hackers and train in the same arenas as them. The big difference is that they choose to use their skills for good instead of evil and operate with the permission of the organization they’re trying to hack.
There are many notable white hats who turned from the proverbial dark side:
We’ll talk about these guys and other renowned white hat hackers in a future article (stay tuned.) But for now, let’s get back on topic.
What Do White Hat Hackers Do?
To put it simply, white hats are offensive security analysts that help companies and organizations gain awareness and strengthen their security and cybersecurity posture. They do this by helping those organizations identify ways to shore up their defenses by:
- Continuously engaging in learning new knowledge, skills, techniques and programming languages.
- Staying abreast of industry changes and technological developments.
- Gathering intelligence about the organization, their IT infrastructure and employees.
- Using various legal and approved methods of digital and physical infiltration.
- Discovering and reporting bugs, vulnerabilities and other weaknesses (sometimes through bug bounty programs).
- Writing or developing code for programs, apps, rootkits, and honeypots.
- Simulating a variety of cyber and social engineering attacks.
- Recommending security improvements based on their findings and industry best practices.
Check out this video from Tech Insider, which shows a group of hackers breaking into the U.S. power grid:
But white hat hackers aren’t the only category of computer experts out there. As with many things in life, they’re a whole spectrum of them who work with different intentions in mind.
White Hat vs Grey Hat vs Black Hat: What’s with the Colors?
The whole idea of the different colored hacker “hats” — white hat, grey hat, black hat — comes from the concept of identifying hackers by their intentions (good, evil, or a mix of the two). There were originally three types of hackers: White, black, and grey hats.

Black Hat Hackers
Black hats are the n’ever-good-doers of the digital world. They like to cause mayhem and panic to serve some type of an agenda. Black hats are known for:
- Stealing money or other information that they can sell or use,
- Carrying out acts of revenge,
- Hurting the reputations of others (people, businesses, governments and other organizations)
- Carrying out political or social issues, or
- Simply causing mischief because they can.
Grey Hat Hackers
A grey hat hacker (or grey hat for short) is someone who isn’t 100% good or bad; on the spectrum of good to evil, they fall somewhere in between. (They’re kind of like tofu or certain types of pickles in that regard.) They’re the guys and gals who like to dip their toes in both the white and black hat pools. Essentially, they tend to whichever way the most profitable wind blows at any given time.
While grey hats mostly seem to like to do good, they may not always use the most ethical or legal channels to do so. They also often like to make a profit from their activities (often times engaging in bug bounties). So, while a grey hacker doesn’t necessarily have malicious intentions (unlike their black hat buddies), they may use unauthorized or illegal channels or methods to achieve their goals.
A white hat hacker, unlike their grey or black hat counterparts, always goes through official channels. They also have the permission of the organizations or institutions that they try to hack. A black hat hacker is someone who will do just about anything to make a profit or achieve another goal.
Feeling Left Out?
But, wait, aren’t there also green, blue, and red hat hackers as well? There sure are, depending on whom you ask. There’s debate within the industry about whether these other types of hackers should have their own separate classifications or simply fall under the umbrella of black hats.
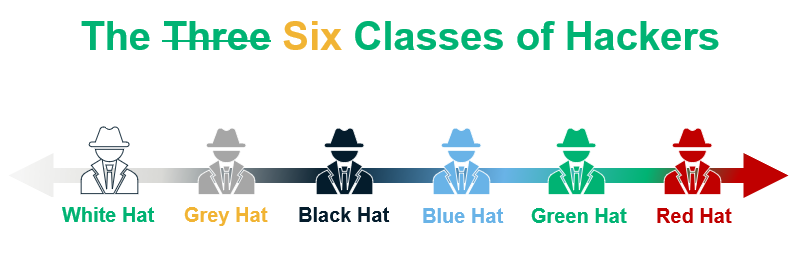
But for the purpose of this article series, we’re just going to focus on the three most commonly known types of hackers (white, grey, and black hats). We’ll touch on the other classes in a future article that covers the different types of hackers.
In the meantime, let’s get back to the topic of white hats…
What Tactics and Skills Do White Hat Hackers Use?
Take your pick. There are plenty of ways that white hats practice their craft and sharpen their skills. They use a variety of tools and techniques to discover both the human- and technology-based security deficiencies that exist within your organization, network, and other IT infrastructure.
In fact, many of the tricks they have up their sleeves are the same as black hat hackers — the big difference, though, is that white hats employ these tactics with the permission of their target. Yes, I mean that the organizations or businesses give them the green light to try to break into their business through virtual or physical means.
For example, some common white hat hacker tactics and skills include:
- Social engineering — White hat hackers commonly use social engineering (“people hacking”) to discover weaknesses in an organization’s “human” defenses. Social engineering is about tricking and manipulating victims into doing something they shouldn’t (making wire transfers, sharing login credentials, etc.).
- Penetration testing — Penetration testing is the bread and butter of white hat methodologies — and there are many different types, which we went over earlier. Ultimately, the objective is to uncover vulnerabilities and weaknesses in all of your defenses and endpoints so they can be remediated.
- Reconnaissance and research — Researching the organization to discover vulnerabilities within the physical and IT infrastructure. The objective is to gain enough information to identify ways to legally bypass security controls and mechanisms without damaging or breaking anything.
- Programming — White hat hackers create honeypots that serve as decoys to lure cybercriminals to distract them or help them gain valuable information about the attackers.
- Using a variety of digital and physical tools — This includes hardware and devices that allow the penetration testers to:
- pick or bypass physical locks,
- clone ID access cards,
- gain visibility and identify physical security blind spots,
- install bots and other malware, and
- gain access to the network or servers, etc.
Drilling Down on the Different Types of Ethical Hackers (By Roles and Responsibilities)
“Ethical hackers” is a bit of an umbrella term. When it comes to categorizing the different types of hackers, white hats tend to fall within a few camps based on their specific skillsets or specializations. You can find white hat hackers employed in a variety of IT and cybersecurity roles, including as security engineers, software developers and software testers. But the key takeaway here is that they’re always in high demand because of the value they provider.
Now, I’m not going to list these different roles in any type of “order of importance” because, frankly, they’re all important. Each different type of white hat hacker contributes to the greater good of their business or organization (and, by proxy, their customers or users) in some way. So, with that in mind, I’m going to take the easy way out and just list them in alphabetical order.
Cybersecurity Researchers
Cybersecurity researchers are much like researchers in other industries: They have to know where to find information, analyze it, and understand how to apply it. These types of researchers typically fall into one of two camps:
- They’re academics who dedicate their lives to researching and writing about cybersecurity, or
- They’re computer and operating system experts who like to get their hands dirty. They research and study things (operating systems, software, malware, etc.) to figure out how they work and to identify exploitable vulnerabilities.
Penetration Testers (Pentester)
Penetration testing is a very worthwhile profession that requires a lot of hands-on know-how and expertise. It’s the perfect example of taking hacking skills that could be used for evil and instead using them in a way that benefits society.
A pentester’s primary job is to find exploitable security vulnerabilities and identify other areas of security weaknesses (ideally before any black hats do). They may do this by testing new software and applications or even by taking a stab at breaking through your in-place security defenses. In addition to systematically trying to find weaknesses, they’re also responsible for:
- Communicating these weaknesses in via written reports, and
- Providing strategies and recommendations for how to fix those vulnerabilities.
- Providing feedback on existing security tools and solutions that the organization is already using.
Information Security Analysts
The U.S. Bureau of Labor Statistics (BLS) describes information security analyst as computer and information technology pros who plan and carry out security measures. Basically, these infosec pros are responsible for inspecting your organization’s network infrastructure and other IT systems.
Often times, their jobs are to monitor your systems and investigate any potential breaches. In some cases, they may manage or oversee a team of penetration testers or they may engage in pentesting themselves as part of their roles. Either way, they take the information that they have about those security weaknesses and vulnerabilities and figure out the best ways to address them.
There’s a lot of overlap between information security analyst jobs and cyber security consultant work. These consultants also focus on analysis and assessments of network, computer, and application security. Their goal is to help their clients identify and mitigate exploitable vulnerabilities. The biggest difference between them is the job title.
What Is a Certified Ethical Hacker?
The term certified ethical hacker refers to a type of certification training program for infosec professionals. The goal of this training is to provide you with the knowledge, tools, and resources that you need to protect an organization. In fact, it’s one of the baseline certifications that’s accepted by U.S., British and other countries’ intelligence agencies. CEH certificate holders must re-certify every three years to retain their status.
There are other types of certifications and courses you can complete, including:
- Computer Hacking and Forensic Investigator (CHFI)
- Certified Information Systems Security Professional (CISSP)
- Certified Register of Ethical Security Testers (CREST)
- Offensive Security Certified Expert (OSCE)
- Offensive Security Certified Professional (OSCP)
Technically, anyone who successfully completes the training can be called a certified ethical hacker. However, while some white hat hackers are certified ethical hackers, not all CEHs are white hats. This is an important distinction.
Final Thoughts on White Hat Hackers
Many times, the definition of a white hat hacker just doesn’t do them justice. To put it bluntly, white hat hackers are integral to the security of organizations, businesses, and governments. They help those organizations find and mitigate exploitable weaknesses before the bad guys do. And as we see from the growing number of organizations that are hacked or experience cyber breaches every day, these are the types of people that we need more of in this world.














 (28 votes, average: 4.71 out of 5)
(28 votes, average: 4.71 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security