Email Security: 10 Steps for How to Secure Your Email Communication
Email phishing increased 667% in March 2020 — here are some best practices to improve email security within the context of using secure SMTP, IMAP, and POP3
A look at the history of email tells us that this digital form of communication was initially designed with message deliverability in mind and not with a focus on email security. However, today’s virtual mail, though built on a protocol meant to handle only text-based communication (SMTP), has evolved considerably to support other messages formats through service extensions (such as MIME). This is where having secure SMTP is crucial.
As the risk of email-based cyber attacks has continued to grow over the years — with phishing attacks spiking more than 660% in March alone — it’s easy to see why security features relying on SSL/TLS, end-to-end encryption, etc. have been incorporated to enable secure SMTP communications.
But with criminals getting smarter and more skilled in their attacks, how can you keep your personal and professional messages secure? Here are a few email security pointers that can help us to stay protected:
10 Email Security Tips to Secure Messages Sent via Mail Transfer Protocols
Below, we’ll explore 10 practical checks you can use to achieve secure SMTP, IMAP, and POP3 communications for your email accounts:
1. Learn to Inspect Message Headers
Your email message headers are usually hidden by default, but you can Google ways to view the original message headers for your specific email client. For example, if you’re using the Outlook 365 email client:
- Double-click on an email to open it in a new window.
- Go to the File menu and select Properties.
- In the Properties window, you’ll see a field at the bottom that contains email header information.
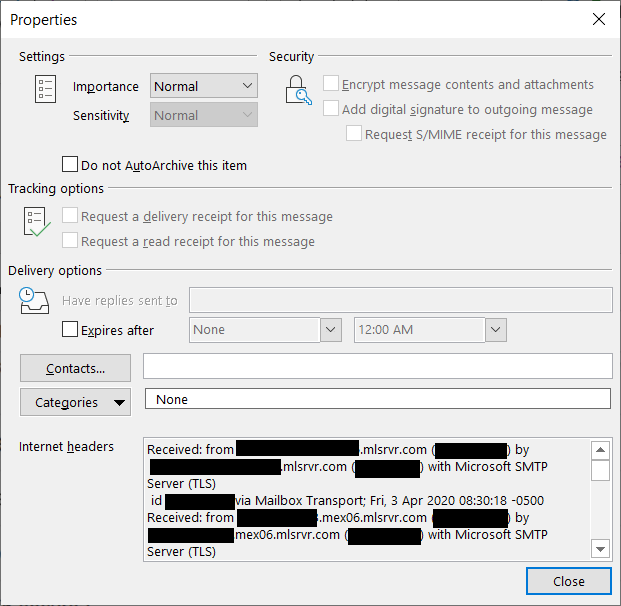
Once you can see the headers, look for the “Received From” field that tracks the route the message traveled across the net via servers to reach you. If you get a suspicious email, search for the sender’s IP and do a reverse lookup to trace the message back to where it originated. You can also check if the message fails sender policy framework (SPF) and domain keys identification mail (DKIM) checks.
Though most mail programs have email security indications like a red question mark for unauthenticated emails in Gmail, knowing how to examine email headers is a useful skill to have.
2. Avoid Clicking on Links or Downloading Attachments
As most of us know, email security’s biggest weakness often boils down to human error. This fact is continuously hammered into our brains by security experts and tech gurus. However, getting too curious to know what an attachment is, or being too absentminded to notice that we’ve accidentally clicked on a link are not impossible scenarios. Even the best of us can fall prey to phishing attacks — at least, the well-crafted ones. This is why, in addition to having spam filters and antimalware installed, we must be careful not to open any attachments or click on links from unknown senders (or attackers pretending to be Gary from the accounts department).
3. Update Your DMARC Records With the Domain Registrar
DMARC, aside from running checks on the messages using SPF and DKIM standards, is the only method that informs a receiving server of the action it should take in the event that a message fails these tests. If you’re a domain owner, besides configuring SPF and DKIM, consider setting up DMARC records with your domain registrar. iIn case you’re unsure about the process, they should be able to help you with it.
Neither SPF nor DKIM can prevent attackers from forging the “From” address that you see displayed in your inbox. However, DMARC verifies that the “from” matches the return-path checked by SPF and the domain name in the DKIM signature.
4. Test Your SMTP Server
To do this, try sending test emails to see how it responds to genuine and spam messages alike by monitoring the SPF, DMARC records. If it’s possible to tweak the SMTP configurations, change the default settings and update them with more secure alternatives (starting with changing default admin usernames and passwords).
5. Make Use of SMTP SSL/TLS Ports
SMTPS traditionally has used port 465 as a way to secure SMTP at the transport layer by running it over a TLS connection. When we refer to an SMTP SSL port (or, more accurately, SMTP TLS port), that’s exactly what we mean — it’s a way to have a secure exchange of messages between the email client and the email server over SSL/TLS channels.
TLS implementation can be done using two approaches – opportunistic TLS or forced TLS. With opportunistic (explicit) TLS, we try to shift from the use of unencrypted SMTP to a secure TLS encrypted channel utilizing the STARTTLS SMTP command. If the attempt fails, the transmission resumes in plain text, meaning without the use of any encryption. However, with forced (implicit) TLS, the email client and server are either able to negotiate an encryption version they can both support, or the transmission stops and the email communication doesn’t progress. You can make your choice depending on whether you want maximum deliverability or maximum privacy.
The Internet Assigned Numbers Authority (IANA) had registered port 465 for SMTPS, though it was never published as an official SMTP channel by the Internet Engineering Task Force (IETF). A new service had been assigned to port 465 by the end of 1998. while 465 functioned as a secure SMTP port, port 25 continues to be used as the default port for SMTP relaying. ISPs and hosting providers have restricted the use of port 25 for SMTP connections (to send mails across the net), and most modern email clients don’t use this port at all. Unless you’re managing a mail server (a message transfer agent or an MTA), typically, you should see no traffic over this port.
Port 587, along with TLS encryption, should be used as the default secure SMTP port for message submission as recommended by IETF in accordance with RFC 6409 that separates message submission (port 587) from message relay (port 25). Because many legacy systems continue using port 465 for SMTPS, you may still be able to find support for it from your ISP or hosting provider, but it is not recommended to use this port. Lastly, if port 587 is blocked, port 2525 though not officially recognized, is a commonly used alternative supported by most email service providers.
6. Deploy End-to-End Encryption for Maximum Email Security

With the note from the authors of RFC 5321 in mind, a note that indicates that SMTP mail is inherently insecure, consider using end-to-end encryption standards like S/MIME or PGP to encrypt messages on the sender’s device, as well as during transmission. This ensures that even if the message falls into the hands of an attacker, all they see is garbled data that makes no sense.
An additional benefit of using an S/MIME certificate (or email signing certificate, as it’s also known) is that it enables you to add a digital signature. This verifies the authenticity of the sender and validates message integrity.
7. Use TLS With IMAP and POP3
So, what’s POP3 and IMAP? The internet access message protocol (IMAP) and post office protocol (POP3, indicating version 3) deal with retrieving the messages from the receiving server. These are the protocols used by email clients like Outlook when getting your emails from mail servers. While IMAP syncs messages across all of your devices, POP3 downloads the message onto a single machine so that it’s available offline before deleting it from the server. Encrypted POP3 connections use port 995 (also known as POP3S), and IMAPS uses port 993.
8. Maintain IP Blacklists to Block Targeted Spams
If you’re frequently the target of junk and spam messages from IP addresses that share unsolicited marketing and sales pitches, it makes sense to block them on your email server.
To do this, you can use DNS blacklists (e.g., DNSBL, Spamhaus, etc.) or spam URI real-time block lists (e.g., SURBL, URIBL, etc.). A quick Google search will show you a bunch of available options, but be careful utilizing these kinds of tools — they’re not free of controversies and may inadvertently block some legitimate emails.
9. Use Restrictive Mail Relay Options
You don’t want to be an open relay because any spammer from anywhere in the world can use your server and resources for spamming others. The mail relay parameter specifies for which domains or IPs your server can forward mail. Configure these options with the utmost care if you wish to avoid getting on a blacklist.
10. Other Considerations to Improve Email Security
Some additional email security considerations that may come in handy include but are not limited to the following:
- Limit the number of connections to your SMTP server. You can do this based upon usage and server hardware specifications as these checks can prevent denial of service stacks.
- Define a failover configuration for MX records. Whenever possible, have a failover configuration when listing MX records to improve availability.
- Set up reverse DNS lookup to block IPs when authentication fails. Activate reverse DNS lookup that blocks emails if an IP mismatch occurs between the hostname and domain name of the sender.
Final Thoughts on Email Security
With attackers taking advantage of the global health crisis, email security has emerged as a primary concern area. Barracuda Networks reports having detected 467,825 cases of spear-phishing attacks since the beginning of March. While the numbers are certainly alarming, the good news is that these numbers can plummet by properly training employees on simulated attack scenarios, especially at a time when most employees are telecommuting to work.
Hopefully, the above pointers on secure SMTP will come in handy while configuring mail servers, or to exercise caution if you happen to receive any suspicious emails.














 (35 votes, average: 4.43 out of 5)
(35 votes, average: 4.43 out of 5)





2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security