Security Honeypot: 5 Tips for Setting Up a Honeypot
A security honeypot is a great tool for mature cybersecurity researchers and defenders. This article explores what it is and how to create a honeypot that may help you learn from legitimate attackers in a more controlled environment
Have you ever tried luring fruit flies away from your fruit with a container of sugar water, honey, or vinegar? If so, you’ve used a honeypot. Don’t check your address bar — you’re not on the wrong blog! In this post, we’re talking about honeypots in network security.
So, let’s see what a security honeypot is and explore some tips on how to safely set one up for your network.
What Is a Honeypot? What to Know Before Setting Up a Honeypot
In cybersecurity, a honeypot is a virtual decoy you set up to lure attackers into attacking it instead of your legitimate network resources. Honeypots are typically designed to look like real networks and resources, including formatting, content, and data.
Some examples of different types of honeypots that entice bad guys to attack include the following:
- A phony database
- A fake SSH portal
- A decoy email server
- A fake vulnerable web app
What Does a Security Honeypot Do?
Honeypots mimic other networks, software, or applications to lure in cybercriminals and collect information on who they are and how they attack to learn from them. This may leave you wondering: why in the world would you want someone to attack anything on your network?!
Basically, it’s a way to discover information about the attackers and their specific attack techniques and mechanisms. If you can figure out who they are, how they attack, and how well your cybersecurity and network measures hold up against them, it’ll arm you with the knowledge you need to help strengthen your defenses.
Let’s return to the fruit fly analogy we mentioned earlier. In our fruit scenario, we can think of the criminals as the flies and the network as the fruit. By setting up a more inviting target (the sugar water), you divert the flies away from your fruit, trapping them and keeping your fruit secure while also restricting them to an isolated environment where you can study them (if you so desire). A digital honeypot works the same way.
Honeypots are designed so that cybercriminals mistake them for legitimate assets. The more time the bad guys spend in the honeypot instead of attacking your authentic resources, the better it is for your security and overall organization.
What Are the Different Types of Honeypots?
We can divide honeypots into the following types:
- Production honeypots: Typically used by companies for private purposes. Fairly simple to set up and maintain, production honeypots capture limited information.
- Research honeypots: Used by governments or researchers to harvest serious data about cybercriminals and their attack tactics and methods. Research honeypots are complex and capture more information than production honeypots.
We can further divide honeypots based on the level of interaction they have with the outside world:
- High-interaction honeypot: High-interaction honeypots are complex and allow the cybercriminal to interact however they like, mimicking entire networks and operating systems. They are difficult to set up and manage due to their complexity.
- Medium-interaction honeypot: Medium-interaction honeypots are less complex, imitating layers of applications and sometimes file systems, but without their own fake operating system.
- Low-interaction honeypot: Low-interaction honeypots are the easiest to set up and maintain, but because of their simplicity pose risks, including detection by cybercriminals.
How Do Security Honeypots Work?
Honeypots allow intruders into the fake system to access information, but the information shared is heavily controlled. The administrators use fake information that looks legitimate to attract intruders.
We’re familiar with using firewalls to keep intruders out, but honeypot firewalls have the opposite purpose. These specific firewalls aim to keep the intruders inside the honeypot and restrict their exit to keep your legitimate network resources running the honeypot secure. The allows you to watch and assess the intruders to learn more about:
- Vulnerabilities in the host network
- The identities of the intruders
- Possible objectives of the intruders (what they try to access, steal, or modify)
- Intruders’ attack techniques (you can potentially even record their keystrokes)
- How to defend against attacks
- How well your network security resources are holding up
Multiple Honeypots Make a Honeynet
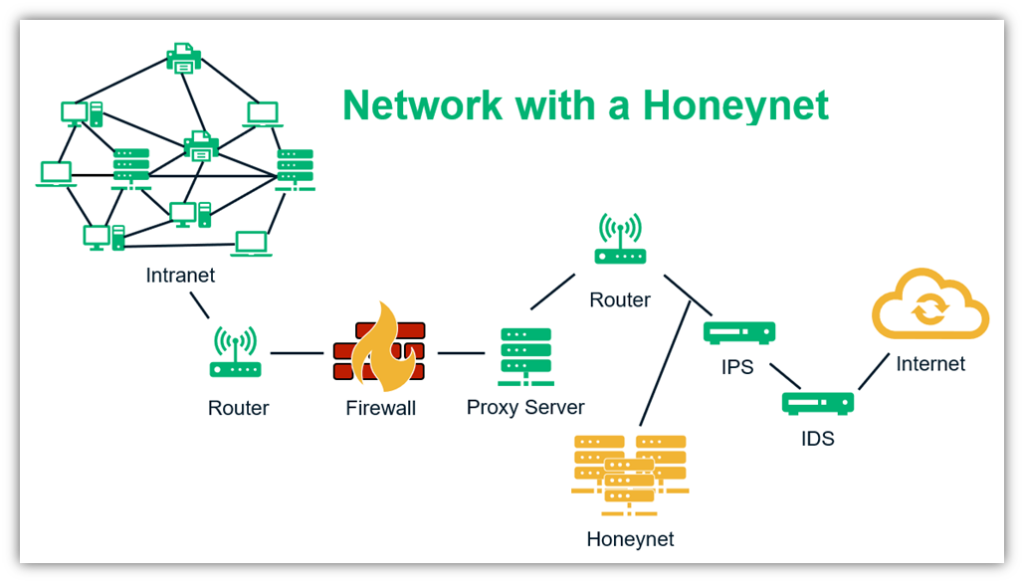
When the creators of a honeypot want the criminals to dive deeper and spend longer in the trap, they create a “honeynet” – a collection of honeypots with a complete collection of assets, including networks, software, and equipment.
A typical honeynet aims to do four things:
- Capture data about the identity, methods, and purpose of the bad guys
- Control how much data the criminals can access
- Share data captured with other relevant parties
- Analyze the data to give a more holistic view of the attackers
5 Tips for Setting Up a Honeypot for Network Security
By setting up a honeypot, cybersecurity experts can learn a lot about vulnerabilities in their network or software and the threat actors who try to attack it. They can then patch the vulnerabilities and develop techniques to prevent actual breaches.
But setting up a honeypot is a serious process that is not without risks, and it’s vital to seek help from professionals if you want to use one. Let’s look at some starter tips to avoid trouble when setting up and using honeypots. (This article is not meant to serve as a comprehensive guide to setting up honeypots.)
Tip 1: Understand the Legal Implications
When you use a honeypot, you’re setting up a safe target for cybercriminals who want to access your systems illegally to target. Since they’re performing illegal actions, it’s obvious that they don’t care about the laws of the land, but you still need to. Keeping on the right side of the law makes it more likely that any evidence you gather will be admissible, should you take the matter to court.
You could face trouble if you put other people’s data at risk, for example, by using real data in your honeypot.
Some of the legal issues you could face include:
Privacy Issues
Honeypot administrators ensure that sensitive information is not shared with intruders. If the intruders manage to access sensitive information, administrators could end up with a breach of trust lawsuit. The owners of the data could even sue the company for jeopardizing their information.
There is also the issue of what data can legally be collected from those trapped in the honeypot. Different countries have their own rules about this, and you need to be familiar with them if you’re going to use a honeypot. Check out this regarding privacy concerns and the use of honeypots.
Liability Issues
Honeypots can cause big problems if the intruders manage to break the firewall and enter the protected part of your network. From there, they could:
- Insert malware or malicious code into the system,
- Add any of your devices they infect to a botnet they control, or
- Make your system into a distribution node for their illicit data.
In that case, you could be held liable for the distribution of these data.
Entrapment Issues
The U.S. Supreme Court defines entrapment as “the conception and planning of an offense by an officer, and his procurement of its commission by one who would not have perpetrated it except for the trickery, persuasion, or fraud of the officer.” Put more simply, entrapment occurs when a government representative or other entity lures or tricks someone into committing a crime. These types of charges could be filed against you if it seems like you are “inviting” intruders to your network, so it’s important to take adequate measures to avoid that eventuality.
This issue is not applicable to private honeypot operators. If the honeypot owner is a private party and no government is involved in inducing the crime, then the entrapment concern isn’t an issue.
Tip 2: Plan Your Approach and Security-Related Considerations Ahead of Time
If you want to set up a honeypot on your network, you should have a foolproof plan — any errors and your original network will be at stake. You should consider the following questions when your honeypot is in the planning stage:
- How long do you want to keep your honeypot up/available?
- What are your specific, measurable goals/what do you want to achieve?
- Who is responsible for what aspects of this project/undertaking (i.e., do you want to rely on internal or external resources, such as a third-party vendor)?
- How will you test the honeypot? Before you put any intentionally vulnerable
- What will you do with the gathered data?
Tip 3: Use the Right Tools for the Job (Types of Honeypot Software)
Setting up a honeypot by yourself can be quite a challenging task (and dangerous if you misconfigure something). There are some tools that can come to your rescue and make your task easier. When setting up a honeypot, you need to have in-depth knowledge of what they are, how they work, and how to use them safely. Without knowing the subject inside out, you can invite more harm to your network.
You also need to have the right tools at your fingertips. The following list consists of examples of honeypot platforms (listed in no particular order) and are not product endorsements or recommendations:
Blumira
Blumira is a virtual honeypot software that helps you detect an attacker’s lateral movements on your network or in your system by following simple steps. It is low-maintenance, low-cost software. If Blumira detects a security threat, the software will help you block and contain it by showing you a step-by-step response workflow.
Argos
Argos is a tool that aims to help you set up honeypots to catch zero-day attacks in action. When it detects a threat, it logs the memory footprint of the attack. Setting up Argos doesn’t require any modification in the guest operating system. It is equipped to detect different attacks, including control flow attacks and code execution attacks.
Glastopf
Glastopf is a low-interaction honeypot that’s disguised to appear as a server hosting multiple web pages and web apps. All the pages and applications have many vulnerabilities to attract plenty of attackers.
Tip 4: Make the Honeypot or Honeynet Resemble an Actual Network
If the intruders find out that they were tricked with a honeypot, they could retaliate. They could find a way to breach your private network and cause damage there, or they might even threaten physical violence. It’s crucial for your security to keep your honeypot inconspicuous.
- Choose the right placement. Put your honeypot somewhere that makes it look legitimate to try to entice bad guys while still serving your needs. Part of this decision should be based on what you’re trying to accomplish — for example, some companies may want to place honeypots on their internal networks to try to snare bad guys who are already in their system.
- Use realistic-looking data. For example, you could use misspellings of inactive email addresses (by swapping or removing random letters from email addresses).
- Carefully select your interaction level. Higher interaction honeypots look more legitimate but are also riskier. Weigh your options based on your needs and your experts’ knowledge levels and skillsets. Using virtual machines and other additional technologies can help keep attackers from accessing your legitimate systems.
Check out this great video that discusses important honeypot security and implementation considerations:
Be Aware of Clues That Can Give Your Honeypot Secret Away
Let’s briefly cover some clues that could alert intruders that they are in a honeypot:
- The network is too easy to breach — Design your honeypot to mirror a real network
- The network has a lot of empty space for no apparent reason — Upload lots of files and folders (containing fake data) and connect resources to replicate a real network
- Responses from the network are slow — When someone is observing the traffic of your honeypot, the responses from the network are likely to be slower than those of a legitimate network. This can be a big giveaway that they’re in a honeypot.
- The network has too little traffic — Ensure optimum traffic on the honeypot akin to the network it mimics
- Outdated software indicates that the asset is not used often — Update software and firewalls regularly to prove that it is a genuine network.
Remember – a honeypot network should resemble a real network as closely as possible, not only on the surface but also in behavior. Little things can easily give it away!
Tip 5: Don’t Compromise Your Privacy for a Honeypot
When you set up a honeypot, you’re allowing bad guys to attack your network and are counting on your firewalls to keep them inside the designated area. However, you might underestimate their capabilities and could unwittingly give them access to your protected network, potentially compromising your data or those of your customers.
When you try to scam a scammer, it’s all too easy to get scammed. If the bad guys find a weakness, they will attempt to exploit it. It’s important for you to take a few steps to stay safe when setting up and using a honeypot:
- Use virtual machines to set up the honeypot so it’s hosted in an isolated environment that it’s easier to reboot when breached.
- Keep your honeypot separate from your original network.
- Use fake, tempting data to lure your targets in. This includes fake customer details, a fake credential database, employee bank details, etc.
- Install firewalls to keep the intruders inside the network for as long as possible.
- Employ experts to design and test the honeypot.
Final Thoughts on 5 Tips for Setting Up a Honeypot
A good honeypot can help us discover vulnerabilities in our networks and understand more about criminals’ identities, objectives, strengths, and weaknesses. We can then use this knowledge to strengthen our cybersecurity posture.
However, it’s imperative to remember that honeypots are serious tools that shouldn’t be used lightly. Although there are plenty of guides out there for setting them up, it isn’t safe to do it without expert knowledge. There are legal, privacy, and security-related issues to understand, and if you make the slightest error, you could face serious legal issues or cyberattacks. This is why you should either have someone in-house trained/knowledgeable about honeypots handling it or consider working with a third-party provider that’s experienced in this area.





















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security