What Is an X.509 Certificate? What to Know About PKI Certificates
X.509 certificates are the bricks and pavers that help to create the public key infrastructure that internet security is built upon…
If you’re looking for the answer to the question “what is an X.509 certificate?” then you’ve just hit gold. An X.509 certificate is a type of digital certificate that’s used across the internet in many different ways. In fact, you’re using one right now while visiting our website!
In a nutshell, X.509 certificates help to protect organizations and individuals from those who wish to impersonate them or spy on them. They do this through the use of asymmetric keys and third-party validation — which we’ll explain more in depth shortly.
Alright, so, let’s get right to it. In this article, we’ll cover key items to know about X.509 and X.509 certificates:
- What an X.509 certificate is,
- Who issues these types of certificates,
- The different types of X.509 certificates are and how they’re used, and
- What the X.509 public key infrastructure (PKI) standards are that they use.
What Is an X.509 Certificate?
An X.509 certificate allows websites, users, businesses and other organizations to prove their identities on the internet. In other words, they use an X.509 certificate like a passport to prove who they are. To put it in more technical terms, an X.509 certificate is a type of digital certificate that offers third-party authentication to websites, users, businesses and other organizations across the internet. This is known as third-party authentication.
But if you have an X.509 certificate for your business, couldn’t someone just steal the certificate and use it as a fake ID? Heh, not very easily. And that’s thanks to something that’s known as public key infrastructure, or PKI for short.
![]() X.509 Certificates and PKI
X.509 Certificates and PKI
X.509 certificates are an integral part of the international X.509 public key infrastructure (PKI) standards. These standards were first released back in 1988 and have been updated every few years since. The most recent release of the X.509 PKI standards was in October 2019. So, X.509 certificates are also known as public key certificates (or PKI certificates) because they’re created and managed according to these formatting standards.

The reason why someone can’t just easily steal and use your certificate as their own is because an X.509 certificate ties information about you (your organization) to a cryptographic public key and by making that key available to third parties. A public key is part of an asymmetric key pair that consists of a public and private key.
An illustration of how public key encryption (asymmetric encryption) works using public-private key pairs.
A Quick Look at the X.509 Certificate Format
X.509 certificate contains identifying information about your organization, your public key, and the digital signature of the entity that issued your certificate. More specifically, each certificate contains the following information as part of its X.509 certificate format:
- Your distinguished name.
- Your public key.
- The distinguished name of the issuing entity (typically a public certificate authority, which we’ll talk about shortly, but there are also self-signed certificates).
- The issuing entity’s digital signature (which is signed by their private key).
- Certificate issuance and expiration dates.
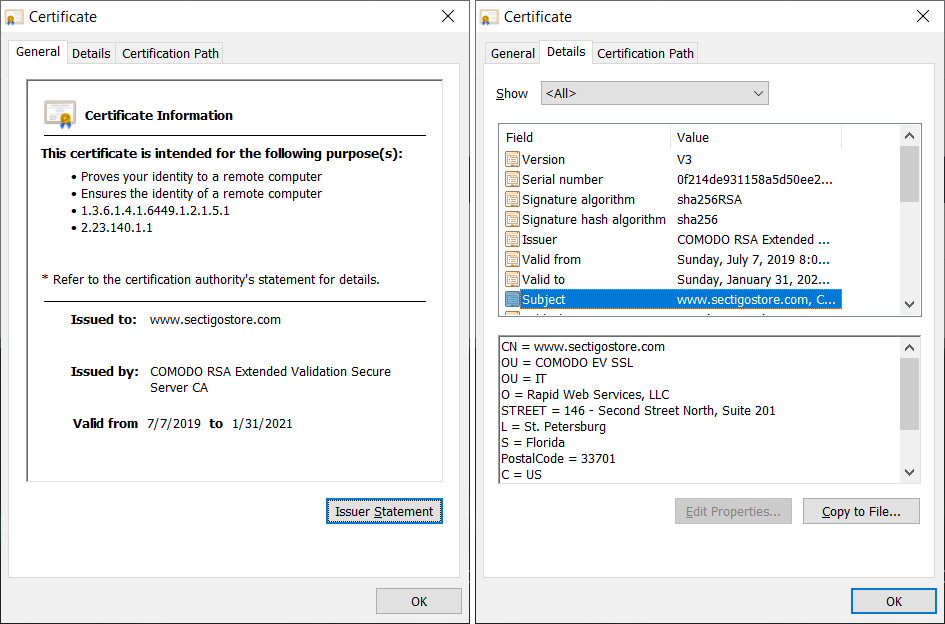
Screenshot of the SSL/TLS certificate that we use to secure SectigoStore.com.
Who Issues X.509 Certificates?
Certificate authorities (CAs) — originally called certification authorities — are the entities who are responsible for issuing X.509 digital certificates. They do this to ensure that each certificate they issue adheres to specific authentication standards and meets specific validation requirements.
Typically, when people talk about CAs, they’re specifically referring to public certificate authorities. However, there are also private CAs, which can issue and self-sign certificates for use within their own organizations and intranets. (Self-signed certificates should never be used for public-facing applications.)
Sectigo is an example of such a publicly trusted certificate authority. Although there are a few hundred CAs in existence around the world, only a handful or so of them issue the majority of certificates used globally.
The Roles That CAs Play in X.509 Certificates
So, what is it exactly that CAs do? According to the X.509 standards that were published in 2016:
“In order for a relying party to be able to trust a public-key of another entity, for instance to authenticate the identity of that entity, the public key shall be obtained from a trusted source. Such a source, called a certification authority (CA), certifies a public key by issuing a public-key certificate which binds the public-key to the entity which holds the corresponding private key.”
OK, that was a bit dense. Let’s unpack it…
CAs Validate Organizational Identities to Ensure They’re Legitimate
Before a certificate authority issues a public key certificate to anyone, they first validate that the requestor (your organization) is genuine. For example, if you’re requesting an X.509 certificate for your company website, there are three ways they can do this:
- Domain validation (DV) — This process involves the CA using automation to verify that an organization controls the domain in question. This typically involves either:
- Sending an email to a registered email address for that domain, or
- Sending an email with files that need to be uploaded to a specific folder of that domain.
- Organizational validation (OV) — This mid-level validation process involves the CA performing basic business validation. This verifies that you not only own or control the domain, but that your organization is legitimate. This helps to establish trust by showing that CA has verified your organization identity and that you’re, therefore, trustworthy.
- Extended validation (EV) — This process is the most in-depth of the three validation types. It requires multiple verifications checks using documents that are provided by the certificate requestor as well as other third-party sources.
CAs Bind Unmodifiable Public Keys to Organizational Identities
Now, after validating the organization in question, the CA binds the verified identity to the organization’s public keys. Think of this like the official seal on your passport. This helps to prove that your identity is genuine and verified.
So, what makes this public key so great? Basically, when a key is generated using secure cryptographic algorithms and appropriate entropy (randomness), these keys are essentially “unforgeable.” This means that they can’t be altered or modified in any way without those changes being detected.
What Are the 4 Types of X.509 Certificates?
It may surprise you to know that there’s actually more than just one type of X 509 certificate. There are many, and they’re used for different purposes. To help you understand the differences between them, we’ll go through each individual X.509 certificate example to breakdown what they are and why they’re useful.
1. TLS Certificates (SSL Certificates)

Let’s start off with the most popular and commonly used X.509 certificate. A TLS certificate, also known as a website security certificate, allows your browser to connect and securely exchange data with a website’s server. See that padlock in your browser’s web address bar? Yeah, that means your browser is sending and receiving data from our website’s server via a secure, encrypted connection. This is known as data-in-transit encryption.
This is why there’s “HTTPS” in the URL instead of just “HTTP.” Basically, HTTPS = the secure hyper text transport protocol. HTTP = insecure hyper text transport protocol. A protocol is a set of rules that dictate how devices exchanges data across networks and the internet. There are a wide variety of different protocols that are useful for different applications.
Whenever an organization has a TLS certificate installed on its servers, it means that the data exchanges that take place on the site use the transport layer security (TLS) protocol. TLS certificates are also known as SSL certificates because website certificates previously used the secure sockets layer (SSL) protocol to exchange data. (SSL is now a deprecated protocol.) The TLS replaced SSL as the go-to protocol for secure data transmissions.
SSL vs TLS Certificates
So, why do people sometimes call them SSL certificates instead of TLS certificates? Frankly, it’s because people are slow to change — particularly when it comes to the terms they use. So, you’ll still often hear people calling them SSL certificates instead of TLS certificates.
No matter. Just know that we’re talking about SSL/TLS certificates, we’re really talking about TLS certificates.
Types of SSL/TLS Certificates
SSL/TLS certificates are X.509 certificates that are typically categorized by 1) validation, and 2) functionalities. They can be issued with DV, OV or EV validation. There are several types of certificates that are available depending on the functions you need them to fill:
- Single domain SSL/TLS certificates — These certificates are great for securing both the WWW and non-WWW versions of a domain that you control.
- Multi-domain SSL/TLS certificates — These certificates allow you to secure multiple domains on one certificate by listing additional domains as subject alternative name (SAN) domains.
- Wildcard SSL/TLS certificates — These certificates enable you secure an unlimited number of subdomains on a single level.
- Multi-domain wildcard SSL/TLS certificates — These are your jack-of-all-trades type of SSL/TLS certificates. I say that because they allow you to secure an unlimited number of subdomains on all levels for multiple domains and SANs.
2. Code Signing Certificates
The next type of X.509 certificate we’ll cover is known as a code signing certificate. These certificates serve as a way for software developers and publishers to assert their publisher identity. This helps to protect the integrity of the software and its code.
The way the certificate aids in the effort is by allowing the software creator to affix a digital signature to their code, script, or executable.
You know these types of warning screens that pop up from Microsoft Windows?
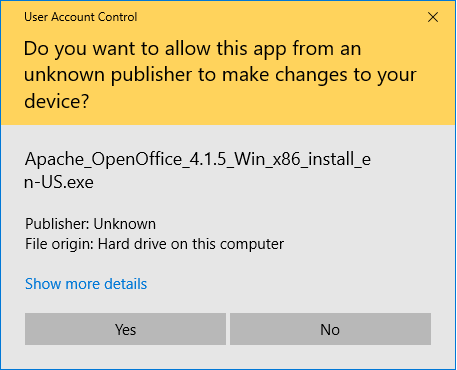
This warning message is a great way to drive away potential customers and users. A code signing certificate makes it so that your verified publisher information populates in the publisher field. This way, it doesn’t just say “Unknown” or “Unverified” anymore.
3. Email Signing Certificates
These X.509 certificates, which are also known as S/MIME certificates or personal authentication certificates (PACs), are a great way to securely send emails and to authenticate yourself to servers and other devices. They allow you to:
- Authenticate yourself to your recipients — This proves to your recipient that it was you who sent it (and that you’re not an imposter).
- Digitally sign emails — This proves to your recipient that the data and content within your email hasn’t been modified in any way since it was sent. It includes information showing how the certificate was cryptographically signed and at what time and date you signed it.
- Encrypt your email data — the message and any attachments within the email before you hit “send.” This is known as data at rest encryption. In order to send an encrypted email, however, both you and your recipient must be using an email signing certificate. This is necessary because you must get a copy of the recipient’s public key prior to sending an encrypted email. (You can get this by having the recipient send you a digitally signed email ahead of time.)
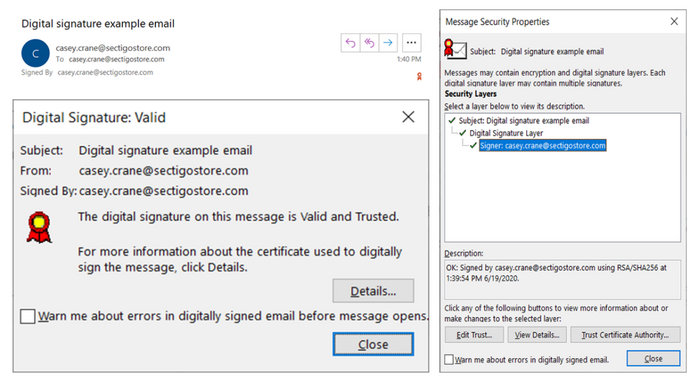
These certificates are also known as personal authentication certificates because they’re useful for authenticating users (or, more specifically, the clients on their applicable devices) via two-way authentication. This type of authentication allows you to gain access to specific applications, sites, servers, or devices.
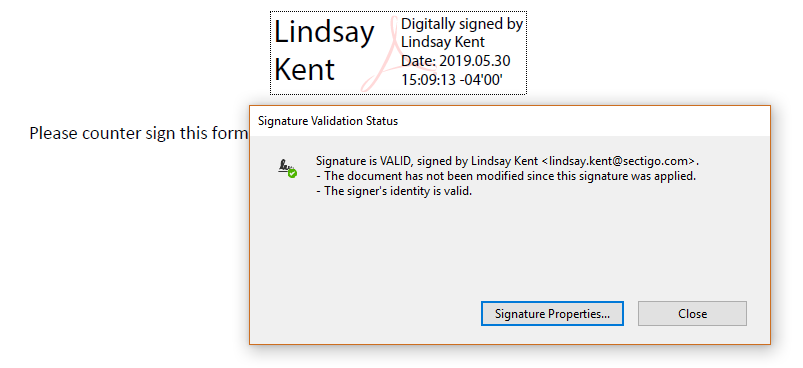
![]() 4. Document Signing Certificates
4. Document Signing Certificates
These X.509 digital certificates enable users to digitally sign the documents they create (Word docs, PDFs, etc.). What this does it allow the document creator to prove that they created the document and that it hasn’t been altered or modified in any way. Basically, you’re validating the document’s integrity so that people know it’s safe to use.
What Is the X.509 Public Key Infrastructure Set of Standards?
Public key infrastructure (PKI) is the foundation of global internet security as we know it today. The X.509 international standards is a document that defines the format, processes and entities that are involved with the creation, management, and revocation of public key digital certificates. It also covers asymmetric cryptographic techniques and how identities are paired with cryptographic key pairs.
Back in 1988, two international standards organizations set up committees to collaborate and create a set of standards for dealing with the technical aspects of public key certificates. This set of standards is known as the X.509 public key infrastructure standards, and there have been multiple versions of these standards that have been released over the past three decades.
The two organizations that were involved in creating the standards are:
- The International Standards Organization (ISO), and
- The International Telegraph and Telephone Consultative Committee (Comité Consultatif International Téléphonique et Télégraphique, or CCITT), which later became the International Telecommunication Uninion Telecommunication (ITU-T) standardization sector.
The process also now involves the International Electrotechnical Commission (IEC), who has a joint committee with ISO. (The IEC joined the collaborative effort for the version of the X.509 standards that were released in 1993.) Together, these three organizations develop the international standards that businesses and technologies worldwide use today.
There have been about 30 updates made to the X.509 public key infrastructure standards since they were first released since 1988. The latest version of the X.509 standards document was released in October 2019.
A Summary of X.509 Certificates
To summarize the point of this entire article, X.509 certificates (aka public key certificates) are integral to the security of data and authentication of communications over networks and the internet. Many types of data exchanges and their applicable protocols rely on X.509 certificates. They come with different validation levels and have different functionalities as well.
Today, X.509 certificates are useful for many tasks, including:
- Authenticating clients, servers, and other devices as well as individuals and organizations.
- Ensuring the integrity of emails, software and code, digital documents, and various data transmissions.
- To secure data exchanges for websites and email communications using encryption. This helps to protect data both while it’s in transit and at rest (depending on the application).
I hope this article answers your questions about what X.509 certificates are and how websites, businesses, organizations and individuals around the world use them.














 (49 votes, average: 4.73 out of 5)
(49 votes, average: 4.73 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security