Wondering how does HTTPS encryption really work? We’ll break it down into 5 simple steps
It’s no secret that an HTTPS connection is required for data security on websites. In fact, Google uses it as one of its search ranking factors. But to answer the question “how does HTTPS work?” you first need to understand how an HTTPS connection protects your data and what role an SSL certificate plays in the HTTPS protocol enabling process.
This is where an SSL/TLS certificate comes into play.
In this article, we will answer your questions about “how does HTTPS work?” and “how does HTTPS encryption work?” We’ll also explore how it secures data, and how an SSL certificate is required to enable the HTTPS protocol in the first place.
How Does HTTPS Work?
The hypertext transfer protocol (HTTP) is made for transferring data via internet from one computer to another. It uses port 80, and the data remains in plaintext format in transit. An HTTPS protocol, on the other hand, is the secure version of this protocol that relies on port 443.
HTTPS works on public key infrastructure (PKI) to encrypt online communications. A PKI encrypts and decrypts the data using two types of keys – public and private – to ensure its security. Nowadays, the data transmitted online is protected using transport layer security (TLS), a protocol within the PKI infrastructure.
An SSL/TLS certificate is needed to make this happen. When you install an SSL certificate on your server, it provides a layer of security around this data. It enables your website to be served via the secure HTTPS channel where the data gets encrypted while it is traveling from one endpoint to another. It also ensures that the data is routed to the right server.
To make things a little clearer, let’s explore what exactly happens when you install an SSL certificate and how does HTTPS encryption work with this five steps process.
1. Exchanging Hello
When a website visitor opens a website on a browser, the browser sends a “client hello” (also written as ClientHello) to the server (where the website is hosted). The message, which is part of the SSL/TLS handshake process, contains the set of algorithms (cipher suites) it requires the make an HTTPS connection and the latest TLS version it can support. The server responds by sending the server hello (ServerHello) message to make the browser know whether it can support the ciphers and TLS version required by the browser.
If it does, they move forward to the next step in the handshake process. If not, the browser will show the users the error page with error messages such as “ERR_CERT_WEAK_SIGNATURE_ALGORITHM.”
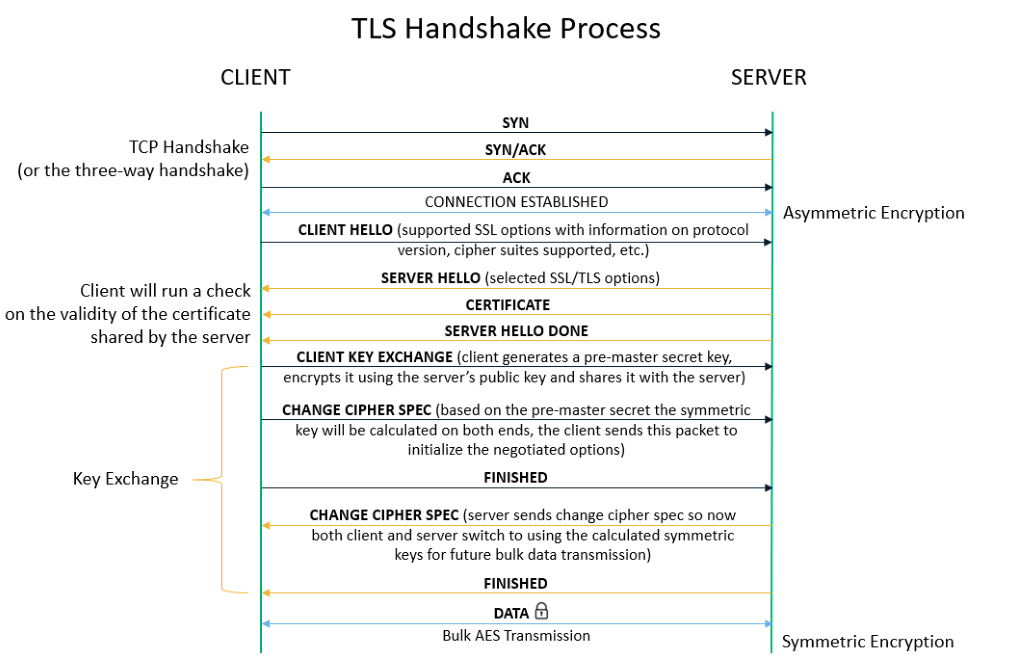
2) Verifying SSL/TLS Certificate
Now, the server sends its SSL certificate to the client. The SSL certificate would be just a simple text file containing the domain’s public key, hostname, issuance and expiry dates, etc. The client verifies whether the certificate is valid or has been revoked, and ensures that it supports the required ciphers. It also confirms whether the certificate belongs to the “hostname” (i.e., domain name or an IP address) that the user has requested.
3) Validating the CA Signature
After verifying the TLS/SSL certificate, the browser confirms who issued and signed the certificate. Typically, this is a trusted third-party entity that’s known as a certificate authority (CA).
- An SSL certificate is just a text file that anyone can make and sign. So, the browsers need a third-party, whom it trusts, to vouch that the details written in the certificate are legitimate.
- When you buy your SSL certificate from a CA, it follows a strict validation process stipulated by the CA/Browser Forum.
- Only after successful validation does the CA sign your certificate with its own intermediate root certificate’s private key.
- The browsers have a pre-installed root store, which it uses to verify the validity of the signature.
- If the certificate has a legit CA’s signature, the SSL handshake process completes (finally!), and it would follow the next step. If not, it will show error messages such as ERR_CERT_AUTHORITY_INVALID to the user.
- If you are using a self-signed certificate, the browser won’t trust it and will show the ERROR_SELF_SIGNED_CERT error message to the users.
4) Generating a Shared Session Key
During the SSL handshake process, the browser generates a random session key (typically made using the RSA key exchange algorithm). It encrypts it using the public key contained in the SSL/TLS certificate. The server needs to decrypt the session key with the private key.
All the servers have a unique public key and its corresponding private key. Each public key is stored in the certificate and can be viewed by anyone. It’s used to encrypt the data. Its mathematically related private key is safely stored on the server and is used for decrypting the data.
5) Transferring the Data Via HTTPS
Now, when someone visits your website, all their user data will be transmitted in a secure, encrypted channel throughout the entire session using this session key. Their data also will travel over the internet using a secure HTTPS port to reach your server. The server then decrypts the data using the same session key.
So, in a nutshell, this is how HTTPS works.
Although the entire process looks lengthy, it’s automatically happening in the background so quickly, within just seconds (or, rather, fractions of a second), that you won’t even notice. Most of the time, this process doesn’t affect the speed of the website, but if you have a large number of visitors accessing your website simultaneously, the server needs to deal with numerous session keys at the same time. So, the connection speed might get little hampered. But in such cases, you can use SSL offloading to improve the site speed.
Get the Top-Notch Brand Sectigo’s SSL Conly For $8.95/Year!
Save 87% on SSL Security Certificates! Get the lowest prices on trusted SSL certificates from Sectigo.
Shop NowWhat If Someone Gets Access to Your Encrypted Data?
The magic of the HTTPS protocol is that, just like it happens with HTTP, anyone can intercept the data while it is in transit. However, all they would get is an encrypted form of the data (ciphertext), which would be nothing more than a bunch of gibberish that doesn’t make sense at all!
So, even after getting access to the data, no one can read, interpret, modify, or steal it without having the private key to decrypt it! That’s how the HTTPS encryption works and secures the data in transit.
Wrapping Up the Topic of “How Does HTTPS Work?”
As you can see, an SSL certificate must be installed on the server (where the website is hosted) to enable the HTTPS protocol. An SSL/TLS certificate must be signed by the publicly trusted CA, too, to ensure that the browser trusts the certificate. All of these things come together to make a secure connection possible via the HTTPS protocol.
If you get your SSL/TLS certificate from a reputable CA like Sectigo (formerly Comodo CA), all the browsers will trust your certificate. With every SSL certificate purchase, you’ll get up to an 82% discount on the retail price, a free dynamic site seal, a generous warranty, a 30-day money-back guarantee, and 24/7 live customer support.
Learn About Standard SSL Certificates
 (8 votes, average: 4.50 out of 5)
(8 votes, average: 4.50 out of 5)