The Difference Between Authentication and Authorization — Explained in Detail by a Security Expert
Authentication vs. authorization — what these two terms are and why should you care about them
People tend to get confused between the words “authentication” and “authorization” because they sound and are spelled in a somewhat similar manner. And while the terms appear similar on the surface, their goals are different — the first is about figuring out who you are, and the other focuses on verifying whether you’re allowed to do something.
Although they have different meanings and serve different functions, authentication and authorization are both essential concepts of identity and access management (IAM) and good security design. In this article, we’ll explore what these terms entail and discuss examples from real-life scenarios.
So, without further delay, let’s explore authentication vs. authorization in detail.
Authentication vs. Authorization: What’s the Difference Between Authentication and Authorization?
Authentication is one of the stepping-stones for authorization: Only after you’re authenticated, you gain authorization, but typically not vice versa.
For example, I need my user ID and password to authenticate myself to Facebook and log in to my account. Once I authenticate myself, I’m authorized to make changes to my Facebook profile. But if I forget my credentials, I can’t log in to my account. Hence, I can’t use my privileges (authorization) until I successfully pass through the authentication phase.
Both the concepts have different levels: Even after authenticating myself, can I change the entire Facebook’s color from blue to pink? Absolutely not! So, when I log in as a user, Facebook does authorize me to post text and media on my account, manage my friend list, and make some other account-specific changes. But I am not authorized to make changes in their website’s coding, CSS, or databases. For that, I need to authenticate myself to be Facebook’s webmaster, admin, development manager, or Mark Zuckerberg!
Human Intelligence Vs. Machines in Authentication and Authorization
In a real-life, human intelligence is an important part of the authentication and authorization processes. So, let’s say, a cop asks for your driver’s license and you show him a license with Donald Trump’s name and picture on it. The cop instantly knows that the license is fake. He would also consider you ineligible to drive until you provide an authentic license that has information that matches your description.
However, in the digital world, authentication isn’t as clear-cut. For example, if you were to use Trump’s correct user ID and password on Twitter, the system will instantly believe you and give access to his account and all the privileges that entails.
As you can see, although machines have made our lives way more comfortable, it is easy to defraud them. There are many types of advanced cyberattacks (such as cross-site scripting (XSS), SQL injection, DDoS attacks, cross-site request forgeries, etc.) that hackers can deceive the authentication and authorization process to commit cybercrimes.
That’s why businesses must set the authentication and authorization policies carefully and with due vigilance.
Authorization and Authentication Within an Organizational Environment
In all organizations, authentication and authorization are separate but related processes. If your organization fails in the authentication step (i.e., if it doesn’t have a robust verification system like strong passwords, biometrics, etc. to correctly authenticate users), then outsiders can access whatever information is available to that account based on its privileges.
If your organization doesn’t implement authorization strategically and hands out unnecessary levels of access, then you’re increasing the risk of data leaks, data breaches, and other damage from insider threats. For example, if an employee decides to steal critical company databases, files, documents, resources, and sell them to competitors, or on the dark web, then you’ve essentially handed them the keys to your kingdom.
So, please make sure you carefully set the permission and access rights of all the employees. You must also encourage employees to set strong passwords or use password managers.
Authorization and Authentication in WordPress
If you’re running a WordPress site with having multiple contributors such as co-authors, editors, designers, WP developers, etc., make sure you pay equal attention to the authentication and authorization.
For robust authentication, you need to use plugins like Force Strong Passwords, which forces all users to create strong passwords. You can also use password managers like Password Pointer, 1Password, LastPass, Secure Password Generator, Disable Post Passwords, etc.
To mitigate unauthorized access via brute force attacks, use plugins like Limit Login Attempts, Loginizer, or WPS Limit Login.
For authorization, you could limit other contributors’ functions and permissions. Only you should have 100% control over your admin panel, and others should only have access to the functionalities that are necessary for them to do their job. You can also set a separate password to access some parts of your admin dashboard, via .htaccess or cPanel to protect crucial parts of the admin dashboard.
What’s Authentication and How Does It Work?
In the most basic sense, authentication refers to the process of confirming someone’s identity. To confirm a person’s identity through non-digital means, documents such as passports, driver’s licenses, state ID, social security cards, etc. are used as a part of the authentication process.
In the digital world, though, we rely on machines and artificial intelligence to verify users’ identities. To make sure it is dealing with the same person they are claiming to be, the machine needs to use authentication methods such as passwords, one-time passwords (OTPs), and biometrics.
The authentication methods are selected from three main types of information:
- what you know (like passwords, answers of security questions, access pins, ATM pins, etc.),
- what you possess (like a digital ID card, a mobile device or app, a security token, etc.), and
- who you are (biometric data like fingerprint authentication software, retinal scans, face recognition software, etc.)?
There are three main types of authentication:
Single-Factor Authentication (SFA): This is the simplest form of authentication. A person needs to provide only one piece of information to confirm their identity. The most common example of SFA is a password. So, for example, just by entering your specific password, you can access your email, social media accounts, and pretty much any website where only a password is required to log in.
Two-Factor Authentication (2FA): In 2FA, there are two verification steps involved to get access to a system.
A common example is a one-time password or one-time pins (OTP). To complete online purchases, you need to provide a credit card/debit card number, CVV, and card expiry date information. If all this information is accurate, you may be asked by your bank to provide an OTP that’s sent to your registered mobile number as a second layer of protection. Only after providing the six-digit OTP, the transaction can be completed.
In short, for 2FA, two pieces of confidential information are needed to verify the person’s identity. For transactions that handle sensitive information, this is obviously a safer method than simply relying on single-factor authentication alone.
Multi-Factor Authentication (MFA): Multi-factor authentication is the most advanced form of authentication. Here, you have to pass through two or more layers of verification processes to prove your identity to a system.
Examples of Authentication Methods in Action
The concept of authentication plays a crucial role in the public key infrastructure (PKI). All the digital certificates use cryptographical “keys” as an authentication method to make sure the data exchange is taking place between the intended endpoints only.
Authentication and Email Signing Certificates
Email signing certificates also use PKI to enable the email senders to insert their digital signature with all the outgoing emails. These digital signatures can’t be tampered with, hence they’re robust proof of the sender’s identity. When the recipients authenticate the sender’s true identity, they can protect themselves from becoming victims of email spoofing.
Authentication and Code Signing Certificates
A code signing certificate is another security tool made exclusively for software publishers’ identity authentication. The CA conducts a strict background check before issuing a code signing certificate to any entity. When a user downloads a software, which is digitally signed using a code signing certificate, the security window displays the original software publisher’s name on it as a proof of their authenticity. It gives power to the users to know who they are downloading software from and decide whether to trust the source.
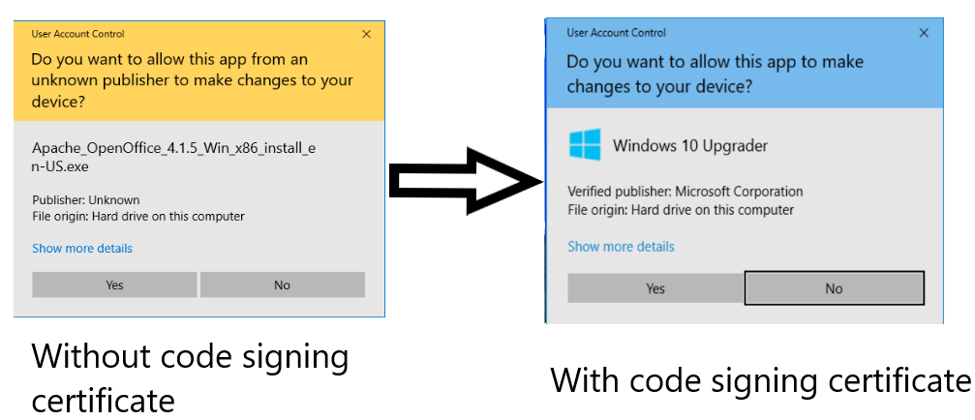
Authentication and SSL Certificates
All websites that use SSL/TLS certificates have unique public keys and corresponding private keys. During the TLS handshake, the browser generates a session key using a website’s public key and sends it to the server. The server can decrypt the session key only with its unique private key. This is how the browser authenticates the server’s identity and ensures that it’s communicating with the same website it claims to be.
What’s Authorization and How Does It Work?
Authorization is a process that determines whether you have the access rights, permissions, or privileges to do something. This typically takes place once your identity is authenticated. For example, if a police officer pulls you over, he can verify your identity after reviewing your driver’s license. However, your license is expired. Now, even though you have passed the authentication step, you’re not authorized to drive until your license is renewed.
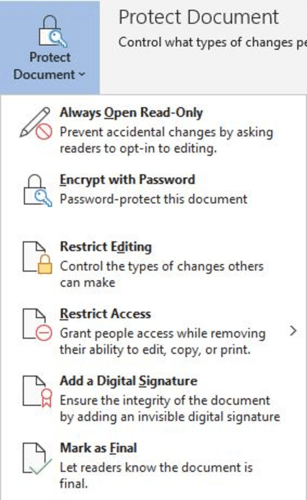
A good example of authorization is editor capability options available with Microsoft Office products such as MS Word, MS Excel, etc. If you have enabled “Always Open Read-Only” or “Restrict Editing” mode, you authorize other people to read the content of the document but not to make any modification in the same.
In the same way, WordPress and other CSM platforms also allow the admin to set the permissions for each of the contributors. For example, you can authorize staff writers to publish content but restrict them to change the theme or plugins of the blog.
A Final Word
Authorization and authentication are integral components of any organization’s security efforts. In fact, virtually all organizations implement these methods for their employees and users in one way or another. The question is how well or poorly they do so.
It is a general understanding that the safer the authorization and authentication method is, the more expensive it will be. For example, implementing biometrics. But this is a short-sighted view — and here’s why:
Consider the cost associated with cybercrimes. Once your data lands in the wrong hands — and we say “once” instead of “if” because it’s just a matter of when and not if a data breach will occur — the direct cost (like paying the ransom or unauthorized fund transfer from a bank account) and indirect cost (like spoiling company reputation due to data leaks, or losing sales due to leakage of company’s confidential information or know-how) can be devastating. Therefore, it’s essential to implement stronger and safer authorization and authentication methods to strengthen the overall security of your business or organization.
























 (19 votes, average: 4.58 out of 5)
(19 votes, average: 4.58 out of 5)






No comments