What Is Scareware? Examples & What to Know
Explore what scareware is & how it infects devices. We’ll also share scareware examples & how to protect yourself from scareware scams
Imagine that you’re surfing the internet when, suddenly, you receive a notification telling you that your computer is infected with multiple viruses! The message appears legitimate and says that using their antivirus software will eliminate the threats. But, in reality, all it does is allows worthless or malicious software to install on your device. This is just one of many scareware example scenarios users have encountered over the years.
But exactly what is scareware? And why is it something that all users should be aware of when using the internet?
What Is Scareware?
Scareware refers to scam tactics and fake software applications that cybercriminals use to incite feelings of panic and fear. They do this to get users to make irrational split-second decisions and to trick them into:
- Buying worthless software,
- Downloading different types of malicious software, or
- Visiting websites that auto-download and install malicious software onto their devices.
Scareware scammers use social engineering tactics and language that creates a sense of urgency in their targets to compel their targets to act. But how do they reach their victims? They frequently rely on pop-ups that are designed to look like antivirus alerts. In some cases, the messages can take over part (or all) of the target’s screen.
In general, scareware messages are associated with fake antivirus software and tech support scams. They falsely notify people that their devices (such as their computer, tablet, mobile phone) are infected with various types of malware.
But just how big of a problem is scareware nowadays? While scareware has declined with the growth of ransomware, the FBI’s Internet Crime Complaint Center (IC3) reports that tech support fraud is a growing problem that resulted in 13,633 complaints with losses surpassing $54 million in 2019 alone. The IC3 reports losses specifically relating to “Malware/Scareware/Virus” as totaling $2,009,119 in that same year. That still equates to a lot of scares for a lot of people.
What Does Scareware Do?
At best, the software does nothing and “only” costs you the money you spent to buy it. But oftentimes, the software causes harm by installing malicious software that can:
- Commandeer your computer,
- Spy on you,
- Result in data theft, or
- Lead to further financial losses.
Some types of scareware rely on the user downloading the software. Others will auto-download without the user’s knowledge or consent. But why bother doing this at all? The purpose of the scareware can be to achieve any of the following:
- To make people buy the rogue software, which is non-functional.
- To make people install the software, which contains malware in itself.
- To steal victim’s payment card number, bank account details (which they use to purchase the software), or personally identifiable information (PII), to deploy further financial fraud or identity theft-related crimes.
To better answer the question “what is scareware?” let’s look at a few scareware examples.
Examples of Scareware: What Does Scareware Look Like?
If scareware malware gets installed on your device, it stays dormant for some time and analyzes a user’s activities. It starts showing fake malware threat pop-ups to the users that looks like coming from the Windows/iOS or their current antivirus software. The pop-up could look something like this:
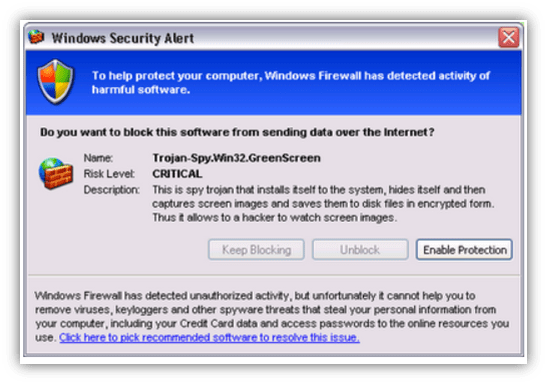
Sometimes, the pop-ups have a “clickjacking” feature. That means, if a user clicks on the “cancel,” “close” or the “X” buttons to close the scareware window, it redirects them to an infected website or triggers malware to download automatically.
Certain types of scareware can also:
- Alter the device’s internal settings,
- Change the background wallpaper,
- Redirect users to malware-laden websites as soon as they open the browser, or
- Make the computer slow.
When users notice any of these changes, they panic and believe that their computers are infected, so they take the actions recommended in the pop-up window to try to fix the issues.
But as we pointed out earlier, the scareware might be residing on third-party platforms like websites or mobile applications, too. That means you can encounter such a scareware pop-up when you visit certain websites that will try to get you to install a scareware application onto your device. The ad might be a small dormant banner, or it could take up the whole screen and makes you unable to access the website’s content.
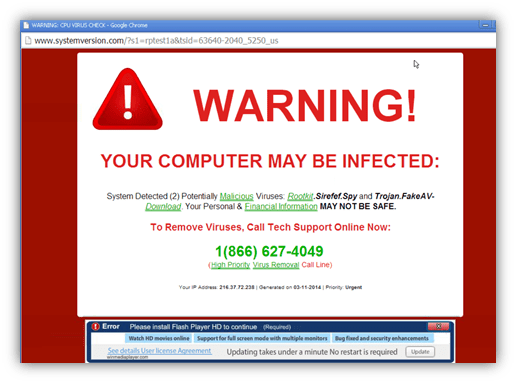
Scareware Examples
Although the scareware programs’ goal is the same (i.e., to scare users in order to defraud them or get them to download malicious software), each scareware program is made differently. This is the list of all scareware examples: smithtechres.com/fake-antivirus-and-antispyware.html
Some past popular scareware examples of fake antivirus and anti-malware solutions include:
- SpySheriff
- XPAntivirus/AntivirusXP
- ErrorSafe
- Antivirus360
- Antivirus2009
- PC Protector
- Mac Defender
- DriveCleaner
- WinFixer
- WinAntivirus
- Spyware Protect 2019
Scareware Examples That Have Made Major Headlines
Scareware has been used by cybercriminals and real businesses alike to try to scam users and customers into downloading or buying software they don’t need. Let’s consider a few quick examples:
Office Depot and Support.com Carry Out a Decade-Long Tech Support Scam
While you’d expect underhanded tactics from cybercriminals, you wouldn’t necessarily assume the same thing from a legitimate organization like Office Depot. The Federal Trade Commission reports that Office Depot and tech support company Support.com, Inc. were ordered to pay a total of $35 million in settlements with the Federal Trade Commission (FTC) in 2019. The settlement aimed to refund consumers for fraudulent services they purchased over nearly a decade.
The company required its employees to run a rigged PC diagnostics check known as PC Health Check, which BleepingComputer reports allowed them to sell “unnecessary tech repair services.” Furthermore, employees had “daily quotas for PC repair services” that they were expected to meet. The warnings would be activated if users indicated any of the following:
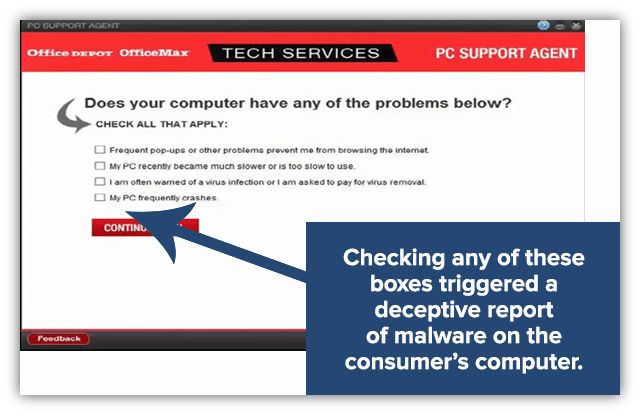
Hacker Uses Minneapolis Star Tribune Website to Carry Out Scareware Attacks
In 2018, the U.S. Department of Justice reports that Latvian national Peteris Sahurovs pleaded guilty to being part of a scareware hacking scheme between May 2009 and June 2011. Part of that time was spent giving technical support to the scheme that targeted visitors to the Minneapolis Star Tribune’s website. Sahurovs admitted to receiving upwards of $250,000 (U.S. dollars) for his years’ long participation in the scheme.
As the DOJ reports:
“According to admissions made in connection with his plea, from at least May 2009 to June 2011, Sahurovs operated a “bullet-proof” web hosting service in Latvia, through which he leased server space to customers seeking to carry out criminal schemes without being identified or taken offline. The defendant admitted that he knew his customers were using his servers to perpetrate criminal schemes, including the transmission of malware, fake anti-virus software, spam, and botnets to unwitting victims, and he received notices from Internet governance entities (such as Spamhaus) that his servers were hosting the malicious activity. Nonetheless, Sahurovs admitted he took steps to protect the criminal schemes from being discovered or disrupted and hosted them on his servers for financial gain.”
ChronoPay Tied to Massive Scareware Campaign
ChronoPay, a Netherlands-based company that was once hailed as Russia’s largest online payment processor, was tied to various scareware schemes. This includes Apple-focused scareware threats like MacSecurity and MacDefender.
A report by Brian Krebs of Krebs on Security shows that ChronoPay was a major player in the fake antivirus and scareware market as a whole. In addition to handling payments for many well-known and controversial scareware and fake antivirus companies, ChronoPay also paid for their support and hosting as well. Krebs, who reports having access to leaked ChronoPay documents, says that the documents indicate that ChronoPay itself owned many such scareware companies and paid for their domain names and other operations.
Some of those companies and domains ChronoPay used include:
- Martindale Enterprises Ltd.,
- Shield-EC,
- Trafficconverter.biz,
- Pandora Software and its tech support company Innovagest2000,
- Yioliant Holdings,
- Flytech Classic Distribution Ltd.,
- Creativity-soft.com, and
- Software-retail.com.
How Does Scareware Work?
Not sure how a scareware scam works? Basically, it involves using social engineering-based tactics to manipulate people into downloading or buying software. Now, the software could be harmless; but in some cases, it could be downright nasty and malicious. In either case, the goal is to get victims to pay the scammer or get them to install software by eliciting fear and a sense of urgency.
Here are some common methods that scareware operators (hackers) use to carry out their scareware attacks and to distribute malware:
- Pop-Ups: We’ve already talked about this, but pop-up messages and alerts are a common way for cybercriminals to deploy scareware.
- Malvertising: Malvertising = malicious advertising. In the case of scareware, hackers use third-party ad distributors to display phony or malicious ads on websites (with or without their knowledge). The cybercriminals spread various types of malware, including scareware displaying fake antivirus advertisements on reputed websites and apps via malvertising.
- Downloads/Installations: The hackers lure the victims by offering free goodies — such as software, songs, images, videos, PDF files of popular books, etc. — and hide scareware malware inside them. They might also make replicas of popular apps and software to trick users into downloading them instead of the legitimate ones.
- Phishing Emails: The attacker sends you a phishing email with a warning that your device is infected and offers you rogue antivirus software or tech support. They might also send you emails impersonating a company or person you trust and send the scareware malware as an attachment. The attachment looks like a benign purchase receipt, transaction document, business file, or free media file. But when you click on it, scareware downloads onto your device.
- Infected Websites: The attackers make websites that capture user’s attention, and when users visit such sites, the scareware pop-ups take over the screen.
What Happens to the Scareware Victims?
Let’s find out what happens if you fall for such a scareware attack.
1. You get useless software. Okay, while it’s not ideal, this isn’t as bad as some other scenarios that we’ll talk about momentarily. With this type of scareware, you end up paying for fake and worthless software that doesn’t perform any of the promised malware detection and removal services.
2. You pay money for fake tech support. You might make the call on the given number, they provide the fake virus removal service (fake because your PC is not infected in the first place), and you pay for it.
3. Cybercriminals steal your payment card info. When you make a payment for buying the fake antimalware software or tech support, the hacker steals your payment card number or bank details. They misuse this data to deploy financial fraud in the future.
4. Cybercriminals steal your personally identifiable information (PII). Before buying the fake software or service, you might be asked to fill a form with your PII such as name, phone number, physical address, email address, date of birth, type of device you are using, etc. Sometimes hackers collect this information and sell it to marketers or other hackers on the darknet.
5. You install malware onto your device. Like the last example, this scenario also spells disaster for you. The fake antivirus program itself can be a malicious trojan horse. Once you install it on your device, cybercriminals can:
- Use your device as a botnet to execute other cybercrimes.
- Install spyware that takes a screenshot of your activities and blackmail you into leaking your sensitive data if you don’t pay the extortion money.
- Steal your credentials and other sensitive information.
- Install ransomware on your device that encrypts the files or locks the device and allows them to demand ransom to get back the access.
- Spread malware to all of your other files, software, applications, and the operating system.
- Spread virus via your Wi-Fi and infect other connected IoT devices on your network.
- Take control of your email client and send a phishing email to your contacts.
- Access your social media profiles and send malware-loaded attachments to your friends or ask them to transfer money from your profiles.
How to Protect Yourself Against Scareware
Follow these steps if you encounter scareware.
1. Install Robust Security Software on Your Device
A security software (i.e., antivirus, antimalware, antispyware, firewall, etc.) is your first line of defense against scareware. It scans your device in real-time, detects, and removes many types of malware, including scareware. When you accidentally or intentionally try to visit a scareware-laden site, the good security software blocks these websites and downloads or shows you an alert notification.
2. Use Common Sense
Just because you see a pop-up window, email, or an ad banner telling you that your device is infected with viruses, you shouldn’t automatically believe it. Never download or install any unknown security software or call tech-support number believing such pop-ups even if you see signs of malware infection. Instead, download and scan your device for free only with some reputed and trusted antivirus programs like Comodo Antivirus.
3. Close the Window and Quarantine Your Device
Don’t use the “X,” “cancel,” or “close” buttons to close the window. It might trigger automatic malware downloads. Instead, close your browser by pressing Ctrl-Alt-Delete. If you see a scareware window and can’t get rid of it, disconnect your device from Wi-Fi and all other connected IoT devices (like your printer, scanner, router, etc.). Then, open the device in safe mode and scan it with a trusted antivirus program. If that doesn’t work, you can turn your computer to a reliable tech-support center or professional in your area.
4. Wipe Your Device’s Memory
This should be your last option and is something you can employ if you have scareware on your device. Use it if the scareware infection is spread in a way that you can’t open any files, browser, or access anything, and the security program and tech support professional can’t solve the issue. By wiping out the device’s memory, you will lose all the saved data of your device and won’t be able to recover anything after that. But on the other side, you will be able to get rid of all the scareware traces and save your device.
To reset your phone to its factory settings, select the phone manufacturer to follow the reset steps:
Final Words on Scareware
Not everyone is tech-savvy and aware of various cyber threats. But after reading this article, you know what scareware is and that if you see a potential scareware notification, you shouldn’t panic or make a fear-based decision. The best defense against the scareware is to:
- Be vigilant,
- Not click on or otherwise engage with unsolicited messages or pop-ups, and to
- Use a strong antivirus/anti-malware solution.
Be sure to share this article with your friends and relatives so that they know what scareware is and so they can explore the scareware examples and take rational steps if they encounter these scam tactics.














 (17 votes, average: 4.29 out of 5)
(17 votes, average: 4.29 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security