How to Implement Continuous Threat Exposure Management (CTEM) Within Your Small Business
Go beyond traditional threat detection to learn how to implement continuous threat exposure management within your small business in 5 steps and achieve robust cybersecurity
The world’s economy has slowed down in 2024, leaving businesses and individuals with less money in their pockets. But business is booming for bad guys. In the first half of the year, Perception Point recorded a 24% increase in cyber attacks per employee, while Chainalysis tracked over $459 million in ransomware payments to cybercriminals’ crypto wallets.
Organizations are scrambling to patch vulnerabilities and mitigate damages. However, staying on top of new threats and an ever-expanding attack surface can be challenging, especially for small businesses (SMBs) with limited budgets, personnel, and other resources.
So, can the holistic approach offered by continuous threat exposure management (CTEM), a process enterprises choose to enhance security and minimize risks, help SMBs balance effective resilience and efficient operations, too? Spoiler alert: Yes, it can.
How? This is what we’re going to find out. Keep on reading to learn what CTEM is, examine its value, and explore how small companies like yours can implement it.
What Is Continuous Threat Exposure Management (CTEM)?
Did you know that 94% of your business’s critical assets can be compromised in four steps or less?
Continuous threat exposure management (CTEM) is typically a set of automated processes that helps organizations proactively assess, identify, and address cybersecurity risks before attackers can exploit them. This is done through continuous systems and network monitoring with the goal of hardening your attack surface.
This strategic approach was introduced by Gartner in 2022. The thought behind it is to help businesses assess threats from the perspective of mitigating exposures rather than focusing on stopping events. While CTEM is generally viewed from an enterprise perspective, its structured approach enables organizations of all sizes to prioritize potential threats and remediation efforts effectively.
Here’s a quick overview of the process:
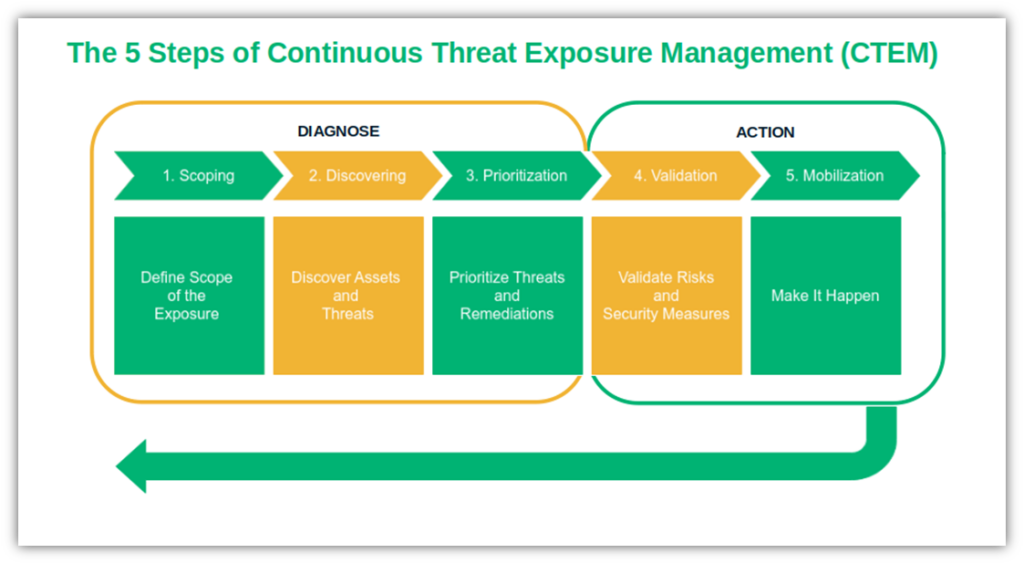
This can be a blessing for small businesses (SMBs), which are often unable to fix every issue due to limited budgets and insufficient personnel to correctly identify and prioritize remediation actions.
How SMBs Can Implement Continuous Threat Exposure Management
CTEM is an iterative five-step program that’s generally divided into two phases:
- The diagnosis phase. This process includes scoping, discovery and threats prioritization.
- The action phase. This period encompasses the validation and mobilization processes.
As an SMB owner, let’s see how you can implement each step without breaking the bank.
CTEM Implementation Step #1: Scope Your Organization’s Attack Surface
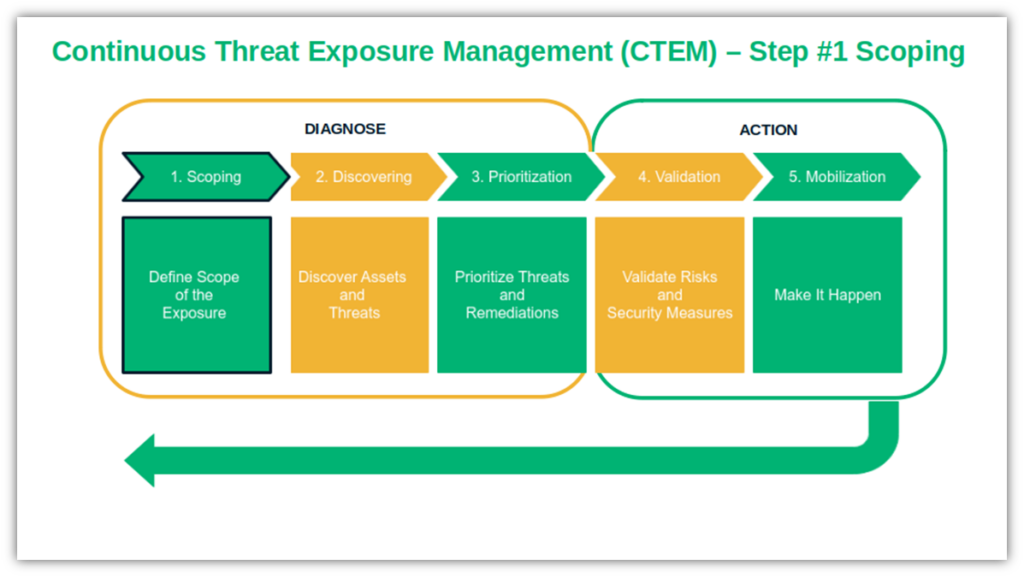
Identify the most important assets to include in your first cycle of continuous threat exposure management. Segmentation is key, so don’t go wild. As a small business, you won’t be able to address everything — not even large corporations can — so focus on the one area you consider most at risk. You don’t know where to begin? Maybe follow Gartner’s suggestions and start with the external and SaaS threats.
Ask yourself, “Which area of my business is the most at risk?” Your internal network could be the answer. If compromised, attackers could gain a free ride throughout your whole system. A favorite example that comes to mind is the Casino heist stemming from an insecure smart fish tank that was connected to its network.
If you go for it, don’t limit your list to only the devices accessing the network. Incorporate less obvious elements, such as:
- Credentials (e.g., usernames and passwords),
- Stored sensitive customers’ information (e.g., personal information such as social security numbers, addresses, and credit card details),
- Databases,
- Stored PKI assets such as personal authentication certificates and cryptographic keys.
CTEM Implementation Step #2: Discover and List all Vulnerable Assets
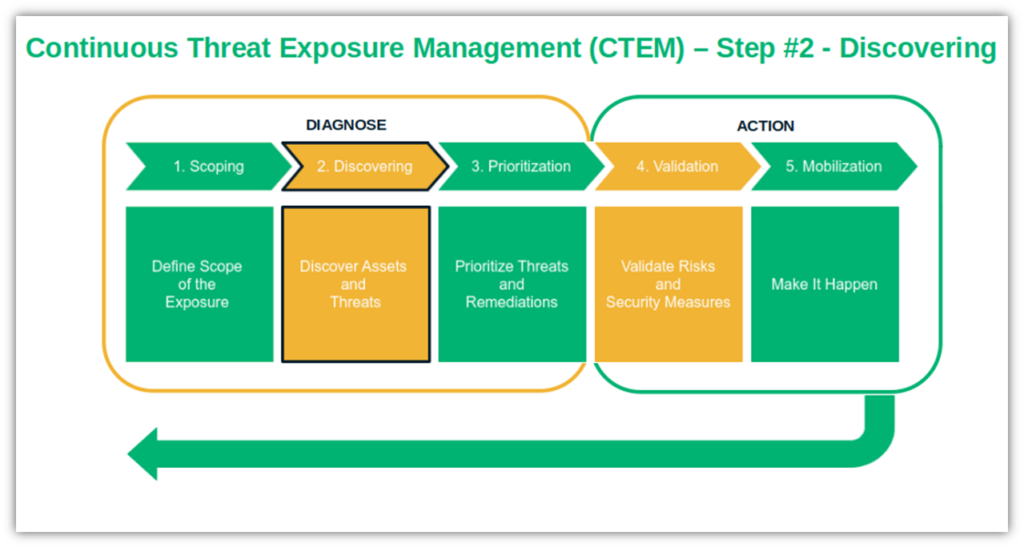
OK. You’ve identified your most vulnerable entry points and assets, but are you sure that you’ve listed them all? Double-check it. This section will help you view your organization’s attack surface from the hacker’s point of view and detect forgotten or otherwise neglected assets, vulnerabilities, and risks.
Let’s say you’ve decided that your internal network is your most critical or weakest link. Now, put your hacker hat on and consider how to take advantage of it as part of your discovery process. You could exploit
- Known common vulnerabilities and exposures (CVEs),
- Outdated or unpatched software programs,
- Exposed cryptographic keys or other secrets, or
- Incorrectly implemented passwordless solutions.
Unsecured connections that use HTTP instead of the more secure HTTPS protocol could expose the network to dangerous data breaches and other attacks.
Is your list too long? That’s okay. The next step will help you refine it allowing you to concentrate on the essentials.
CTEM Implementation Step #3: Prioritize the Most Exploitable Threats and Their Impacts
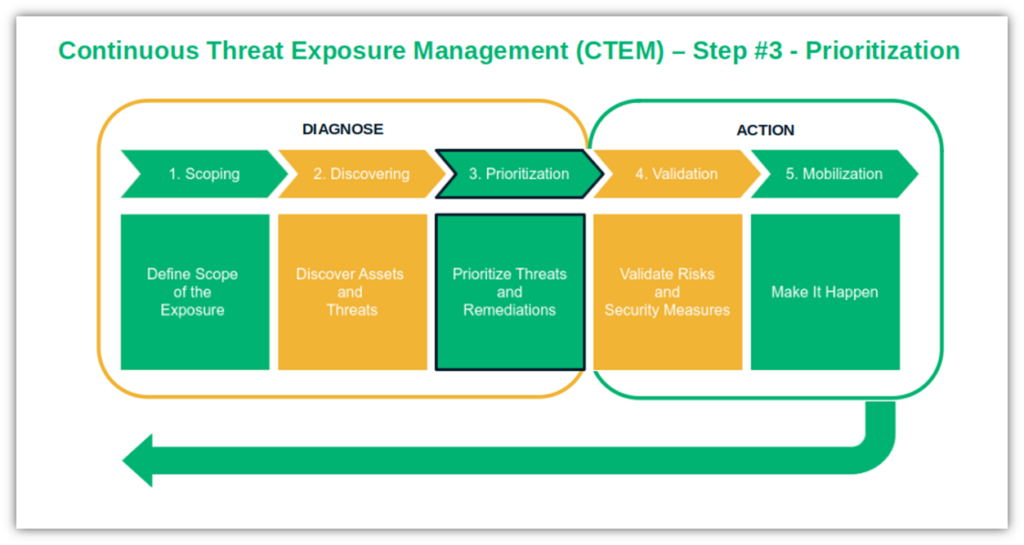
Time to prune everything that isn’t critical from the list you’ve created in step two. Does this mean that lower-priority threats don’t matter in continuous threat exposure management? Of course not. It just means that items that don’t make the first cut can be addressed further down the road. This way, you can focus on taking care of the most pressing issues that will impact your operations sooner than later.
Prioritizing threats means acknowledging not only each threat’s severity score but also:
- How likely the flaw is to be exploited,
- The security defenses (and resources) available, and
- The potential impact on your company’s reputation, finances, and operations.
Have you ever wondered what would happen to your business if all your data disappeared overnight due to a ransomware attack or another disaster that could lead to a data breach? These are the types of questions you should ask yourself to make the most of your resources and focus on the threats posing the greatest danger to your organization and customers.
So, if you concentrate on your network’s security, you may discover that an employee clicking on a single phishing email could damage your company more than the legacy software used only once a year.
Thus, you could train your staff to recognize phishing attacks and invest in email signing certificates for your email client. Attaching a digital signature automatically to every email can help your employees know whether a dodgy email has been sent by one of their peers or by a bad actor.
CTEM Implementation Step #4: Validate How Attackers Exploit Flaws & How Your Systems May Respond
It’s action time! Now that you have a clear and comprehensive picture of your priorities and the potential countermeasures, it’s time to:
- Verify the threats you’ve identified are correct,
- Identify specific ways that an attack can exploit your vulnerabilities, and
- Determine whether the mitigation actions are good enough to protect your organization from those risks.
OK, we get it. Most SMBs don’t usually have a pen-tester in their teams that can simulate attacks and test remediation theories. Heck, many don’t even have a “team,” period. But there are plenty of alternatives out there that can do the trick. Certain ones might be better than others, but you’ve sometimes gotta work with what you’ve got. Pick the approach that’s right for you and you’re good to go.
- Automate the whole thing. Scan your servers and websites with automated website security scanning tools. Even the most expensive plan will cost you less than a cuppa at your favorite coffee shop.
- Let somebody else do it. Hire an external ethical hacker to run pen tests. Are social engineering attacks among your top worries, but you can’t afford a white hat? Opt for a red teaming as a service solution.
- Make do with what you have. Can’t invest a penny? Get one of your developers to leverage the free pen tester tools and resources available in the digital world.
Review the results and draft a continuous threat exposure management remediation plan. This will ensure you won’t waste your limited time and resources addressing the wrong issues.
CTEM Implementation Step #5: Mobilize Your Processes and Teams
There you have it. At this stage, your continuous threat exposure management plan should be ready to share with your cross-team peers to get them on board. Don’t take all the weight on your shoulders, though. Top management should be the driving force behind this initiative.
Ensure everyone understands their roles and the CTEM plan’s objectives. Once done and dusted, you can start assigning tasks and allocate resources to implement the agreed security measures.
Is basic cyber security staff training part of your action plan? That’s a step in the right direction. Did you know that 26% of organizations surveyed by Hornetsecurity don’t offer any security training to their users? That’s crazy when you consider the scale of potential damage and the number of ready-to-use online courses for SMBs available on the internet. Some are even free.
The Implementation of CTEM Is Just the Beginning of an SMB’s Road to Security
Hey, you made it. You’ve implemented continuous threat exposure management within your small business without breaking the bank. Remember, though, CTEM’s unique characteristic (and advantage) is that it’s an iterative process. In other words, you should continuously repeat these five steps to refine and adjust your security posture.
You don’t have the time, personnel, or financial resources? Automate as much as you can. But before you do that, let’s discuss what you get in exchange.
6 Benefits of CTEM vs. Traditional Vulnerability Management for SMBs
ESET reports that 44% of Asia Pacific (APAC) SMBs’ cyber security incidents stemmed from poor security defenses.
Implementing a continuous threat exposure management program can fix that by expanding past the traditional vulnerability management devices and providing end-to-end visibility of assets, attack paths, and potential solutions. This is already a great advantage. However, it does more than that. With CTEM, you can do the following:
1. Address Vulnerabilities Before the Worst Happens
CTEM revolutionizes the way you manage vulnerabilities. It’ll enable you to:
- Automatically and proactively monitor your systems and infrastructures.
- Identify potential issues.
- Preemptively address these problems before attackers can exploit them.
For instance, isn’t it better to spot that your online payment page SSL/TLS certificate will expire soon instead of finding it out when it’s already too late?
It’ll give you enough time to renew it without jeopardizing your customers’ credit card information being stolen by a man-in-the-middle (MITM) attack. Tools like SiteLock will automatically scan your SSL/TLS certificates to ensure they’re valid. SMBs with a slightly bigger budget can also opt for Sectigo Certificate Manager, a platform that automates certificate management processes from A to Z.
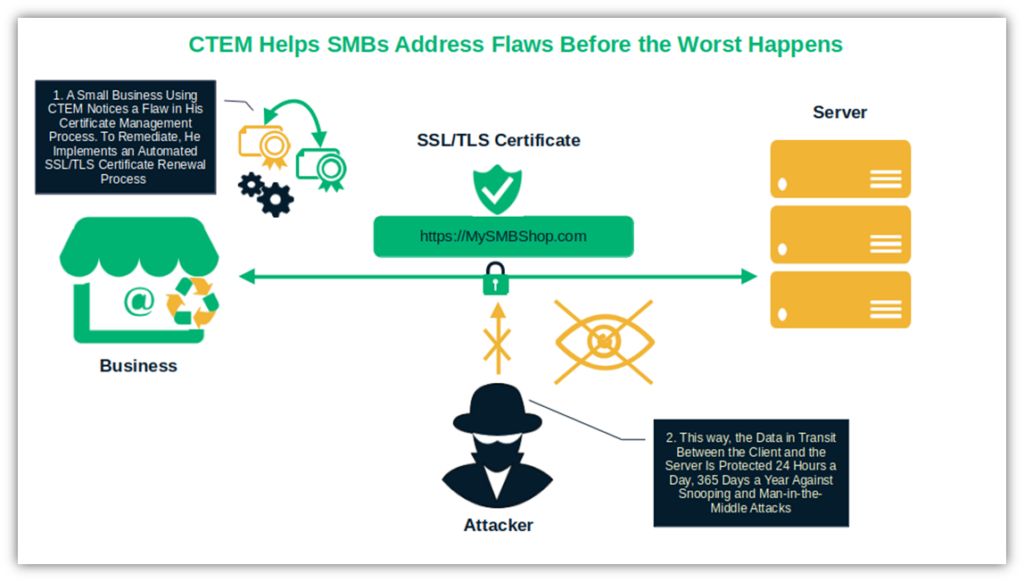
2. Focus on the Entire Attack Surface (Including Your Supply Chain)
99% of the world’s largest companies polled by SecurityScorecard work with vendors that suffered a data breach between Q4 2022 and Q1 2024. Why does it matter? SMBs love to use third-party vendors, so there’s a high chance that you could be impacted, too. For example, you might use a simpler (and cheaper) version of a software program that a vendor sells to their enterprise customers.
Moreover, the latest CybelAngel report shows that 79% of cybersecurity hazards lie outside the company’s internal IT. Think about your social media pages or the software as a service (SaaS) applications you use that can hide security threats, too.
Continuous threat exposure management goes beyond identifying simple internal technical threats. It helps you detect issues from other sources such as employees sharing sensitive information on social media or an unsecure SaaS app.
3. Prioritize What Matters
When comparing the six-month period between January and July, the number of reported CVEs went from 17,114 in 2023 to 22,254 in 2024. That’s roughly a 30% increase year over year. No company can eliminate all of its exposure risks, let alone an SMB with a limited budget.
However, by using continuous threat exposure management, you’ll create actionable improvement plans that prioritize fixing the threats that pose the greatest risks to your business and assets. For example, if ransomware and malware are at the top of your vulnerabilities list, you could add an automated backup tool such as CodeGuard Backup and a website scanning software like Sectigo SiteLock to your remediation plan.
4. Comply With Privacy and Security Regulations
Don’t you just love crispy baguettes? French bakers are masters of artisan bread making. But they, too, must comply with regulations, no matter how small their businesses are.
In June 2024, a French baker was slapped with a €5,000 fine by the French Data Protection Authority because he did not comply with a principle of the European Union (EU) General Data Protection Regulation (GDPR) regulating video surveillance data processing.
Would continuous threat exposure management have helped in this case? Yup, absolutely. The same solution would also help SMBs handling online payments that must comply with the new PCI DSS 4.0 and 4.0.1 requirements.
5. Save Money
CTEM won’t only help you avoid regulations and hefty fines, but it’ll also reduce the chance of cybersecurity incidents and their costly consequences. We’re talking about everything from ransomware payouts to lost customers and sales due to a poor reputation.
We live in tough times. The average ransomware payment has increased by a terrifying 500% in just one year (from 2023 to 2024, according to Sophos). The average recovery costs have skyrocketed to $2.73 million, up from $1.82 million the previous year.
Continuous threat exposure management might not save you from everything. However, if implemented correctly (more about that in a moment), it can make the difference between the life and death of your business.
6. Help You Leave No Stone Unturned
As we’ve just learned, CTEM is an iterative process. This means that it doesn’t stop traditional automated periodical scans. It empowers you to continuously assess readiness for critical threats and validate mitigation solutions.
Leveraging the power of automation, you’ll identify new areas of improvement and achieve a constant refinement of your defenses.
For instance, not many companies would consider GitHub a threat to the security of their software development projects. However, the platform is being exploited to spread malware through fake code fixes suggested in the comment section.
Is CTEM not your cup of tea? Check out these alternative solutions:
- The recently released National Institute of Standards and Technology (NIST) update to the Cybersecurity Framework (CSF) for SMBs.
- Our free SMB cybersecurity plan template.
- Our top 25 security recommendations for SMBs.
Final Thoughts on How to Implement Continuous Threat Exposure Management as an SMB
Just because you’re a small business, it doesn’t mean you can’t enjoy and provide your customers with a good level of security. A continuous threat exposure management approach that’s tailored to your needs can help you overcome many obstacles and constraints SMBs typically encounter.
Start looking beyond common vulnerabilities and exposures:
- Focus on finding the weaknesses in your critical assets and systems that can be remediated,
- Validate potential impacts and scenarios,
- Prioritize risks based on your business’s specific needs,
- Get ready to remediate,
- Learn the lesson, adapt, and repeat.
You can’t fix or prevent every bad thing from happening — no one and nothing can. However, implementing an SMB approach to CTEM can help you tackle what matters most and reduce your organization’s threat exposure risks.





















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security