What Is Vulnerability Management? A Look at the Vulnerability Management Process
Unpatched vulnerabilities are the cause of 60% of total data breach incidents, ServiceNow reports. Explore how vulnerability management can protect your organization from such security disasters.
Edgescan reports that the average mean time to remediate (MTTR) vulnerabilities is 60.3 days. But it’s not just new vulnerabilities that pose risks to your organization, customers, and data — their 2021 report shows that vulnerabilities and exploits dating back to 2015 are regularly used in ransomware and malware attacks.
Now, we don’t want to scare you, but we can’t ignore the fact that once a cyber attack takes place, the process of detection, remediation, restoration, and the subsequent investigation that follows are complicated and expensive. Furthermore, falling prey to cyber attacks and other vulnerability exploits can cause a load of compliance-related issues and ruin your organization’s hard-earned reputation.
Needless to say, it’s better to prevent such attacks’ occurrence in the first place. One of the best ways to do so is to find and fix the weak areas of your IT infrastructure before a hacker exploits them for deploying an attack or getting unauthorized access to your system. The processes of assessing the assets, finding the loopholes, and remediating those vulnerabilities within your environment fall under the umbrella of vulnerability management.
In this article, we’ll answer the question, “what is vulnerability management?” We’ll also explore how it differs from vulnerability assessment and how the vulnerability management process works in general.
What Is Vulnerability Management? A Definition & Explanation
Vulnerability management is the continuous process of identifying, prioritizing, and remediating security vulnerabilities within your IT environment. Vulnerabilities mean weak areas in your defenses, processes, and employees’ knowledge that attackers can exploit to get unauthorized access to your sensitive systems and perform unauthorized tasks. As you can imagine, this is a pretty broad list. Examples of vulnerabilities include:
- Software bugs and errors,
- Unprotected databases,
- Misconfigurations,
- Lack of proper authentication mechanisms,
- Unsecured physical spaces,
- Insecure networks,
- Open ports,
- Weak encryption (or a lack thereof),
- Employees who lack cyber awareness, and
- Missing security software in devices, etc.
Vulnerability management is a set of functions and responsibilities that can be handled by your in-house team (if you have the skills and resources available) or by outsourcing the work to a third-party service provider.
What Vulnerability Management Helps You Do
During the vulnerability management process, you must identify and analyze all of your assets to figure out where there are weak areas (attack surfaces) that attackers exploit and fix those vulnerabilities before the hacker finds them. So, vulnerability management’s main purpose is to be one step ahead of the attacker.
In short, the vulnerability management process is a series of routine checks that include several key tasks:
- Detecting and identifying existing vulnerabilities,
- Prioritizing which vulnerabilities to address first,
- Remediating those weaknesses,
- Verifying that those vulnerabilities have been mitigated, and
- Reporting the vulnerabilities that have been eliminated.
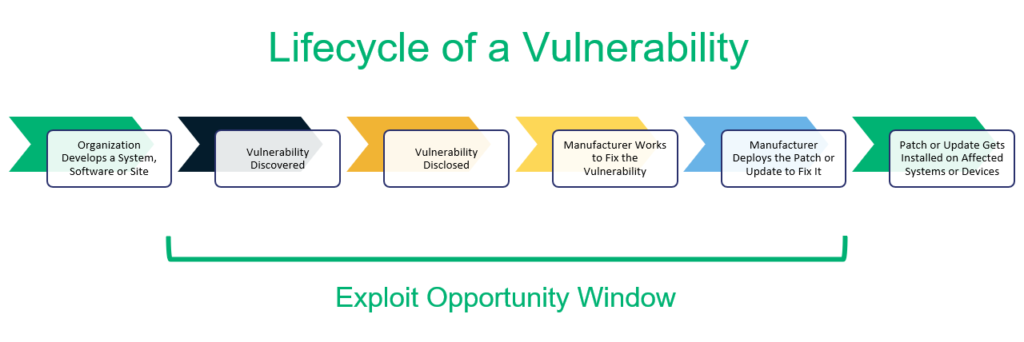
Vulnerability Management vs Assessment — What’s the Difference?
Please note that vulnerability management is different than a vulnerability assessment. You’ve probably heard these terms used interchangeably, but it’s important to note that they’re related but not the same.
Vulnerability management is a continuous process of detecting, prioritizing, patching, reevaluating, and reporting vulnerabilities. In contrast, a vulnerability assessment is a one-time project with a limited scope. It’s done periodically with a specific starting date and end date. Once the vulnerabilities are detected, the IT team:
- Analyzes their risk level,
- Prioritizes them according to the threat intensity, and
- Suggests recommendations.
However, a vulnerability assessment doesn’t include actually implementing the mitigation strategies. Nor does it involve reevaluating whether those vulnerabilities have been mitigated and reporting the steps you’ve taken. As such, vulnerability assessments are just one component of an organization’s overarching vulnerability management program.
A Look at the Vulnerability Management Process (Framework)
Please note that there aren’t set universal standards when it comes to vulnerability management, as each program is customized as per the organization’s needs and threat surface. So, software vulnerability assessment steps can be different from physical premises’ assessment or employees’ cyber-awareness inspection. But these are some common steps involved in the vulnerability management process in a variety of applications.
1. Discover What You Have and Where Everything Is Located
Shadow IT is a looming threat when it comes to your organization’s cyber security. Any devices and applications that you don’t know about increase your organization’s attack surface. This is why companies should assess their existing assets to decide where they need to deploy vulnerability assessments. Some areas where you’d carry out include,
- Ports
- Network
- Devices
- Servers
- External facing and intranet websites
- Databases
- Logs
- IoT devices
- CMS
- Operating system
- Physical premises
- Social media accounts
- Email clients
- Living assets (i.e., employees, vendors, suppliers, and other stakeholders)
Inventory discovery involves both system scans and network scans (scanning all the devices connected to the company’s internet network). Companies should perform this step periodically at regular intervals to ensure no new devices are left out and to detect the unauthorized connection to the network at its earliest stage.
2. Prioritize Which Areas to Focus on First
Organizations decide which items pose more risk and prioritize them in the vulnerability management process. To prioritize, they generally assign values to each component, measure the exposure, and decide the threat level. Organizations might not put everything under surveillance due to budgetary constraints, lack of security staff, or lack of proper methodology, tools, or technology to do so.
3. Assess and Carry Out Vulnerability Detection and Identification Processes
Once the priorities are set out, vulnerability scanning takes place. To do so, companies need to decide on a risk baseline as a reference point and a methodology for assessment (i.e., tools, technology, scanners, and techniques).
Most of the time, an automated scanner tool keeps scanning each asset to detect vulnerabilities. But this isn’t the only way that companies should look for vulnerabilities. Many companies periodically also do pentesting, red-team exercises, and hold bug bounty competitions to find vulnerabilities.
Before starting the assessment process, management needs a thorough analysis of each method’s pros and cons, ROI, chances of false positives, workload, and result accuracy.
You also have to decide:
- Whether your current security staff will do this job,
- If you should hire a specialist in-house team for it, or
- Whether to outsource this work to a third-party vendor who provides vulnerability management as a service program (VMaaS).
4. Prioritize and Remediate the Vulnerabilities You Find
After the vulnerabilities are found, the security team analyzes them to understand their risks and to prioritize them based on their potential threat level. The team decides the tools, techniques, time, and the cost it will take to address the vulnerabilities.
There are some tools available that patch the vulnerabilities automatically. For other types of bugs, manual intervention is needed.
Some of the common remediation steps are
- Make changes in the codes
- Fix any misconfigurations
- Change or update your user access and authentication settings
- Install the latest versions of third-party applications and software
- Remove malware from the devices, cloud, website, and apps
- Make changes in your on-prem security
- Remove weakness from the validation and sanitation features for public-facing forms and login fields
- Encrypt the confidential pages, databases, files, etc. with a robust authentication method
- Change settings in the firewall or security software to block phishing sites and malware-laden downloads.
Of course, there are many other ways the patching needs to be done depending upon the type of vulnerabilities.
Note: Some vulnerabilities possess negligible risk but fixing them can cause more hassles and expenditures. Others belong to third parties such as vendors. (For example, a vulnerability in third-party plugins or operating systems.) Since your company can’t fix the issues yourself, it’ll require you to reach out to those organizations directly. Management generally has no other choice than to accept them, to reach out to those organizations, or to choose an alternate platform or vendor.
5. Verify the Vulnerabilities Have Been Mitigated
Once the vulnerabilities are addressed, your team revaluates the results to confirm that the remediation steps have been applied correctly. If the number of vulnerabilities is large, management randomly selects a sample percentage of systems to test.
In general, management rerun the same tests from which the vulnerabilities were found in the first place. So, for example, if certain vulnerabilities are found during penetration testing, the same tests are run after the patching is done to ensure the vulnerabilities are lessened or removed.
6. Report Key Items Relating to the Vulnerability Management Process
After the vulnerability has been patched, the security team prepares reports for higher management and also for compliance purposes. This is a continuous process that comes at the end of each vulnerability assessment.
Although each organization has different methods of making reports, these are some common inclusions.
- List of vulnerabilities found. It includeswhere (cloud, third-party apps, servers, etc.) and why the vulnerabilities took place, i.e., weak passwords, software coding bugs, employees’ lack of cyber awareness, etc.
- Risk analysis report. Risk means the extent of damages the vulnerability can do. Its general formula is Risk= threat * vulnerabilities. Some companies use a scoring system, in which they devote points to each vulnerability according to its level of causing harm and discrepancies.
- Remedial steps. It includes which steps the security team took to fix the vulnerabilities, the difficulty level of each corrective step, and the cost involved.
- Comparison report. It includes the effectiveness of corrective actions.It shows the result of the reevaluation and whether the risk has been either lessened or eliminated. It’s like a “before-after” report.
- Patterns and recurrence prevention steps. The security team finds the root cause, shows the repeating vulnerabilities to find a pattern, and suggests the steps to prevent future occurrences.
Conclusion of Vulnerability Management
Hackers are continuously upgrading themselves and finding new innovative ways to hack the organization. Your vulnerability management program must be highly customized and meticulously planned. 24/7 automatic scanners are useful because they can find some of the quick vulnerabilities.
The reality is that a hacker needs to be correct just one time — it requires only exploiting one loophole to penetrate your organization’s IT infrastructure. Hackers are real humans with their own logic, motives, and goals. So, you need the pentesters, threat hunters, and a security team that understand human behavior and how to find vulnerabilities. Hence, a hybrid approach of both machine- and human-based intelligence is the key to making an effective vulnerability program.





















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security