7 Cyber Security Basics Every SMB Should Know
Stop flying blind. Nail the top SMB cyber security basics in less than five minutes, even if you’re an absolute beginner…
78% of SMBs are concerned that a cyber attack could put them out of business. Do you feel the same but have no idea where to start to protect your data, customers, and often cloud-based systems from the bad guys?
We’ve compiled the most important cyber security basics you need to know, jargon-free. Ready to go from a cyber security rookie to a cyber-aware business owner? Let’s go.
Cyber Security for SMBs — Is It Necessary?
In a word: ABSOLUTELY. In 2023 alone, 73% of Asia Pacific-based SMBs were victims of at least one cybersecurity incident. Many of those incidents (44%) were caused by poor security measures. In the U.S., nearly 47% of SMBs were breached due to a stolen password.
Such incidents cost money. In its 2024 Data Breach Investigations Report (DBIR), Verizon’s data indicated that median losses for SMBs affected by ransomware or extortion-related crimes were $46,000. That’s an awful lot for cash-strapped small businesses.
Cybersecurity is something SMBs can’t do without. But why would the bad guys target such small prey when they could cash in more by breaching into corporations?
Because they’re easier to catch for several reasons, namely they’re often not as well protected.
7 Cybersecurity Fundamentals You Can’t Do Without
OK, I guess you’ve got the picture. Now, let’s get down to business and learn seven golden rules your SMB cybersecurity basics handbook should include.
Cyber Security Basic #1 — Employees Are Your First Line of Defense
In the digital era, Verizon’s 2024 DBIR reports that 68% of breaches are caused by human-related factors. These are issues that frequent cybersecurity basic training can help prevent. For example, an employee
- downloading a malware-infected attachment,
- revealing sensitive information on social media, or
- being tricked into transferring funds to a threat actor’s bank account.
By the way, training doesn’t have to be boring. A quick search on YouTube shows how password security can become a fun topic if presented the right way to engage your audience. Learn how to unleash your creativity, much like how The Defence Works did in this short, entertaining video about phishing:
Set up small contests (e.g., spot the phishing email) or use gamification to make training interactive. The more you engage your employees and other network users, the more likely they will remember the lessons learned and apply them in their roles.
Cyber Security Basic #2 — Strong Passwords & Access Controls Keep Your Data Safe
Are you still requiring your users to utilize passwords that are at least eight characters long? Sure, that meets the absolute base requirements, but it’s time to take it up a notch. The National Institute of Standards and Technology (NIST) updated its password guidelines in 2024 to recommend a minimum password length of at least 15 characters.
That’s nearly twice as long as its eight-character minimum requirement. But there’s a reason behind it, which I think you’ll understand with our next example. How long do you think ChatGPT takes to crack an eight-character password comprised of numbers, lowercase and uppercase letters, and symbols? According to data from Hive Systems, it can take as little as one second (depending on the hardware and hashing functions used).
Implementing and enforcing a strong password policy helps you secure the following against attackers:
- Applications,
- Systems, and
- Data (including the passwords themselves)
Beware: A password is only considered strong and effective if it’s unique (i.e., only used once). Reusing the same password for multiple sites or applications leaves it vulnerable. If the password gets compromised through any one of those use cases, it means the password is compromised across all of them because it can be used to carry out brute force attacks.
To make it even more secure, use access controls and multi-factor authentication. MFA requires a second form of verification (e.g., a one-time PIN) before granting access to the resource. Want to stop worrying about password cracking for good? Go passwordless.
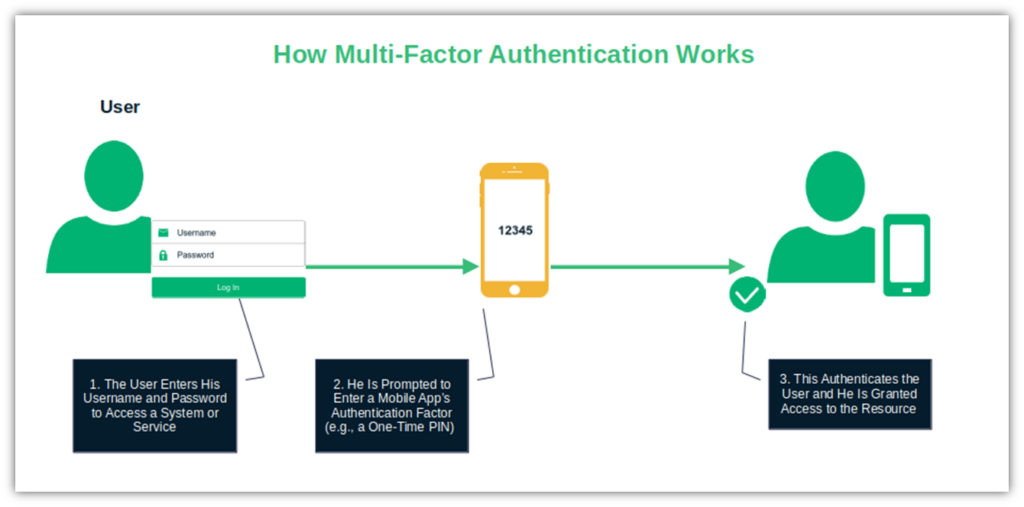
And if, despite all these measures, a cybercriminal does manage to break through — yes, it does happen — implementing access controls (i.e., the principle of least privilege) limits the potential damage by ensuring that people have only access to what they need to do their work.
Cyber Security Basic #3 — Maintaining Up-to-Date Software Keeps Vulnerabilities at Bay
A software vulnerability is like a hole in a physical gate. Even if you can only open the gate without a key from inside, a thief can put his hand through the hole to access the opening mechanism. Bingo, he’s in.
Seal the holes in your gate as soon as you find them. Yes, keeping your software up to date and installing patches can be hard work. However, your diligence will pay off by preventing attackers from exploiting vulnerabilities to access your network, install malware, or modify code.
To eliminate such vulnerabilities, you’ll want to keep all of the following up to date:
- Systems,
- Devices, and
- Any antiviruses and antimalware software.
So, think twice before using that old smartphone to check your work emails. The device might still be working, but old (legacy) operating systems don’t get security updates.
Cyber Security Basic #4 — Encryption Secures Your Communication and Information
Encryption transforms plain text data into indecipherable gibberish that can only be decrypted with a private key. It uses small files (i.e., digital certificates) that contain the owner’s details (e.g., info that verifies the certificate is tied to your identity or company) and are issued by a certificate authority that vetted you.
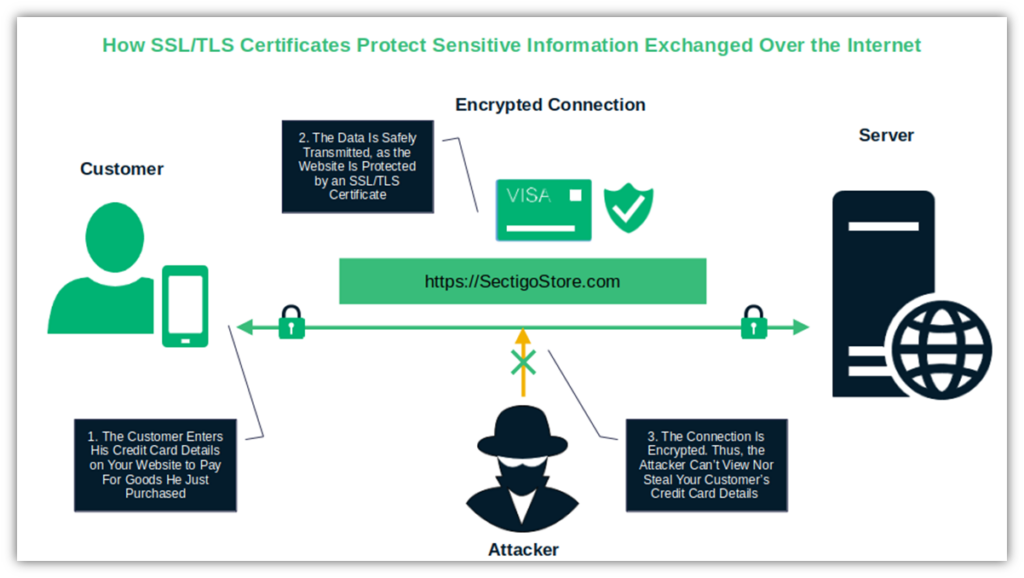
Use a secure socket layer/transport layer security (SSL/TLS) certificate to encrypt and protect data in transit. This will help keep your customer’s sensitive data, such as credit card details entered on your website, secure from cybercriminals’ prying eyes.
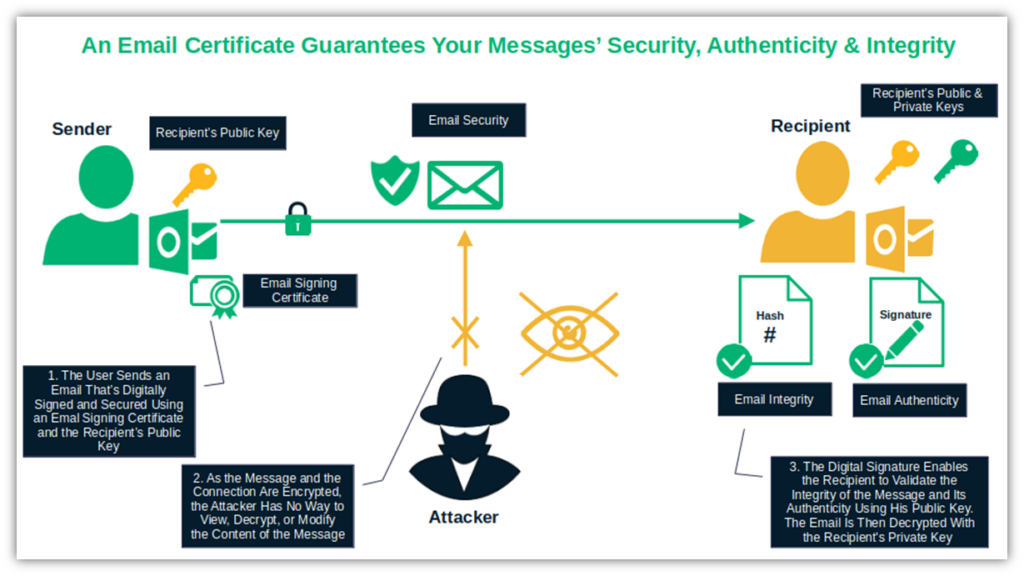
Opt for an email certificate to encrypt your sensitive messages, especially those containing payroll information, customer data, etc. NOTE: This only works if both parties are using email signing certificates. The same certificate will also add a digital signature to each email. (Digital signatures don’t require both parties to have an email signing certificate — only the signer.)
This approach will introduce another layer of authenticity, integrity protection, and security to every email you send.
Cyber Security Basic #5 — Your Network Is Only as Secure As You Make It
Do you use remote security cameras, one or more point of sale (POS) devices, or any smart devices? In the first half of 2024, SonicWall reports that Internet of Things (IoT) related malware attacks increased by 107%.
Of course, good, up-to-date antivirus software and antimalware will shield you from several SMB threats (e.g., ransomware, spam, phishing). But that’s not enough. Critical systems should be on a private, dedicated network, separated from IoT devices and guest access, and protected by firewalls.
Cybersecurity Basic #6 — Backing Up Your Data and Websites Frequently Can Save Your Bacon
In 2024, the percentage of organizations that experienced data loss due to ransomware nearly doubled. The takeaway? Back up your data regularly. You don’t even need to do it manually. Tools like CodeGuard’s backup and restoration features do it for you automatically. This way, if something happens, you’ll be up and running again in a few clicks. It also uses AES 256-bit encryption to add another layer of security to your backup data.
Other tools go even further. For instance, Sectigo’s SiteLock combines antivirus, antimalware, and vulnerability scans with fully automated daily backups of your website files and databases. Install it, grab a cup of coffee, and watch it do the heavy lifting for you.
Cybersecurity Basic #7 — Cybersecurity Isn’t Only About Protection; It’s About Prevention
“Anything that can go wrong will go wrong.” In cybersecurity, “Murphy’s Law” really resonates. The digital world isn’t a place for slackers who don’t take action to ensure their security. Be proactive and set up your safety net (i.e., create plans for incident response, business continuity, and recovery) for when, not if, something goes wrong.
Hopefully, you’ll never have to use them. But there’s a reason why recovery is one of the core functions of the NIST Cybersecurity Framework 2.0. Furthermore, this new framework version was published to address SMBs’ concerns specifically.
Final Thoughts About Cyber Security Basics Every SMB Should Know
So, there you have it. You’ve now learned the most important cybersecurity basics for SMBs. It wasn’t overly complicated, right? What you’ve learned today won’t only boost the security of your SMB and keep it out of trouble; it’ll also increase trust with your customers and business partners and help you improve your brand’s image. Beware, cybercriminals! There’s a new SMB guardian angel in town. Hungry for more? Check out this brilliant SMB Cybersecurity Basics guide issued by the U.S. Federal Trade Commission (FTC).





















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security