Active Directory Certificate Services 101: An Overview
59% of professionals interviewed in 2024 struggle with orchestrating their PKI. Enter Active Directory Certificate Services, which, when paired with the right certificate management approach, empowers even smaller organizations to streamline private PKI responsibilities
Imagine a world where securing your SMB’s communications isn’t too expensive or overly complicated. This would be a place where even the +80% of SMB victims of at least one cyber attack in the 12 months before June 2024 can issue, validate, and manage their digital certificates by establishing their own private–public key infrastructure (PKI).
Is this a dream? Nope. It’s the world of Microsoft Active Directory Certificate Services (AD CS), which is a Windows server feature that’s part of Microsoft’s Active Directory (AD) infrastructure. (NOTE: AD is a critical underpinning of Windows Servers!) AD CS, which enables organizations to establish trust between authenticated users, devices, and systems and secure internal communication channels, is integral to issuing certificates for your Active Directory Domain Services (AD DS) infrastructure.
In this post, we’ll introduce you to the basics of Active Directory Certificate Services and explore what it does, how it’s used, and why implementing it may be a good option for your organization.
What Is an Active Directory Certificate Services (AD CS)?
Active Directory Certificate Services is Microsoft’s answer for an on-prem private PKI platform. More specifically, it’s a Windows Server role that enables organizations of all sizes to implement and manage internal PKIs and the digital certificates they facilitate.
AD CS allows businesses with the resources to set up private certificate authorities (CAs) to issue, validate, new, revoke, distribute, and otherwise securely manage digital certificates that are trusted within their internal networks. When integrated with Active Directory and with relevant Group Policies in place, organizations can use AD CS’s automation capabilities to simplify their certificate management within the Windows ecosystem.
AD CS Is for Private (Non-Public) PKIs
A private PKI differs from a public PKI, which is owned and operated by a trusted third-party CA (e.g., Sectigo). Private PKIs secure internal resources, whereas public PKIs secure public-facing resources such as websites, software, and emails to external recipients.
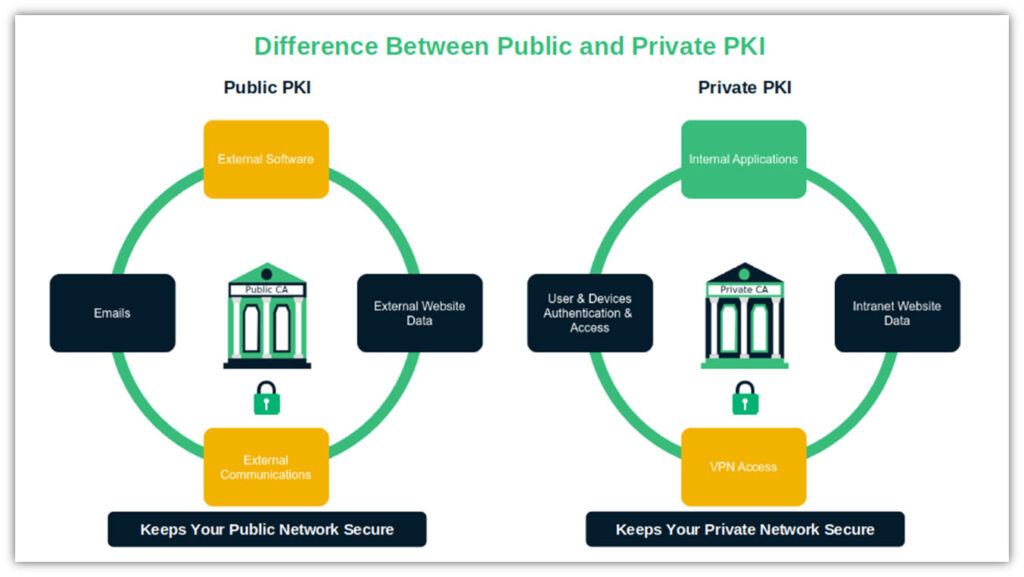
NOTE: The certificates issued by your internal CA infrastructure will only be trusted by the devices, applications, and systems within your AD domain or on devices you’ve manually installed the root CA certificate on. The certificates will not be trusted by anything else! But we’ll get more into that a little later.
Where AD CS Fits Into Active Directory
Certificate Services is strictly responsible for things relating to PKI digital certificates (issuance, management, revocation, etc. AD CS represents just one of several services offered through AD:
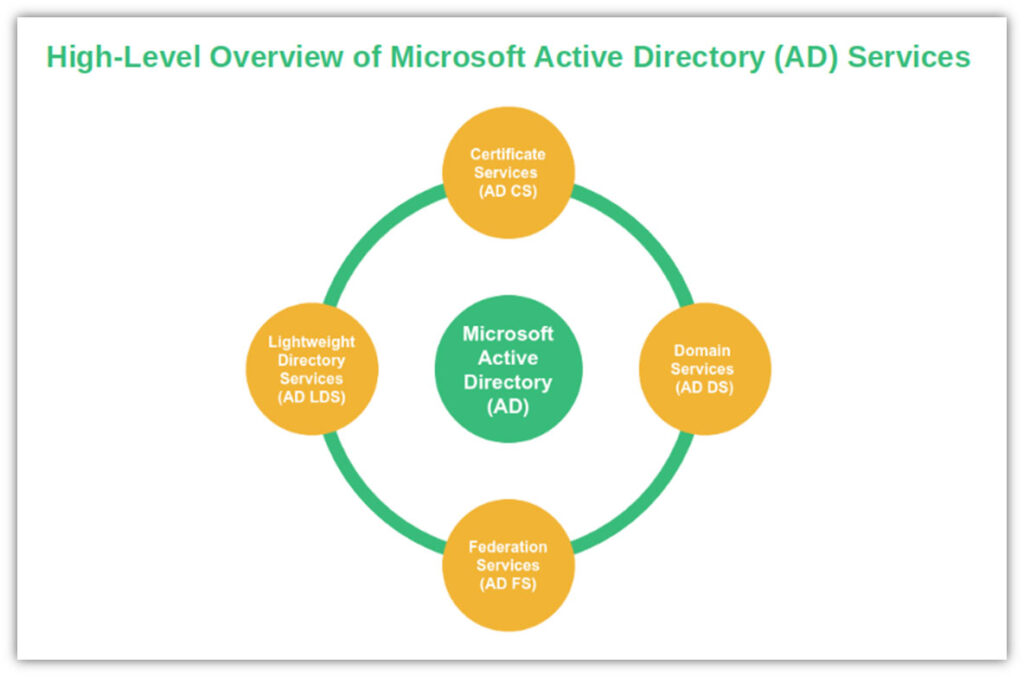
AD CS can be used on its own (though with more limited functionality) or by integrating with AD DS.
Take Your Existing Microsoft CA to the Next Level with Sectigo Private PKI
Sectigo Private PKI is a managed PKI service that complements your Microsoft CA and expands it to protect the non-Windows devices on your networks.
It works with Sectigo Certificate Manager to simplify and streamline certificate deployment and management across all devices and applications within your ecosystem.
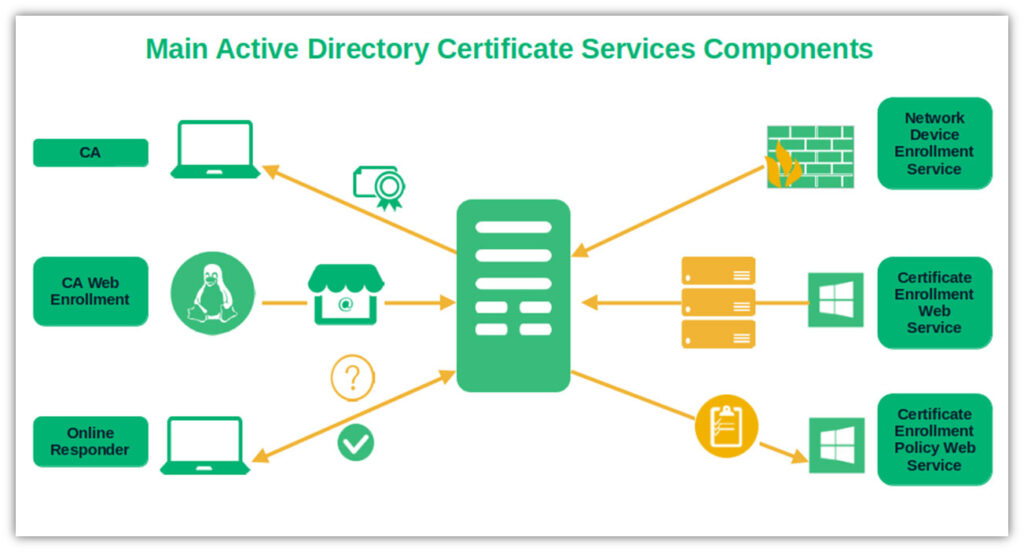
A Breakdown of Integral AD CS Components
AD CS provides different role services, each responsible for specific aspects of an organization’s internal PKI. You can select one or more of these roles when setting up your Certificate Services. Let’s examine these components and what they do.
- Certification Authorities (CAs). The CA root, intermediate, and server certificates create a chain of trust (i.e., hierarchy) that proves that the certificate issued comes from a trusted source. AD CS lets you deploy multiple internal CA hierarchies (i.e., root CAs and issuing CAs that serve as buffers). This way, if one intermediate CA is compromised, you’ll only have to revoke the certificates related to it and not risk the root CA it chains back to.
- Certification Authority Web Enrollment. This service allows you to connect to the CA through a web browser using a secure connection (i.e., HTTPS) to request certificates or revocation lists with devices that aren’t joined to the domain or run on non-Windows operating systems (e.g., Linux). This works in conjunction with the CEP.
- Online Responder. The online responder allows you to configure and manage the online certificate status protocol (OCSP) and get real-time information about revoked certificates. This way, users and devices won’t be able to utilize them within your network. Goodbye, malware infections.
- Network Device Enrollment Service (NDES). This component acts as an intermediary for all those devices (e.g., routers, firewalls, and switches) that don’t support the certificate enrollment process or don’t have AD credentials.
- Certificate Enrollment Web Service (CES). CES acts as a proxy between a Windows device and the internal CA. Users, devices, and applications interact with the CA through CES to automatically perform certificate-related tasks (e.g., certificate requests, renewal, download, and installation) on Group Policy-joined Windows devices. This is useful for organizations looking to reduce the number of deployed CAs, or needing to issue certificates to externals (e.g., remote employees or business partners using Windows devices).
- Certificate Enrollment Policy Web Service (CEP). This service enables users to obtain certificate enrollment policy information. Does your staff use their own devices (BYOD) to do their work? We get it. It saves you money, which is a big plus for an SMB. However, how do you deal with those tricky devices or with unmanaged Internet of Things (IoTs)? The CEP works with the Certificate Enrollment Web Service (CES) to solve these problems. Together, they enable BYOD owners or non-domain joined devices to get certificates for those assets.
What Does AD CS Enable Organizations to Do?
In a nutshell, Active Directory Certificate Services allows an organization to use its Windows Server to deploy the benefits of public key cryptography throughout its internal network(s). AD CS lets you leverage the power of digital certificates (i.e., X.509 certificates) — essentials for secure communication and authentication — to:
- Encrypt data exchanged between parties within your systems,
- Send digitally signed and encrypted emails,
- Digitally sign software and Microsoft Office files to protect them from unauthorized modifications and
- Authenticate and identify users and devices to secure access to your internal resources such as your networks, applications, web apps, intranet sites, and other endpoints.
The beauty of it? You don’t have to buy an additional Microsoft license. You can use the Windows Server license you already have (although large-scale deployments may require additional features.)
However, it’s crucial that organizations take their time setting up Microsoft AD CS to ensure that it’s done properly. At the end of 2023, Microsoft estimated that 30-40% of AD CS deployments had “at least one exploitable misconfiguration of the highest severity.” Furthermore, the NSA and CISA ranked insecure AD CS configurations in the Top 10 Cybersecurity Misconfigurations list the federal security organizations released jointly in October 2023.
How Do Organizations Commonly Use Active Directory Certificate Services?
The Active Directory Certificate Services lets you bind the identities of your users, devices, and services to a unique private key and digital certificate.
AD CS uses Active Directory (i.e., a Windows server acting as a database that stores users/devices/groups within a domain, access permissions, and credentials) to build a PKI to create and manage trusted digital certificates. For best results, this is typically paired with AD group policies.
Each certificate has its use and scope, much like how a driver’s license proves your identity and confirms that you’re authorized to drive. Here are a few examples of PKI certificates you can issue with the Active Directory Certificate Services:
- Secure Socket Layer/Transport Layer Security (SSL/TLS) certificates that protect data in transit. These certificates encrypt the connection between the client (e.g., an employee’s web browser) and the web server via PKI and authenticate the certificate holder’s identity. (Reminder: These certificates are used for internal websites and should never be used on public-facing websites.)
- Code signing certificates that prevent unauthorized modifications and malware infection. Code signing is another digital certificate that software publishers/developers use to sign software and codes. Within your private PKI, it confirms the integrity and authenticity of internal applications.
- Device certificates for highly secure authentication (i.e., mutual authentication) and encryption. They’re used to authenticate and secure all sorts of devices (e.g., computers, routers, smart cards, and IoT) without requiring a password that can be phished (i.e., passwordless authentication).
- Virtual Private Network (VPN) certificates that protect remote access. Implemented to secure and encrypt remote access connections via VPN tunneling or other remote access tools.
That’s a lot of different certificates, right? But how can the Active Directory Certificate Services issue and manage them all smoothly? According to Keyfactor, 83% of surveyed organizations had operational issues due to the exploding number of certificates they had to manage. Keyfactor’s report indicates that surveyed organizations manage an average of 81,139 internally trusted certificates across seven internal CAs.
Without effective automation in place, managing the PKI and certificate lifecycles for all of these assets is virtually impossible. (You’d likely have little to no time to work on anything else.)
Let’s examine how to effectively set up the Active Directory Certificate Services and how it all works.
An Overview of Setting Up AD CS on a Windows Server
We won’t get into the nitty-gritty of the Active Directory Certificate Services installation process here. It isn’t the scope of this article, and there may be slight variances depending on the version of Microsoft Server you’re using and the specific selections and configurations you’ll want to make. However, we’ll provide enough information that’ll give you a general idea of the steps involved.
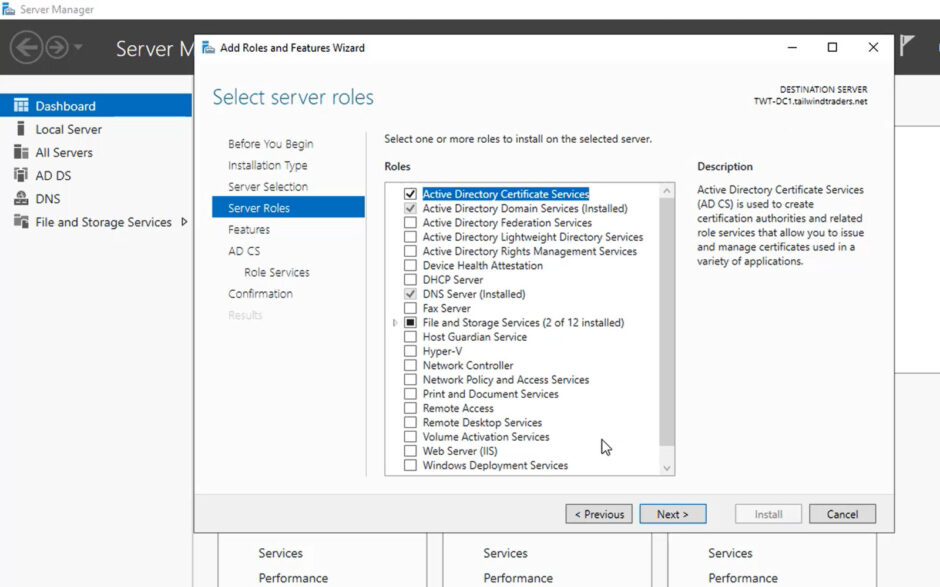
- Launch the set-up Wizard. Start Windows Server Manager and click on Manage and Add Roles and Features.
- Select the installation type. Stick to the Role-based or feature-based installation.
- Pick the server, roles, features, and services. Choose the server where you want to install AD CS. (Note: Avoid installing your root on a domain controller, as doing so outside of a lab environment is dangerous.) Select the Active Directory Certificate Services roles (CA, CEP, CES, Online Responder, etc.) and click Add features to specify them.
- Install the Active Directory Certificate Services. Confirm your selection(s) to install AD CS. This typically involves installing Internet Information Services (IIS) as well.
- Select your post-deployment configurations for your AD CS role services. This process allows you to specify the specific type(s) of CAs you want to create (on domain versus off domain, root versus subordinate), the cryptographic options (key and hash functions), the CA’s name, validity period, etc. (NOTE: When setting up AD CS for the first time, you’ll have to select a Root CA with a new key.)
Done! Remember: security is paramount. Hence, make sure you:
- Secure your CA server. Restrict admin access and perform regular audits. Ideally, your Root CA should be kept offline in a secure facility to keep it out of reach of cybercriminals.
- Create a root hierarchy. Ideally, you should use a two-tiered PKI setup as a minimum rather than issuing certificates directly from your root CA. (This entails setting up a root CA that creates an issuing CA [which stays online] before taking the root CA offline.) You can then set up group policy objects (GPOs) and distribute the Root CA certificate to devices throughout your organization. You can then use the ICA online through a Registration Authority (RA) or for signing.
- Protect your private key. Store it in the Microsoft Strong Cryptographic Provider or a hardware security module (HSM). These devices can be expensive, costing anywhere between several thousand to tens of thousands of dollars per appliance (depending on the device’s brand, functionalities, etc.).
- Set up an effective certificate revocation status update. Configure the certificate revocation list (CRL) and the OCSP to ensure real-time certificate revocation status and updates.
- Create your templates. Generate a template for each certificate you’ll want to issue (e.g., SSL/TLS certificate, code signing certificate). NOTE: Certificate profiles aren’t available for standalone CAs.
- Back up your critical assets. Back up your AD CS private key and configuration data.
Want to dig deeper? Check out Andy Malone’s video, which shows you step by step how to install and configure the Active Directory Certificate Services:
Are you looking for even more detailed information? Go through Microsoft’s super detailed AD CS documentation and training materials.
How the Active Directory Certificate Services Works
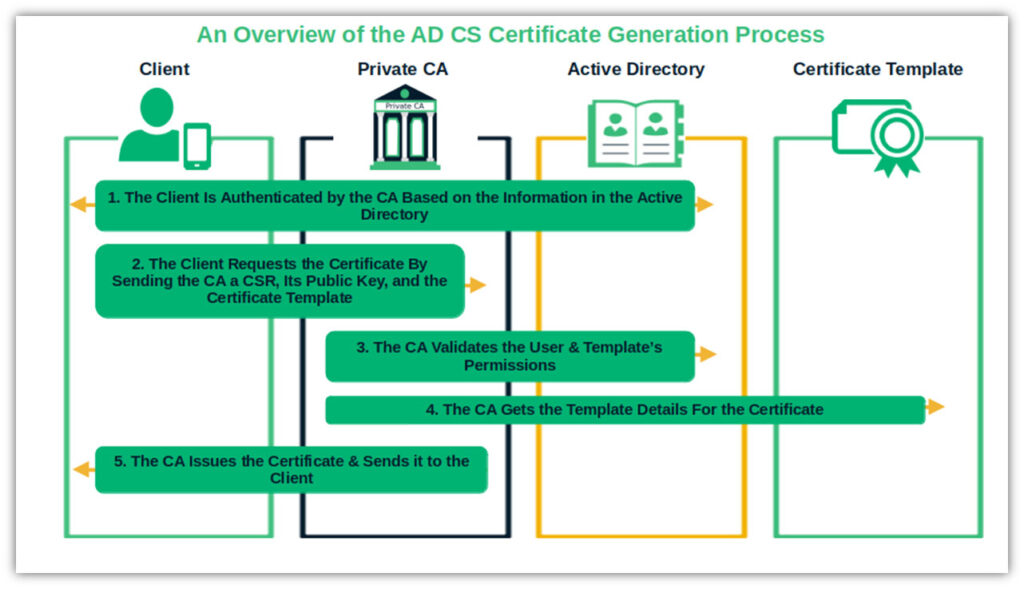
Let’s say you’ve already built and implemented your private PKI using the Active Directory Certificate Services platform, and now you want to start issuing certificates to your users, devices, and internal web apps and services. What does this process look like? In this example, we’ll request and issue an SSL/TLS certificate using a Microsoft Enterprise CA for a web service. This certificate will be used to authenticate an intranet service and secure access for the devices that connect to it.
- Authentication. An authorized user authenticates through a browser’s secure connection (HTTPS) into the CA web enrollment interface linked to the Active Directory.
- Certificate request. Once the CA authenticates the user (based on the information in the Active Directory), the user generates a key pair. The public key is attached to a certificate signing request (CSR) and the specific certificate template that defines the requested certificate’s properties and usage. This information is submitted to the CA in AD for verification and approval.
(Note: If you interact with a stand-alone CA, you won’t be able to generate a CSR with the Microsoft Management Console (MMC) Certificates snap-in. Use the CA web enrollment interface instead.)
- CA Verification. The CA validates the requestor’s permissions and the template settings against the permission lists included in the Active Directory.
- Certificate Generation. If the check is successful, the CA issues the SSL/TLS certificate based on the template settings and signs it with the CA’s private key.
Boom! The CA sends the SSL/TLS certificate to the client, which can be used for secure authentication of the service and to establish encrypted connections with your network’s web servers and devices.
Does this overarching process seem familiar? That’s because Active Directory Certificate Services follows an CSR process that’s similar to those used by the public CAs. The difference? There are several, namely that you:
- are the trusted CA,
- decide who to trust in your network, and
- issue the certificates for your internal services, apps, and devices.
The Boons and Banes of the Active Directory Certificate Services
We now have an idea of what Active Directory Certificate Services does and how it works. But what are its advantages and disadvantages? Why and when should you, as an SMB, go for it or find another solution? Check out our top pros and cons to find it out.
| AD CS Pros | AD CS Cons |
| 1. Reduces the risks of manual management-related mistakes in Windows ecosystems | 1. Isn’t Ideal for complex (multi-vendor) environments |
| 2. May help save money on certificate-related costs | 2. Requires you to hire the right people |
| 3. Integrates with the Active Directory Domain Services (AD DS) | 3. Can lead to visibility gaps in your PKI environment |
| 4. Vulnerable to security and compatibility issues |
Active Directory Certificate Services Pros
- Reduces management-related mistakes in Windows-centric environments. AD CS helps minimize human-related risks via AD group policies and by automating certificate provisioning and deployment without requiring additional user/device actions. This is true for Windows-only environments but requires manual management for non-Windows devices and systems.
- Saves time and money by using your existing Windows Server hardware. As we’ve said before, with the Active Directory Certificate Services, you’re in charge and can issue and manage your certificates for Windows devices and users using your existing hardware and systems. That’s money and time saved (for companies with AD CS integrated with AD) because you issue Windows certificates to the users and devices you trust in the timeframe that suits your needs. However, you’ll still have to manage any third-party devices and certificates manually. You’ll also have to pay costs related to HSM devices, servers, and eventual replacement costs for when those systems age out.
- Leverages the power of AD integration to improve security. Because Active Directory Certificate Services integrates with AD DS, SMBs can boost the security of their internal network using the existing AD group policies to implement role-based access control. For example, you could allow only the developers’ group to get a code signing certificate to avoid misuse and unauthorized software modifications.
Active Directory Certificate Services Cons
- Isn’t a good option for complex, multi-vendor environments. If you’re like most organizations, you likely use Microsoft Azure Key Vault or products or devices from multiple third-party vendors (i.e., non-Microsoft apps and operating systems), many of which are not compatible with AD CS. There’s also the consideration of scalability and supporting all of these different facets as your organization (and its PKI needs) grows, as automation isn’t possible with a standalone CA that isn’t integrated with Active Directory or for certificates from third-party CAs.
- Requires staff who are experienced in private PKI.Having the right people in place to set up and manage your AD CS is crucial to the security and success of your internal PKI. It requires skilled individuals with specialized knowledge who can, when necessary, create certificate management workarounds to deal with AD CS’s shortcomings.
- Doesn’t provide a complete picture of your PKI environment. Having full visibility of your PKI ecosystem and all the certificates within it is essential to security and compliance. AD CS works well when managing Windows CA certificates. However, when using CAs from other third-party CAs, there are blind spots you may not realize until it’s too late. Furthermore, search and reporting limitations make certificate management in larger organizations nearly impossible.
- Leads to security concerns if not properly configured. Implementing AD CS isn’t a walk in the park for PKI novices. This is when security risks can arise, above all for SMBs that usually don’t have highly technically skilled people in place or rely on non-Windows devices and digital certificates.
In summary, Active Directory Certificate Services can be a good tool for organizations looking to issue and manage digital certificates for (relatively) cheap in a simple, Microsoft-only environment. But what if your organization’s situation aligns more with the “cons” column of the table than the “pros”?
How to Beat the Downsides of Active Directory Certificate Services
Sectigo Certificate Manager (SCM) enables you to get the best of two worlds (i.e., the benefits of the Active Directory Certificate Services together with the high flexibility and automation of SCM) by overcoming the limitations of AD CS. As a vendor-agnostic automation tool, it allows you to manage certificates from multiple public and private CAs.
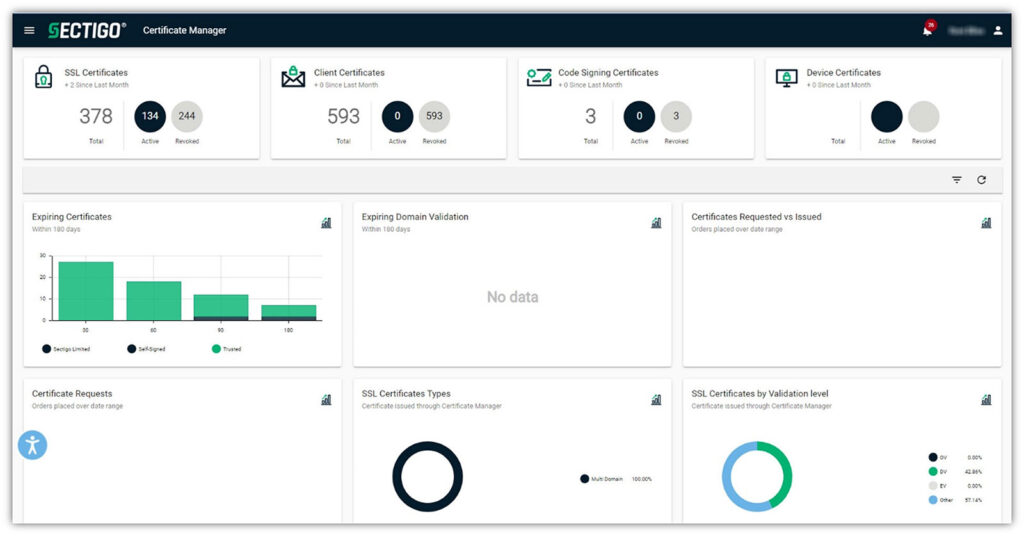
Sectigo Certificate Manager (SCM) is a comprehensive cloud-based certificate management solution that integrates with AD CS and enables organizations to:
- Automate the Microsoft applications’ digital certificate lifecycle and extend it to non-Microsoft apps. This is a critical feature considering that the 2024 State of Open Source Report shows that more than 67% of organizations increased their usage of open-source software in 2023, and nearly 61% of the companies polled were SMBs or startups. SCM also supports ACME, EST, and SCEP certificate management protocols, which enables scalable automation across your environment that reduces monotonous tasks.
- Scale your private PKI to meet your organization’s needs. The cloud-based Sectigo private root CA offered through SCM provides a more flexible solution that grows with your company and needs without compromising your systems’ security and performance.
- Get a unified view of all certificates across your business. Tired of having to separately manage your private PKI and public PKI certificates? Sectigo Certificate Manager lets you discover, issue, deploy, and manage every digital certificate across your organization on a single centralized platform. This is true regardless of which CA issued them and extends beyond your Microsoft environment.
- Minimize costs and security risks. Automating the certificate lifecycle, including revocation and renewal, further reduces the need for manual intervention. This will help lower costs, minimize the risk of errors and attacks, and speed up certificate revocations. Not bad, considering that the respondents to the same Keyfactor report we’ve mentioned above experienced an average of three certificate-related incidents (e.g., outage, failed audit, or security breach) in two years.
Active Directory Certificate Services + Sectigo Certificate Manager make the perfect pair to meet your organization’s growing certificate management needs. And if you eventually decide to make the leap from Active Directory to Microsoft Entra ID, the good news is that SCM integrates with this cloud-based identity system, too!

Simplify Digital Certificate Management with Sectigo Certificate Manager
Sectigo Certificate Manager is an all-in-one platform that streamlines certificate management and scales with your business. It allows you to supplement or upgrade your existing private CA capabilities and integrates directly with many third-party applications.
Final Thoughts About Active Directory Certificate Services 101: An Overview for SMBs
Active Directory Certificate Services make private PKI and enhanced security possible also for SMBs by empowering them to:
- Automatically issue and manage CA-approved digital certificates,
- Secure internal communication through encryption,
- Streamline certificate management, and
- Validate users’ and devices’ identities.
Yes, it has limitations. For instance, it doesn’t integrate well with many non-Microsoft technologies and managing certificates can be challenging. This is all based on the assumption that you already have someone on staff with the knowledge and expertise to set up and run your internal PKI.
However, integrating AD CS with comprehensive certificate manager platforms such as Sectigo Certificate Manager (SCM) can be a marriage made in heaven that’ll help make your organization more secure and resilient without the need for additional complex (and costly) solutions.




















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security