10 Digital Identity Examples for Small Business Owners
VikingCloud reports that one in five SMBs believe they’d be forced out of business if they fell prey to a cyber attack. Discover 10 ways SMB owners like you can use digital identity within their businesses to thwart attackers.
Menlo Security’s research data indicates that cybercriminals created 12 million new phishing sites in 2024 alone. Furthermore, nearly half of browser-based attacks included a form of brand impersonation. Knowing this, how can you, as a small business owner, ensure your customers recognize and trust you?
In the era of deepfakes and generative artificial intelligence (GenAI), how do you prove it’s really you they’re communicating with when you can’t rely on face-to-face interactions? By implementing some or all of the digital identity examples we talk about throughout this article to enable smooth, secure online transactions.
In this article, we’ll explore 10 digital identity examples that cover key aspects of your business. They help you go from “zero to hero” by enhancing security, building trust, and improving your customers’ experience with your organization.
Digital Identity Makes PKI and Digital Certificates Work Together
In the real world, it’s easy to prove who you are in face-to-face situations as an employee of a specific business. To travel abroad, you can simply show your passport, or to assert that you are a trusted reseller of a known brand, you can display a physical certificate along with your official employee ID badge.
Online, it’s a totally different story. You can’t hand over your ID card or registered license for inspection to instill more trust in your interlocutor. Someone can intercept your messages and insert fraudulent information without you or the other party (e.g., your software or code users, in this case) knowing it. Thankfully, the following digital identity examples fill this gap with the support of public key infrastructure (PKI) and digital certificates.
PKI works behind the scenes with X.509 certificates issued by trusted certificate authorities (CAs) to authenticate and secure the entities and devices in the digital ecosystem. In other words, together, they foster trust and enhance security by verifying identities and protecting sensitive data and communications against the bad guys through authentication and authorization.
Sounds good, right? Now, let’s see a few practical examples of how you, as an SMB, can make digital identities work to your advantage.
Digital Identity Example #1 — Enable Secure Physical Access Controls for Your Office
A few years ago, I visited a data center. To my surprise, to access it, besides having to show my badge, I was asked to step on a scale! The security guy recorded my weight, using it as a biometric identifier, and I was in. That was the oddest (and most embarrassing) security measure I’d ever experienced.
Luckily, there are better (and less embarrassing) ways to secure physical access to your offices and server rooms. PKI certificate-based smart cards are one of the most effective (especially when paired with other security measures). This digital identity solution embeds the employee’s unique X.509 digital certificate and private key into the ID card (which, ideally, should have the employee’s photograph printed on it).
Every time a staff member needs to access a company’s building or an internal secure area, they use their certificate-based strong authentication card that acts as a digital ID. No one should have physical access to an employee’s smart card except the employee to whom it’s assigned.
In the background, the PKI validation process checks the validity of the certificate and signature to verify the user’s identity. It authorizes or denies access to the premises — no PINs or scales required.
Digital Identity Example #2 — Server Certificates Prove Your Site Is Authentic and Secure
Your organization’s website is its window into the digital world. It allows you to showcase your company’s products and services, promote your brand, and connect with current and prospective customers. Nevertheless, the news is filled with stories of phony websites impersonating brands to steal users’ data and money.
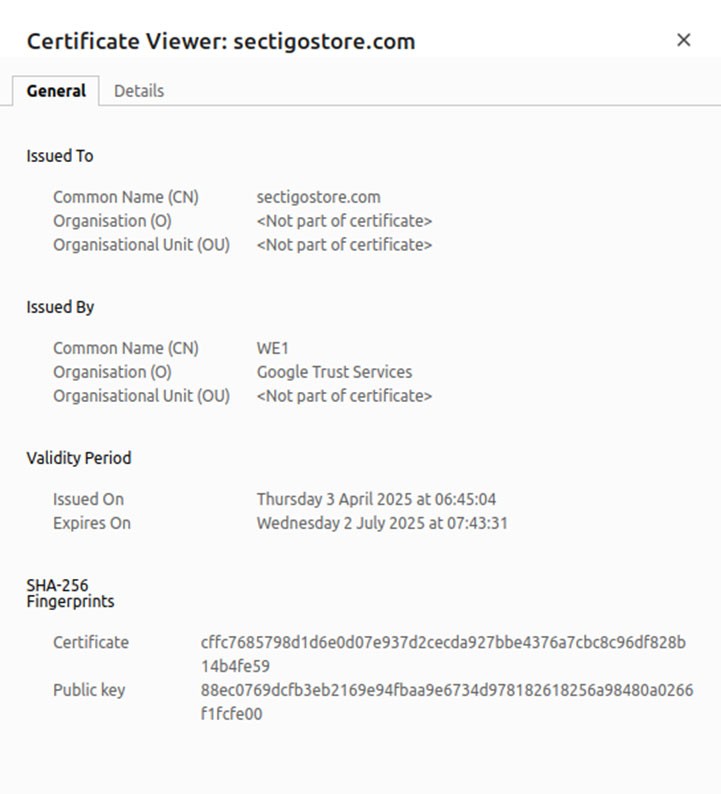
So, how do you reassure your customers that they’re really browsing your website and not a copycat created by an imposter? Confirm your organization’s information with a secure socket layer/transport layer security (SSL/TLS) certificate, a type of digital identity certificate that’s issued by a trusted certification authority (CA). There are various levels of digital identity validation (such as domain validation, organization validation, and extended validation).
A few clicks on the address bar, and voila’, an OV or EV SSL/TLS certificate will display your organization’s validated information in all its glory, just like in the example below. It’s that easy. Now, customers can browse your website with the peace of mind that your site is secure and legitimate.
Digital Identity Example #3 — User Certificates Ensure Only Authenticated Users Access Secure Resources
In February 2025, KELA researchers revealed that an infostealer malware stole 3.9 million credentials from infected machines. A personal authentication certificate (PAC) is one of the examples of digital identities that eliminates the need for traditional IDs and passwords that can be phished or stolen, leaving attackers empty handed.
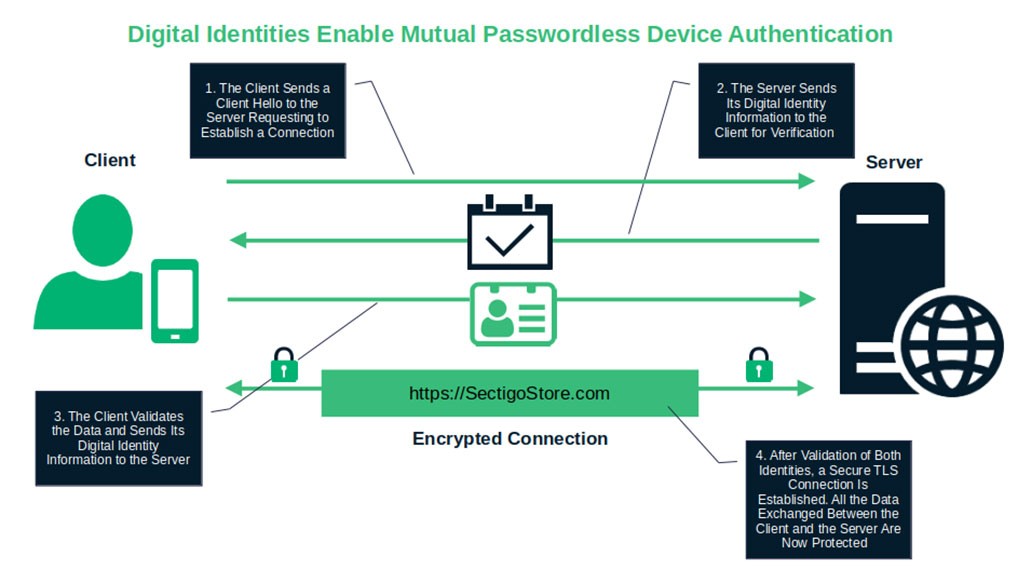
Here’s how it works. When a user accesses your website or app, their device exchanges its certificate and public key with the server’s certificate (i.e., mutual authentication). The trick? The user’s private key is never sent to the server, and depending on the user’s device, the key is typically stored in a secure trusted platform module (TPM) that’s inaccessible. Furthermore, the user is allowed to access the website/app only with the device that stores the certificate and the corresponding private key.
This way, the bad guys have no password to steal. Moreover, they can only access the website/app if they manage to get hold of the private key, which is easier said than done if you do things wisely (more on this momentarily).
Digital Identity Example #4 — Mitigate Wi-Fi Credential Theft Risks with Passwordless Authentication
Next on our list of digital identity examples is one that’ll be highly useful for large and small businesses alike: passwordless authentication for access to secure resources.
Passwordless authentication via PKI digital certificate isn’t only effective for secure access to websites and applications. Once implemented, it lets employees securely connect to your company’s Wi-Fi network by first confirming their digital identities.
Do you have remote workers who need to use a virtual private network (VPN) to do their jobs? No problem. Most VPNs allow users to connect, harnessing the power of digital identity and X.509 certificates.
Digital Identity Example #5 — Ensure Only Authenticated IoT & Mobile Devices Access Your Network
In 2024, Forescout analyzed the risk represented by Internet of Things (IoT) devices. The outcome was shocking: IoT vulnerabilities skyrocketed by 136% in just one year. We’re talking everything from vulnerabilities in proprietary and open-source software to security-related issues in the hardware itself.
The usage of IoT devices such as security cameras, routers, and smart lights is growing, as is the number of employees using their personal mobile devices for work. With this in mind, would you trust these devices with access to your network without having access controls and authentication measures in place first? I guess you know the answer.
Give a digital identity to your IoTs and mobile devices. Your network will automatically recognize them as secure and grant them access without requiring credentials.
Digital Identity Example #6 — Validate Your Software’s Integrity and Authenticity
With the support of AI, attackers are creating malicious applications that look like legitimate apps. In 2024, Malwarebytes identified 3,900 phony applications that could read one-time password (OTP) information directly from the notification bar.
So, how can you authenticate and secure your software’s integrity as a developer or publisher? Sign it using a special digital certificate known as a code signing certificate.
Imagine you’ve just created a new application, signed it with a trusted code signing certificate, and published the app on your website. When a customer downloads it, their device’s operating system or client will use the certificate’s public key to
- decrypt the signature,
- verify your identity, and
- ensure the code is authentic and hasn’t been modified by an unauthorized third party.
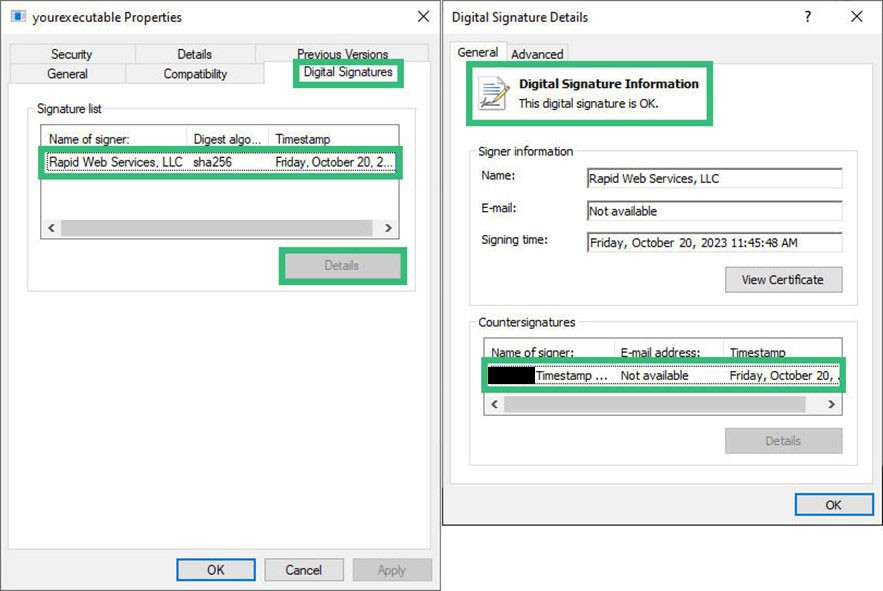
If everything is peachy, the installation continues. If it isn’t, the installation is blocked. The user can also check the certificate’s digital identity and information directly via the digital signature’s certificate details.
Much like a browser shows an SSL/TLS certificate’s validated data, a popup window displays your digital identity information in detail and enables Windows systems to display the information upfront. Empowering users to verify your digital identity as a software publisher and confirm the integrity of the code will reassure your customers and help you boost downloads.
Here’s a code signing digital certificate example that shows part of an app’s digital signature info:
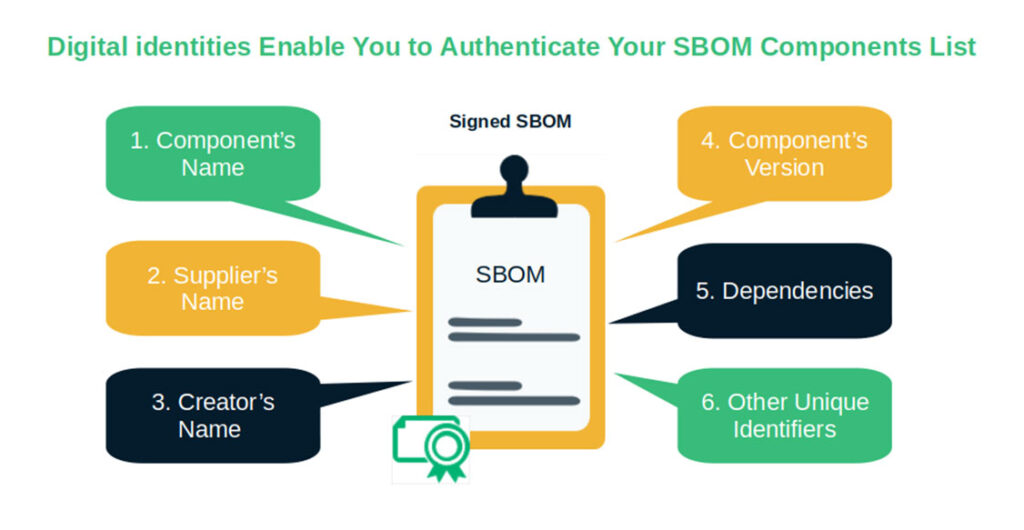
Digital Identity Example #7 — Authenticate Your Software Bill of Material (SBOM) and Components
The latest version of the National Institute of Standards and Technology (NIST) Cybersecurity Framework, specifically focused on SMBs, stressed the importance of using SBOMs in mitigating vendor-related risks.
An SBOM enables you to list all of the components that comprise your software. This simple action helps you identify vulnerabilities and flaws and fix them quickly. This is great considering that in 2024, Reversing Labs detected an average of 33 high-severity vulnerabilities and six critical-severity vulnerabilities in each of the top 30 open-source software packages (i.e., npm, PyPI, and RubyGems) they scanned.
Want some good news? The code signing certificate you used to sign your software can also be used to add a digital signature to your SBOM. This approach helps guarantee to your customers and users that you really made the product, and that the list of components hasn’t been modified. Isn’t it great? One digital certificate to sign them all — well, at least all your codes and SBOMs.
Digital Identity Example #8 — Authenticate Your Email Server to Prove Messages Are Legitimate
Email isn’t dead, even with the proliferation of instant messaging apps and collaboration tools. In fact, it’s thriving — and so are email-based attacks. According to SlashNext, email attacks increased by 202% in the second half of 2024.
Since early 2024, major email providers like Google and Yahoo have required bulk senders to authenticate their email servers as a precondition for email deliverability. Microsoft recently joined the party, announcing that its Outlook.com consumer services would require a higher level of authentication for bulk senders starting May 5, 2025.
So, how can you do this? Besides implementing DNS-based authentication measures, installing an SSL/TLS certificate from a trusted CA or authorized reseller like SectigoStore.com lets you kill two birds with one stone by:
- Boosting email deliverability by confirming your email server’s digital identity in a verifiable way.
- Protecting your emails from prying eyes by transmitting data through an encrypted channel.
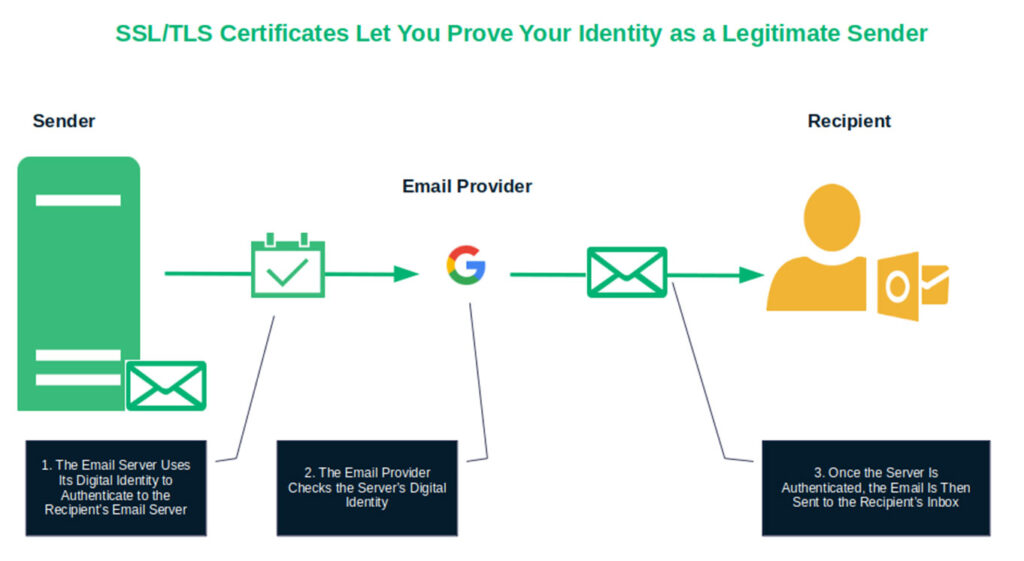
The problem is that SMTP connections aren’t encrypted by default. This means that cybercriminals can intercept, read, and modify everything you send without your knowledge and that of your recipient. This is another way that SSL/TLS certificates for email servers come into play. In this case, they enable businesses to create a secure channel for their messages to transmit through to recipients’ email servers.
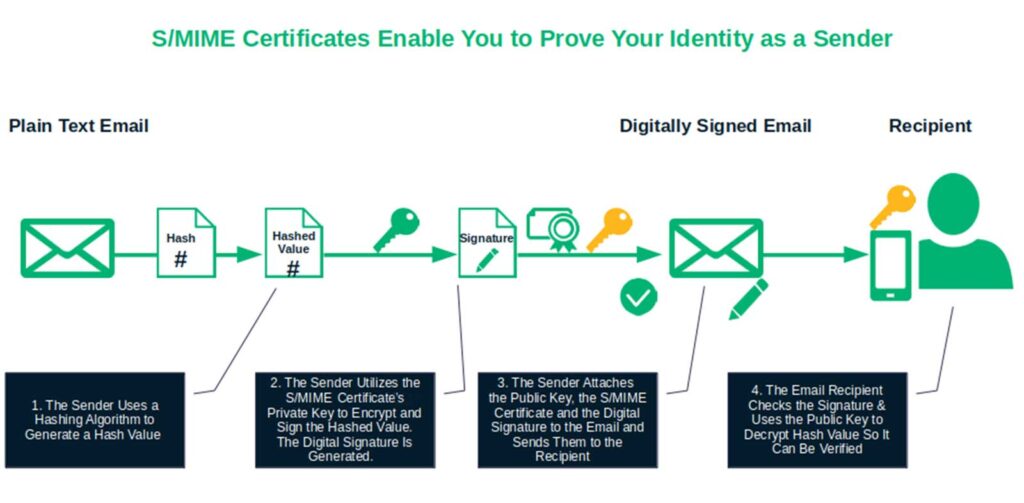
Digital Identity Example #9 — Authenticate Your Email Messages to Prove Their Legitimacy
An S/MIME digital certificate, or what’s otherwise known as an email signing certificate, will ensure that every email you send will be digitally signed using the same PKI principle applied to the other examples we already mentioned. The digital signature enables recipients to verify whether you sent the message and if it has been modified in transit.
As a bonus, you can use that same S/MIME certificate to encrypt your messages and attachments directly if your recipient also uses one. Just sign it using their public key, and they’ll use their private key to decrypt the message on their end. This provides end-to-end encryption that keeps your emails secure, even when they’re sitting in the recipients’ inboxes.
This is a fantastic way to boost trust and increase email open rates. Think about it from your customers’ perspective. Wouldn’t you feel more confident engaging with a company that signs its emails than with a brand that doesn’t? I’m sure you would.
Here’s a quick overview of how the email digital signing process works:
Digital Identity Example #10 — Prove Your Microsoft Office Files and PDFs Are Unaltered and Were Made by You
Picture this: you’ve just prepared an invoice for a customer and saved it as a PDF file. When you send it to the client, the PDF file is intercepted by a threat actor, who replaces your bank account details with his information. Since the document was sent from your organization’s email address, the client assumes it’s genuine and pays for it. Boom. You’ve lost the money and probably the customer as well.
Prevent this and foster trust. Here, you can confirm your digital identity in two ways, depending on the document format:
- Microsoft Office files can be signed using a Sectigo Document Signing Certificate.
- Does the Excel file contain macros? Sign them using a code signing certificate. Attackers won’t be able to exploit them for malware.
- Adobe PDF files can also be signed using an Adobe-trusted Sectigo Document Signing Certificate. (Contact us today to learn more about this type of digital certificate.)
Implement These Digital Identifiers Wisely and Securely
Do the words SolarWinds and Nvidia sound familiar? These two organizations were both victims of attacks where hackers exploited legitimate certificates and/or private keys to compromise thousands of systems and customers.
The digital identity examples we’ve shared so far, once implemented, will help SMB owners like you to foster digital trust in your brand and products and secure your assets, but only if you take good care of your digital identity certificates and, more importantly, their corresponding private keys. Therefore:
- Store your certificates and keys on secure hardware. Choose between USB tokens, hardware security modules (HSMs), or cloud-based HSMs.
- Automate your certificate management process. Software like Sectigo Certificate Manager lets you effectively manage and protect all of the digital certificates in your ecosystem, regardless of CA, saving you resources and time.
- Opt for strong algorithms. The post-quantum era is nearer than you think. With harvest now, decrypt later (HNDL) attacks, the bad guys are hoarding massive amounts of stolen encrypted data that they’ll easily decrypt as soon as they can put their hands on quantum technology. Future-proof your systems by choosing hybrid and quantum-resistant algorithms whenever you can.
Final Thoughts About These Digital ID Examples for SMBs
These digital identity examples are more than just virtual passports: they’re at the heart of a secure and smooth online experience for businesses and customers. They foster trust by affirming your identity as an organization, help you achieve compliance with privacy and security regulations, and protect your websites, network, users, and data from attacks.
Digital certificates play a key role in digital identification, but they can be challenging to manage, especially for SMBs with limited headcounts and resources. The solution? Streamline and automate your certificate management process with Sectigo Certificate Manager. It’s perfect for every use case.





















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security