What Is Passwordless Authentication?
Verizon’s 2020 DBIR reports that 80% of breaches within hacking involve brute force or the use of lost or stolen credentials. Learn how passwordless authentication can help you avoid such cyberthreats
Passwordless authentication is all about making the authentication process more user-friendly and improving the security. But why did the need for passwordless technology arise in the first place?
NordPass estimates that the average user has between 70 and 80 passwords. It’s not feasible for a person to remember 80 unique and complicated passwords. That’s why people often use easy-to-remember passwords or reuse the same passwords for multiple accounts.
But then also, according to a survey by HYPR, 78% of respondents said they had to reset their passwords due to forgetting them within the previous 90 days. Apart from causing an inconvenience to users, passwords also pose a great cyber risk to organizations.
In this article, we’re going to talk about passwordless authentication methods and how they work.
What Is Passwordless Authentication?
Authentication means confirming your identity in a way that third parties make sure you are the person/entity/organization that you claim to be. Traditionally, a cumbersome password is used for identity verification. But with passwordless authentication, you may use one of the following authentication factors:
- A one-time password (OTP),
- Magic links,
- Hardware that produces system-generated PINs or codes,
- Biometrics, or
- Cryptographic digital certificates.
Don’t worry, we will talk about each of these in detail shortly.
So, for example, whenever you log into your bank account, you generally use the traditional password-based method to authenticate yourself to that financial institution. But if the bank has enabled any passwordless method, you will be using one of the above-stated techniques instead of providing the cumbersome, hard-to-remember password.
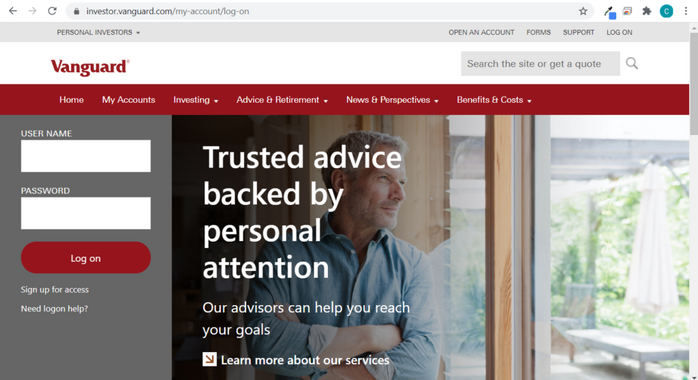
Passwordless authentication is something you can implement on everything from personal laptops to smartphones. Organizations can implement it on their public-facing and intranet websites, internal email network, work accounts, as well as on hardware resources like computers, tablets, and smart phones.
5 Passwordless Authentication Tools
Let’s explore some common tools of passwordless authentication.
1. Biometrics
This category includes fingerprint scans, retina scans, and facial recognition scans. Biometric authentication is convenient for users because, barring any terrible accidents, users are always going to have those authentication factors with them. They’re parts of users’ bodies.
So, you need to neither remember anything nor carry any hardware devices or cards. Many desktop, laptop, tablet, and cellphone manufacturers have already embedded biometrics authentication to provide security and convenience to their users.
However, there have been cases of biometric data (fingerprints) getting leaked or stolen in data breaches:
- VPNmentor researchers discovered 28 million fingerprint and facial recognition records in Suprema’s BioStar 2 data breach.
- The U.S. government’s Office of Personnel Management (OPM) hack leads to the theft of 5.6 million fingerprint records.
- SafetyDetectives researchers discovered an insecure database owned by Antheus Tecnologia containing 2.3 million data points, including 76,000 unique fingerprints.
Although there are ways to bypass the biometrics authentication, it requires a lot of hard work on the hacker’s end to replicate biometrics even for a single account. Hence, the chances for bulk hacking are negligible.
2. One-Time Passwords
When users register new accounts, they need to provide their phone numbers and create user IDs. Every time users want to log in to their accounts, they receive unique one-time passwords (OTPs) on their mobile phones via push notifications, SMS text messages, or on their registered email addresses.
Each OPT stays valid for a limited period of time (generally 30 seconds to 24 hours) and can be used only once. In this way, users don’t need to remember the password.
3. Security Tokens
A security token is a physical device that validates a user’s identity and lets them access the system and resources. These are often called dongles. The user must possess this token to complete the authentication process. There are three main types of security tokens:
1. Connected Tokens:
A user must plug the security token into the system, computer, cardholder, etc. to complete the verification. Two examples of this type of token includes a USB token and a common access card (CAC), the latter of which requires the use of a CAC reader.
USB Tokens: You can log in and/or access some confidential resources on a computer only after plugging in this USB device. It generally involves 2-factor authentication (2FA). So, even after plugging it, you might need to activate the USB using your fingerprint or providing a secret code as a second form of authentication.
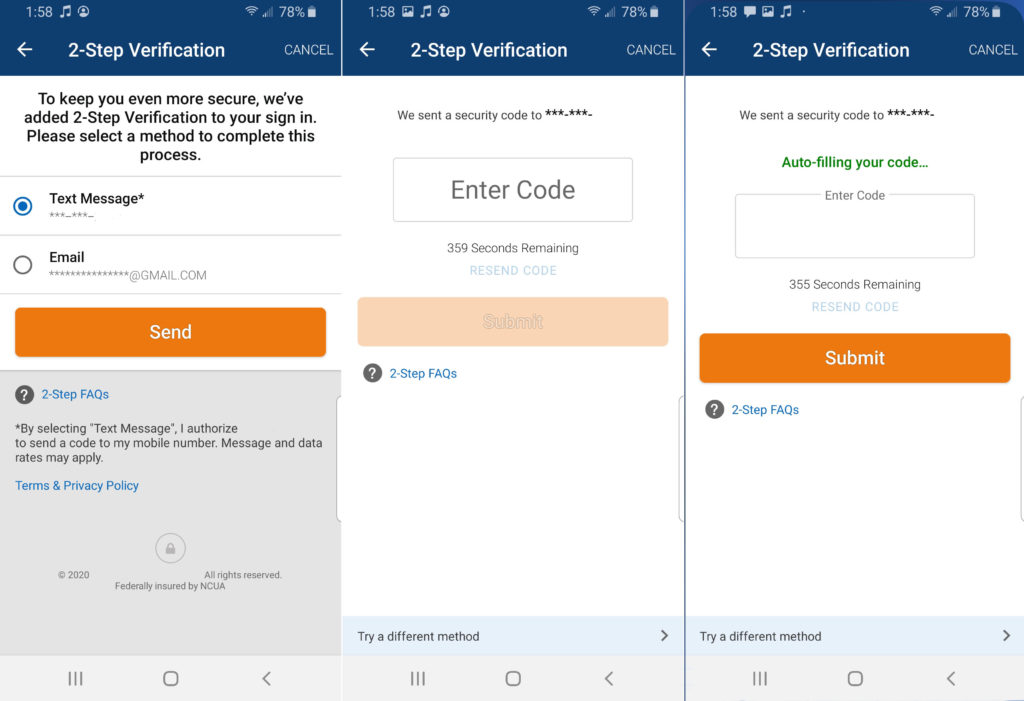
2. Disconnected Tokens
These are the small devices that look like a sim card, keychain fob, or USB flash drive. These tokens generate a unique and temporary cryptographic code that must be input by the user to gain access to a computer resource. Users don’t need to insert the token in the system. Check out the image below.

Another example of disconnected tokens is grid cards.
Grid Cards: Almost reminiscent of Bingo cards, these cards have grids containing combinations of numbers and letters in different rows and columns. When users need to verify their identities, they have to log in with their biometrics or PINs. Then the system will ask to supply a particular value from the tables in the card.
See the example below for an idea of what one of these cards looks like:
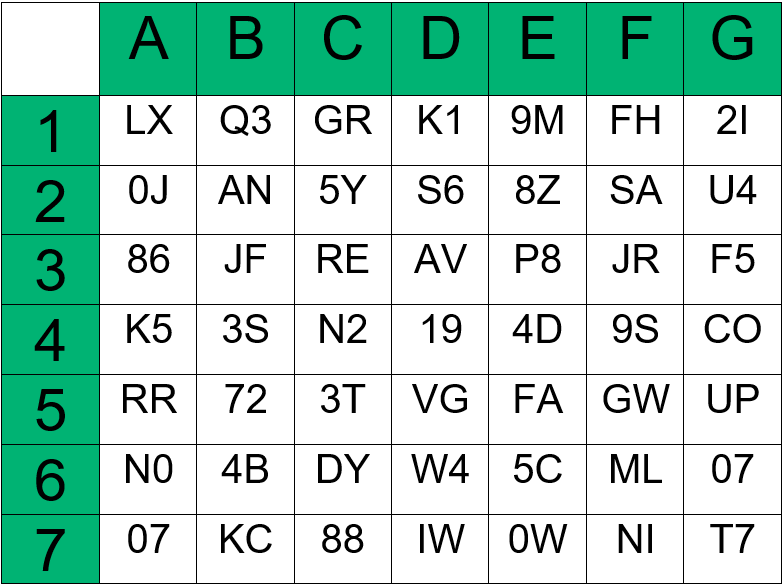
This is an example of a grid card. If the system asks you “B1, F3, D2”, you need to find and input the values written on those cells. So, using the card example above, the values will be Q3JRS6.
Eployees can carry that card in their wallet, or the company may choose to imprint it behind the employee badge.
3. Contactless Tokens
Some tokens don’t require users to plug the token in the system or insert any key. The authentication is done automatically — for example, Bluetooth tokens.
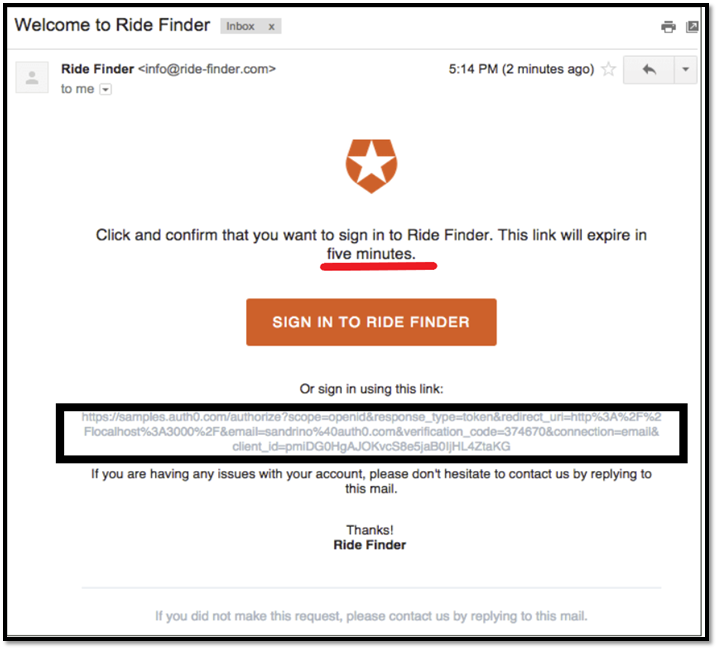
4. Magic Links
In this passwordless authentication method, anauthenticator sends a unique link-URL to your registered email address or on the SMS. The URL contains a special token. When you click on the link, the server verifies it and sends it back to you (client). The token is then saved on your browser as a cookie for that particular session. If the link is not clicked on within a specific time period, it expires.
5. Client Certificates
These PKI certificates are of great benefit to organizational setups, especially for businesses with remote employees. These certificates, which authenticate users, are also known as client certificates, personal authentication certificates (PACs), user certificates, and email signing certificates. (They are sometimes called this because they are used to digitally sign and encrypt emails, too.)
These certificates are installed on the organization’s server and employees’ devices (desktop, laptop, or even smartphones). What they do is make mutual authentication possible, authenticating both the users’ clients and the servers they’re connecting to through an exchange of certificates. This twist on the traditional TLS handshake involves the server providing its SSL/TLS certificate as usual with the addition of the client providing its own certificate and public key.
The organization’s server stores public keys while the client devices store private keys. So, employees can only access the company’s resources only when they log in from the devices where the corresponding private keys are stored. If the server can’t verify and authenticate the user’s certificate, it’ll reject the connection.
Hence, even if hackers steal the user’s credentials, they can’t access anything on the company’s server. Because here, the authentication is done via the certificate exchange. And since the private key never gets sent to the server, it remains secure.
The certificates, particularly when used with trusted platform modules (TPMs), offer greater security than phone-based multi-factor authentication methods. TPMs are cryptographic hardware modules that allow you to securely store your digital certificates or keys.
5 Crucial Reasons to Avoid Using Password-Based Authentication
Let’s understand why a password is considered a weak security measure and why you may want to consider passwordless authentication methods:
1. Cybercriminals Can Guess Passwords with Social Engineering
People often aren’t serious about setting strong passwords. Avast reports that 83% of Americans use weak passwords, and 53% of Americans use the same password to protect multiple accounts. In general, people frequently use the names of their loved ones, friends, pets, or their favorite movie, sports, celebrities as their passwords. They also use their dates of birth, marriage anniversaries, or other important dates as their passwords.
While this info makes it easier for people to memorize the passwords, it also makes it easier for hackers to guess them using social engineering. This method allows a cybercriminal to gather and use the information they learn about the victim through their social media profiles, career networking sites, and other information that’s available on the public domain.
2. Hackers Use Brute-Force Attacks to Bypass Password-based Authentication
In brute force attacks, hackers set a script or bot on login fields, which keeps applying a pre-guessed database of millions of user IDs and passwords automatically until it makes a successful login attempt. Sometimes a botnet is used, where a large number of infected devices deploy the brute force attack on a targeted login field.
According to SafetyDetectives, which has collected more than 18 million passwords, these are the10 most commonly used passwords in the world:
- 123456
- password
- 123456789
- 12345
- 12345678
- qwerty
- 1234567
- 111111
- 1234567890
- 123123
This shows how careless people can be when creating passwords. When users use weak passwords, hackers can easily bypass the authentication mechanism through brute force attacks.
3. Risk of Password Leakage Increases When Multiple Users Sharing the Same Password
In an organizational setup, it’s common for multiple employees and teammates to share the credentials of the company’s core accounts, resources, services, and email addresses. This may help to save money on purchasing licenses for separate accounts, but it can be far more costly in terms of credential compromise.
Sometimes, these employees reside in different cities, countries, and/or are working remotely. If any of those employee’s device is infected with malware, gets stolen, or otherwise becomes compromised via the man-in-the-browser, man-in-the-middle, or botnet trojan, the credentials get compromised. The hacker can break into the corporate email network, files, and access confidential data.
4. Hackers Buy and Share Password Lists on the Dark Web
Some attackers find leaky databases or use malware to steal users’ login credentials and passwords. They use the lists themselves or sell these credentials to other cybercriminals on the dark web.
There are numerous data breach incidents that took place in the past, and big companies like Yahoo, Equifax, First American Financial Corp, Facebook, and Marriot became victims of data theft. For example, in May 2020, a hacker group named Shiny Hunters stole 25 million students’ email addresses and passwords from a math solving app, Mathway. They were selling that database on the dark web for $4,000.
So, the perpetrators who don’t know programming or common hacking techniques can also buy and misuse the passwords. When people use the same passwords for multiple accounts, it becomes very easy for attackers to hack all other accounts, too.
5. Keyloggers and Other Malware Can Record or Steal Your Passwords
A keylogger is a software that can monitor and record users’ actions and behaviors. This type of software can read, copy-paste, and take screenshots of the devices’ in which they are installed. Hackers use keyloggers to steal passwords, along with other personal data. But if you’re not using a password-based method of authentication, it helps to mitigate some of the risks associated with keyloggers.
Multi-Factor Authentication (MFA) vs. Passwordless Authentication
Multi factor authentication (MFA) is related to passwordless authentication but is also still different because it traditionally involves the use of a password. In MFA, there are two or more layers of verification. In general, a password, followed by at least one secondary verification method like a hardware token or a biometric scan. Many often refer to these secondary authentication factors as “what you know,” “what you have” and “what you are:”
1) What you know: Passwords, security questions’ answers and pass phrases.
2) What you have: A possession that you have in your control such as a smartphone, laptop, USB token, or grid card.
3) What you are: Biometrics such as fingerprints, iris or facial scans, etc.
With passwordless authentication, however, no password or other types of knowledge-based secrets are necessary. It does, however, involve the use of cryptographic key pairs (we’ll talk more about those soon). And passwordless authentication mechanisms may or may not have multiple layers of authentication. This means that it may only use one standalone verification method or may rely on more than one method (this is often referred to as “passwordless MFA”).
The Role of PKI in Passwordless Authentication
Public key infrastructure (PKI) is the very foundation (the processes, procedures and technologies) that internet security is built upon. It’s all about asymmetric encryption, and many passwordless authentication methods are based on PKI at their core.
Certificate-based authentication methods — such as SSL/TLS certificates for websites or the client certificates we just talked about moments ago — rely on asymmetric encryption. This involves the use of digital certificates that are issued by trusted third parties (known as certificate authorities, or CAs) and asymmetric key pairs. These certificates, which CAs sign, authenticate third parties while the keys encrypt and decrypt data.
These key pairs consist of two mathematically related yet distinct keys.
- Public key: This key is available in the public domain and is something users’ clients and websites share to prove their identities through third party authentication. This is what you use to encrypt data to keep it secure from prying eyes.
- Private key: This key, like the name would imply, is private and must be kept secret. This key is what you use to decrypt data that’s encrypted by the public key. What’s great about these keys is that they’re virtually impossible to crack. For example, a 2048-bit RSA key would take approximately 300 trillion years to crack using modern computers, according to Quintessence Labs.
Only when you have the right combination of validated certificates and public and private keys, the authentication gets completed, and you can securely access the system. The onus of PKI’s success entirely relies upon the secrecy of the private key and the trusthworthiness of certificate authorities.
For more information about public key infrastructure, be sure to check out our in-depth piece on this topic.
Wrapping Up on Passwordless Authentication
Passwordless technology provides a robust private key to organizations, websites that offer online services, and the users’ devices. Users don’t need to memorize a large number of passwords or hit “forgot password” numerous times and reset them.
Passwordless authentication frees up the IT department’s time as they no longer require setting password policies and comply with password storage laws and regulations. They don’t need to be constantly alert to detect and prevent password leaks.
So, is a passwordless solution right for your organization? Are there any disadvantages to passwordless authentication to consider? Let’s explore these questions in one of our next articles that talks about the advantages and disadvantages of passwordless authentication.














 (25 votes, average: 4.68 out of 5)
(25 votes, average: 4.68 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security