What ‘Harvest Now, Decrypt Later’ Means for SMBs (and 7 Steps to Prevent These Attacks)
Quantum computing doesn’t mean the end of the world, but its eventual arrival will threaten the security of your data. There are steps you can take to help harden your business against harvest now, decrypt later (HNDL) attacks
A recent episode of Sectigo’s “Root Causes” podcast explored the enterprise threat harvest now, decrypt later (HNDL). This attack method involves collecting encrypted data now (harvesting) to hold onto it to “break” (decrypt) the encryption later once quantum computers become more readily available.
Understandably, discussions about harvest now, decrypt later attacks typically focus on enterprises. However, small and mid-size businesses also collect and store data, and they typically don’t have as many resources as their larger business counterparts. So, this makes them potentially easier prey for HNDL attacks.
So, what does this threat mean for small and mid-size businesses? And what can you do to protect your data against harvest now, decrypt later attacks?
Don't make the same mistakes
Yahoo, Equifax, Home Depot,
LinkedIn, and Ericsson did!
Get our free 15-point checklist and
avoid the same costly pitfalls.
Contact details collected on InfoSec Insights may be used to send you requested information, blog update notices, and for marketing purposes. Learn more...
Breaking Down the Harvest Now, Decrypt Later Threat for SMBs
In a nutshell, a harvest now, decrypt later attack is a way for bad guys to collect your data now and sit on it until later (i.e., when the quantum-based technology becomes available later that allows them to decrypt it). The data they collect now could be exposed within the next few years or potentially a decade from now. This is why this attack method is also known as retrospective encryption.
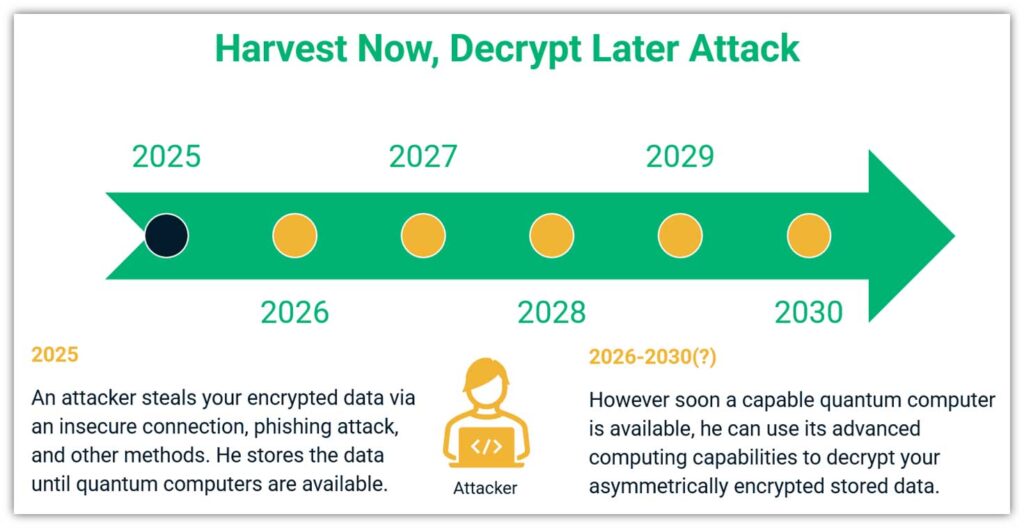
Data harvesting could be happening right under your nose as we speak. This means your company’s most sensitive data — customers’ personally identifiable information (PII), employees’ PII, proprietary data, research, intellectual property, everything — is at risk of being compromised by cybercriminals who want to exploit it.
All they have to do is play the waiting game… because the types of data they’re after don’t have a short shelf life.
Attackers Focus on Collecting the Most Valuable (Evergreen) Data Possible
While it’s true that harvest now, decrypt later attackers are collecting massive amounts of data, not all data will remain useful over time. For example, credit card numbers aren’t necessarily useful because they change every few years, and cardholders can cancel their cards and have new ones issued relatively easily if there’s concern about a potential compromise.
This is why bad guys seek the types of data that retain perpetual value and have long lifespans. A few examples include:
- Customers or employees’ Social Security/national ID numbers
- Other types of personally identifiable information (PII)
- Intellectual property (proprietary product schematics, recipes, etc.)
- Government or military secrets
- Medical records
Furthermore, storing massive quantities of data over time can rack up a pricey bill regarding storage, energy, hardware, etc. To keep costs to a minimum, bad guys must carefully evaluate and determine which data to target to get the most bang for their buck. They use contextual info to determine where to source the most valuable data.
For example, imagine an attacker figuring out how to identify the encrypted traffic transmitting to and from financial applications or the IP addresses of key employees within your organization (CEO, CFO, payroll officer, etc.). They’ll be able to steal encrypted data that likely has high intrinsic value once decrypted.
Likewise, they’re more likely to get more valuable evergreen data by targeting a small medical office or insurance company than, say, a bakery.
7 Ways SMBs Can Sabotage Harvest Now, Decrypt Later Attacks
Now that we know what harvest now, decrypt later attacks entail and which types of information bad guys are looking for, it’s time to learn what steps you can take to secure your data against HNDL attackers.
Of course, there are the basic small business cybersecurity measures you can implement. But you must take things further to mitigate the threats posed by quantum computing capabilities in the future.
Implement Quantum-Resistant Cryptography Wherever Possible
Ultimately, the best way to combat quantum computing-related threats like harvest now, decrypt later attacks is to fight fire with fire. This means all organizations, regardless of size, need to begin implementing post-quantum key encapsulation and encryption algorithms in place now within their IT ecosystems.
Unfortunately, time is not on your side and the clock is ticking down:
- Gartner predicts that quantum computers will “render traditional cryptography unsafe by 2029” and that “advances in quantum computing will make asymmetric cryptography unsafe and by 2034 fully unbreakable.”
- Quandela has announced its Quantum Roadmap, which outlines plans to launch “general purpose quantum computing libraries” and assemble “large-sale, error-corrected quantum computers” by 2028.
- In August 2024, the National Institute of Standards and Technology (NIST) released its first three PQC standards.
- In November 20204, the National Institute of Standards and Technology (NIST) set a deadline to deprecate multiple cryptographic algorithms by 2030. They’ll be disallowed entirely starting in 2035.
Simplify Digital Certificate Management with Sectigo Certificate Manager
Sectigo Certificate Manager is an all-in-one platform that streamlines certificate management and scales with your business. It allows you to supplement or upgrade your existing private CA capabilities and integrates directly with many third-party applications.
1. Ensure Your Organization’s Web Clients Are Using Hybrid Algorithms
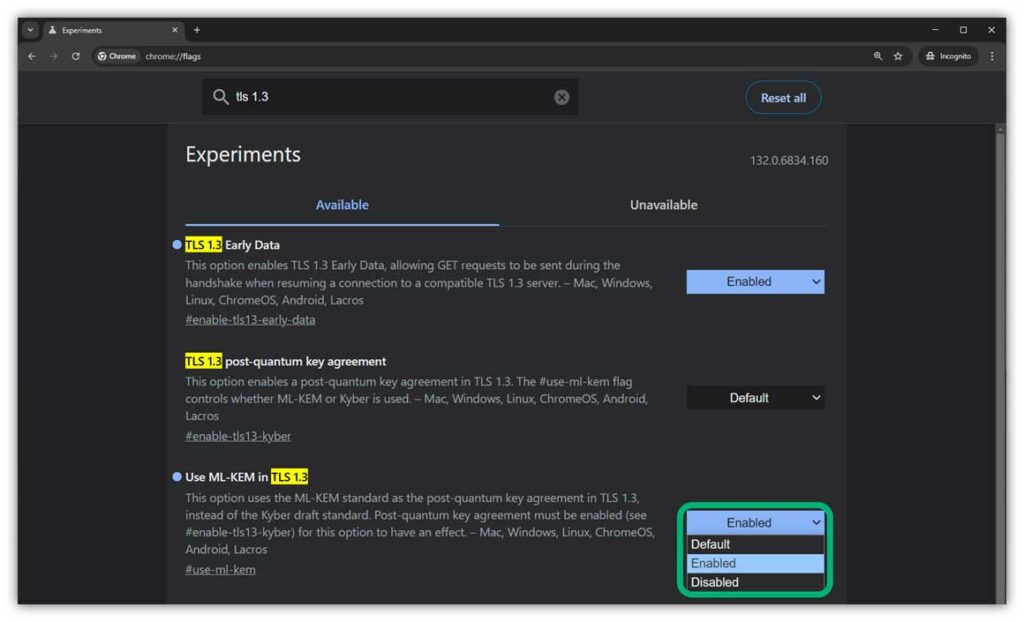
One easy way to do this is to ensure that your employees’ web browsers are using hybrid key encapsulation mechanisms (i.e., ML-KEM768) to secure data transmissions. This is a quick fix that adds another layer of security to your company’s data transmissions by making it so that data is encrypted using this PQC hybrid key agreement algorithm whenever compatible TLS 1.3 connections are available.
In Google Chrome, you can implement it by
- entering chrome://flags in your browser address bar and hitting Enter,
- typing TLS 1.3 in the Search Flags field at the top, and
- enabling Use ML-KEM in TLS 1.3 in the dropdown menu.
(NOTE: This should already be done by default if your Chrome browser is up to date, as Chrome implemented the change by default in Chrome 131.)
2. Ensure Your Domain Supports PQC Hybrid Algorithms
If your company is using Cloudflare to serve your domain, then you’ll be happy to know that the company has enabled the ML-KEM768 hybrid PQC key agreement algorithm on its servers for TLS 1.3 traffic.
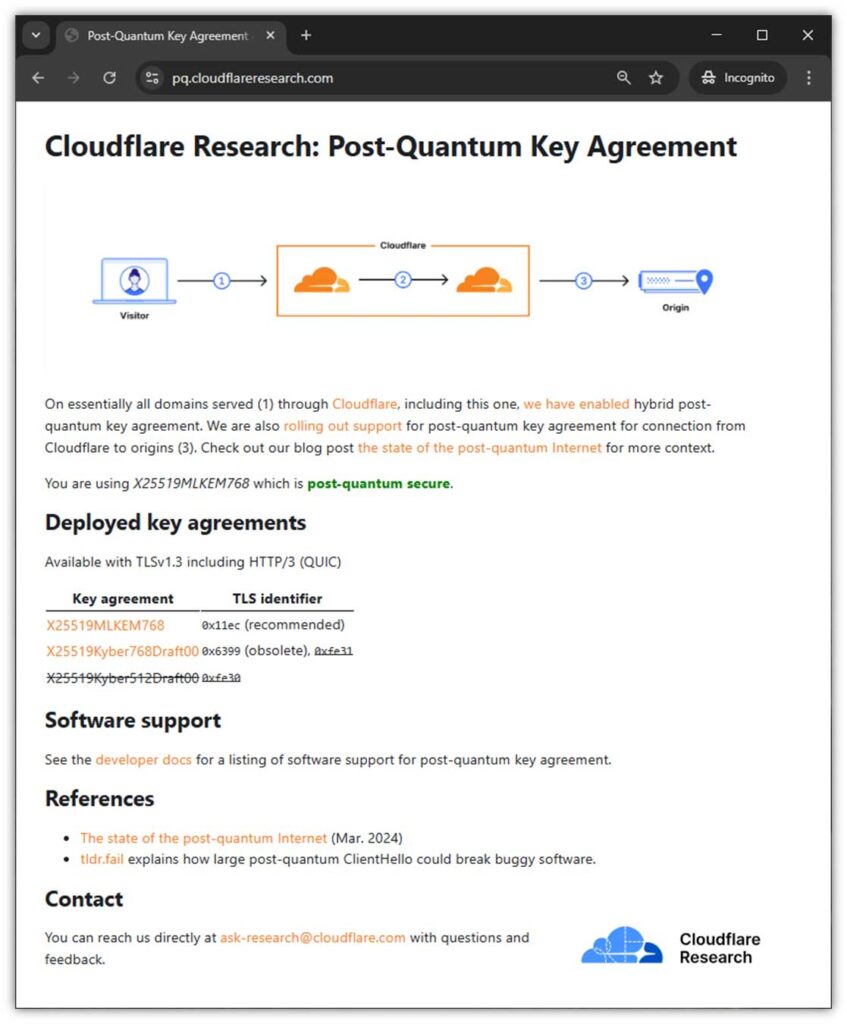
Research from Cloudflare shows that the adoption of post-quantum encryption in HTPS request traffic has jumped from 18.4% on Feb. 1, 2024 to 32.9% on Feb. 1, 2025.
3. Test Your PQC Readiness with Sectigo’s PQC Labs Sandbox
Sectigo, in partnership with Crypto4A, recently launched Sectigo PQC Labs. This sandbox platform, equipped with Crypto4A’s quantum-safe HSM, gives organizations a way to generate and test PQC digital certificates and keys in a secure environment. It also provides a wealth of educational tools and resources relating to strategic PKI integration.
Here’s a quick example of what it looks like once you’ve created a test PQC digital certificate:
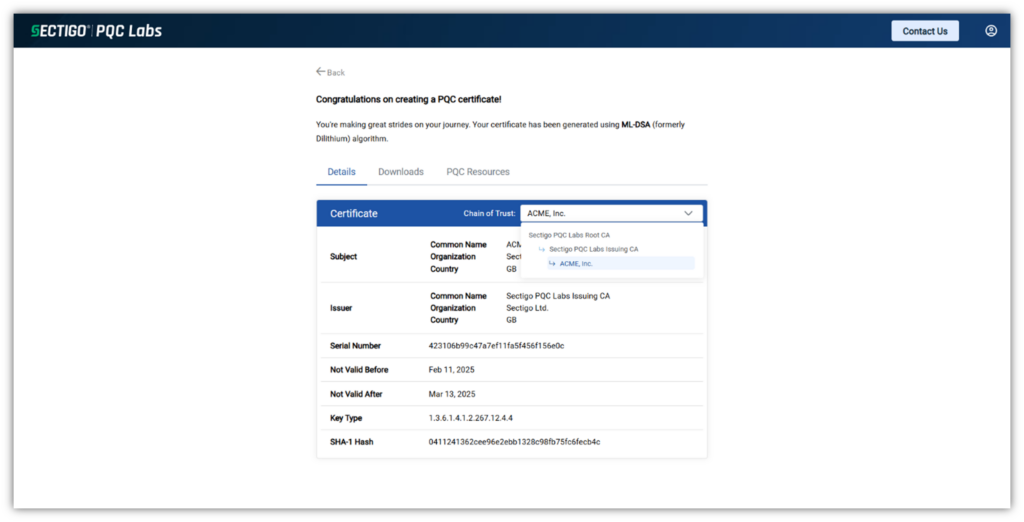
Preparing your business for quantum computing is a must, and crypto-agility should be at the heart of your organization’s PQC initiatives.
Inventory Your Cryptographic Assets and Capabilities
Of course, before you can adopt PQC, you first need to know exactly what cryptographic assets, tools, and capabilities exist within your IT ecosystem. In order to secure your PKI environment and IT ecosystem as a whole, then everything must be accounted for.
4. Ensure You’re Running Hardware and Systems That Can Support Hybrid Algorithms
It’s not uncommon to find small businesses running legacy systems. This can include everything from servers and hardware security modules (HSMs) to firewalls and routers. For example, a server’s “useful life” is generally viewed as three to five years, although some businesses are known to run servers for 10-20 years.
But running systems with long service lifespans simultaneously is a great and terrible thing. We get it — servers are costly investments that are a pain in the patootie to upgrade due to the time and migration costs, and as a small or mid-size business owner, you want to save money. But if you’re running outdated systems that aren’t receiving updates and aren’t capable of supporting PQC hybrid algorithms, then you’re asking for trouble.
This is why it’s crucial to incorporate quantum-safe capabilities into your hardware and system upgrade plans. As technology continues to evolve and each day brings us one step closer to mainstream quantum computing capabilities, traditional HSMs and other solutions no longer cut it. Use your upgrade cycle to bring your organization’s security up to snuff with PQC-capable hardware and systems.
Related resource: Up Your Game with this Small Business Cyber Security Plan Template
If you’re using third parties’ hardware and systems, then carefully assess each vendor’s PQC readiness and capabilities. If quantum readiness isn’t even a blip on their radar, it’s a good idea to find another vendor.
5. Get Visibility of Your Entire PKI Ecosystem and Inventory Everything
In order to adopt PQC, you first need to know exactly what cryptographic assets and tools exist within your IT ecosystem that must be secured and accounted for. This includes virtually everything within your public key infrastructure (PKI) environment:
- Digital certificates and their corresponding keys (noting their sizes, types, locations, which ones require quantum-resistant algorithms, etc.)
- Key storage solutions and key management systems
- Which cryptographic schemes (encryptions, digital signatures, etc.) and security protocols are in use
Sectigo Certificate Manager (SCM) offers Discovery and Visibility capabilities that enable you to identify all of the digital certificates within your landscape. This all-in-one certificate management tool allows you to securely manage your PKI certificates in a single pane of glass.

Simplify Digital Certificate Management with Sectigo Certificate Manager
Sectigo Certificate Manager is an all-in-one platform that streamlines certificate management and scales with your business. It allows you to supplement or upgrade your existing private CA capabilities and integrates directly with many third-party applications.
Take Additional Steps to Secure Your Data Now to Keep It Secure Later
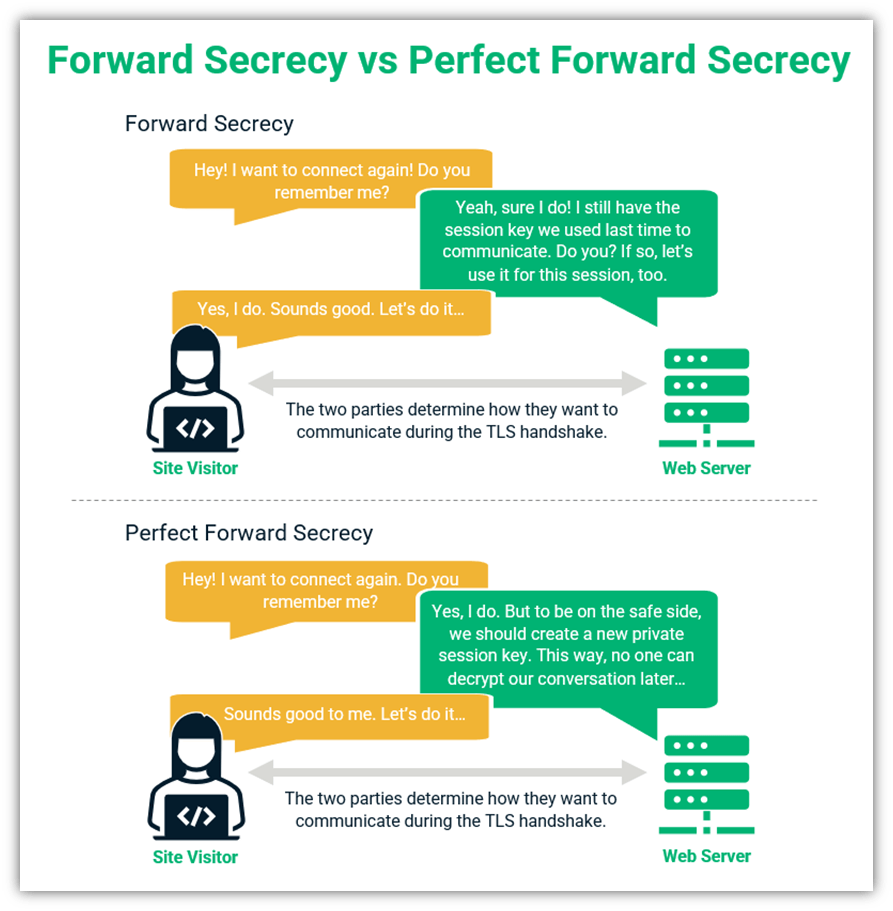
6. Enable Perfect Forward Secrecy as Another Layer of Security
Perfect forward secrecy (PFS) refers to a specific key agreement protocol set that keeps your secrets (i.e., keys) secret. The idea behind it is a two-pronged approach:
- A new, unique key is generated for each session (even for two parties that have previously connected), and
- The generated keys must never be stored (This way, they can’t be reused to secure future sessions).
This prevents data from being exposed at a later date, even if a server’s private key gets compromised in the future.
PFS isn’t a new concept — in fact, it’s actually mandated by the TLS 1.3 protocol, which eliminates the use of RSA and traditional Diffie-Hellman (non-ephemeral) key exchange protocols in the TLS handshake. (Reminder: An ephemeral key = a unique, dynamic key.)
So, the idea here is that by using a dynamic key for every session (rather than the server’s traditional static private key) that doesn’t get stored, you’ll help to ensure that your previously transmitted communications remain secure even if future communications become compromised.
This differs from forward secrecy, which involves using a generated secret key that never gets exchanged directly but does get stored for use in future sessions.
7. Don’t Hold onto Data That Your Company Doesn’t Need
Data is often viewed as one of the most valuable resources to businesses. However, storing excess data you don’t actually need can be detrimental to your business and customers. Why? Because the more data you hold onto, the higher the risk that your data may get exposed over time.
This is, in part, why many data privacy regulations — think of the European Union’s General Data Privacy Regulation (GDPR), Health Insurance Portability and Accountability Act, and the Payment Card Industry’s Data Security Standard (PCI DSS) — specify that businesses should properly (i.e., securely and safely) destroy any excess data they don’t need to carry out a service.
Harvest Now, Decrypt Later Isn’t Just a “Tomorrow” Problem
The reality is that HNDL attacks are happening now, and your sensitive data is at risk of future compromise once commercial quantum computers make their mainstream debut. The longer you wait to increase your PQC readiness, the more time cybercriminals have to steal your encrypted data.
As a small/midsize business owner or IT admin, adopting quantum-resistant cryptography into your organization’s IT ecosystem likely hasn’t been at the top of your priorities list. But knowing that your business’s data is vulnerable to harvest now, decrypt later attacks by relying on traditional cryptographic algorithms that will be broken by quantum computers should serve as a real eye-opener.
We hope that this article has provided you with some actionable ways that you can start preparing for quantum computers now to stay ahead of the curve.



















![The TLS Handshake Explained [A Layman’s Guide]](https://sectigostore.com/blog/wp-content/uploads/2023/01/tls-handshake-feature-300x200.jpg)


2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security