Is Email Encrypted? Sometimes… Here’s How You Can Tell
Although encryption is the go-to standard for Internet data security, not all service providers offer email encryption as an option. Here’s what to know about email encryption and how to tell whether an email is encrypted
Encryption is an essential component of internet and email security. In part, it’s what helps protect your communications against unauthorized users and their nefarious purposes by scrambling data into an unreadable format. This way, only an authorized individual (i.e., someone with a secret key) can read your emails.
We’ve talked previously about how you can send documents securely via email using an email signing certificate (S/MIME certificate). In this scenario, an email client uses public key cryptography to:
- Secure the message content and attachments (i.e., secure data at rest) using an S/MIME certificate
- Send messages via a secure communication channel (i.e., secure data in transit) using transport layer security (TLS) encryption
Now, it’s time to explore whether all emails are encrypted and how you can identify encrypted messages.
Is Email Encrypted? Not Always…
In general, messages transmit via the simple mail transport protocol, or what’s known as SMTP. This is an insecure transfer protocol, meaning that data can be intercepted in transit. To make the connection more secure, it requires enabling TLS to add another layer of security.
So, emails can be encrypted, but that doesn’t mean that all emails you send or receive are encrypted. This is because not all email providers support TLS; thankfully, the big ones (Gmail, Yahoo, Apple Mail, etc.) do. And this is good news because many industry regulations (HIPAA, PCI DSS, etc.) require the use of encryption to protect sensitive data. Unfortunately, some email providers opt to use SMTP on its own, which is open to man-in-the-middle (MitM) attacks (i.e., in-transit data interception attacks).
This is bad news all around. Sending data unencrypted is akin to sending your message on a postcard because the data is open to being intercepted a read by virtually anyone. This means that when you send your message, it transmits in plaintext (i.e., a readable format) instead of in a string of random characters and letters.
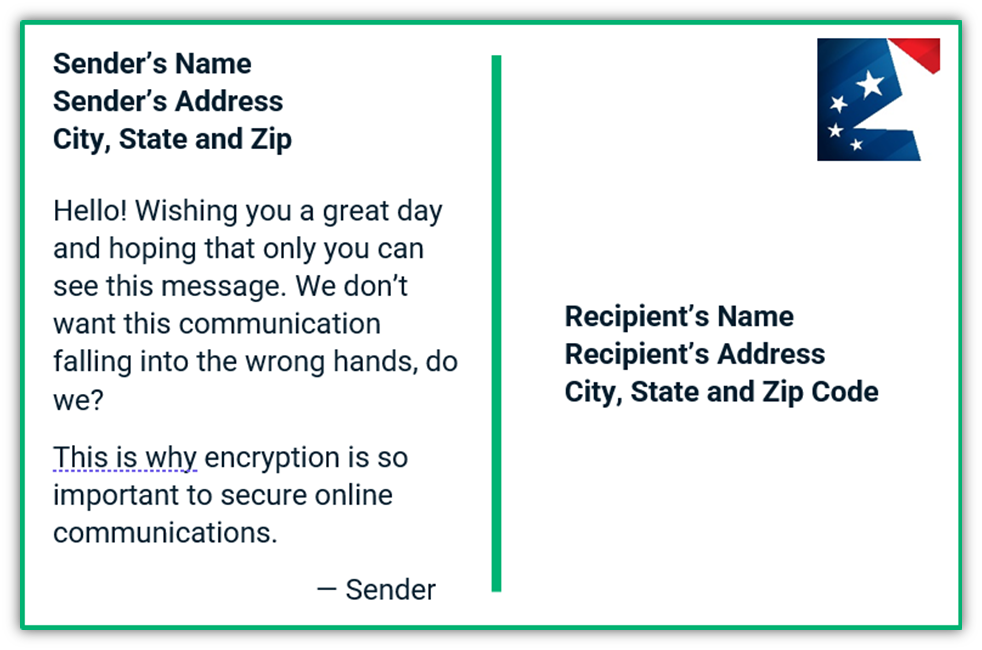
But if the message is encrypted, such as by pairing STMP with the mail transfer agent strict transport security (MTA-STS) or TLS, the attacker won’t be able to read the contents. When someone who doesn’t have access to the key tries to read the message, it would look like this to them:

3 Types of Email Encryption
There are three main types of encryption that can be used to secure email communications worth mentioning:
- Transport layer security (TLS) — This secure protocol protects your data in transit by encrypting the communication channel you use to send the data. This is often added to SMTP to make the latter more secure and prevent MitM attacks.
- Secure/Multipurpose internet mail extension (S/MIME) certificate — This requires the use of an email signing certificate (which is issued by a trusted public certificate authority like Sectigo) and secures the message itself by encrypting the email’s contents and attachments.
- Pretty Good Privacy (PGP) — This decentralized form of encryption aims to protect data at rest. It also requires a third-party tool and you have to create a code (which may or may not be secure).
Often, people will use S/MIME encryption in combination with TLS to create end-to-end encryption. This means that the email and the channel it transmits through are secured via public key encryption.
Imagine that you work in the IT department at a local hospital: you want to ensure that any data transmitted by your employees is as secure as possible. Your best bet is to instruct them to avoid sending sensitive information via email. However, seeing as how email is a common communication tool nowadays, it’s likely that some sensitive information will need to be emailed. In this case, you’ll need to ensure that it’s encrypted first to prevent prying eyes from seeing your sensitive data. We’ll quickly walk you through how to do that later in the article.
What Email Encryption Does
Email encryption involves applying a public (known) cryptographic key to data that you want to keep secret to make it unreadable. This involves applying complex math to that data that turns your readable message into a string of gibberish. Now, it’s important to note that every public key is created with a corresponding private key; together, they form a public-private key pair. So, when a message is encrypted, it means that it can only be decrypted using the corresponding private key.
Now, we’re not going to dive into the nitty-gritty of how encryption works in this article. But the important takeaway here is that it helps to secure your sensitive data against access by unauthorized users by using public key cryptography.
Both Parties Have to Support Encryption to Use It
Email encryption isn’t something that can facilitated on one end; it has to be supported by both the sender and recipient’s email clients and servers. If only one party supports encryption, then a secure connection can’t be established; this means the message can still be sent via SMTP but it’ll be insecure.
In general, email is encrypted if the sending and receiving email service providers both support transport layer security (TLS). This enables you to secure data in transit (i.e., when it moves from one party to the other).
In order for emails to be encrypted before being sent — meaning that they’re still unreadable to unauthorized users once they’re sitting on the recipient’s email server — both parties must:
- Use the same email encryption service (such as ProtonMail) or integrate a third-party tool for PGP, or
- Use email signing certificates (S/MIME certificates). This is because the sender would need to use the recipient’s public key to encrypt the message before sending it so only the recipient has the private key that decrypts it.
How Do You Know Whether an Email Is Encrypted?
Alright, now that we know what encryption is and what it does, let’s look at how you can identify encrypted email messages. The most obvious sign is when your email client displays some kind of security-related icon. Let’s take a quick look at what you see when a message is encrypted using TLS encryption only and then move on to what it looks like when a message is encrypted using an S/MIME email signing certificate.
TLS Encryption in Gmail
According to Google’s Transparency Report, 89% of outbound and 93% of inbound emails in Gmail have been encrypted thus far in 2022 (measured Jan. 1-Oct. 18, 2022). When you use TLS encryption for email, you’re securing the communication channel that the data will be sent through to the recipient. You’re not encrypting the email itself. But what does this look like? In Gmail, you’ll see a grey security padlock for messages sent using the secure TLS protocol:
If a message is sent via an unencrypted protocol, then you’ll instead see a red padlock icon with a slash through it. If it’s encrypted using an S/MIME email encryption certificate, then you’ll see a green icon with a plus sign in the middle:

End-to-End Encryption Using an S/MIME Certificate in Outlook
Now, let’s explore what it looks like when you sign the message itself using an email signing certificate. This process encrypts the message so it’s secure while sitting on the recipient’s server after you hit “send.”
When you receive an encrypted message while using Outlook on a Windows device, you’ll see a yellow padlock as shown below:
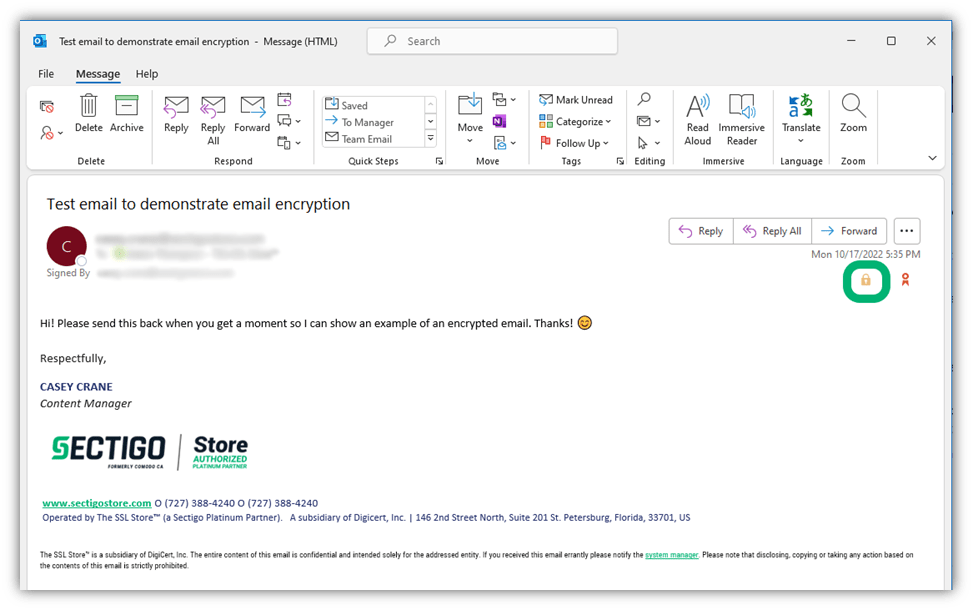
In Outlook on a Mac, you’ll see the following grey padlock when you receive an encrypted email:
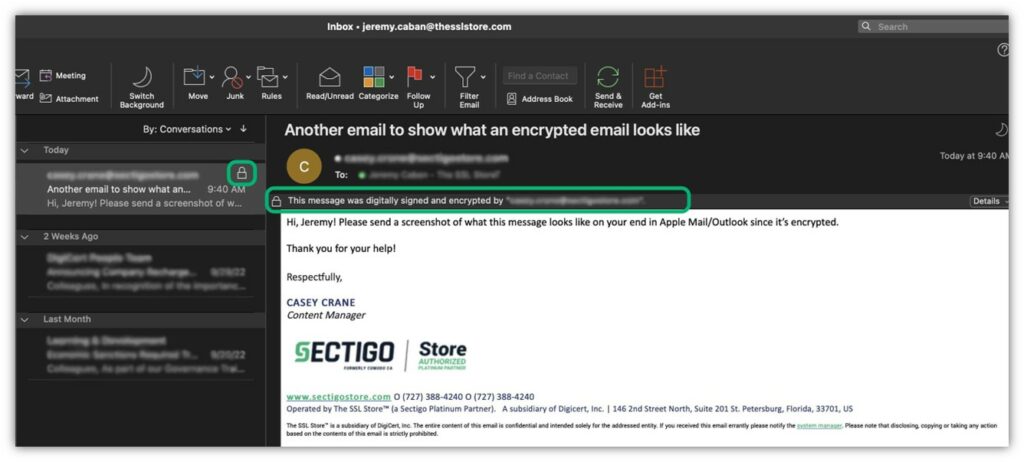
All of this is great, right? But you may wonder how you can tell whether the encryption is legitimate. This is another advantage of using these digital certificates: they help you assert your digital identity in a verifiable way.
When you click on the padlock icon when using Outlook on Windows, you’ll see a new window popup that displays the message’s security properties information. (Basically, this is information regarding the S/MIME email signing certificate that was used to sign the message.) Here’s a quick progression of the information you can see when you click through the different encryption and digital signature layers:
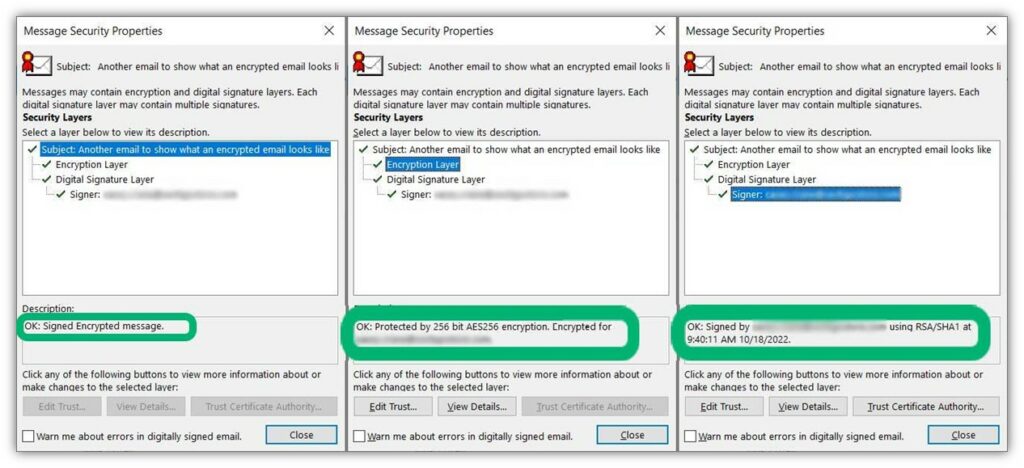
Sending an Email Using S/MIME Is an Easy Process
Sending an email using an S/MIME certificate is easy once you have it installed in your email client. We’ll use Outlook as an example. Simply have the recipient send you a digitally signed email; this will give you their public key. Once you have that, then you can use it to digitally sign and encrypt your email.
Simple create a new email, add all of your content and any attachments. Next, select Options > Encrypt > Encrypt with S/MIME in your top navigation bar:
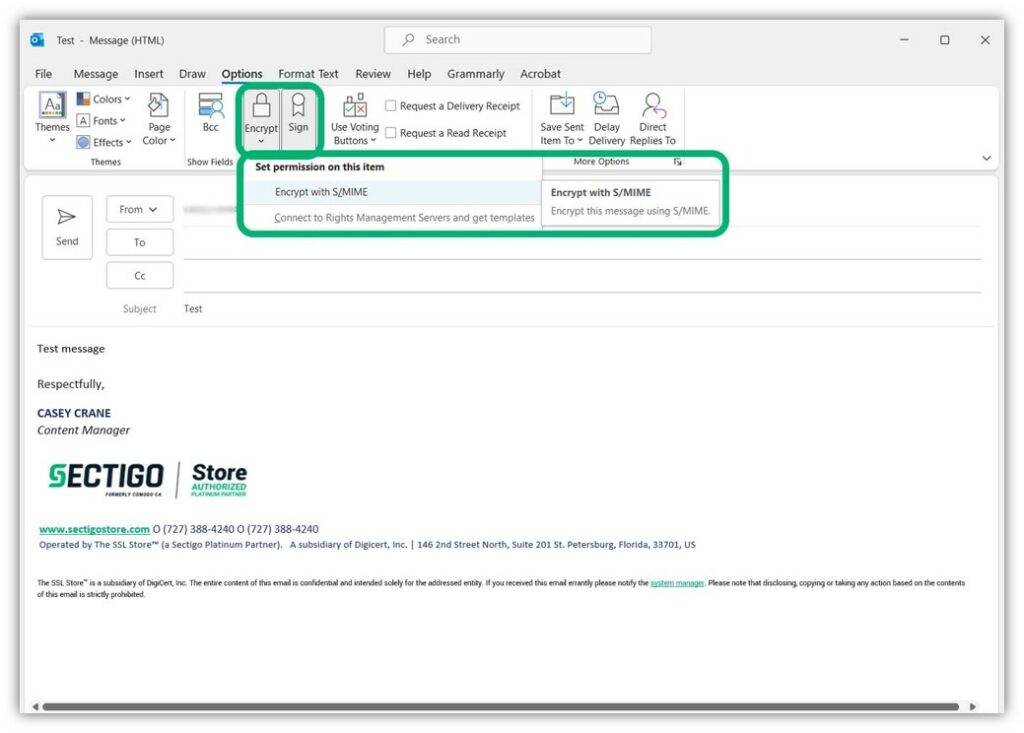
After that, simply send the email and it’ll be encrypted automatically. Yup, it’s really that simple. Now, your message is encrypted and can only be opened by the recipient who has the private key.
Final Thoughts on Email Encryption
As you’ve learned, not all emails are automatically encrypted (even though they should be). The good news, though, is that most major email service providers do use TLS encryption to secure their customers’ messages in transit. But if you need another layer of security to send sensitive data, then you need a little something extra to secure your messages while they’re sitting on the email server. A common way of achieving this outcome is to use an S/MIME certificate.
When you talk about encrypting emails, it sounds like it would be a highly complicated and involved process. But as you’ve learned, it’s really not; virtually anyone can do it when they have the right tools (such as an email signing certificate) in place.




















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security