8 Practical PKI Uses & Applications That Drive SMB Security
More than half of the breaches investigated by Verizon in its 2025 DBIR report stemmed from system intrusions. Discover which PKI use cases every small and mid-size business can implement to minimize these risks (and others)
In our previous article, we introduced you to public key infrastructure (PKI), a framework that enables organizations of all sizes to prevent cybersecurity threats and minimize the risk of attacks. From securing emails and website data to adding layers of security to your software and network devices, there are many PKI uses and applications that every small and mid-size business should know.
Now, we’ll explore eight specific PKI use cases demonstrating how small and mid-size businesses can use this technology to their advantage.
Editor’s Note: This article is the second in a three-part series that dives into the details of PKI technology. This series explores the roles of PKI technology in IT security, examples of PKI uses and applications small and mid-size businesses can enjoy, and answers the question “how does PKI work?“
8 Examples of PKI Uses and How They’ll Benefit Your Organization
PKI uses digital certificates and cryptographic key pairs to secure public and private resources. Although people typically associate it with SSL/TLS certificates, PKI is a set of versatile tools and a framework that can do much more than “just” protect websites and applications.
Here are some PKI uses that can help you turn your cybersecurity plans into action, all without breaking the bank.
1. SSL Certificates Secure Your Website Data & Transactions
It seems only fitting to start with one of the most obvious and common PKI uses: the secure socket layer/transport layer security (SSL/TLS) certificate. This type of digital certificate can be used to secure internal and external site resources — for example, public-facing websites and web apps, as well as intranet sites and web apps. The difference here boils down to whether you’re using a public certificate or one from an internally trusted certification authority (i.e., private PKI).
When you install an SSL/TLS certificate on your public-facing web server, PKI uses it together with the related key pair to:
- Authenticate your website’s identity to clients (i.e., any device/browser that a customer uses to visit your website),
- Secure the information exchanged between the two parties (e.g., passwords, credit card data) via a secure transmission channel to protect it from interception,
- Protect the transmission’s integrity against tampering by malicious third parties.
NOTE: Publicly trusted SSL/TLS certificates are valid for a maximum of 398 days. However, their validity period will drop to 47 days by 2029.
An Example of How This PKI Use Case Would Work for Your Organization
Let’s look at this PKI use case of a publicly trusted SSL/TLS certificate.
Before a customer places an order on your website, they’ll want to verify that your website is legitimate. With an organization validation (OV) SSL/TLS certificate (as a minimum), all they have to do is click on the padlock icon (in Firefox) or the Tune icon (in Chrome) located next to the website’s URL in the browser’s web address bar. This will bring up options where users can view your organization’s Subject details in the site’s SSL/TLS certificate:
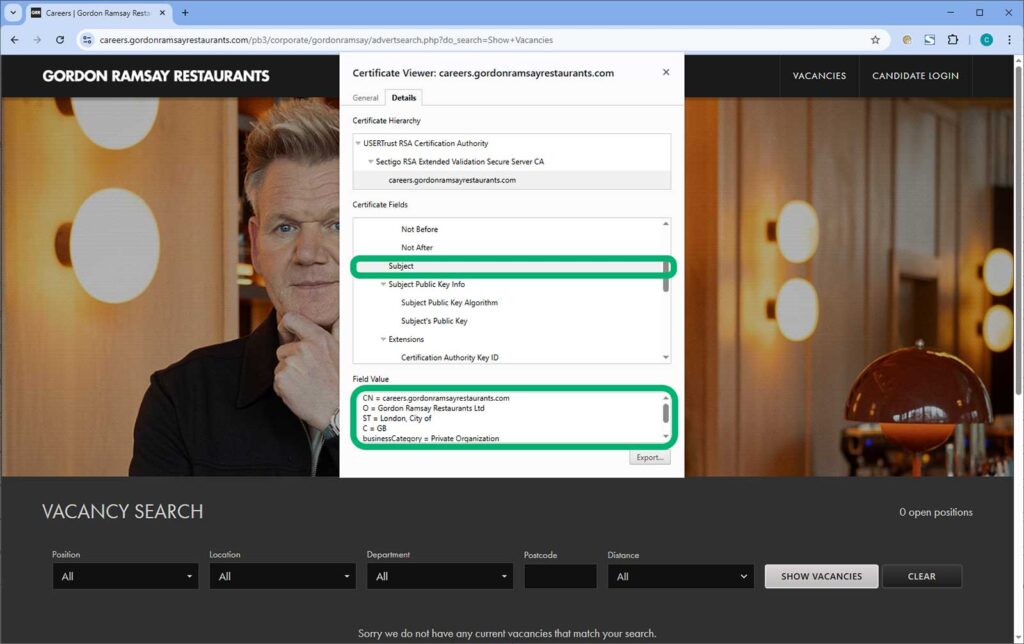
Now, let’s talk about protection. The customer places an order and needs to sign in to make an online payment. If you’ve properly installed and configured your certificate, then you can harness the power of PKI (including secure cryptographic protocols, algorithms, and the site’s SSL/TLS certificate for server authentication) to ensure the confidentiality and integrity of the data exchanged between the client and your web server.
Without it, bad guys can use man-in-the-middle attacks (MiTM) to
- intercept your data in transit,
- steal credit card details and personally identifiable information (PII), and/or
- carry out other nefarious acts.
Save Up to 87% on SSL/TLS Certificates
Get the lowest prices on trusted SSL certificates from Sectigo.
Shop SSL Certificates2. Digitally Sign and Secure Your Emails with End-to-End Security
PKI uses and applications extend beyond securing websites. Did you know that PKI technology adds security layers directly to your outbound email messages as well? Here’s how:
- Encrypts your mail server’s communication channels. You can install an SSL/TLS certificate on your email server to transmit messages via a secure connection. That protects your email against MitM attacks that can otherwise enable hackers to steal your data, alter it in transit, or result in data confidentiality issues.
- Proves the authenticity and integrity of your messages. Installing an S/MIME certificate (i.e., an email signing or personal authentication certificate) enables you to add a cryptographic digital signature to your emails. This uses cryptographic hashing to prove to recipients that your message hasn’t been altered since the sender signed it.
- Secures your email contents before they leave your inbox. An S/MIME certificate also enables you to encrypt messages when both parties (i.e., the sender and recipient) are using valid S/MIME certificates. This PKI use case helps you protect the confidentiality of your communications.
An Example of How This PKI Use Case Would Work for Your Organization
Imagine you need to share a prospective customer’s personal info with a colleague in another geographic region via email. You want the recipient to know the message is legitimate and uncompromised, so you add your cryptographic digital signature to the message to authenticate it and protect its integrity.
Thankfully, your coworker also has an S/MIME certificate, so you ask them to send a digitally signed message so you can grab a copy of their certificate’s public key. (This allows you to use the coworker’s key to encrypt the contents of the email itself to protect the customer’s privacy.) Since the message is sent via an email server that has an SSL/TLS certificate installed, this S/MIME-encrypted and digitally signed message is also transmitted via a secure channel.
Together, these security measures facilitate end-to-end encryption because the email is secure both in transit and at rest in the recipient’s inbox.
Save 15% on a Sectigo Email Signing Certificate
Add layers of security to your email communications with a trusted email signing certificate from Sectigo.
Shop Email Certificates3. Protect the Integrity and Reputation of Your Software and Code
Did you create a new software application, driver, or another type of code? That’s another perfect PKI use case. With the support of a code signing certificate and its public and private key pair (the latter stored on secure hardware), PKI lets you:
- Attach a unique digital signature to your new code. Think of it like posting a sign that says, “Hey, I made this. Therefore, you can trust it.”
- Prove that no one has modified the software without authorization. By protecting the integrity of your code using a cryptographic digital signature, you’re providing assurance and a way to verify that it’s safe to download and install.
Using a code signing certificate boosts your reputation by protecting the integrity of your software application products against tampering.
An Example of How This PKI Use Case Would Work for Your Organization
Say, our sample customer purchased a software program from your website. If you use a code signing certificate to add your digital signature to the code, the user will immediately know whether they can trust and install the application.
Here’s how PKI does its magic, in a nutshell. When the customer downloads your software, their client generates a new signature hash and compares it with the original hash created when you signed the code.
- If the hash values match, the software is safe to install.
- If they don’t, the user is alerted, and the installation is blocked.
The example below shows what happens when my colleague hashes a .txt file, makes a change to the file, and then re-hashes the file using the same command (in this case: certutil -hashfile c:\example-filepath\test_document_name.txt SHA256):
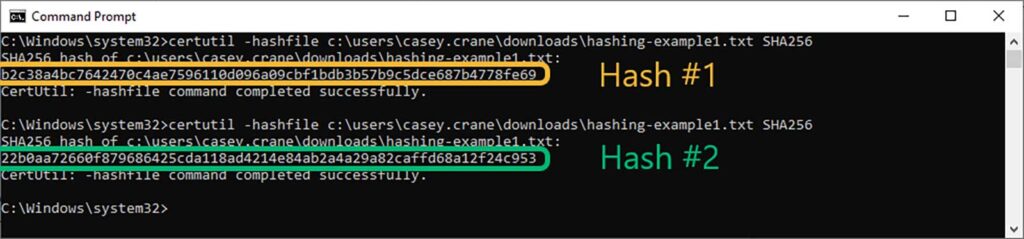
What does this accomplish? It indicates when your software applications or code have been altered after being signed.
Save Up to 42% on Sectigo Code Signing
Users can no longer afford to blindly trust unsigned software. Adding your digital signature provides assurance that your software is legitimate and hasn’t been altered.
Get a Code Signing Certificate4. Secure Your Software Supply Chain Against Cyber Threats
A publicly trusted code signing certificate does more than keep malware away and protect it from tampering. It also shields your software supply chain from attacks. How? By using PKI to help secure your code from start to finish by:
- Signing each component during the full software development life cycle (SDLC). It helps you prevent and identify malicious code injections, protecting your organization and customers from malware infection.
- Fostering secure development best practices. Everybody in the team becomes responsible for the security of the code. As a result, every application created will be more stable, easier to maintain, and more resilient against potential attacks.
Pro Tip: A software bill of materials (SBOM) lists all components in your code or software application. Signing it with a code signing certificate will add another layer of protection to your software supply chain.
An Example of How This PKI Use Case Would Work for Your Organization
Imagine that you’re a small software publisher and that the code the customer bought from you was developed internally by your team. To add another layer of protection to your code, you decide to use PKI.
How? By signing the code right at the beginning of its building phase. You then automate code signing and embed it into your SecDevOps continuous integration and continuous delivery (CI/CD) process. Any subsequent patches and updates should also be digitally signed.
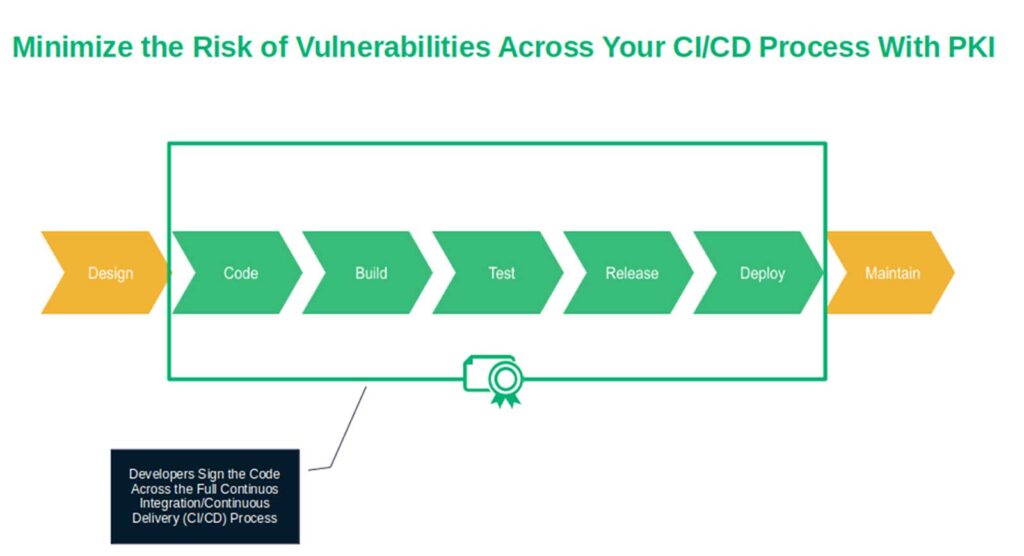
Boom. You’ve drastically reduced the risk of vulnerabilities by ensuring that the source code and its components are defended against hackers at every step of your SDLC. Furthermore, your developers can verify the integrity and authenticity of the code whenever they want/need, regardless of which stage the development is at. Goodbye, deployment of infected or vulnerable code.
Pro Tip: If you create Excel macros and own a code signing certificate, you can sign them, too.
Save Up to 42% on Sectigo Code Signing
Users can no longer afford to blindly trust unsigned software. Adding your digital signature provides assurance that your software is legitimate and hasn’t been altered.
Get a Code Signing Certificate5. Prove That Your Documents Are Authentic and Legitimate
Do you send out invoices or exchange information within your organization in a PDF format? The Check Point Research team recently discovered that 22% of malicious email attachment attacks in 2024 weaponized the commonly used PDF format.
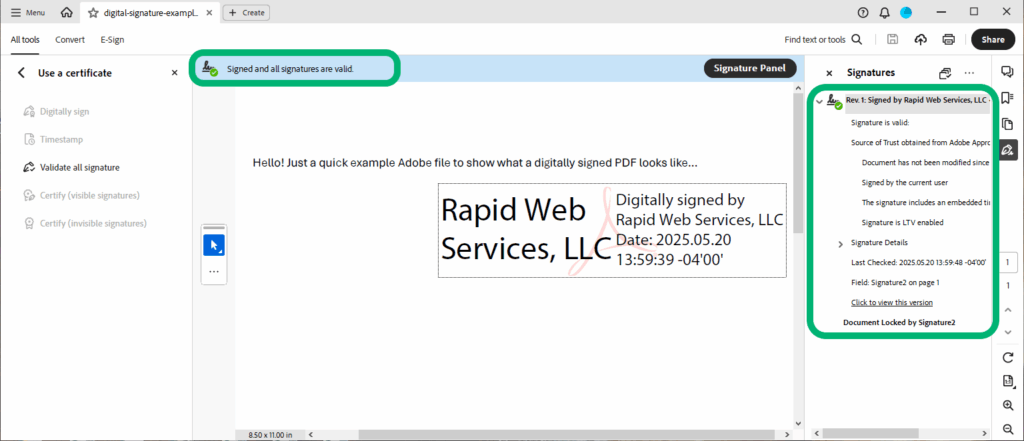
A document signing certificate is a PKI use case that safeguards your precious Microsoft Office and Adobe PDF documents from malware infections. So, every time your signature is added to a document that a user downloads or opens, PKI:
- Asserts your digital identity. A digital signature will confirm that the PDF is legitimate and hasn’t been replaced by a phony one.
- Enables their operating system to compare the signature hashes. This simple action lets users corroborate that no one has modified the document since it was signed.
- Aids your organization’s reputation and builds trust in its products. A digital signature is like a quality label that lets you build instant trust in your brand and products.
An Example of How This PKI Use Case Would Work for Your Organization
Let’s refer back to that customer of yours from our previous examples. Imagine that the customer now wants to sign up for one of your services. They need to digitally sign a contract, and you want them to feel confident knowing that the document is legitimate and really came from your company.
Guess what? PKI technology helps here, too. Purchase a document signing certificate from a trusted CA or reseller such as SectigoStore.com and use it to apply a digital signature to your file. Once you’ve cryptographically signed the PDF, the deed is done. PKI will reassure anyone opening it that you made the document and a malicious third party didn’t mess with it since you signed it.
Save Up to 19% on Sectigo Document Signing
Need to sign PDF documents to verify their authenticity and integrity? We’ve got you covered.
Get a Document Signing Certificate6. Secure and Authenticate the IoT Devices on Your Network
Between the end of December 2024 and early 2025, critical services worldwide were brought to their knees via massive botnet DDoS attacks that leveraged the power of artificial intelligence (AI) and exploited Internet of Things (IoT) devices’ vulnerabilities (e.g., hardcoded default passwords).
Think about all the IoT and personal devices connecting to your organization’s network. Now, imagine the damage such an attack could do to your company, considering that the average cost of a data breach was a whopping $4.88 million in 2024. Scary, right?
PKI and device certificates give you peace of mind by identifying and authenticating hardware within your network without requiring a physical password and username. Using the same process we’ve already explored, PKI works hand-in-hand with a device certificate to:
- Prove the authenticity of connecting hardware. IoT devices such as wireless cameras, routers, thermostats, and wireless printers.
- Manage their identities and security. Each IoT device gets its own digital certificate that proves its identity.
- Ensure that only authorized and verified devices access your organization’s resources. Rogue devices become a problem of the past when you take this approach.
Pro Tip: X.509 certificates and PKI work with virtually any kind of IoT device, even with your self-driving car, smart fridge, or surveillance system.
An Example of How This PKI Use Case Would Work for Your Organization
It’s no secret that IoT devices tend to be more vulnerable to attacks than other devices. However, that doesn’t mean they’re bad for your business or that you should stop using them. For instance, think about wireless security cameras. Installed on your premises, they keep your property physically secure, so long as they aren’t left unmanaged or tampered with.
So, when you install them, equip each one with an IoT device certificate. Like other PKI certificates, an IoT device certificate includes identifying information (in this case, about the specific device) and is combined with a public-private key pair. However, these certificates are different in that specialized IoT PKIs issue them, and they typically have different uses and longer lifespans. When you switch the wireless camera on, the device and the server automatically authenticate (i.e., mutual authentication) in the background. No password needed. Now, you can ensure that only authorized IoT devices can access your organization’s network and its sensitive resources.

7. Provide Secure Virtual Private Network (VPN) Authentication
ZScaler ThreatLabz 2025 VPN Risk Report found that 56% of companies polled struggle to keep their VPN connections secure and compliant. Sounds familiar? PKI certificate-based authentication boosts your VPN security by:
- Allowing your users to connect without risks. User IDs and passwords can’t be stolen via phishing attacks or keyloggers if you don’t use such access credentials in the first place.
- Verifying the users’ identities in the background. The PKI process uses theinformation vetted by the trusted CA and embedded into the device certificate to confirm the legitimacy of the user.
Pro Tip: VPN isn’t always easy to integrate into a secure infrastructure. However, Sectigo Certificate Manager simplifies issuing and managing certificates in a single pane of glass.
An Example of How This PKI Use Case Would Work for Your Organization
Picture this: it’s your day off. You’re enjoying a cappuccino at your favorite coffee shop. However, like many business owners, you can’t take your mind off that key project you and your team have been working on and feel compelled to check its status. To safely access your organization’s project tracking tool, you open your VPN so your PKI client certificate can protect your connection from snoopers and MitM attacks.
Instead of being prompted to type your username and password, which could be stolen or spied on when using the coffee shop’s unprotected network, PKI flips the script by enabling the VPN to automatically recognize and authenticate your device. Voila’. You can now access your project management tool, look for any updates, and finally enjoy your day off with the confidence that everything is on track.
8. Protect Your Cloud-Based Application and Services
The Cloud Security Alliance recognizes identity and access security control as one of the top 2025 essential actions to keep cloud services secure from today’s most dangerous threats (e.g., data breaches, AI-based attacks, and ransomware). Why? Because without verified identity and authentication, anyone with access to an API could request data that could result in unauthorized access, data breaches, and a slew of other issues.
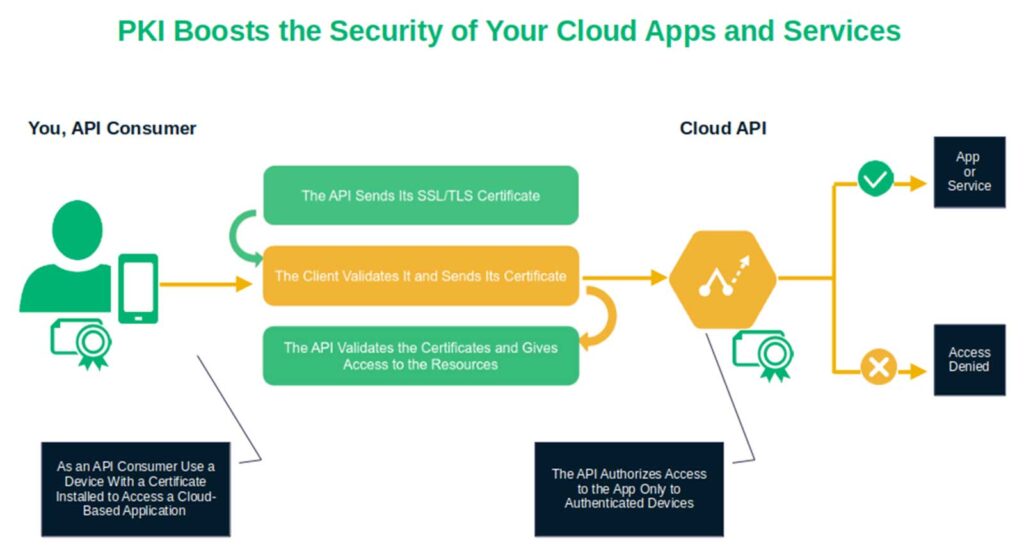
Once again, PKI facilitates certificate-based authentication to secure API access and user login. This way, cloud apps and services can use mutual authentication (i.e., mTLS) to:
- Immediately verify users, services, and applications’ identities. All these actions are executed without requesting a password, thereby reducing the risk of breaches.
- Block rogue devices from accessing your API. With mTLS, the client and the server must authenticate each other to establish a connection. This prevents the bad guys from breaching your API with a dodgy device without a valid certificate.
NOTE: Although self-signed certificates are cheap and handy, they also won’t (and shouldn’t) give you access to those apps and APIs using certificate-based authentication because they’re untrusted.
An Example of How This PKI Use Case Would Work for Your Organization
Suppose you have a cloud app that includes customers’ sensitive information accessed only by a few of your employees. You have already secured it with an SSL/TLS certificate so that all data exchanged goes through a hypertext transfer protocol secure (HTTPS) connection.
You have also set password-protected access and limited access to specific IP addresses via whitelisting. However, you still feel uneasy — and rightly so, considering that Specops’s latest analysis confirms that 230 million stolen passwords met the standard complexity requirements.
Will PKI help in this case, too? You bet it will. Instead of having authorized users rely on passwords that can be phished, stolen, or guessed, they can instead use device certificates that the server will recognize as unique identifiers. So, when your employee attempts to access the app, the client and the server exchange their certificates and mutually authenticate. The client can then access the application via an encrypted connection.
Take Your Existing Microsoft CA to the Next Level with Sectigo Private PKI
Sectigo Private PKI is a managed PKI service that complements your Microsoft CA and expands it to protect the non-Windows devices on your networks.
It works with Sectigo Certificate Manager to simplify and streamline certificate deployment and management across all devices and applications within your ecosystem.
Did an attacker attempt to access your app without a device certificate or using a self-signed certificate? The connection will terminate right away, and they’ll be denied access.
Final Words About PKI Uses and Applications for Small and Mid-Size Organizations
Did you realize there were so many PKI use cases for SMBs? PKI and digital certificates are a surprisingly affordable way to secure your assets and organization. They’ll also help you implement a zero-trust security strategy where no one is trusted by default, and everyone’s identity is verified.
It’s time to empower your small business with enterprise-grade security. Pick your favorite PKI use cases, implement them using digital certificates, and transform your reactive organization into a proactive and resilient company that your customers can trust.





















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security