WP Security: The Ultimate Guide to WordPress Security
Make yours a secure WordPress site with these 10 proven, easy-to-implement tips and keep the hackers away
WordPress is a real blessing for bloggers, freelancers, and startup business owners. You don’t need to pay thousands of dollars for software development and maintenance. Anyone can simply learn WordPress with online tutorials and start promoting their business, products, or services right away. But what about WordPress security? Sucuri reports that 90% (i.e., 9 out of 10) of their total clean-up requests are from WordPress sites.
Because WordPress is an open-source technology, anyone can make plugin and theme. These plugins and themes might have a weak security structure or contain malware. Wpvulndb.com reports that they have a total of 21,785 vulnerabilities in their database — of these vulnerabilities, 80% are WordPress, 17.8% are plugins, and 2% are theme.
The irony is that startups generally choose WordPress because they have a tight budget, lack programming knowledge, or are looking for an easy-to-use platform. If you’re one of them, you might be asking, “So, do I have to hire a techie and spend thousands on securing my website?” The answer is, “No.”
In this article, we’ll cover 10 proven and powerful tips to secure WordPress sites. The plugins and products suggested in the article are either free or inexpensive.
10 Proven Tricks to Make Yours a Secure WordPress Site
We have included some of the best freemium or least expensive security plugins and tools that are easy to use and won’t add burden to your pockets. Even a non-tech savvy person can instantly apply these tips to secure WordPress sites.
WordPress Security Tip 1: Block Malicious and Spam Comments
How: Install plugins like Akismet, CleanTalk, or Antispam Bee to detect and remove spammy and malicious comments.
Why: If you have a blog or discussion section that allows people to post comments, you must be beware of malicious comments. The hackers write scripts and codes in the comments to hack the website or get inside the WordPress database. They also insert backlinks to their website and unsolicited advertisements about their product/service. Akismet, a WP security plugin to remove malicious comments, has blocked more than 503 billion spam comments to date (as of Sept. 24, 2020).
WordPress Security Tip 2: Limit Login Attempts
How: Install plugins like Limit Login Attempts, Loginizer, or WPS Limit Login, to enable login lockdown feature to secure WordPress site.
Why: All WordPress sites allow unlimited login attempts by default. That means users have unlimited chances to insert their user IDs and passwords in the login field until they figure out the right credentials. This lack of control is very appealing to hackers who can exploit this feature with brute force attacks.
In this type of cyber attack, hackers use a script or bot to apply a database of pre-guessed user IDs and passwords automatically to websites’ login fields until one of the attempts is successful. Sometimes a botnet is used, where a large number of infected devices deploy the brute force attack on a targeted login field.
The best way to prevent brute force attacks is by limiting the number of logins attempts a user can make in a specific period. After the set number of failed login attempts (generally 3 to 5), the system temporarily blocks the user/IP address.
WordPress Security Tip 3: Regularly Scan Your Website
How: Install WordPress security scanners and firewalls to detect and remove threats. One such example is cWatch, scans your website and provides detailed reports on a variety of threats and vulnerabilities, including malware, brute force attacks, and DDoS attacks. Sectigo’s HackerProof Trust Mark provides scans of your website on a daily basis to identify vulnerabilities and offer actionable intelligence on mitigation.
Why: Cybersecurity is an ongoing process that often involves detecting and removing malware. You need a malware scanner and firewall that monitors your website 24/7 for cyber attacks and malware-related threats. It must be efficient enough to remove the malware, block suspicious IPs, and prevent the cyber attack in the initial stage only to cease further damage.
WordPress Security Tip 4: Encrypt Website Data Exchanges
How: Install an SSL/TLS certificate on your website. It’s always best to choose a commercial TLS certificate because the free ones don’t come with any sort of support or warranty in the event that something goes wrong. And paid commercial certificates won’t break the bank, either — in fact, many cost less than $10 per year! Use the Really Simple SSL plugin to ease the installation process.
Why: If you don’t install an SSL/TLS certificate, all the browsers will show a “Not secure” warning next to your domain name in the address bar. This message indicates a major security flaw, showing that the data your users’ browsers and your server exchange is unencrypted. Hence, if the hacker breaks the internet network and gets access to the data, they can read, interpret, modify, and steal it. Your website will be vulnerable to man-in-the-middle (MitM) attacks.
The SSL/TLS certificate will encrypt the data using public key infrastructure (PKI) processes and technologies. PKI is the framework for public-key encryption (asymmetric encryption), which is a strong mathematical algorithm that assures robust data security in transit. It will remove the “not secure” warning in front of your domain name and will display a green or grey padlock symbol (depending on your browser).
Note: After installing your certificate, you must regularly manage it. If it gets revoked or expired, all the browsers will show “your connection is not private” or “security risk ahead” error page to your website visitors. You need to renew free SSL certificates every three months (90 days) and commercial ones at a maximum of two years (more specifically, 398 days). Free certificates have a bad history of getting revoked, too. So, just choose your SSL/TLS certificate wisely.
WordPress Security Tip 5: Enable 2FA as a Minimum
How: There are many two-factor authentication (2FA) tools such as Two-Factor, WordPress 2-Step Verification, Unloq Two Factor Authentication, etc. There’s also Google Authenticator, which is free and simple to implement.
You need to install the Google Authenticator plugin on your WP site and download the Google authenticator app on your cell phone. Every time you log in to your WordPress dashboard, you need to provide a unique code generated on your cell phone on the Google Authenticator app. It also works for multiple site admins, employees, and co-authors.
After completing the installation process, your WP admin login page would look something like this:
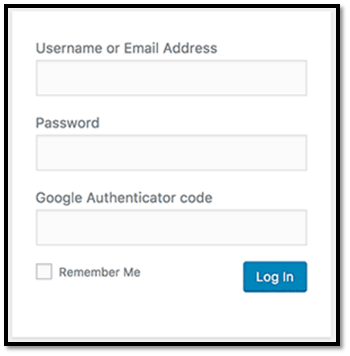
Note: 2FA is a term that’s often interchangeably used with multi-factor authentication (MFA). Any authentication that has two or more authentication processes fall under the umbrella of MFA. So, all two-factor authentication is a type of multi-factor authentication, but not all MFA is 2FA. Got it?
Why: Two-factor authentication is more secure than passwords alone. After all, passwords can be stolen, leaked, or guessed. According to Verizon’s 2020 DBIR, 80% of breaches within hacking involve brute force or the use of lost or stolen credentials.
As we mentioned earlier, hackers even use brute-force attacks to find the right user ID-password combinations. But when you enable two-factor authentication, no one can break into your WordPress admin dashboard because the only person holding the cell phone can access the unique code, one-time password (OTP), or secret PINs.
WordPress Security Tip 6: Scan Your Backups Before Storing Them
How: We strongly recommend CodeGuard because it automatically creates a backup of your site, scans it for malware, removes if it finds anything suspicious, and stores only the clean copy on a third-party platform.
Why: We all know that maintaining a current backup is crucial to the health and security of your online business. If the hacker has locked your website’s file, folders, and databases for a ransomware attack, you can easily restore it using your secure backups. But if an attacker inserts malicious code into your website, and if you take a backup without first scanning it, that malware will be stored in your backups, too. So, the backup copy will be useless, and you’ll have to build your site from scratch!
In short, all your backups won’t help you when you actually need them! Hence, the best WordPress security practice is to scan the backups before storing them. CodeGuard is one of the most efficient backup tools that will automatically scan your entire website and databases before taking the backup.
WordPress Security Tip 7: Change Default Settings
How and why: Because WordPress has a default structure for URLs, file names, and storage locations, it’s easy for attackers to find important pages and files to hack them. You should manually change these paths and file names to something unique so that only you know where to find them.
You can follow the below-mentioned tricks using plugins such as iThemes Security or WP-DBManager.
1. Change your file and web page names.
WordPress has default admin page URLs,
- www.yourdomain.com/wp-login.php, or
- www.yourdomain.com/wp-admin
Be creative and change your admin page URL to something unique like www.yoursite.com/greenelephant.php or www.yoursite.com/alaskacruise, etc.
Why: If you are using the default admin page URL, anybody can easily reach the admin login page and use bots to activate the brute force attack. But if your admin URL is unique, only the person having the exact URL can access your login page.
2. Don’t use the default “admin” as your admin user ID.
Use an email address or any unique word as your admin user ID instead of using “admin.” You can do it from your hosting account, too.
Why: When you install the WordPress on your hosting site, it will give the option to set the user ID as “admin” by default. Hackers are aware of that fact. In a brute force attack, the user ID and password should match. And when your user ID is admin, the hacker’s job becomes 50% easier. Now, they just need to try different passwords for the “admin” user ID.
3. You should change the table name in your WordPress database.
By default, a table uses a wp-table prefix. Change it with a unique name like summerwp- or coolwp- or somethingnewwp- etc. Follow this guide to change the prefix with some unique name: Instruction for changing table prefix in WordPress
Why: All your login credentials, user info, transaction details, audit logs, etc. are stored in these tables. That’s why it’s quite popular among hackers. They use bots to search and break into this database.
4. Move your wp-config.php file from the root directory.
Your wp-config.php file is by default in the root directory and can be accessible to a hacker. Move the wp-config.php file from the root directory to any other folder above the root directory. Follow these instructions: Change the location of the wp-config file.
Why: Wp-config.php file stores information about your website’s important settings, configurations, WordPress authentication keys, and databases. When you store files in well-known places (such as the root directory), it becomes easy for attackers to exploit URL access vulnerabilities for forced browsing. That’s why you must shift the wp.config.php file to a secure location.
WordPress Security Tip 8: Require Strong Passwords
How: Install plugins like Password Policy Manager or Force Strong Passwords to ensure that all of your users create strong passwords.
Why: By default, WordPress doesn’t force users to make a strong password (one uppercase, one lowercase, one digit, and one special character). Not all your co-authors, employees, and customers are going to be as serious about setting passwords as you are.
According to NordPass, the average user has 70-80 passwords. It’s really difficult to memorize 80 unique passwords, so people often use weak passwords or reuse their passwords across multiple accounts. Avast reports that 83% of Americans use weak passwords, and 53% of Americans use the same password to protect multiple accounts. That’s why you must use the plugins that force the users to create strong passwords when they register or create an account on your website.
WordPress Security Tip 9: Block Image Hotlinks
How: We recommend three methods to secure the WordPress site from image hotlink. You can choose one of them.
1. Use a Firewall
Some reputed firewall plugins (like All in One WP Security and Firewall) have a feature to block image hotlinks. You just need to go to your firewall’s settings, search for the image hotlinks section, and enable it.
2. Enable Hotlink Protection via cPanel
In cPanel, go to security section, locate Hotlink Protection and click on it. On the next page, select Enable.
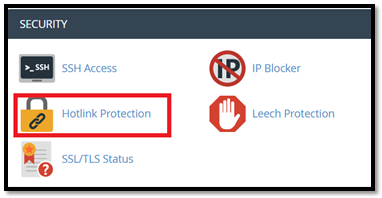
3. Insert Code Into Your .htaccess File:
- Go to your cPanel> File manage> public_html>.htaccess.
- Right-click and select View/Edit.
- Scroll down and at the bottom of the page and copy-paste the following codes:
/* Prevent image hotlinking in WordPress */
RewriteCond %{HTTP_REFERER} !^$
RewriteCond %{HTTP_REFERER} !^http(s)?://(www\.)?yourdomainname.com [NC] RewriteCond %{HTTP_REFERER} !^http(s)?://(www\.)?google.com [NC]
RewriteRule \.(jpg|jpeg|png|gif)$ – [F]
*Write your website’s URL on the place of yourdomainname.com
The third line, where we have written “google.com,” indicates that Google is allowed to use your images. Add the same code line for all other websites like LinkedIn, Facebook, Twitter, etc. if you want these sites to access your website’s images.
For example:
RewriteCond %{HTTP_REFERER} !^http(s)?://(www\.)?facebook.com [NC] Why: When third-party websites directly link your images’ URLs to their website, it is known as image hotlinks. People hotlink images because it is quick, easy, and doesn’t require them to host the images on their server, which otherwise can be highly space consuming. Hotlinks use your website’s bandwidth and reduce the speed and performance of your webpages. They also create an undue burden for your server with little to no benefit to you.
WordPress Security Tip 10: Keep All WP Components Updated
How: Install the updates for WordPress software, themes, and plugins as soon as the new versions are available. Never delay or ignore the updates as they are essential for WP security.
Why: Updates are not only for tweaking the appearance and functionality of the software. The old versions generally have security bugs that attackers can exploit to hack your WordPress site or insert the malware in it. The publishers fix the security vulnerabilities in the old versions and publish the patched version. Hence, always install the updated version of all the WordPress components.
Final Thoughts on WordPress Security
WordPress is indeed a revolution in the world of technology due to its ease of use and free components. But when a technological platform is so famous among millions of people, it also attracts the attention of cybercriminals.
Needless to say, the need for WordPress security isn’t going anywhere anytime soon. This is why it’s imperative that you ensure you’re running a secure WordPress site (as much as possible, at least).
Wordfence, a leading WordPress security provider, blocked a total of 3,818,725,238 cyber attacks and blacklisted 202,650 malicious IPs between Aug. 14 and Sept. 14, 2020. These numbers show that it’s high time to take WordPress security seriously. By following the above mentioned ten tips, you will be able to strengthen your WP site’s security posture.














 (23 votes, average: 4.48 out of 5)
(23 votes, average: 4.48 out of 5)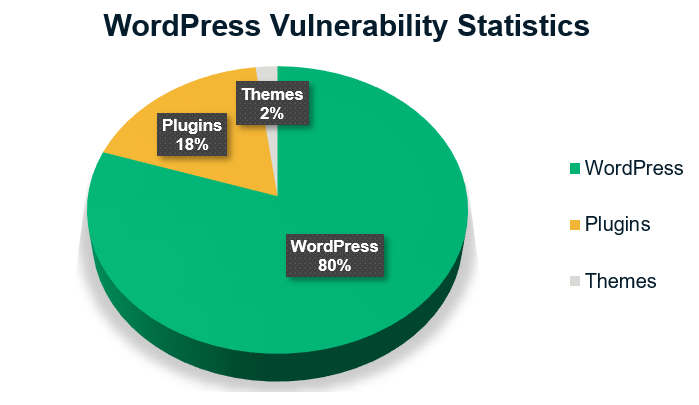



2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security