5 SMB Takeaways from the NIST Cybersecurity Framework 2.0
61% of small businesses victims of a cyberattack in 2023 lost over $10,000. Learn how to harden your digital defenses with these five NIST CSF 2.0 key points
According to the State of SMB Cybersecurity in 2024 report, 94% of small businesses (SMBs) have been victims of at least one cybersecurity attack in the past. This marks a 30% increase in just five years.
Too many business owners work hard to build their companies, only to hand over the fruits of their labors to cybercriminals. This is why you must take steps to protect your business in the face of growing cyber threats and increasingly complex technologies.
Don’t fret. The NIST Cybersecurity Framework (or, more specifically, NIST CSF 2.0) is coming to the rescue. In this article, we’ll explore five key takeaways that SMB owners like you can learn from this new framework and discover how to implement them to protect your digital assets and infrastructure from the bad guys.
What Is the NIST Cybersecurity Framework (CSF) 2.0?
The National Institute of Standards and Technology (NIST) released its first major update to the Cybersecurity Framework (CSF) in a decade in February 2024. Unlike its previous incarnation, NIST CSF 2.0 goes beyond critical infrastructure to aid organizations of all sizes and industries in managing and mitigating security risks.
This new version was developed in response to the U.S. Congress’s explicit request in 2018 to address small business concerns. Six years later, the NIST Cybersecurity Framework 2.0 was born.
The update throws a lifeline to the growing number of small and mid-size businesses in the crosshairs of cybercriminals due to their limited resources to invest in robust security protections. It’s a new set of risk-based best practices aimed at all businesses, with a specific focus on SMBs, so they can effectively protect their data and reduce the risk of attacks.
NIST CSF 2.0 is divided into six functions, providing organizations guidance for effectively managing their cybersecurity risk:
- Govern. Helps businesses to build and monitor a risk management strategy, expectations, and policy.
- Identify. Explains how businesses should manage cybersecurity risks.
- Protect. Details ways to minimize and contain security incidents.
- Detect. Illustrates how to identify attacks and security issues.
- Respond. Describes how to react to potential attacks promptly.
- Recover. Provides guidance on how to recover in case the worst happens.
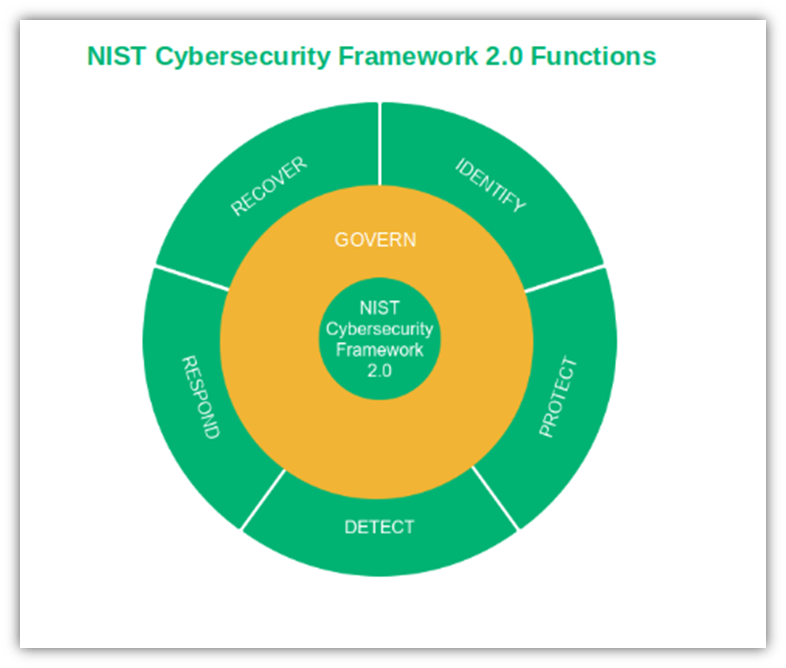
“The Functions should be addressed concurrently. Actions that support Govern, Identify, Protect, and Detect should all happen continuously, and actions that support Respond and Recover should be ready at all times and happen when cybersecurity incidents occur.”
What’s Changed? A Look at NIST’s CSF Version 1.1 to Version 2.0
While the biggest change in version 2.0 is the shift from mainly focusing on critical infrastructure to include other types of businesses, including SMBs, it wasn’t the only notable change. Another critical adjustment was the inclusion of the new function category: Govern.
Now, we aren’t going to get too into the weeds here about what’s changed from version 1.1 to 2.0. Instead, our goal is to provide a few examples of how this new version of the NIST Cybersecurity Framework can help SMBs boost their cybersecurity.
However, if you’re intrigued by the details and want to learn more about the changes from NIST CSF 1.1 to NIST CSF 2.0, check out the following video:
NIST CSF 2.0: 5 Small Businesses Takeaways
In the actual cybersecurity landscape, no one is too small to become the next cyber attack victim. When money is tight, and a report shows that attacks increased globally by 30% year-on-year in Q4 2024, gearing up for the fight isn’t easy.
Here, we’ve listed five NIST CSF 2.0 key takeaways that can help SMBs like yours dodge a few bullets in their uphill battle to ward off the bad guys. Are you a busy bee? Don’t worry. We’ve summarized the core concepts in the table below.
| NIST CSF 2.0 SMBs Takeaways | NIST CSF 2.0 Examples |
| 1. Identify, Understand, and Prioritize Your Risks | Run risk assessments. Analyze the risks you’ve identified. Hash out a plan of action. |
| 2. Protect Sensitive Data and Access | Protect data in transfer. Implement strong authentication and restrict access. Prevent data loss. |
| 3. Prioritize Your Supply Chain Risk Management | Put security at the heart of your software development process. Take steps to mitigate vendor-related risks. Implement a supply chain risk management framework. |
| 4. Embed Security Into All Your Processes | Sign your codes using a code signing certificate (and install only signed software). Protect your containers with an SSL/TLS certificate. Scan your software and websites. |
| 5. Have Robust Response and Recovery Plans | Create an incident response plan. Set up a recovery plan. Implement both to use when things go south. |
NIST CSF 2.0 Takeaway #1. Identify, Understand, and Prioritize Your Risks
Understanding and prioritizing risks is paramount for organizations with limited budgets that cannot afford to splash out on each threat. The govern and identify functions of the NIST Cybersecurity Framework help you pick the right strategy for your business and identify and prioritize the most critical threats.
Use NIST CSF’s tailored pathways and numerous implementation examples to draft a cybersecurity strategy and policies that align with your company’s mission. To do so:
Run Risk Assessments
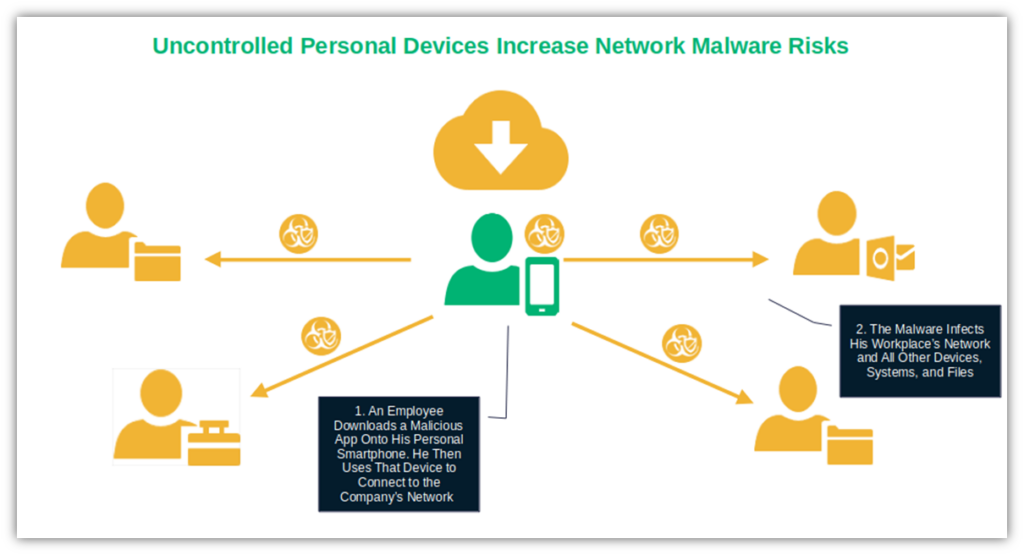
A cyber risk assessment allows you to examine the risks to your organization’s operations, IT and digital assets, and people. Businesses take risks every day — this is just part of how business works. But for SMBs, a faux pas (misstep) can mean the end of it. Proactively detecting and assessing potential risks that could negatively impact your operations, finances, and reputation will help you make the right decisions.
For example, SMB malware infections rose by 5% in Q1 2024. Is this something that could happen to you? Hopefully not, but it’s always a possibility. These days, employees often use their personal devices for work. This increases the risk of introducing malware to your larger network, which can quickly spread across your entire organization like wildfire.
Analyze the Risks You’ve Identified
Once you’ve compiled a comprehensive list of potential risks, analyze their probability of occurring and any possible impacts. 47% of U.S.-based SMBs polled by LastPass in 2024 suffered a data breach due to a compromised password. How likely is it that something like this will happen to you?
Analyze your situation and inventory the sensitive data (e.g., credit card numbers, passwords), critical hardware, systems, and software you need to protect. Assign a ratio to each risk (e.g., =1; >1; <1). It’ll help you prioritize efforts and focus on the right threats.
Hash Out a Plan of Action
Involve key stakeholders in the risk management plan’s development activities. This will help you minimize the chances of a security incident, reduce its impact should the worst happen, and get their buy-in. So, what does all this look like from a high-level perspective?
- Set up policies and processes,
- Determine who will monitor the identified risks, and
- Figure out how these crucial tasks will be achieved.
For instance, no matter how small, SMBs must abide by industry and country regulations and requirements. The European Union’s General Data Protection Regulation (GDPR) and the global Payment Card Industry Data Security Standards (PCI DSS) version 4.0.1 are just two examples of key regulations and standards.
Ensure your employees understand them and set up a process to track compliance. It’ll keep you out of trouble and avoid costly fines.
Sounds complicated? It doesn’t have to be. Once again, the NIST Cybersecurity Framework 2.0 comes to the rescue by pointing to some of NIST’s additional resources:
- NIST SP 800-37: Risk Management Framework for Information Systems and Organizations.
- NIST SP 800-30: Guide for Conducting Risk Assessments from the NIST Risk Management Framework (RMF).
NIST CSF 2.0 Takeaway #2. Protect Sensitive Data and Access
Data is your most valuable asset if your company is like most businesses. Securing that data and controlling who has access to it is paramount to its value and integrity.
Over half of the survey respondents in the Cyber Readiness Institute’s 2024 report (“The State of Cyber Readiness Among Small and Medium-Sized Businesses”) consider phishing, business email compromise (BEC) attacks, and ransomware the top threats for SMBs. All these attacks can result in bad guys getting their hands on your most valuable asset. So, what can you do to protect your data?
Here are some examples of the NIST Cybersecurity Framework 2.0’s suggested measures to boost the security of your sensitive data and access.
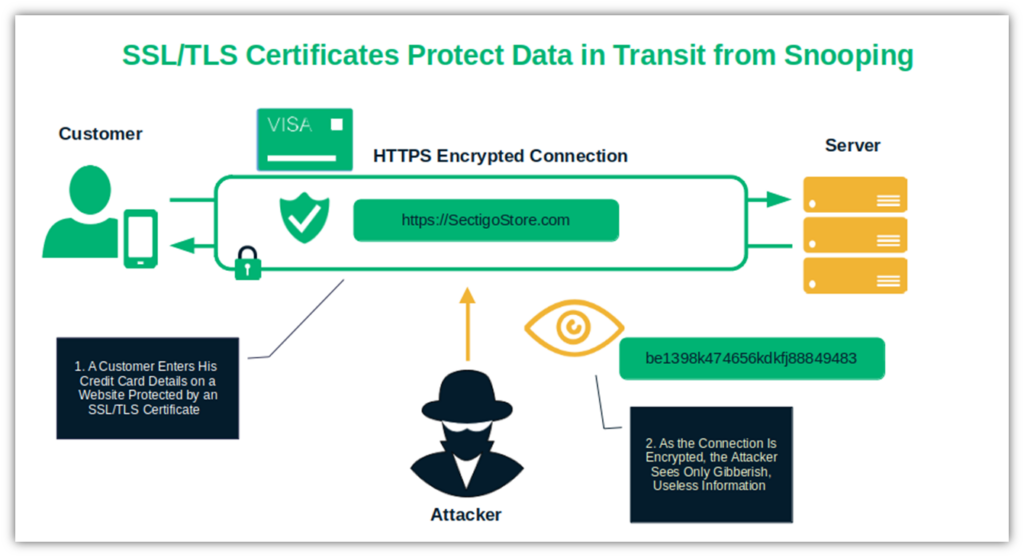
Protect Data Transfers via Encrypted Connections
The bad news: 90% of attacks reported to Sophos in 2023 involved data theft. The good news: You can protect the confidentiality and integrity of communications and sensitive information transmitted over the internet (e.g., credit card details during online payment transactions, emails, and API connections) with end-to-end encryption. This is possible by installing trusted secure socket layer/transport layer security (SSL/TLS) certificates on your web servers.
When you encrypt your data transmissions between a client and a server with an SSL/TLS protocol, the browser confirms to the user that the connection is secure by replacing “http” with the secure “https” protocol. This creates a secure communication channel between the two parties where everything is encrypted. This means that unless the attacker gets hold of the user’s private key, all he’ll see is gibberish nonsense when he tries to intercept the data.
Implement Strong Authentication and Restrict Access
In 2023, IBM reported a 71% increase in the attacks that used stolen or compromised credentials. It’s no secret that bad guys are after your passwords. Thus, relying only on one solution isn’t enough. Use a multi-layered approach instead.
- Enable multi-factor authentication (MFA) and use a password manager to generate strong passwords and shield them from crooks.
- Take authentication security one step further with public key infrastructure (PKI)-based digital identity. This passwordless approach shields users’ accounts against brute-force attacks by letting users automatically authenticate with a client certificate and a private key.
- Stay away from default passwords.
- Give users access to data, resources, and systems they need to do their work (i.e., the principle of least privilege).
- Patch your software and systems regularly. Check your website for vulnerabilities and fix them before the attackers find them.
Prevent Data Loss
Data is one of your most precious assets. However, considering that the 2024 Black Kite report shows that 31% of ransomware attacks analyzed impacted SMBs with revenues of <$20 million, it’s also one of the assets that’s most at risk. What makes things worse is that Veeam’s 2024 Ransomware Trend survey reports that businesses hit by such an attack lose an average of 18% of their data.
Protect “your precious,” as Gollum in The Lord of the Rings would say. Back up your data. For instance, if you have an online shop, use an automated backup tool like CodeGuard Backup. This handy solution will even scan your website for malware. Moreover, don’t forget to enable full-disk encryption on your devices and train your employees to recognize and properly respond to cyber threats.
NIST CSF 2.0 Takeaway #3. Prioritize Your Supply Chain Risk Management
The NIST Cybersecurity Framework 2.0 update emphasizes the focus on supply chain risk management. This is particularly important for SMBs relying heavily on third-party vendors, suppliers, and partners.
But what if they aren’t as reliable as they seem? Disaster is just around the corner. In January 2024, an attacker stole more than 15 million profiles (including info on users’ email addresses) from an unsecured Trello API. Due to the popularity of this online project management tool, the number of businesses impacted was massive.
So, what does NIST CSF 2.0 suggest in these situations?
Put Security at the Heart of Your Software Development Process
Follow secure coding best practices, perform vulnerability assessments from the design to the release stage, and implement secure authentication. This approach will help you identify and fix flaws earlier, ensure that only verified and authorized users can access data, and save you money, time, and resources.
Automate security testing with static (SAST) and dynamic (DAST) application testing tools, and include risk management processes into your software development lifecycle (SDLC). It’ll enable you to identify and effectively manage supply chain risks in a timely manner.
Take Steps to Mitigate Vendor-Related Risks
96% of the code base analyzed by Synopsys contained open-source materials. A single application had an average of 526 open-source components. Request a software bill of materials (SBOM) from your suppliers and create one for your software. An SBOM will list every bit of your code so that you can quickly identify dependencies, vulnerabilities, and fixes.
The same report shows that 49% of open-source components analyzed weren’t updated in the last two years. An unmaintained project is a vulnerable project. Knowing this, use a software composition analysis (SCA) tool to scan your software for vulnerable third-party components automatically. Last but not least, follow the NIST CSF 2.0 guide to learn how to choose a reliable service provider/vendor.
Implement a Supply Chain Risk Management Framework
The latest Verizon DBIR report shows that 15% of breaches involved a third party causing direct or indirect software supply chain security issues. We get it: As an SMB, you must take the risk of collaborating with third-party suppliers and vendors, or you can’t survive.
The solution? Adhere to a supply chain risk management framework to outline the policies, procedures, controls, and recovery plans to mitigate these risks. Does it sound familiar? Yup, it has a similar structure to the NIST CSF 2.0. The best of it? You can easily integrate the two frameworks for ultimate protection.
NIST CSF 2.0 Takeaway #4. Embed Security into All of Your Processes
78% of SMBs admitted to ConnectWise that a severe cybersecurity incident could put them out of business for good. And rightly so, considering that IBM reports the average global cost of a data breach reached $4.45 million in 2023.
Integrating security into every aspect of a business will minimize the chances of joining the SMBs and start-ups graveyard. NIST Cybersecurity Framework 2.0’s structured approach facilitates this integration process without breaking the bank.
Sign Your Codes Using a Code Signing Certificate (and Install Only Signed Software)
In March 2023, a software supply chain attack started by an infected software application set the stage for a second attack. If you are a software development company, signing your code with a trusted code signing certificate will help protect you and your customers on the other end of the supply chain from malware and data breaches.
Do you use third-party software? Before you download or install it, ensure it’s signed, too. This way, if a malicious actor has modified the app since it was signed, your company’s users will get a security warning and the installation will stop.
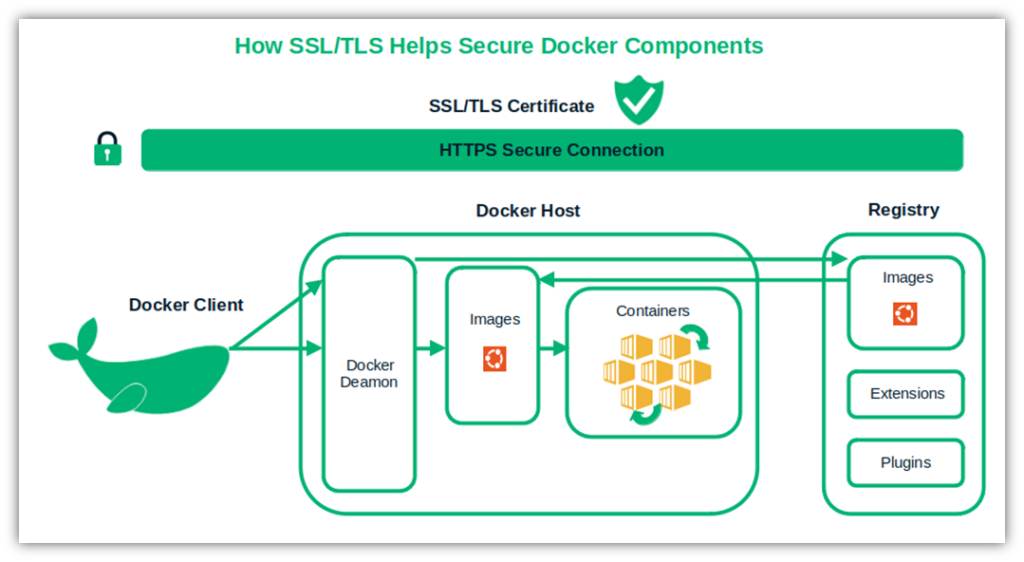
Protect Your Containers With an SSL/TLS Certificate
Did you know that the humble SSL/TLS certificate can also help protect container apps (i.e., a standalone, executable package including everything needed to run an application) by securing their connections? Yup, you can secure the communication between Docker clients, daemons, hosts, and containers with an SSL/TLS certificate. Ask the vendors you work with that use containers to do the same.
This step is crucial because containers often share a common operating system. A single vulnerable container can affect the whole infrastructure and, consequently, your entire software supply chain.
Scan Your Software and Websites
54% of organizations polled by Ponemon Institute for Balbix’s 2024 State of Enterprise Cyber Risk in the Age of AI report consider unpatched vulnerabilities their most important concern. However, only 49% of respondents run vulnerability scans once a week.
Adopt a zero-trust mindset. Trust no one. Did you download a new software or a critical update? Check if it has been digitally signed by a verified company and scan the executable file with a reputable antivirus before installing it.
Do you own a website? Use an automated website security checker tool to scan it for malware, vulnerabilities, and viruses regularly. Software like SiteLock and HackerGuardian come with a plethora of features that’ll keep your website and data secure.
NIST CSF 2.0 Takeaway #5 Have Robust Response and Recovery Plans
Cyber incidents and supply chain attacks happen all the time. Just open a news website and you’ll likely find one that is making headlines. Attackers are even hiding malware in phony patches and updates that promise to fix the CrowdStrike update glitch that impacted millions of Microsoft hosts.
While most SMB attacks don’t make news headlines, today’s threat landscape can’t be ignored. Effective and well-thought-out response and recovery plans can be the difference between life and death, above all for an SMB.
Create an Incident Response Plan
Are you among the 47% of organizations lacking an incident response plan? If so, it’s time to act. After you’ve identified a business champion responsible for keeping the plan up to date, build an incident response team, and list their contact details, roles, and responsibilities. Don’t forget to describe what will be reported, when, and how.
We won’t get into the nitty-gritty here as the NIST Cybersecurity Framework 2.0 already includes an extensive list of resources and guides such as the:
- NIST Incident Response Plan Basics,
- NIST Computer Security Incident Handling Guide, and
- Data Breach Response: A Guide for Businesses.
Set Up a Recovery Plan
After you’ve tested your new incident response plan, offer your business a present. OK, it ain’t Christmas, but having a thorough incident recovery plan is a gift for all occasions and seasons.
Pinpoint potential threats and their impact(s) on your company and an incident recovery team. Next, determine possible recovery strategies. For example, if an SSL/TLS certificate’s private key gets compromised, there should be a process in place to immediately revoke and replace it to limit any potential data exposure.
Check the NIST CSF 2.0 and the NIST Guide for Cybersecurity Event Recovery for additional tips and links. You won’t regret it.
Looking for More NIST CSF 2.0 SMB Resources? Check Out These Links
The NIST Cybersecurity Framework 2.0 is a goldmine of templates, examples, and useful information to help SMBs successfully implement it. Here we’ve listed a few.
- Get an overview of the NIST CSF 2.0 with the SMBs dedicated quick guide and the NIST CSF 2.0 resource and overview guide.
- Share and discuss insights, perspectives, and challenges with other SMBs like you. Join the NIST’s Small Business Cybersecurity Community of Interest (COI).
- Discover more about actual SMB threats by watching the entertaining videos published on the Small Business Cybersecurity Corner.
Final Thoughts About 5 SMB Takeaways from the NIST Cybersecurity Framework 2.0
We hope you’ve found this article and its linked resources useful. It’s clear to see how NIST CSF 2.0 makes cybersecurity accessible to any business, including cash-strapped SMBs. The new framework’s structured approach empowers small and mid-sized businesses to:
- Easily identify focus areas and weaknesses,
- Develop a comprehensive cybersecurity strategy,
- Seamlessly embed security in all processes, and
- Boost customer trust and loyalty, showing them that security is at the heart of your business.
Prepare your business for cybersecurity attacks before they occur by taking action today. Strengthen your defenses by securing your web transactions with trusted SSL/TLS certificates, protecting the integrity and authenticity of your software apps with code signing digital signatures. This will also help you comply with industry regulations that require you to protect your data at rest and in transit.





















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security