What Constitutes a GDPR Data Breach? Definition & Meaning
EnforcementTracker.com reports a cumulative total of €277,239,988 GDPR fines have been imposed on organizations following the breach of covered users’ sensitive information as of March 2021. But exactly what is a “GDPR data breach” and how do you define it?
In general, a data breach means the exposure of confidential information to unintended (unauthorized) parties. In other words, when personal information is leaked, kept unsecured, or lost — and, as a result, an unauthorized person steals, accesses, and uses it — it is known as a data breach. A GDPR data breach refers to data breaches that occur within specific contexts.
Many countries have security laws and regulations to determine the scope and accountability of organizations that are involved in data breach incidents. One of the best known and far-reaching regulations is the General Data Protection Regulation (GDPR). Its purpose is to protect the personal data of people physically located in the European Union (EU) and European Economic Area (EEA), even if they don’t live there. GDPR identifies these individuals as data subjects.
In this article, we’ll discuss what is considered a GDPR data breach. We’ll also go cover the definition of a personal data breach as well to give you a clear understanding of each aspect.
What Is a GDPR Data Breach? A GDPR Breach Definition
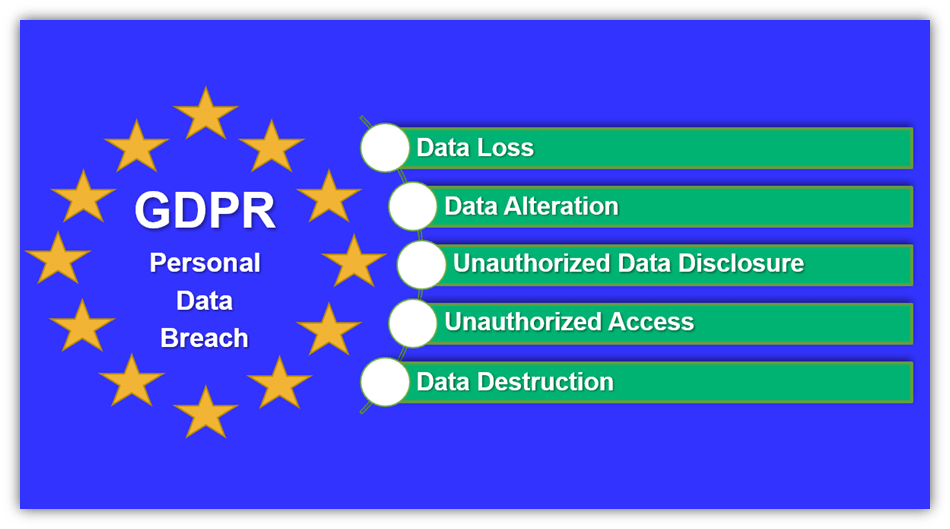
A GDPR data breach occurs when any covered personal data that you’re responsible for protecting experiences a security-related incident that results in a breach of integrity or confidentiality. More specifically, GDPR article 4 defines personal data breaches as:
“[…] a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorized disclosure of, or access to, personal data transmitted, stored or otherwise processed.”
That’s a lot to take it. What exactly does this mean? Let’s divide the GDPR data breach definition into smaller parts to understand it more clearly.
What Constitutes “Personal Data” Under GDPR?
Under the GDPR, a personal data breach means the exposure of any information that can be used to identify a specific person (i.e., a data subject). This information includes a variety of personal and otherwise sensitive data, examples of which include:
- Names: A data subject’s full name and names of family members.
- Identification numbers: European Social Security Number (ESSN), driving license number, state ID number, etc.
- Financial information: Payment card numbers, bank account information, employment related data, salary or other forms of income, taxes, expenses, spending tendencies, information about the financial institutions (such as bank, insurance company) they are involved with, etc.
- Geographical location data: A person’s physical location, address, immigration-related data, etc.
- Physical or physiological attributes: Appearance descriptions such as gender, height, skin color, weight, as well as information relating to mental conditions, physical illnesses, etc.
- Online Identity: IP addresses, email addresses, and information captured by digital cookies such as a user’s browsing information, pages visited, purchase histories, etc.
- Social identity: the cultural groups and their common attributes, ethnic origins, political opinions, religious or ideological convictions, or trade union memberships.
Who Is Responsible for Protecting That Data?
Under GDPR article 4, organizations and other entities are defined in a few ways depending on their individual roles:
- Controller: Anyone that defines the purposes and means of collecting and processing of personal data. In general, the primary organization that collects your personal data is known as controller.
- Processor: The entity which performs various data operations (organizing, storing, structuring, altering, transmitting, etc.) on behalf of the controller is known as the processor.
- Recipient: This is an internal or external person or entity that data subjects’ personal data are exposed to.
- Third party: Any other party who has authority to process the personal data under the direct permission of the controller or the processor.
Under GDPR, data controllers must build their information systems in a way that no unauthorized person can intentionally or unintentionally access the data, which results in a personal data breach. Article 33 states that when a GDPR personal data breach occurs, the controller must inform the appropriate government agency (aka a supervisory authority) about the event without “undue delay” and no later than 72 hours after they become aware that data subjects’ “rights and freedoms are at risk.” Processors are responsible for informing controllers “without undue delay” as well after becoming aware a breach of personal data has occurred.
Organizations handling GDPR-covered data also have a responsibility to inform affected individuals of these breaches in many circumstances (although there are exceptions).
What Constitutes “Data Destruction”
GDPR has specific rules regarding how long the controller can retain the data and how they can lawfully destroy it. That’s because controllers must destroy GDPR-covered personal data immediately when they no longer have any legal reasons for continuing to store it. For example:
- When the data is no longer needed for its original purpose, or
- The data subjects have withdrawn their consent.
For data to be destroyed in a way that meets GDPR criteria, it must be disposed of in a way that it can’t be retrieved. The data media must be physically destroyed, or data must be permanently over-written using special software. All the links, copies or replicates of the personal data stored with the processor and an authorized third-party must be permanently erased, too.
Data Loss
Data loss is an all-encompassing term that describes data that gets destroyed due to negligence or technical errors. Organizations can lose data in a well-planned cyber attack or by mere negligence. According to IBM’s 2020 Cost of
Insider Threats Global Report, the annualized cost of data breaches that result from employee negligence is $4.58M. They also report that 63% of insider-related incidents stem from negligence.
Of course, negligence isn’t the only factor at play here. Data can result from other reasons as well, including:
- Hardware failures,
- Software crashes,
- Coding bugs and other related vulnerabilities,
- Malware infections,
- Administrative mistakes,
- Misplacements or losses of data storage units (like USB, laptop, portable drive, etc.), and
- External issues, such as power failures.
If the data controller has lost the users’ personal data due to any of the above reasons, it also qualifies as a GDPR data breach.
Data Alteration
The term data alteration under the GDPR refers to any unauthorized modifications of covered data. Say an employee intentionally alters stored data to use it for deceptive or otherwise misrepresentational purposes. This could qualify as a personal data breach under GDPR.
Data alteration can be done by all types of people:
- Insiders (i.e., employees and contractors),
- Outsiders (i.e., hackers and other unauthorized users), and
- Third-party processors and entities.
For example, say a hacker breaks into an organization’s HR database and replaces their employees’ bank account numbers with his own. This counts as one form of data alteration. Another example might be a hacker accesses an organization’s email client and alters outbound email content to convert them into phishing emails.
So, what can your organization do to prevent these types of unauthorized data modifications? Companies generally deploy technology like file integrity monitoring (FIM) to detect unauthorized alterations. FIM software detects unusual attempts to access data, modify it, or destroy it. So, you can spot any GDPR data breach incident before it’s too late.
You can also implement robust access controls. Access management enables you to set up user permissions so that only authorized individuals can access your organization’s sensitive IT systems and data. This limits your organization’s potential exposure to situations that result from insider threats.
Unauthorized Data Disclosure
As the name indicates, the disclosure of any data subjects’ personal information to unauthorized individuals falls under the umbrella GDPR breach definition. An example of this would be if a hospital employee accidentally publishes or shares a data subject’s electronic health records with an unauthorized user via an unencrypted email.
But not all unauthorized disclosures are accidental. Sometimes, individuals intentionally disclose the personal data of another person for personal revenge, blackmail, to cause reputational harm, make money, or other nefarious purposes.
Let’s consider another hypothetical example. Say you’ve got an unscrupulous employee named Bob — he’s your sales executive who works with customers on several continents. Bob has access to your database that includes the personal information of EU customers (GDPR data subjects). Unfortunately for you, he copies the entire file to a personal USB drive and secretly sells it to one of your competitors.
Here, the data breach victims include all of your customers whose personal data Bob exposed to this unauthorized third party.
Unauthorized Access
When an unintended person reads, interprets, and uses the confidential data of the data subjects, it falls under the GDPR personal data breach definition. The unauthorized access can happen in one or more of the following ways.
1. Cyber attacks: Attackers try to gain access to your organization’s stored data by directly attacking your databases, servers, cloud platforms, and other connected devices. To this end, they can use many types of cyber attack methods, including
They can also use phishing attacks and social engineering tactics to gain access via an authorized user’s legitimate credentials.
2. Malware: Hackers use spyware, ransomware, and other types of malware to gain unauthorized access to users’ protected data. For example, an attacker can use an army of infected devices that they control (known as a botnet) to carry out brute force attacks to try to gain access to your IT systems and data.
3. Equipment theft or loss: The University of Pittsburgh reports that one out of every 10 laptop gets stolen and that an incredible 98% of stolen laptops are never recovered. If you store sensitive data on unsecured devices (i.e., devices not protected with robust security mechanisms like biometrics, 2FA/MFA, strong passwords, etc.), you’re at risk of suffering a GDPR data breach. When attackers get their hands on unprotected devices or sell your company’s equipment without properly wiping their memories, any unauthorized person can access confidential data.
4. Negligence: If an outsider accesses GDPR-covered data due to a controller’s negligence, it counts as a GDPR data breach. Accidentally transmitting files containing confidential data via insecure channels or allowing an unauthorized user to access a device containing such data are two examples of how such a breach can occur.
Data Transmission
When personal data transmits between two endpoints, companies must take appropriate measures to protect that data. Website owners must install an SSL/TLS certificate to prevent security data breaches when data is transferred between the website visitor’s browser and the website’s server. In the same way, companies can use email encryption certificates to enable end-to-end encryption when sending and receiving personal data via email.
If data transmitted digitally or through physical devices like USB, or portable hard drive, it must be protected with strong passwords, PKI certificates, 2FA/MFA, biometrics, or other passwordless authentication methods.
Stored Data
There are many ways to store your organization’s data (although some are neither ideal nor secure). You can store data on devices like laptops, desktops, smartphones, external hard drives, USB drives and other portable data storage units. You can also use cloud storage platforms and servers. And while all of these methods of storing at-rest data offer varying levels of convenience, they also create potential vulnerabilities that cybercriminals can exploit.
As such, you must implement strong authentication mechanisms to protect your devices and prevent a GDPR data breach from occurring. For example, you need to keep your servers and databases behind firewalls. You can also use tactics such as data sanitization, whitelisting, and validation to prevent SQL injection-based cyber-attacks.
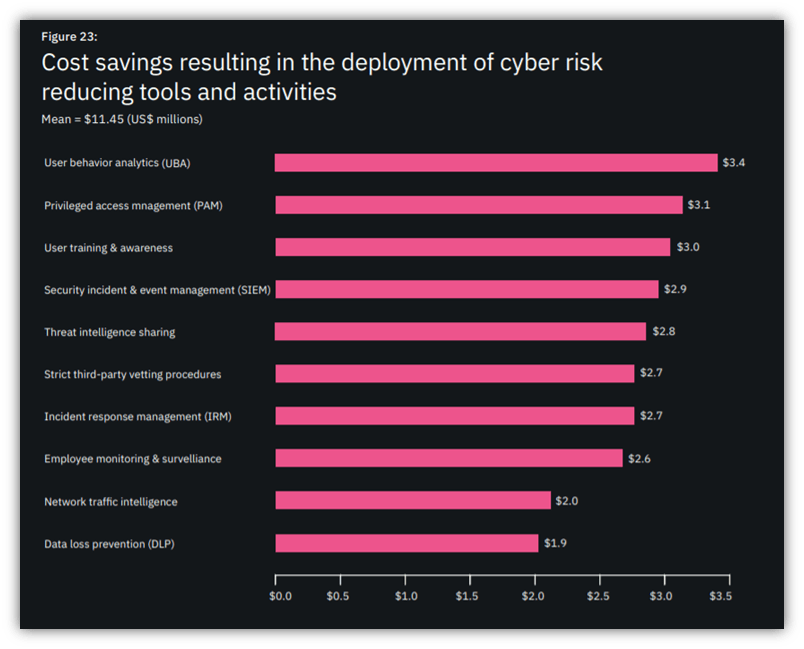
Organizations can also install file integrity monitoring tools to identify unauthorized alterations of stored data. Other cyber risk mitigation tools and training also provide additional benefits. According to IBM’s 2020 Cost of Global Insider Report mentioned earlier, companies that put user behavior analytics to work for them save an average of $3.4 million. They can also average savings of $3.1 million by implementing privileged access management (PAM) solutions.
Data Processing
In GDPR, data processing covers a multitude of meanings. The term refers to virtually any manual or automated operations conducted on data subjects’ personal data, including:
- Collecting,
- Storing,
- Using,
- Recording,
- Organizing,
- Structuring,
- Transmitting
- Combining,
- Disclosing,
- Recovering,
- Restricting,
- Altering, and
- Deleting.
As such, data controllers must take the necessary protective steps to prevent a personal data breach in each of these steps.
Final Thoughts on GDPR Data Breaches
A final note that’s important to mention: GDPR breaches and data security violations are significant in terms of costs. They result in enormous fines — up to 10,000,000 EUR, or up to 2 % of the total worldwide annual turnover of the preceding financial year, whichever is higher.
The truth is that no companies, including major corporations, are immune to the consequences of GDPR data breach violations. Between 2019 and 2020, Google attracted €57 million in GDPR fines, and H&M was slapped with €35 million fine in 2020 for violations relating to employee monitoring.
If big companies that employ cybersecurity and policy experts can find themselves the subject of a GDPR breach, imagine how challenging it would be for small businesses and startups to comply with these stringent regulations. Nevertheless, GDPR non-compliance can be a potentially lethal (or, at least, damaging) move for any organization. So, if your organization collects or otherwise handles people’s personal data in that part of the world, you must take GDPR rules seriously. This means doing everything within your power to comply with its requirements to avoid becoming the next headline relating to a GDPR personal data breach.














 (44 votes, average: 4.91 out of 5)
(44 votes, average: 4.91 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security