7 Tips: How to Protect Your Phone from Hackers
RSA data shows that 70% of fraud transactions come from mobile devices — here are seven simple ways that you can keep your phone safe from hackers and other criminals
Phones are an integral part of our lives. Results from reviews.org survey show that 75.4% of respondents feel that they’re addicted to their phones. Furthermore, nearly two-thirds of respondents reported checking their phones up to 160 times per day! Now, we’re not here to judge anyone’s mobile addictions, but we do want to help you understand how to protect your phone from hackers.
If you’re wondering “how to block hackers from my phone,” or what you’ve come to the right place. In this article, we’ll cover seven easy-to-follow tips that will help you to protect your phone from hackers.
7 Tips: How to Protect Your Phone From Hackers
1) Install Security Software Tools on Your Mobile Device
Antivirus software and anti-malware software are not limited to computers only. You should use them on your mobile phones as well to protect your phone from hackers. When you surf online, different types of malware (like viruses, trojan horses, worms, etc.) can be installed on your device via malware-loaded websites. Your device also might get infected through malicious email attachments or apps.
Security software not only detects and removes malware but also can warn you when you visit a bad site or download a malicious app. Some malware gets downloaded on your mobile without your notice. A good security program scans and notifies you every time something downloads to your device.
With “freemium” security software, typically the basic service is free. If you want to tighten the security and need more features, you can upgrade them to a commercial service. You should check the advantages and disadvantages of both free and paid versions to determine the best solution for your device.
2) Be Judicious About What You Download and Install on Your Phone
Not everything is as it appears. Be vigilant when installing apps or downloading images, videos, files, songs, email attachments, etc. from the internet. There are a few general rules of thumb to follow when downloading content from the internet:
Only Download Files from Well-Known, Reputable Websites
Scan all the files with your antivirus and antimalware programs before downloading them.
Do Your Homework
If you’re installing a new or unknown app, research the app publishers and read the customer reviews online. 70% of mobile fraud originates from malicious apps.
3) Check Your App Permissions
When you install an app, it will likely request access to some integral features of the device, such as a camera, email, contact list, photo gallery, location, etc. Carefully review each of those features and ask yourself, “does this app really need to access this particular feature”? For example, if you’re installing a food delivery app, it likely needs access to location tracking. But there’s likely no reason why it should require access to your email clients, phonebooks, files, and camera. Disallow!
Here’s how you can check the permissions for all your installed mobile apps:
For iPhone: Go to Settings > Privacy. You will see a list of all the device features. Click on that specific feature to see which apps have permission to access it. You can turn off the permission from that screen.
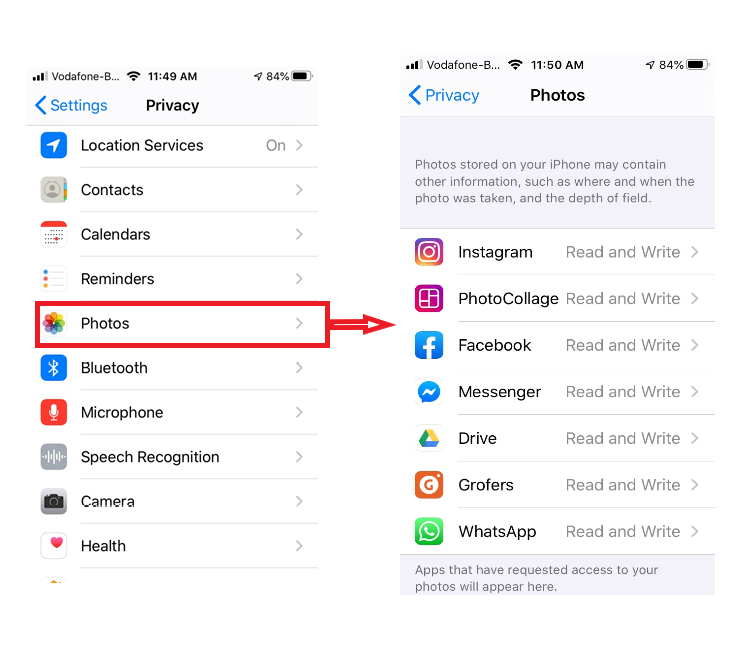
For Android: Go to Settings > Permission Manager*. You will get the list of the feature and the apps which have permissions to access those apps.
*Note: All the Android phones have different names for the permission checking tab. It depends on which brand’s phone you are using.
4) Avoid Using Public Wi-Fi (Or Use a Virtual Private Network If You Do)
Hackers can exploit insecure connections to eavesdrop and steal the data from connected devices. It’s is one type of man-in-the-middle (MitM) attack. So, for our next tip on how to protect your phone from hackers: avoid using public Wi-Fi (in airports, malls, hotels, shops, cafes, etc.). Use cellular network data instead.
Make sure when you use a mobile hotspot, you keep it password protected to keep it secure. But what if you don’t have an abundance of cellular data? Then don’t do your professional work or access websites where you need to provide any confidential or sensitive information until you can use a secure connection.
If you do have to use public Wi-Fi, you can reduce your risk by using a virtual private network (VPN). They are many free or inexpensive VPN providers available to choose from. One of the many benefits VPNs provide is that the VPN passes on the web-traffic via a private encrypted channel. Hence, even if someone has broken the internet connection and intercepting your traffic, they won’t be able to read, interpret, and modify anything due to VPN’s encryption facility. You just need to install the VPN app and turn it on at the time of using the public Wi-Fi. It’s quite simple to use.
5) Protect Yourself from SIM Swapping
SIM swapping occurs when a bad guy calls your mobile service provider and asks for a replacement SIM card. This unauthorized SIM swapping is possible when a hacker has access to some of your confidential information (such as the last four digits of your social security number, or any identity proof document) and uses it as part of their social engineering scam.
If they’re successful in convincing your mobile provider to port your number, the attacker can intercept all your phone calls, SMS text messages, and potentially gain access to all accounts and services that are linked to your phone number.
Pro Tip: To protect yourself from unauthorized SIM swapping or number porting, set up a unique PIN or passcode with your mobile service provider. This would be a number that only you know that you have to use to access or make changes to your mobile account (including number/account porting to other devices).
You can also use apps like Google Authenticator, Authy, or Google’s code-less authentication method to add another layer of security. Apple’s two-step verification feature can send an OTP to a registered device (rather than to the phone number) whenever someone tries to log in from a new device. This adds an additional layer of non-SMS-based MFA security to your device.
In other words, even if the perpetrator inserts a replacement SIM card into a new device, they still can’t activate it until they provide the OTP, which iOS sends only to your (registered) device or to another phone number linked/connected to your primary phone number. You can also set an app-specific password, so no one can open your apps without providing those passwords.
6) Keep Your Tracking and Remote Locking Settings On
At this stage, we assume that you’ve enabled your mobile’s lock screen feature with a multi-digit passcode, face/fingerprint recognition, or a complicated pattern. This is particularly helpful if you lose your phone or if a thief has gotten their hands on your device. But if you think that your screen lock will make it impossible for thieves to misuse your phone, you’re not aware of the tricks hackers can use to bypass the phone’s initial security mechanism. There are ways to bypass even fingerprint lock and facial recognition security mechanisms!
This is where the ability to remotely lock your device is essential. This is the first step in protecting your phone from hackers or anyone, really, who shouldn’t have access to your device. Fortunately, virtually all the phone providers offer Find My Device and remote lock functionalities. You just need to install those apps (if they don’t come pre-installed on your device) and register your device.
For example, you can use the Google Find My Device app for Android phones and Find My iPhone for Apple phones. To enable these apps, choose your type of device below and follow these easy directions:
- For iPhones: Go to Settings > Passwords, and Accounts > iCloud > Turn on Find My iPhone, Enable Offline Finding and Send Last Location.
- For Android Phones: You just need to link your Gmail account in Google Find My Device app, and it will start working without any further settings. All the android device providers have this feature available. For Samsung phones, you can use Samsung’s Find My Mobile tool, too.
These apps also give you the ability to lock your phone remotely. If you’re sure that your phone is in the wrong hands, you can also erase your entire phone memory remotely so that no one can misuse your data. Erasing your phone is a risky step, so create regular backups of your important data.
7) Additional Tips on How to Protect Your Phone from Hackers
Before moving forward, let’s have a quick look at these powerful tips that will help you to protect your phone from hackers.
- Disable “Allow Siri When Locked” function. Go to Settings > Siri and Search > Disable the Allow Siri When Locked feature. In the past, some bugs in the iPhone allowed anyone to bypass the screen lock and access a couple of functions using Siri.
- Password protect your cloud storage apps. This includes apps such as Google Drive, Google Docs, iCloud, etc. Check out these resources for more information on how to protect your iCloud account and how to protect your Google Drive and docs.
- Disable the “smart unlock” feature. Some mobile devices have this feature, which automatically unlocks your phone when you are at a “safe” location (home, work, etc.) or when your smartwatch is nearby. But it’s very risky because the attackers can bypass the lock screen authentication if they are in near proximity.
- Password protect important files, folders, and apps from getting an additional layer of security. Use Apps like Folder Lock (available for both Android and iPhones) for this purpose.
- Avoid using public charging ports. Hackers can compromise charging ports (this is known as juice jacking) to intercept the data and break into your device.
- To avoid getting spam calls and spam SMS messages, make your number undetectable or unknown. Use the steps mentioned in this article for the same: How to Make Your Number Unknown When Calling.
- Avoid jailbreaking devices. Jailbreaking (or rooting) means making unauthorized changes in the default device settings using some software. People jailbreak their phone to unlock it (change service providers), use banned or pirated apps, customize the looks, or enable tethering (hotspot) service without paying an extra fee. But when you jailbreak your phone, you not only void the device’s warranty but you also weaken the phone’s security posture. Hackers can easily insert malware and steal confidential data from a jailbroken phone.
Why Mobile Use Is Increasing in Popularity (For Users & Cybercriminals)
To put it simply, mobile = convenience. Nowadays, we use mobile phones to do bank transactions, pay bills, and to send personal and professional emails. But mobile is great for more than that — we also use mobile apps and browsers to shop, book cabs, monitor our health and fitness goals, order food, etc. Simply put, mobile is integral to our modern lives.
For the sake of convenience, you may find yourself enabling the auto-login or credential auto-fill features on your mobile apps and browsers. You also may store sensitive information — such as photos, videos, conversations on social media apps, health and fitness information, personal or work-related documents, etc. — on your personal and company devices as well.
Hackers and cybercriminals know this, and they like to use our love of convenience and connectivity to their advantage. If someone gets access to your phone — physically or virtually — they can do a lot of damage. They can choose to sell your information to other cybercriminals. But it gets worse — they (or someone they sell your information to) can also:
- Steal your identity,
- Log in to your banking apps to conduct fraudulent financial transactions,
- Access your email and send phishing emails in your name,
- Use the data for ransomware attacks,
- Use your device as a zombie (bot) in botnet attacks,
- Harm your reputation by posting inappropriate things from your account, etc.
Wrapping Up: How to Protect Your Phone from Hackers
Nobody likes imagining the scenario in which perpetrators hack, install malware, or steal the data from their phones. But when there’s a 680% increase in fraudulent transactions that are performed via mobile, let’s not deny the fact that no one is immune to mobile fraud.
The best way to protect your phone from hackers is to:
- Do everything within your power to secure your mobile account with your service provider.
- Be vigilant while visiting any websites and downloading anything from the internet.
- Never underestimate the importance of security software and always keep it patched and up to date.
- Use trusted and reliable antivirus and antimalware protection tools.
We hope this article has helped you to strengthen the security posture of your mobile.














 (27 votes, average: 4.41 out of 5)
(27 votes, average: 4.41 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security