11 WordPress Security Best Practices & Tips to Do on Your Lunch Break
This list of WordPress security tips and best practices features quick fixes that don’t take a lot of time but result in big paybacks in the form of improved website security
WordPress is one of the world’s leading platforms, but much like other major platforms, it isn’t without its issues. WPScan reported more than 38,679 WordPress security vulnerabilities in their database as of March 21, 2023 — 92% of which were related to plugins specifically. Of course, these aren’t the only security issues you’ll face. And this is why we’ve put together an article that covers the most essential WordPress security best practices and tips you should implement to make your site more secure.
Of course, contrary to what you may think from reading the title of this article, we don’t advocate working through your lunch break. (We’re big proponents of work-life balance.) We just mean that these WordPress website security best practices are so quick and easy, you could handle completing one of them in the time it takes to grab takeout or get a delivery from your favorite lunch spot each workday.
WordPress Security Best Practices & Tips: 11 Things to Do While Waiting For Your Food
Got time to kill between when you ordered your lunch and when it’s expected to arrive? Here’s a list of 11 things you can start working on while waiting for the delivery guy:
1. Run Website Vulnerability and Malware Scans
First on our list of ways regarding how to secure WordPress is one of the most basic: running vulnerability scans. Regularly checking your website for security vulnerabilities and issues is integral to its health and security. Some examples of the things you should be looking for are vulnerabilities relating to
- expired or revoked certificates,
- vulnerable WordPress plugins and themes,
- malware,
- cross-site scripting (XSS) issues, SQL injection vulnerabilities, and other OWASP Top 10 cyber attack methods.
To simplify the process of finding these security-related issues on your site, you can use an automated website security vulnerability scanning tool like SiteLock. This tool combines the capabilities of a 24/7 cybersecurity team with a cloud-based security platform.
Another benefit of using SiteLock is that you can use it to back up and restore your databases and website files as well. However, you can also use other tools (such as CodeGuard) to back up and restore your website as well.
2. Change Any Default Account Passwords
Although there are many best practices regarding password security, three of the biggest rules to remember are the following:
- Never use a default password. This is just asking for trouble as it means that anyone who has a list of default passwords can brute force their way into your account with ease.
- Never hardcode your passwords. Unless the idea of enabling your website or web apps to become of becoming compromised).
- Implement other password policy best practices. Doing this can help you keep your password security at the highest level.
Surprised to not see salting and peppering your passwords on this list? Of course, we always recommend you salt (and pepper, if available) your passwords. But in the case of WordPress websites, the content management platform applies salts automatically to add a layer of security to stored passwords. So, you don’t have to do anything to make this happen.
3. Update Your WordPress Plugins and Themes
First on our list of how to secure WordPress is one of the most basic: applying updates and patches. Much like how you have to update your computer’s operating system software and other applications, WordPress themes and plugins are no different. Software developers use software updates and patches to fix known security vulnerabilities.
Remember the WordPress vulnerability statistics we cited at the beginning of the article? As you likely noticed, the overwhelming majority of those known vulnerabilities were related to insecure plugins. By applying updates regularly, you’re ensuring that your website is running the most recent (and most secure) versions of WordPress plugins and themes.
To ensure your WordPress plugins are updated, navigate to Plugins > Installed Plugins in your WordPress dashboard. Here, you also have the option of setting your plugins to update automatically:
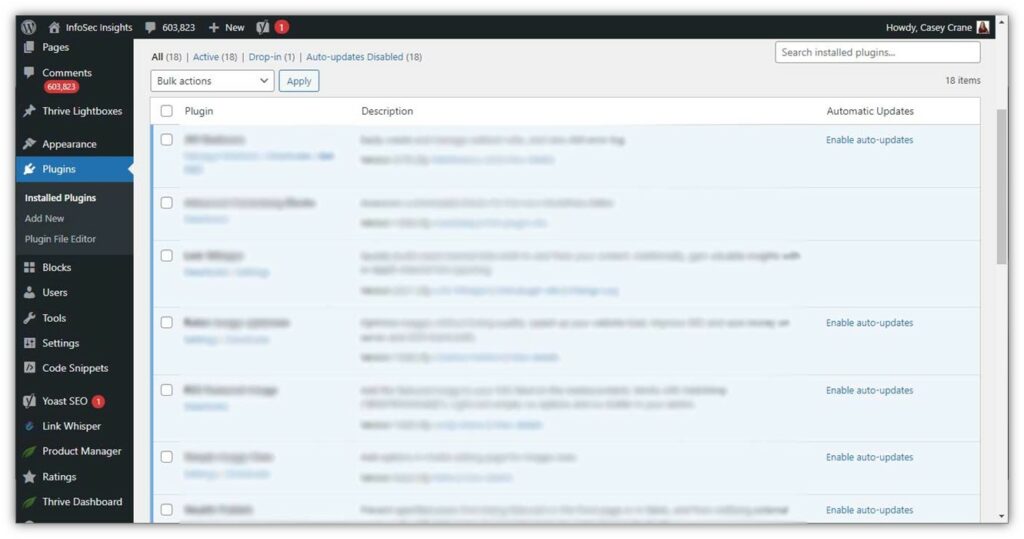
4. Check User Permissions to Ensure They’re Set Appropriately
The big thing to remember when setting user permissions is that people should only have access to the data, files and systems they need to do their jobs. Just because someone says they need access doesn’t mean that they actually do.
For example, low-level users don’t need access to everything in your company’s website dashboard. But if you work as a website administrator, then, obviously, you will need access to everything. Set permissions based on the level of access someone actually needs and not what they want. Doing this will help minimize the attack surface of your website and mitigate the potential security risks associated with them.
For example, this is what it looks like when we set up a new user profile on our blog:
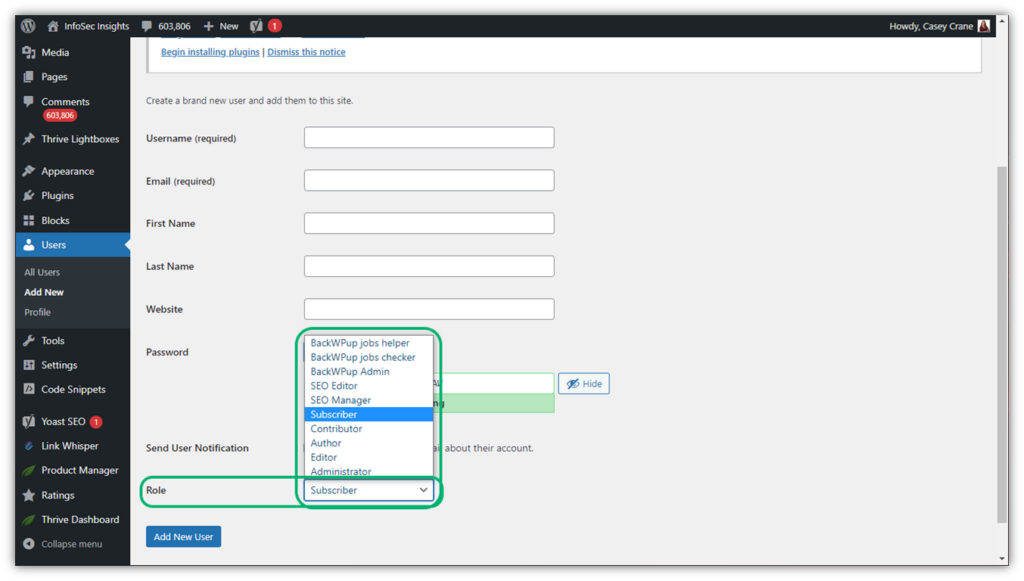
5. Install an SLS/TLS Certificate on Your Website
SSL/TLS = data security in the form of encryption. Installing an SSL/TLS certificate on your web server is what enables the https:// and padlock security icon to appear next to your site’s URL in users’ browsers. This is important because without it, browsers would warn them that your website isn’t secure and poses a threat to their data security.
But encryption on its own isn’t enough — you also need to know that the website is controlled by a legitimate entity. This is why SSL/TLS certificates come in three forms of validation: domain validation (DV), organization validation (OV), and extended validation (EV). These validations range from lowest to highest (DV to OV to EV) and provide increasing ranges of authentication, meaning that they offer assurance of your verified digital identity.
You can get a basic SSL/TLS certificate (DV certificate) in as little as a few minutes. But if you’re looking for a certificate that offers higher validation, such as an OV or EV certificate, then you’ll need to do a little planning ahead. Go ahead and request a certificate and complete the validation process. Once you have your certificate in hand, then you can install it on your website.
We aren’t going to walk you through all of the steps for installing a website security certificate on your website. If you want a step-by-step guide for this process, then check out our other article to learn more about how to install SSL/TLS certificates on your WordPress website.
6. Check Your Existing Website Security Certificates to Ensure They’re Current
If you’ve learned anything from reading our previous Infosec Insights and SSL Resource articles, then you should know that expired SSL/TLS certificates are no laughing matter. Expired or invalid certificates represent a significant issue for organizations globally. These formerly useful bits of data cause website and service outages and leave users’ sensitive data vulnerable to theft and manipulation.
If you can’t be bothered to manage your certificates properly, how can site visitors trust that you’ll handle their data securely? They can’t and, frankly, they shouldn’t. Give them a reason to trust you with their most sensitive information by following certificate management best practices.
7. Enable Two-Factor or Multi-Factor Authentication to Add Another Layer of Security
Next on our list of WordPress security best practices is two-factor authentication, or what’s otherwise known as 2FA for short. Two-factor authentication is a type of multi-factor authentication (MFA), meaning that you must provide two separate forms of identity verification in order to log in or access protected resources. In some cases, you may use more than two factors (which is when you shift into the realm of MFA).

Enabling 2FA or MFA helps adds another layer of security to the authentication process by requiring you to provide two or more of the following factors:
- Something you know (this can be something like a PIN, password, etc.),
- Something you have (such as a physical hardware security token or an authenticator app for your mobile device), or
- Something you are (this is something intrinsic to you, such as a scan of your retina, face, or fingerprint.
Two-factor authentication is available as a feature on WordPress.com. However, if you’re a WordPress.org user, then you’ll need to install a WordPress 2FA plugin.
8. Set a VPN Use Policy Requiring Users to Connect Using a Secure Network
When your WordPress website security users need to log in, be sure to require that they do so using a secure network. (For more information on secure networks, check out our article on network security best practices.) Ideally, users will connect using your in-office network. But what if they’re working remotely from home, an airport, or a coffee shop?
Require users to access your files, databases, and other sensitive data remotely using a virtual private network (VPN) when working offsite. What this does is create a secure connection they can use to access your systems while working remotely, thereby preventing man-in-the-middle attacks and the data compromises that follow.
9. Set WordPress Login Attempt Limits to Prevent Brute Force Attacks
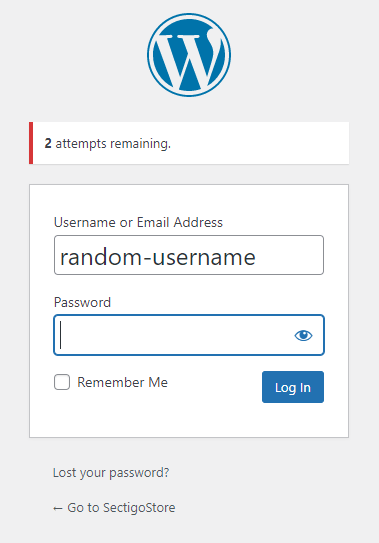
Setting a login rate limit is a way to limit the number of times someone can attempt to log in on your site. This approach is crucial to preventing brute force attacks. Without these login rate limitations, an attacker can repeatedly try to login using different username-password combinations until they find a winner.
What you may not realize is that WordPress allows unlimited login attempts by default. So, if you don’t bother changing your website’s settings, you’re leaving yourself open to a world of hurt. But if you set limits for the number of login attempts an IP address can make within a set period, then you’ll increase your site’s security immediately. Here’s what it looks like when someone fails a login attempt:
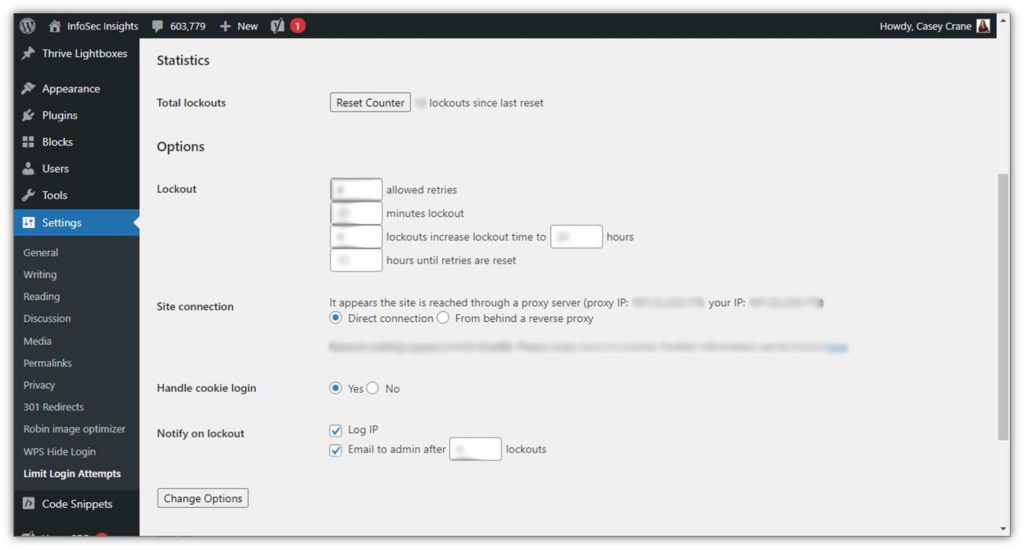
The good news is that setting login rate limits is easy. You can do it in the WordPress Settings menu by navigating to Settings > Limit Login Attempts:
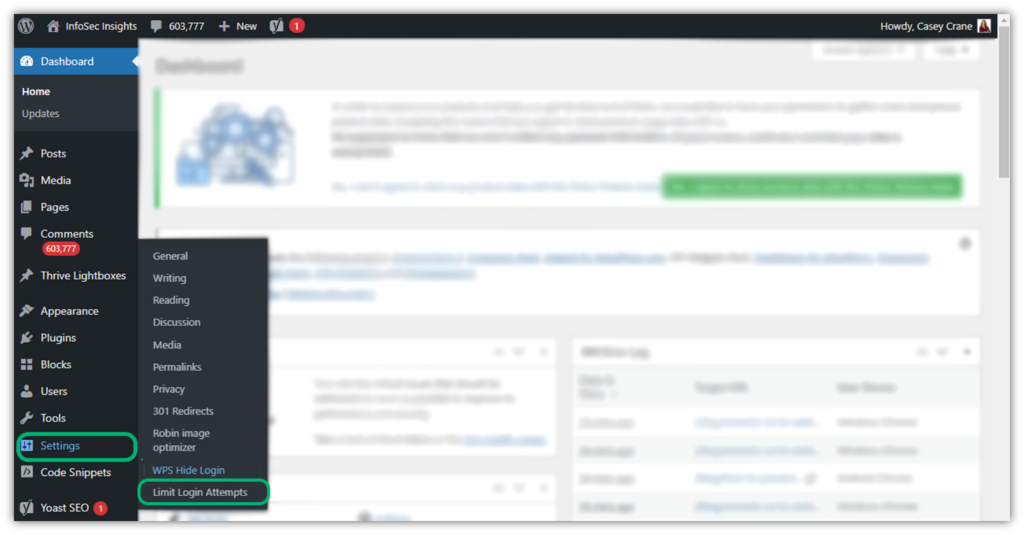
Once you click there, it’ll bring up a new screen where you can customize your settings. For example, you can specify the number of allowed login retries, lockout times, and how many hours until password retries are reset.
10. Whitelist Specific Geographic Region IP Addresses (or Blacklist Others)
Now that we’ve restricted how many times someone can attempt to login, you also can specify which geographic location or IP address groups you’ll allow to sign in to your site. Why is this important? Because if all of your employees are stateside and never has a reason to access your WordPress site’s dashboard from an international location, then it’s just one more way to cut down the number of bad guys who can try to access your site.
Of course, this trick won’t block attackers from those geographic regions if they’re using a proxy server or a virtual private network (VPN) to hide their true locations. But it’ll at least knock out the low-hanging fruit attackers who can’t be bothered to take the extra step to hide their whereabouts.
11. Change Default URLs for Privileged User Login Pages to Unique URLs
Although this isn’t necessarily an industry best practice, this WordPress security tip is one that we’ve come to appreciate over the years. Changing the default URLs for key web pages (such as login pages) makes it harder for cybercriminals to find these access points.
Let’s consider two examples — a default login page and another that’s customized. The first option is the traditional default-style URL: Yourcompanyswebsite.com/login.html. Now, compare this to something unique like yourcompanyswebsite.com/ilikeaccess. Which do you think would be harder for bad guys to find on your website? Definitely the second option!
You can change your WordPress login URL manually or by using a plugin. For the former, simply activate the Hide Login option. Here’s an example of how it looks in WordPress:
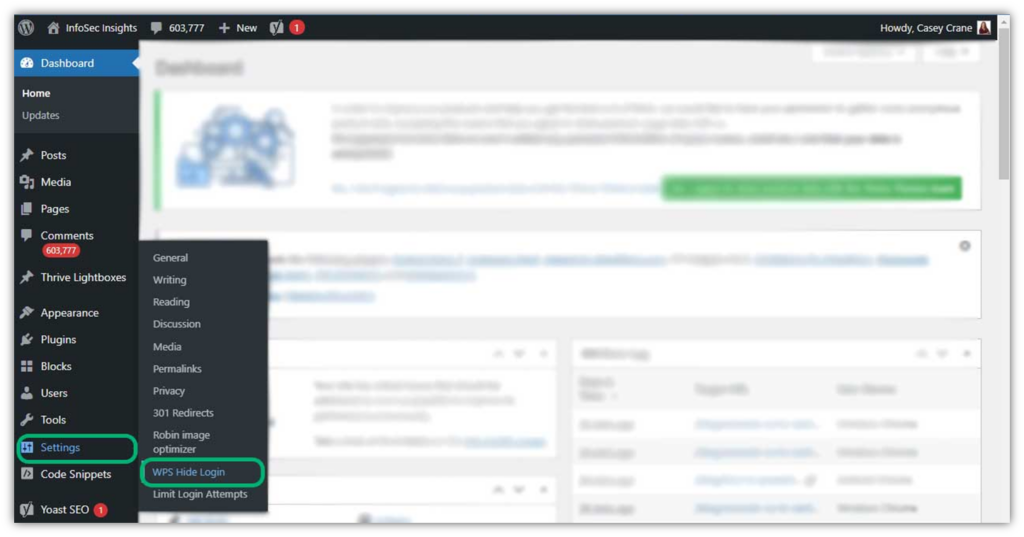
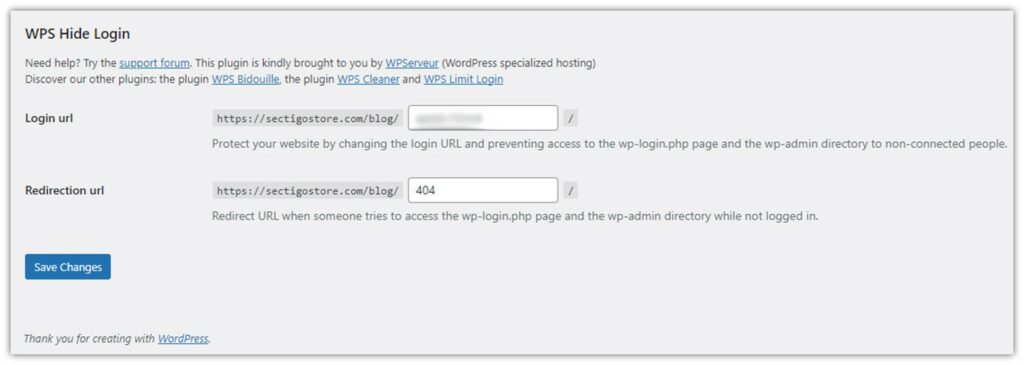
Once you click on the WPS Hide Login option, you’ll see this screen where you can customize your login URL:
Wrapping Up These WordPress Security Best Practices For Enhanced Website Security
W3Techs reports that 63.3% of the websites whose content management systems they track use WordPress as their content management system. This number represents more than 43% of all the websites W3Tech tracks, which makes it pretty substantial. As such, we’re going to continue putting out WordPress security-related content on our blog.
We hope this article on WordPress security best practices and tips serves as a useful resource for your organization. If you’re looking for a more in-depth look at WordPress security, be sure to check out our other related resources:



















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security