Internet Privacy: Anonymity in the Age of Internet Surveillance
Edward Snowden’s 2013 revelations have been heavily debated on both sides by privacy proponents and surveillance supporters alike. However, the one thing that remains indisputable is the impact on trust and the dialogue it has opened up on the topic of internet privacy.
The far-fetched narratives about mass surveillance and governments collaborating with big corporations to undermine privacy and security seems to have jumped out from the realms of dystopian stories and landed in our everyday lives. This is why many users now opt to use the Tor network to maintain their online anonymity. The network uses onion routing and relays to encrypt internet traffic thrice to enable anonymous communication.
In this article, we’ll look at some of the cases where governments and corporations shelved their moral (and often legal) responsibilities to introduce security backdoors that leave us vulnerable to breaches by them and other attackers. We’ll also discuss how to protect your privacy online using open source software and other tools.
Before that, for those of us unsure about the difference between privacy and anonymity — and if they are as important as they’re made out to be — let’s dive into a quick overview.
Internet Privacy: What Do Privacy and Anonymity Mean?
Privacy refers to keeping the activities you do online hidden even though everyone knows your identity. Anonymity refers to keeping your identity under the wraps though your activities are visible to everyone. Within a system that claims to keep you anonymous, there should be no way to link your specific actions to your identity.
Let’s understand these concepts with an example scenario:
It’s Alice’s birthday, and her parents invite all of her classmates — as well as their families — to her birthday party. Everyone’s having a blast until it’s time to cut the cake. That’s when they discover that someone (or multiple people) already ate most of it! In this case, the event is visible — someone ate the cake! But because it could be any of the people attending the party, and assuming there is no way to single one person out, it preserves anonymity.
Now suppose it was Alice’s younger brother, Tom, who ended up eating the cake. He doesn’t want to be grounded for the rest of the week, so he wants his actions (i.e. eating the cake) to remain a secret. While everyone at the party knows who Tom is, nobody is aware of what he did, and that’s privacy.
The government, with the help of their cohorts, claims to want to keep us shielded from the Toms of the world. They want to do this by wiretapping, tracking, monitoring all our actions (legally or illegally). While some might be comfortable with internet surveillance because they believe that they have nothing to hide, others think such individuals don’t realize the full implications such surveillance has on civil rights.
This brings us to the next question…
Internet Privacy: Why It’s Crucial, Even If You Think You Have Nothing to Hide?
We’ve all heard of situations in the workplace where an employee or supervisor’s unprofessional or abusive behavior got reported to human resources (HR) or the ethics and compliance team. Maybe you’ve made such a confidential report against a colleague or supervisor. In such cases, you may want to report a supervisor’s behavior anonymously so as not to derail your own career in the event that they somehow find out that you reported them.
Extend this concept to cover an entire nation. Who keeps tabs on the government that we elect to assess whether they’re using their powers responsibly? And if we raise our voices when they abuse their powers, what options do we have apart from seeking asylum in a country without extradition laws?
Doesn’t anonymity suddenly sound like a really good option right about now?
If any establishment can peep into the lives and minds of all citizens to collect data, monitor their actions and make evaluations based on that information, who’s to say they won’t eventually have the power to manipulate and control us? It’s a slippery slope.
A lot of social movements, especially for marginalized groups, begin in the shadows and gain momentum over time because they’re viewed as having no place in a conventional society. Not all countries are equally open to progress, and not everyone on this planet has access to fundamental human rights. In such scenarios, if online privacy and security become jeopardized, it takes away the platform where individuals can voice their concerns and be heard without risking backlash.
Internet Privacy: To Trust or Not to Trust?
To get a brief glimpse into how serious the threat to online privacy can be, let’s explore a few examples. The following showcase the U.S. and U.K. governments’ blatant disregard for internet privacy:
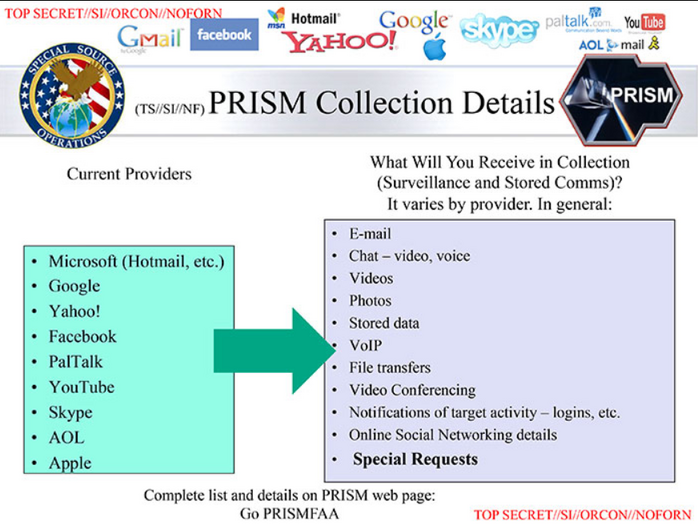
Prism
Prism is the name of a surveillance program under the NSA that compels tech companies like Microsoft, Google, YouTube, Apple, etc. to grant access to user data on their servers.
Optic Nerve
Optic Nerve, a program started by the British intelligence agency Government Communications Headquarters (GCHQ) with the NSA’s assistance, is one that turned the webcams of millions of Britons and Americans against them. It allowed secret access into Yahoo! Webcam chats and took one still image for every five minutes of video per user. These images and their associated metadata were then subjected to experimental facial recognition software. In a six-month period in 2008, it spied on the private conversions of about two million Yahoo! users. The users’ interactions were watched without any targeted focus or limit to only on those individuals who were believed to pose a national security threat.
SIGINT Enabling Project
The SIGINT Enabling Project shatters yet another delusion about the government making efforts in the right direction when it comes to internet security. The NSA spent $250 million per year on this project to bypass encryption in commercial products. They tampered with standards such as those outlined by the National Institute of Standards and Technology (NIST) to weaken protocols and promote vulnerable cryptography.
According to a Reuters report, the NSA paid $10 million to RSA, an influential network security company, to create backdoors in encryption products. RSA set DUAL_EC_DRBG, an algorithm known as a Dual Elliptic Curve Deterministic Random Bit Generator, as the default cryptographically secure pseudo-random number generator (CSPRNG) in its BSAFE toolkit. Until 2014, DUAL_EC_DRBG was considered one of the NIST standardized CSPRNGs.
The world that we live in today is one dominated by alliances such as Five Eyes, Nine Eyes, and Fourteen Eyes. There are several mass surveillance projects run by governments from across the world that attempt to sidestep security controls by force of law, exploiting backdoors, or hacking.
With all of this in mind, what can you do to protect your internet privacy? In the following section, we look at how you can protect your privacy online using various tools and techniques.
Internet Privacy: 10 Ways to Increase Your Data Privacy and Anonymity Online
Every time you visit a website, your browser can potentially reveal a wealth of information about you — everything from your browsing history and search queries to the movements of the mouse on a web page.
Ever wonder why you get flooded with ads similar to the bag you added to your shopping cart? It’s because websites use cookies that can profile you based on your digital behavior, search history, and interests. This information is exceedingly useful (and valuable) to advertisers, website owners, etc.
So, what can you do to limit their access to your data and increase your internet privacy? Let’s look at some ways to avoid tracking while surfing the internet. You can choose to implement some or all of these depending upon your preferred level of online privacy:
1. Clear Your Cache and Delete Temporary Internet Files
Want to increase your internet privacy in the most basic way? Delete your browser cache and temporary internet files to remove stored cookies. The Cookie AutoDelete extension, available on both Chrome and Mozilla, allows you to automate this task. (Note that this will also clear your saved passwords and other details that prepopulate your forms!) Use a password manager instead if you need to autofill your credentials on various sites. Password managers such as Dashlane can also be added as extensions to store, manage, and autofill your passwords.
Once your cookies are deleted, use ad blockers and anti-tracking tools to avoid disclosing your browsing habits without consent.
2. Use Incognito or Private Browsing Mode
Use incognito mode while surfing, especially if you’re on a shared computer or device. but be aware that it doesn’t hide your browsing history from your internet service provider. The private browsing mode merely removes the cookies and deletes your browsing history after you close the window. It’s similar to how you manually clean out the cache and delete temporary internet files. Like the above, it doesn’t provide you with anonymity.
You can allow ad blockers, anti-tracking extensions, and other security plugins to run in incognito mode by adjusting the settings.
3. Use Extensions That Protect Your Privacy Online
Ad blockers and anti-tracking extensions such as Ghostery and Privacy Badger allow you to have some control over your browsing experience. You can view which trackers they block and choose to block or unblock additional trackers.
VPN extensions like NordVPN and SurfEasy, or free alternatives like Windscribe, offer ways to encrypt your traffic from your machine to the exit point of the VPN network. These solutions aim to prevent eavesdroppers from listening in on your network traffic. Websites you visit will see the VPN’s IP address instead of yours. There have been concerns about some free as well as paid VPNs, so be sure to research thoroughly before opting for any such service.
You can also opt for extensions like FoxyProxy to switch your connection across multiple proxy servers.
4. Use the Tor Network to Surf the Internet
Use the Tor browser as it was built for enabling anonymous communication. It uses onion routing to not only prevent third-party trackers from following you around but also to mask your IP address from prying eyes. The idea is to prevent an observer from linking your activities on the web to you. Of course, that requires certain precautions on your end as well, such as:
- using pseudonyms to protect your actual identity,
- compartmentalizing your social media use, and/or
- not leaving trails of your real email addresses.
Orbot is the Tor for Android. It packages the anonymizing features and functionalities of Tor and brings it to the Android mobile operating system. The bad news? There’s no official Tor app for iOS due to interoperability issues. The good news? The Tor project has endorsed the open-source Onion Browser.
5. Switch Search Engines
Don’t use Google. Switch to DuckDuckGo or Startpage as these search engines do not track or store any information about you, or place cookies on your machine. Keep this in mind, especially when you’re using the Tor network.
6. Use a Trusted Service for Instant Messaging
Use open-source apps that use an end-to-end encryption such as Signal, Ricochet, Kontalk, etc. Telegram is another cloud-based, heavily encrypted IM option, but its server-side code is proprietary. Of course, WhatsApp also has an end-to-end encryption, but then again, it’s owned by Facebook. Make of that what you will.
As a general rule of thumb, whenever you use any piece of software, make sure that you have reasonable trust in its creators. Open source applications have a broader scale in terms of access to developers across the globe, and they’re not limited to a company’s payroll. They get exposed to use cases not originally intended by the developers, revealing bugs early on that necessitate rapid development cycles and frequent update releases.
7. Review Your Choice of Operating System
As you already know, Windows by Microsoft (the first company that agreed to participate in the PRISM program) isn’t the only operating system out there. If you’re concerned about privacy and anonymity, switch to security-focused Linux distributions such as Whonix or Tails.
Both operating systems route their traffic through Tor to prevent your IP address from leaking. However, Tails, a live operating system, is better suited from the point of view of forensics as it leaves no trace. Whonix, which runs in two virtual machines (VMs), provides isolation of your workstation from the network. This makes it a better choice concerning persistence and isolation.
With Whonix, you need to take steps to wipe your forensic history. It’s not recommended to use a VPN along with Whonix. Qubes OS, based upon Linux and the XenClient XT architecture, is designed to provide security via compartmentalization and isolates various components. If one gets compromised, the others aren’t affected.
For Android users, Lineage OS, an open-source operating system, comes packed with customization and security features that might help you extend the lifespan of mobile devices.
8. Choose the Right VPN
Select the right virtual private network (VPN) in terms of whether it logs traffic or IP information, or if it falls within the jurisdiction of countries with surveillance alliances. There are many VPN providers with a no data logging policy. Some even offer free plans, but with limits on server availability and the number of simultaneous connections that it supports. You should spend some time researching and running a detailed VPN comparison before making a purchase.
9. Use Good Sense to Judge Whether an App Is Requesting Excess Permissions
It might make sense for a fitness app to track your location to count your daily steps, but if it requests access to read your call logs or messages, it should raise a red flag. Always watch out before hitting on the allow button and take a moment to evaluate if the app you’re downloading needs access to the information it is requesting. The ProtectMyPrivacy (PMP) app can:
- detect when other apps try to access privacy-sensitive data,
- give the user some context before making decisions about permissions, and
- has the capability to share suitably anonymized data.
10. Some Other Tools for Maintaining Internet Privacy and Anonymity Online
HTTPS Everywhere — This extension encrypts your traffic on the web to make your surfing experience more secure. This is especially useful on sites that continue to default to the unencrypted HTTP protocol.
ProxyChains — This UNIX program forces all TCP connections to be routed through a series of proxy servers to provide you with greater anonymity.
Utopia — This decentralized, peer-to-peer ecosystem supports personal messaging, email, file sharing, etc. over a secure connection without the involvement of a third party.
Open Observatory of Network Interference (OONI) — This free software, under the Tor Project, is a global network that you can use to observe and detect censorship, surveillance, and traffic manipulation over the wire.
Final Thoughts
While achieving a 100% anonymity or ensuring impermeable online privacy remains a fantasy, there are certain measures you can take to be in charge of your digital footprint. By supporting those who make it possible to have privacy in the age of mass surveillance, and by using tools that protect our data, we can work to ensure that the internet continues to be an autonomous platform.
























 (15 votes, average: 4.20 out of 5)
(15 votes, average: 4.20 out of 5)






No comments