What Is Symmetric Encryption and How Does It Work?
Everyone loves to talk about the role of asymmetric encryption in online security. Today, we’re here to explore symmetric encryption and its role in keeping data secure online.
Have you ever wondered what steps websites and online platforms take to protect your confidential information from cybercriminals? Or what prevents someone from stealing your data while it’s stored on a server or traveling from one point to another? Symmetric encryption is part of the answer.
In this article, we’ll discuss what symmetric encryption is, how it works and is used, and how it differs from its newer relative asymmetric encryption (i.e., public key cryptography).
To Understand Symmetric Encryption, You First Have to Understand Encryption…
Before we dive headlong into the topic of symmetric encryption, let’s quickly brush up on some basic concepts like encryption and cryptographic keys (more specifically, the private keys).
Don't make the same mistakes
Yahoo, Equifax, Home Depot,
LinkedIn, and Ericsson did!
Get our free 15-point checklist and
avoid the same costly pitfalls.
Contact details collected on InfoSec Insights may be used to send you requested information, blog update notices, and for marketing purposes. Learn more...
Encryption is the process of converting readable data (the plaintext) into an incomprehensible format so that only the person who has the key can access or read it. Without the key, the encrypted information, called ciphertext, looks like gibberish. Without the key, it’s impossible to work out the original data from the ciphertext.
Encryption is like locking a valuable item inside a lockbox. If someone has the lockbox but not the key, they can’t access the concealed item inside. In the same way, to lock (encrypt) the data, you need a key.
When most people think of encryption on the internet, they think of SSL/TLS encryption. This uses a combination of asymmetric and symmetric encryption. Asymmetric encryption uses two cryptographic keys to encrypt (public key) and decrypt (private key) data. But how does this differ from symmetric encryption? That’s what you’re about to find out.
What Is Symmetric Encryption?
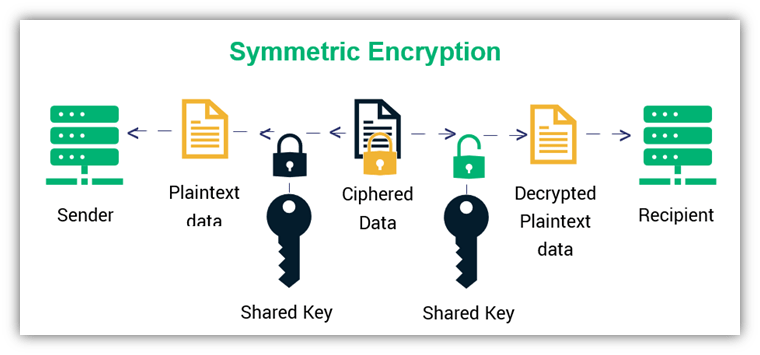
Unlike its asymmetric counterpart, symmetric encryption uses a single cryptographic key to encrypt and decrypt data. This is why it’s also known as private key encryption, private key cryptography, shared secret encryption, or shared secret cryptography.
In symmetric encryption, the sender and recipient must keep this key secret to protect the data. This is why other names for the symmetric key are the private key, shared secret, or secret key. The key itself is a long string of random and unpredictable alphanumeric characters. If it is lost, leaked, or stolen, then the key’s privacy is compromised and should no longer be used.
In a nutshell, the process of symmetric encryption goes like this:
- The sender applies the symmetric key to the plaintext data to encrypt it, producing the ciphertext.
- The sender sends the ciphertext to the recipient.
- The recipient applies the same shared key to the ciphertext to decrypt it.
Is symmetric encryption something new? Absolutely not. Symmetric encryption has been around for a long time — one example, called the Caesar Cipher, has been around since the days of the Roman Empire! (We’ll explore that more in depth a little later.) And it’s thought that symmetric encryption existed well before that.
Compare this to asymmetric encryption, which has only been around since the 1970s or so.
Examples of Symmetric Algorithms
So, what are some common symmetric ciphers you’ll find in use today? Some popular symmetric key algorithms include:
- Advanced Encryption Standard (AES)
- Blowfish
- ChaCha20
- Serpent
- RC5
A Look at How Symmetric Encryption Works
Symmetric encryption works by using a single key to encrypt and decrypt data. This means that one person sends data to another person that they encrypted using a shared key. The recipient then uses the same shared key to decrypt the data. That’s really it in a nutshell.
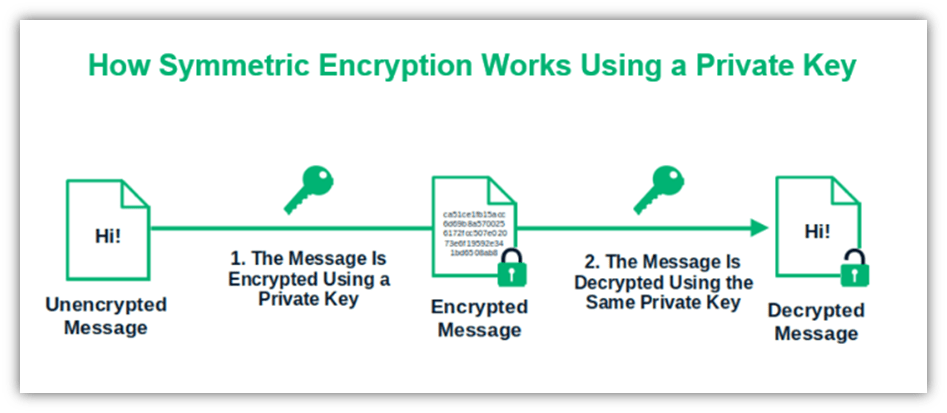
Let’s Break It Down a Bit More…
So, how would it look to encrypt a message using symmetric encryption? Let’s use a basic version of a symmetric cipher, called shift cipher (in this case, the Caesar Cipher we mentioned a little earlier), as an example.
Let’s say you want to encrypt the word “Enterprise.” (Gotta love Star Trek.) You decided to shift each alphabet by a fixed number of spaces (i.e., shift it four letters to the right in the alphabet).
| Plaintext | E | N | T | E | R | P | R | I | S | E |
| The number of spaces each letter shifts | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 |
| Resulting ciphertext | I | R | X | I | V | T | V | M | W | I |
Here, the cryptographic key is four, and “IRXIVTVMWI” is the ciphertext. This kind of cipher uses a symmetric key, which means the same key is used for encoding and decoding. It’s vital to keep the key secret as anyone who knows it can decode the message. In this case, they would subtract four from the ciphertext values to access the original text.
Of course, modern shift ciphers are more complicated. They use a modifier (mod) in addition to the key. But for the sake of simplicity, just go with us here on this.
Now, let’s take an example of a more complex key. Suppose you generate a larger number instead of a single-digit one (four in the above example) for each alphabet to shift the letters.
| Plaintext | E | N | T | E | R | P | R | I | S | E |
| The number of spaces each letter shifts | 150 | 150 | 150 | 150 | 150 | 150 | 150 | 150 | 150 | 150 |
| Resulting ciphertext | Y | H | N | Y | L | J | L | C | M | Y |
Here, the symmetric encryption key is 150, meaning each letter shifts 150 spaces in the alphabet (resulting in “YHNYYLJLCMY” as the ciphertext). As you can see, this key is more complex than the previous one. Only someone with this key knows how many letters to shift in the alphabet to access the original data. Imagine doing this with a key that’s hundreds of bits in length.
For humans, larger keys are difficult to compute and the process of breaking them becomes increasingly challenging. But for computers, these types of keys are not difficult to crack.
Nowadays, significantly complex mathematical algorithms are used to generate keys. These keys are much longer, more complicated, and devised in a way that even modern supercomputers need years to crack them. A modern encryption key looks like this (NOTE: This example key was generated using digitalsanctuary.com’s AES key generator tool):
5Q7ZaYrBMFUzBT/F4h9HCQBf7WFzlSVcgDJWtMXVo10=How Is Symmetric Key Encryption Used?
We use symmetric encryption all of the time in our day-to-day lives. In fact, you’re using it right now. The data transferred between your browser and our website’s server is encrypted using symmetric key encryption.
Of course, this was made possible through the SSL/TLS handshake, which negotiated the symmetric key exchange for your web session. However, symmetric encryption is used for most of the session because it’s faster and requires fewer resources.
But what does this look like in practice? Say, when you visit a website. In a typical website connection, a process known as the SSL/TLS handshake allows your browser and the website’s server to exchange a symmetric session key. Let’s simplify the handshake process:
- After exchanging hello messages and some other essential data with the server, your browser generates a symmetric key (i.e., the session key).
- It encrypts this session key with the website’s public key (using asymmetric encryption) and sends the secure key to the server where the website is hosted.
- The server then decrypts the session key using its private key.
- Now, the data transmitted between your browser and the website is encrypted and decrypted using the symmetric session key.
Symmetric encryption is commonly used to encrypt data at rest (i.e., stored data). Much of our data stored on the various cloud platforms and servers is protected with symmetric encryption. It’s a convenient method to protect a large quantity of data as it is less resource-intensive than asymmetric encryption.
5 Things to Know About Symmetric Encryption
Let’s dive into learning more about symmetric encryption.
1. There Are Two Main Types of Symmetric Encryption
There are two main types of symmetric encryption ciphers: block and stream ciphers.
Block Ciphers
This method of encryption divides the plaintext data into fixed-sized blocks and encrypts each block separately. So, let’s say we want to encrypt the message “U.S.S. ENTERPRISE.” The sentence, including the spaces and period, has a total of 18 characters. We’d make three blocks of six characters, as shown below. (NOTE: the underscore [_] in the following example represents the space between the words.)
- Block one: U.S.S.
- Block two: _ENTER
- Block three: PRISE.
If the final block contains less than the particular number of characters that the block cipher uses (in our example, six), extra bits are added to pad it out.
In real life, block cipher algorithms are much more complex, and the data tends to be in billions of bits. Messages go through various rounds of encryption before the final ciphertext is produced. The Feistel cipher is a popular basis for constructing symmetric block ciphers.
Stream Ciphers
A stream cipher encrypts one element of the plaintext at a time — bit by bit, rather than in blocks. When we shifted the letters in the word “ENTERPRISE” separately to encrypt the entire word, that was an example of a stream cipher.
2. Symmetric Cryptography Uses Smaller Keys That Process Faster
The strength of symmetric keys typically ranges between 40 bits and 256 bits. This is much shorter than asymmetric keys, which can be up to 4096 bits (2048 is recommended for RSA). This means that symmetric keys on their own are less secure in public channels (meaning, you’d have to use asymmetric encryption to share the symmetric key first — i.e., like what happens in the SSL/TLS handshake).
Generally speaking, symmetric keys are faster and less burdensome than asymmetric keys in terms of computational speed and processing power.
3. Symmetric Encryption Is More Efficient (But Less Secure) Than Asymmetric Encryption
Symmetric encryption encrypts large chunks of data. Because only one key is used, and the key sizes are short, the encryption and decryption processes become more efficient than those in asymmetric encryption.
However, it doesn’t scale as well as asymmetric encryption. This is because sharing a symmetric key with one person isn’t necessarily a big risk. But if you share the same key with 50, 500, or even 5,000 people, then it’s less likely to remain secure.
So, while symmetric encryption is more efficient than asymmetric encryption, it’s also less secure when used alone.
4. Symmetric Key Distribution Requires Asymmetric Encryption in Public Channels
One problem with symmetric encryption is secure key distribution. Imagine that two people living on opposite sides of the world want to use symmetric encryption to encrypt their communications. They’d either have to meet up in person or find a way to securely exchange that shared key remotely in order to do so. (For the latter, think back to the asymmetric key exchange I mentioned earlier.)
If they share the private key over an insecure connection, then it’s at risk of someone stealing it in transit.
5. Symmetric Encryption Should Be Used With Other Cryptographic Functions
Ideally, the secret key should only be accessible to the sender and the authorized recipient(s). However, there is no mechanism to verify the identity of the key holders. That’s why symmetric encryption is often used along with asymmetric encryption, where the public and private keys protect the secret key. The sender encrypts the secret key-related data using the recipient’s public key. The recipient can decrypt it using their corresponding private keys.
The enciphered data can’t be decrypted without the secret key, but it can be modified or tampered with. So, while the encryption on its own provides data privacy, it can’t guarantee data integrity. That’s why it is used with hashing to detect data alteration.
How Does Symmetric Encryption Differ from Asymmetric Encryption?
Let’s quickly compare both types of encryption to explore their algorithms, use cases, strengths, and weaknesses. This is just a brief comparison. For a more detailed comparison, check out our article on the 5 Differences Between Symmetric vs Asymmetric Encryption.
| Symmetric Key Encryption | Asymmetric Key Encryption | |
| Number of Keys | Only one key is used for encryption and decryption. | This process uses two separate keys to encrypt (public) and decrypt (private) data. |
| Key Security | The symmetric key is accessible to both the sender and recipient. However, it should not be shared publicly. | The message sender can access the recipient’s public key (which is publicly known), whereas the private key securely remains with the recipient only. |
| Popular Algorithms | Advanced Encryption Standard (AES)ChaCha20BlowfishSerpentRC5 | Diffie-HellmanRSAECDSAElGamalDSAECC |
| Key Length | Symmetric key length ranges from 40 bits to 256 bits. | Asymmetric keys can be as long as 4096 bits. |
| Speed | Processes faster due to its shorter key and smaller computational load. | It’s a slower process due to its larger keys and larger computational load. |
| Preferable Usage | It is preferable for encrypting data at rest and large quantities of transmitted data when using a secure, encrypted connection. | It is preferable for encrypting smaller amounts of data, particularly in a public (i.e., insecure) channel. |
| Number of Endpoints | The more endpoints that are involved, the riskier the key distribution process becomes. | Asymmetric encryption is preferable when many endpoints are involved. |
Final Thoughts on Symmetric Encryption
We live in a world where data is stored digitally and transferred over the Internet. Encryption is central to protecting data in these situations, and symmetric encryption is the most suitable method for large quantities as it’s speedy, secure, and less resource-intensive than asymmetric encryption.
However, symmetric encryption does have limitations. This is why it’s often paired with asymmetric encryption and hashing to ensure identity authentication and data integrity. It’s this pairing of symmetric and asymmetric cryptography that makes secure communications possible.
While asymmetric encryption often steals the spotlight, symmetric encryption is there, working in the background to quietly safeguard our data in countless online transactions.



















![The TLS Handshake Explained [A Layman’s Guide]](https://sectigostore.com/blog/wp-content/uploads/2023/01/tls-handshake-feature-300x200.jpg)


2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security