What Is the Advanced Encryption Standard? AES Encryption Explained
Encryption standards have come a long way since they first appeared in the 1970s. The first data encryption standard, DES, is obsolete and the world has moved onto AES encryption. The encryption provided by AES is much stronger than that of its predecessor. So, what is AES encryption and why does it hold a vital position in modern cybersecurity?
In a world where the internet is a necessity, encryption is crucial for the privacy and integrity of our data. In general, encryption is a cryptographic process that takes plaintext, readable data and turns it into something indecipherable. This is done using either a single key (symmetric encryption) or two different but related keys (asymmetric encryption) to, essentially, scramble or unscramble data shared between two parties.
In an interview with Time magazine, Apple Inc. CEO Tim Cook emphasized the significance of encryption in our online transactions and shared how it protects us from being ripped off by criminals.
Of course, there are different types of encryption and many more types of algorithms. One of the most popular, by far, is the advanced encryption standard, or AES. But what is AES encryption and why is it so important in online communications?
What Is AES Encryption? An AES Definition and Explanation
AES is a type of symmetric encryption, meaning that it uses a single key to both encrypt and decrypt data. (This differs from asymmetric encryption, which uses a public key to encrypt and a private key to decrypt data.) The advanced encryption standard is endorsed by National Institute of Standards and Technology (NIST) and is used by the government agencies and contractors to secure sensitive information from prying eyes.
At its core, cryptography is based on mathematical functions and calculations. The security of the algorithm is in direct proportion to the complexity of the calculations. AES is one of the most secure algorithms around and uses highly complex mathematical functions to encrypt data. Nevertheless, the AES algorithm is short, secure, and compatible with most hardware, software, and firmware.
Today, the AES algorithm is used all over the world in software, hardware, and firmware in all kinds of devices. It’s free to use for public or private enterprises, for commercial or non-commercial purposes.
AES Encryption Keys Come In Multiple Sizes to Offer Varying Levels of Security
It’s available in different varieties based on the size of the encryption keys used:
- AES 128 bits (or 3.4 x 1038 possible combinations),
- AES 192 bits (or 6.2 x 1057 possible combinations), and
- AES 256 bits (or 1.1 x 1077 possible combinations).
So, what does all of this mean? Let’s put it in a little perspective. According to NIST: “For a 128-bit key size, there are approximately 340 undecillion (340 followed by 36 zeros) possible keys.” AES-256 is an exceptionally strong algorithm and is considered quantum resistant algorithm — meaning that quantum computers won’t be able to crack it in a practical amount of time to make quantum computing a threat to it.
Where Is AES Used?
AES is the most widely trusted encryption standard in the world. It’s used to secure data in all kinds of public and private settings, including:
- Online shopping and banking
- Website SSL/TLS certificates
- Virtual private networks (VPNs)
- Mobile apps including WhatsApp and LastPass
- Computer processor chips and operating systems
The Benefits of Advanced Encryption Standard (AES)
There are many reasons why AES is so popular, including:
- Robust Security. AES 256 is the most secure encryption developed so far and is used by the United States federal government for even the most sensitive information. Because of its impracticality to crack, it is accepted worldwide as a reliable algorithm.
- Standardized Algorithm. NIST has standardized the AES algorithm and made it an open-source resource, so it becomes easier for the general public to accept it as trustworthy. There are also no interoperability issues as hardware, software, and firmware all use the same algorithm.
- Variable Key Lengths. AES encryption can be done using different key lengths, including 128-bit, 192-bit, and 256-bit keys. For a businessperson using AES to protect their eCommerce account, 128-bit is ideal. Governments protecting their sensitive documents can use AES-256 for greater security.
- Fast Encryption/Decryption Speed. The processing speed of AES encryption is faster than both DES and Triple-DES. On the same hardware, AES is around six times faster than Triple-DES.
- Low RAM Requirements. When NIST declared it wanted a replacement for DES, they specified that the new algorithm should be supported even on devices with limited computing capabilities. AES fulfills that requirement to a ’T’. It works just as well on 8-bit smart cards as high-speed computers.
A Brief History of the Advanced Encryption Standard
The original data encryption standard (DES) had serious limitations that made it vulnerable to brute force attacks. DES began to lose its footing as a secure algorithm and, in 1997, the NIST began looking for a more secure alternative. NIST wanted an algorithm that was more powerful than DES and Triple-DES, with longer keys for more security. This is where the advanced encryption standard came into play.
Whereas DES was mainly supported by special-purpose hardware, AES was to be implemented on all kinds of software and hardware. It also had to work on hardware with limited computational capacities like smart cards or IoT devices.
Selection Process of the AES Algorithm
Some people mistrusted the DES algorithm, as the source code was not open. There were also rumors that the National Security Agency (NSA) had designed a backdoor in the algorithm to spy on users. Although NSA denied these allegations, trust was hard to recover. So, with AES, NIST wanted to involve the cyber community and the public from the start, hoping to win their trust. This process is one of the major reasons behind the widespread acceptance of AES.
NIST announced AES development in January 1997, putting out a call for proposals in September the same year. They received 15 viable proposals from people around the world, including Australia, Belgium, the USA, South Africa, Japan, and Korea. These were announced at the first AES Candidate Conference in August 1998.
The second AES Candidate Conference (AES2) was held in March 1999 to discuss the proposed algorithms. Based on expert analysis and comments received from the public in Round 1, NIST selected the best five algorithms from the proposals.
In Round 2 comments were again sought from the general public and an online forum was held to discuss the five finalist algorithms. NIST used this forum to examine and discuss issues around the algorithms, from implementation problems to intellectual property issues.
AES3 was held with the developers of the five finalists in New York USA over two days in April 2000. Finally, on October 2, 2000, NIST declared the Rijndael cipher as the new advanced encryption standard.
Details of the new AES were published as Federal Information Processing Standards Publication 197 (FIPS 197) on November 26, 2001. Subsequently, NIST began a cryptographic algorithm validation program (CAVP) to test every component of the algorithm before its implementation.
NIST made a few alterations to the Rijndael algorithm, changing block sizes and key lengths. In the original Rijndael cipher, the block and the keys were of variable lengths ranging from 128 bits to 256 bits. Of course, Rijndael’s authors Joan Daemen and Vincent Jijmen later expanded the variable key and block sizes in the multiples of 32 bits, thereby expanding the list of key and block sizes to 128, 160, 192, 224, and 256.
However, AES has a fixed block size of 128 bits and has the varying key lengths of 128, 192, and 256 bits that we touched on earlier.
What’s the Difference Between DES and AES Encryption Algorithms?
The difference between AES and DES extends beyond their respective security strengths. For example, AES is based on a substitution-permutation network. Just like its predecessor DES, AES is a block cipher, meaning it divides the plaintext into blocks before encrypting it. Additionally, like DES, AES is a symmetric cipher that uses the same keys to encrypt and decrypt the data. This is where the similarities between the two end and the differences between DES and AES begin:
| DES Encryption | AES Encryption | |
| Still In Use and Considered Secure? | No — DES has known vulnerabilities that can be exploited | Yes — AES has no known vulnerabilities, currently accepted as the standard for symmetric encryption |
| Cipher Structure | Based on the Feistel structure | Based on a substitution-permutation network |
| Key Sizes | Key size is 64 bits (8 of which are parity bits, meaning it’s really a 56-bit key) | Keys are available in 128 bits, 192 bits, or 256 bits |
| Block Sizes | 64-bit block size | 128-bit block size |
| Encryption Rounds | 16 rounds of encryption | Number of rounds depends on the key-length used – 128-bit key has 10 rounds, – 192-bit key has 12 rounds, and – 256-bit key has 14 rounds. |
How Does AES Encryption Work?
Let’s briefly explore the process of how the advanced encryption standard works to scramble data. In a nutshell, AES encryption takes the plaintext input data and divides it into 128-bit chunks of data called blocks. A single cryptographic key is then used to generate different subkeys — sometimes called round keys because a separate subkey is used for each round of processing — that will be applied to the different chunks of data. This produces a ciphertext for that data block.
Each block of ciphertext is then added onto the next until, finally, the final ciphertext is created that is the same size as the initial input data.
Depending on the size of the key used, the data will go through 10, 12 or 14 rounds of processing. It’s also important to note that no two round keys are similar. Moreover, as the AES encryption doesn’t use an initial vector; one additional key is generated for encryption at the beginning.
Here’s a great video that walks you through how the AES encryption process works:
The detailed process of AES is explained in our next article. You will be able to learn more about all the jargon used in the process here.
How Secure Is AES?
IBM Security reports that if an organization using 256 AES encryption suffers a data breach, the average cost of the breach would be 29.4% ($1.25 million) less than breaches that involve data secured by no encryption or encryption that uses less secure algorithms. Because AES is much harder to crack than weaker encryption functions, less data would be at risk.
So, just how hard is it to crack AES encryption, and how long does it take with current present processing power? To answer those questions, we’ll have to do some math.
Grover’s Algorithm
In 1996, when NIST was searching for a replacement for DES, Lov Grover was developing what would come to be known as Grover’s algorithm, or the quantum search algorithm. It’s the most powerful tool that can be used against AES and other symmetric algorithms.
Although Grover’s algorithm can’t completely crack symmetric encryption, it can weaken it significantly, thereby reducing the number of iterations needed to carry out a brute force attack. Using this algorithm, the number of iterations required to crack a 128-bit symmetric cryptographic key can be reduced from 2128 to 264. Similarly, a 256-bit symmetric key can be reduced to 2128 iterations, thus reducing the time taken to perform a brute force attack. It still takes a very, very long time though.
How Long Would It Take to Crack AES?
Just how much time does it take to carry out these iterations to try to crack an AES key? To find out, let’s think about one of the most powerful systems operating today — the Bitcoin network. At its peak, the network performed 150 * 1018 ≈ 267 operations per second. With this kind of power, it would take 70,000,000,000,000,000,000,000,000 years to crack AES-128. Knowing that AES-256 has 2128 times as many keys as AES-128, it means that cracking a 256-bit key would take even longer. Much, much longer!
Which Key Length Is Best?
With an increase in key length comes an increase in processing power needed, putting AES-256 out of reach of most regular users. AES-128 is the optimum choice for regular business use, striking the balance between security and practicality.
Although clearly, the 128-bit key is weaker than the 192-bit and 256-bit keys, nobody has cracked AES-128 to date, so using AES-128 is still considered secure — for now. However, AES-256 offers military-grade encryption that’s impossible to break with current processing capabilities, so it’s an option if you have enough processing power.
The Economic Impact of AES
In 2018, NIST published a study on the economic impact of AES from 1996 to 2017. The positive economic impact of the program is estimated to be $250 billion over these years, and the report states that the economy as a whole benefited by a ratio of 1976-to-1 against the cost incurred by NIST.
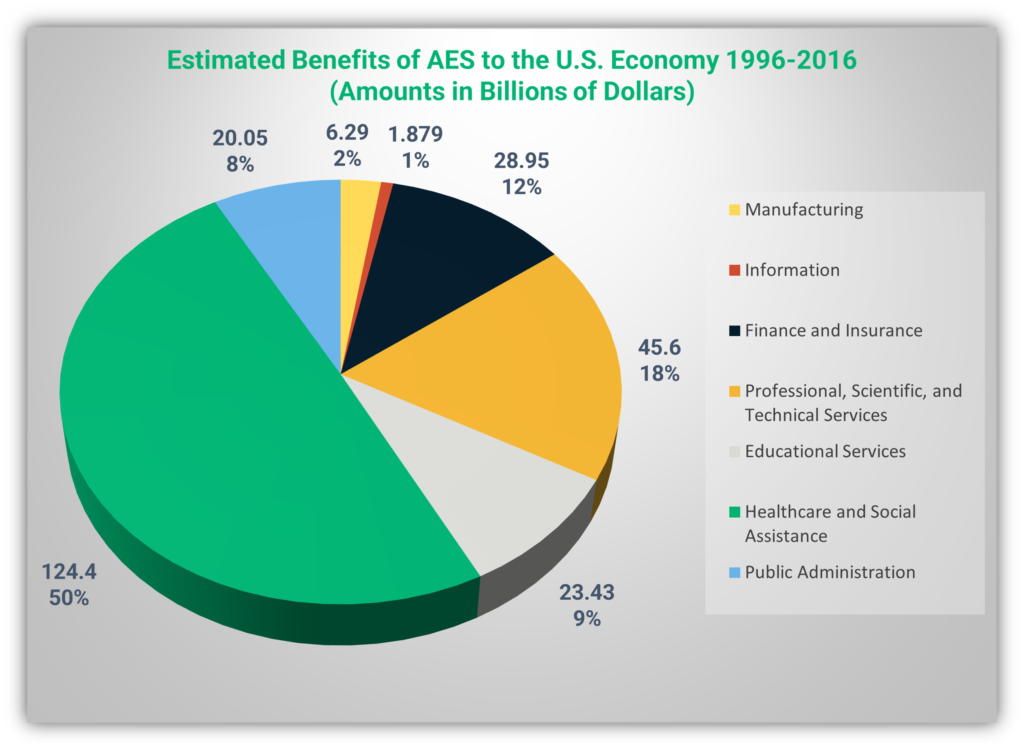
The strong encryption provided by AES was integral to the rise of the eCommerce, remote work, and social media apps that we use every day.
Final Thoughts on AES Encryption and the AES Algorithm
AES encryption is a system that uses complex mathematics to encrypt data, mainly data at rest (stored data). The algorithm is a block cipher that uses symmetric keys to encrypt the data. Due to its impeccable security, AES is recommended by NIST and the NSA in the US, leading to its acceptance as a trusted standard across the globe.
AES is not only secure but is compatible with hardware, software, and firmware. The algorithm is capable of working on hardware with limited computing capacity making it irreplaceable in ecommerce. We’ll look at how AES encryption works in more detail in the next article.
Never forget that cybercriminals can exploit other weaknesses to access your network, like weak passwords, or badly configured firewalls. AES is not a complete security solution but just one tool you should have in your security toolbox.

















![The TLS Handshake Explained [A Layman’s Guide]](https://sectigostore.com/blog/wp-content/uploads/2023/01/tls-handshake-feature-300x200.jpg)



2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security