Email Security Best Practices & Tips From 10 Industry Experts
Egress reports that in 2023, 94% of organizations experienced email-based security incidents. 10 industry experts share email security best practices and tips that can help boost your email security posture
How secure is your email? Hint: It’s not as safe as you think. Between October 2013 and December 2023, small and large organizations worldwide reported to the FBI’s Internet Crime Complaint Center (IC3) a total of $55.5 billion worth of losses. The root cause? Business email compromise (BEC). Abnormal Security reports that these attacks against smaller organizations increased by nearly 60% in the first half of 2024.
However, BEC is just one among the many email security threats organizations are facing:
- Abnormal Security (in the previously cited report) indicates that file-sharing phishing attacks increased by 350% in a single year.
- Osterman Research showed that 80% of critical infrastructure firms that were victims of an email security breach in the past 12 months were hacked through phishing attempts, malicious links, or infected attachments.
- ReliaQuest revealed that phishing remained a top threat in 2023, with 71.1% of attacks using spearphishing as the attack method.
So, how can you increase your organization’s email security? No need to consult a crystal ball — we’ve posed this question via email to IT and cybersecurity experts from around the industry. Here’s what they had to say…
Don't make the same mistakes
Yahoo, Equifax, Home Depot,
LinkedIn, and Ericsson did!
Get our free 15-point checklist and
avoid the same costly pitfalls.
Contact details collected on InfoSec Insights may be used to send you requested information, blog update notices, and for marketing purposes. Learn more...
Actionable Email Security Best Practices & Tips From 10 Experts in the Field
More than five decades after the first Arpanet email was sent, this method of communication remains a vital tool across all industries. But it also lives on as one of threat actors’ favorite attack vectors. Of course, the advent of artificial intelligence (AI) makes things even more challenging. GenAI tools eliminate many of the tell-tale signs of phishing emails, such as poor grammar and spelling, by writing the messages for them.
The good news is that there are ways to prevent the worst from happening. Let’s explore email security best practices and tips that can help you avoid becoming the next email security breach casualty.
1. Make Password Security Your Top Priority
Did you know that, according to Spycloud’s 2024 identity exposure report, 74% of users re-utilized their previously compromised passwords after the breach? OK, we know you would never reuse your passwords… but what about your employees and other network users? Would you swear that they wouldn’t do it? Doubtful.
Once a crook has the victim’s email address and password, they have the keys to their kingdom — and sometimes yours, too. The attacker can use the info to reset passwords for other accounts or services, access credit card details and reports, steal sensitive information — you name it.
Knowing this, it’s no surprise why providers like Microsoft and Google have changed their authentication policies, and the U.S.’s National Institute of Standards and Technology (NIST) has updated its password guidelines for federal agencies. But what do our experts have to say about it?
Brian Pontarelli, CEO of FusionAuth, emphasizes what should be on your top list of email security best practices and priorities. “Password security and encryption have been a top priority from day one. We implement password encryption best practices to keep our customers’ accounts safe.”
But that isn’t all. The engineer at heart who held several engineering roles to start his career, including at BEA and Orbitz, and served in a leadership role for Denver Startup Week, says there’s still more than can be done:
“For example, we use adaptive password strength checking, breached password detection, and multi-factor authentication (MFA). MFA, whether it’s SMS codes, authenticator apps, or security keys, is the best way to block account compromise. At FusionAuth, we require MFA for all employee accounts.”
Jacob Kalvo, co-founder and CEO at Live Proxies, also emphasizes the power of MFA as an effective additional layer of defense:
“[…] One best practice that I highly advocate is to enforce multi-factor authentication across all email accounts. That adds an additional layer of defense, making it much more difficult for attackers to get unauthorized access, even when they are able to compromise a password.”
They’re not alone. Deyan Georgiev, cybersecurity expert at RapidSeedbox, also highlights the importance of MFA: “Even if passwords are compromised, MFA acts as a second line of defense, preventing unauthorized access.”
2. Don’t Ignore Phishing and Malware Threats
Malware and phishing are two of the most common email security threats. Attackers use fraudulent emails to nudge recipients into revealing sensitive information (e.g., credit card details or login credentials), and malware-infected attachments or links to infect victims’ devices or their organizations’ networks. Malware can be used to launch ransomware attacks, which can bring organizations to their knees.
In 2023, 71% of businesses polled by Proofpoint were victims of phishing attacks (down from 84% the previous year). However, what adds insult to injury is that Proofpoint observed a 144% increase in reported financial penalties compared to 2022, and reputational damages stemming from phishing attacks jumped 50%.
And what about ransomware-related threats? Proofpoint’s research shows that 69% of the survey’s respondents indicated their organizations were infected by ransomware.
Pontarelli is conscious that credential theft isn’t the only email security threat keeping business owners up at night. He recognizes that email-based malware and other phishing-related threats are a huge concern, and here’s what his company does to combat these threats:
“We also conduct internal phishing simulations to educate our team on the latest phishing techniques. Anyone who falls for a simulated phish must take additional security training. This approach hardens our security culture and reduces risk.
To avoid malware, we have a strict policy against opening unsolicited email attachments. We recommend customers enable MFA, use unique passwords, and be wary of malicious phishing attempts and attachments to strengthen their security posture. Staying vigilant and keeping up with evolving threats is key to robust email security.”
We couldn’t agree more, considering that SlashNext’s 2024 Mid-Year Assessment shows a 341% surge in all kinds of malicious email threats in the first six months of 2024 on top of the shocking 856% increase already observed the year before.
3. Deploy Modern and Foolproof Authentication Technology
Are you still using the classic internet message access protocol (IMAP), the post office protocol (POP3), or the simple mail transfer protocol (SMTP) username and password authentication?
If so, beware. IMAP is often used for password spraying attacks. That’s the same technique used in January 2024 by Russian hackers to access Microsoft’s corporate accounts and steal sensitive information.
To avoid these issues, Simon Lee, CEO of Glance and tech expert, suggests the following:
“[…] block legacy protocols like IMAP, POP3, and SMTP unless necessary. These older protocols often don’t support modern authentication methods like OAuth, leaving a backdoor open for cybercriminals. By turning off these outdated services and requiring more secure methods like Exchange ActiveSync or using OAuth 2.0 for authentication, you drastically reduce the attack surface for email accounts.”
Proactivity is critical to cybersecurity. You want to mitigate threats, not just fix them once they’ve already happened. This is reflected in Lee’s next insights:
“Many companies set up SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) but don’t go the extra step of configuring DMARC (Domain-based Message Authentication, Reporting, and Conformance). DMARC adds a layer by specifying how email receivers should handle unauthorized emails. It’s a critical practice to protect your domain from being used in phishing attacks or spoofing attempts. The key is to gradually move from ‘none’ to ‘quarantine’ and eventually to ‘reject’ for complete protection while using the reports to fine-tune the policy.”
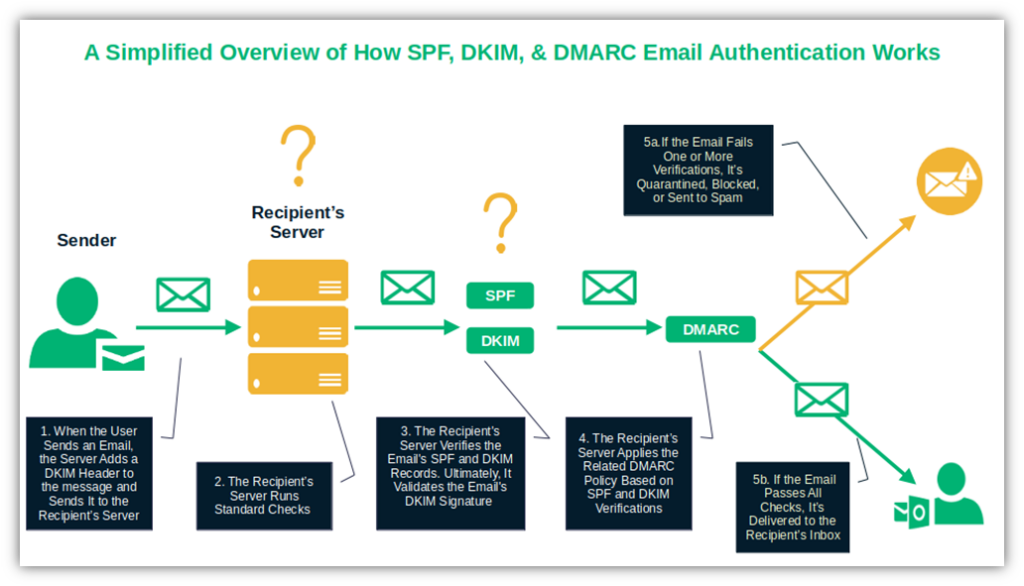
Vlad Cristescu, Head of Cybersecurity at ZeroBounce, takes this a step further. He recommends combining SPF, DKIM, and DMARC with secure email gateways that scan your inbound email traffic:
” SPF (Sender Policy Framework) makes sure the email is coming from where it says it is, while DKIM (DomainKeys Identified Mail) adds a secret signature to ensure your email isn’t tampered with on its journey. And then there’s DMARC, which ensures that no one messes with your domain. Together, they work to protect you from sneaky impersonators.”
But why are SEGs so important? Cristescu says:
“Secure email gateways (SEGs) are your inbox’s first line of defense. They scan every email to catch malware, phishing links, and other sketchy content before it even touches your inbox. Pair them with SPF, DKIM, and DMARC, and you’ve got a higher chance to keep out the bad guys.”
4. Keep an Eye Out for Email Client-Based Shadow IT Threats
75% of professionals interviewed by Kolide use their own devices to do their work. That’s a shadow IT issue, if the devices are not authorized. Shadow IT encompasses all those systems, hardware, and software utilized by your employees or end users, without being officially approved by your IT department.
For instance, when a colleague uses their personal smartphone to check work emails, or ChatGPT to write some code or text without the IT department’s knowledge, they’re using shadow IT. This puts your organization at risk.
This is why Lee suggests using shadow IT monitoring for email clients:
“Shadow IT, especially unauthorized email clients or apps, is a growing problem. Many employees unknowingly use unsecured apps to check company emails. Implementing shadow IT monitoring tools can help detect and block unauthorized email clients, ensuring that all devices accessing corporate email are secure and compliant with your policies.”
Spot on. Data from JumpCloud’s Q3 2024 SME IT Trends Report reveals that the second most common cyber attack source was none other than shadow IT.
5. Make the Most of Your SSL/TLS Certificate Features
A secure socket layer/transport layer security (SSL/TLS) certificate is a small data file (i.e., digital certificate) that packs a lot of security punch for your email server. It lets you authenticate your website/mail server’s identity and establish a secure, encrypted connection between the server and the client (e.g., email client).
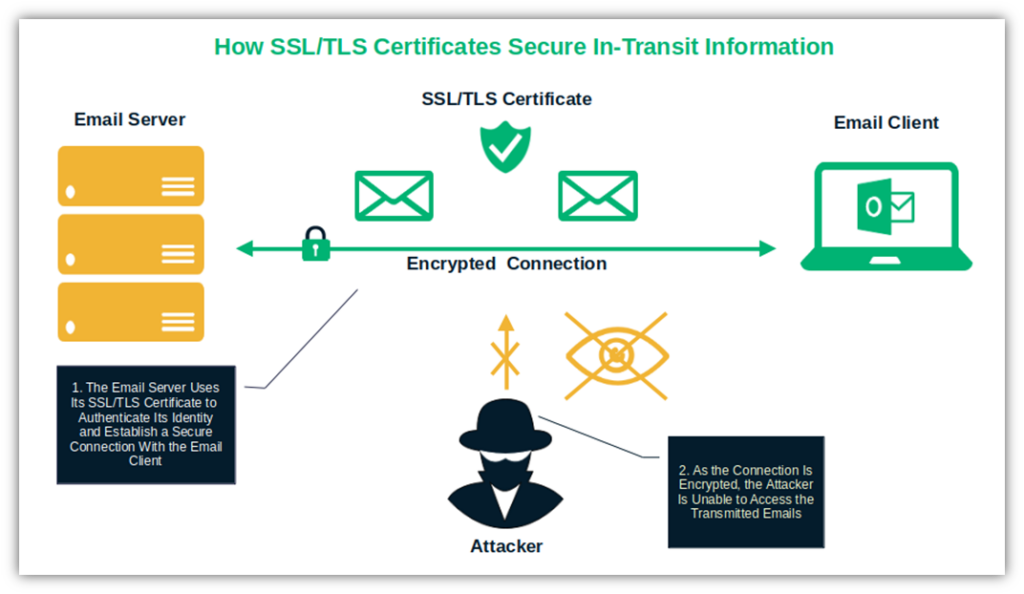
In the case of the email content itself, an email signing certificate helps senders assert their identity and confirm the authenticity of the messages and documents exchanged. It also allows them to send encrypted messages to other email signing certificate users. But, for cybersecurity experts like Uwe Weißbach, an SSL/TLS certificate plays an essential role in email security that can’t be overlooked.
And rightly so. Weißbach is the founder of Tortuga Webspace Security GmbH and an IT security consultant. He specializes in web server security and email security standards and works as a cyber security trainer at several educational institutes. Here’s what he suggests:
“While SPF, DKIM, and DMARC are important, another best practice worth mentioning, is implementing strict TLS encryption policies for email transmissions. By incorporating TLS reporting (TLS-RPT), companies can gain an overview of failed secure connections and thus also identify vulnerabilities early on. In my opinion, this is a good approach to be even better positioned as an email sender.”
Once again, as the adage says, “An ounce of prevention is worth a pound of cure.
6. If You Can’t Do Without Macros, Implement Additional Protections
… And then there are good ol’ macros. Yup. Even if Microsoft blocked them by default since 2022, they’re still alive and kicking. On one hand, organizations still utilize these user-friendly commands to increase productivity by automating repetitive tasks in Excel and other Microsoft Office desktop applications. On the other hand, cybercriminals keep on exploiting them even today to spread malware embedded into legitimate-looking Microsoft Office files sent as attachments in phishing emails.
So, if you really can’t do without macros, learn to digitally sign your macros with a code signing certificate to prevent bad guys from tampering with them. After that, take the advice of freelance security engineer Michael Lazin:
“[…] If you need to have macros on […] allow only digitally signed macros. While it is not a perfect solution because there are other scripting languages on Windows, it is advisable to set PowerShell to allow only signed scripts as well as PowerShell is often used to spread malware on the inside.”
7. Keep Your Old Emails in a Secure Vault
We get it. Deleting old emails to protect your organization and/or data from breaches isn’t a solution. Businesses like yours might be required to store email records due to regulatory compliance (e.g., the European Union’s General Data Protection Regulation [GDPR]). Additionally, you might want to save key emails as backups or keep them for forensic investigation in case of a cyber security incident.
However, using your email client as a document repository isn’t good, either, as it can easily lead to costly data breaches. Steve Tcherchian, experienced this issue first-hand. In addition to serving as CISO and Chief Product Officer at XYPRO, Tcherchian is also on the ISSA’s CISO Advisory Board, the NonStop Under 40 executive board, is part of the ANSI X9 Security Standards Committee, and is a regular contributor to and presenter at the EC-Council.
Here, is what he shared with us — it’s lengthy but well worth the read:
“I’ve personally seen people keep emails for longer than needed due to various reasons. Convenience and habit mostly, as many find it easier to retain all emails to search for past communications, documents, or information without the hassle of deciding what to delete. There’s also a fear of losing important information, whether personal, legal, or professional, leading them to keep emails ‘just in case.’ Also, emails are often kept as a backup or for record-keeping purposes, especially when they contain vital information or agreements. It’s saved our bacon many times.
Industries, such as legal, financial services, healthcare, government, corporate, and education, are more prone to keeping emails longer due to regulatory and compliance requirements. Legal professionals need thorough documentation and record-keeping for cases and compliance. The financial services industry follows regulations like the Sarbanes-Oxley Act, while healthcare must comply with HIPAA mandates. Government agencies and public sector organizations must maintain transparency and accountability by keeping emails. Corporate businesses preserve emails for records of transactions and communications.
The balance becomes when emails are kept for extended periods, they become part of the organization’s records and can be accessed and scrutinized during legal investigations or even exposed during a data breach. Even if the emails are not directly related to the ongoing legal matter, they might still be subject to discovery if they are deemed to contain potentially relevant information – increasing legal risk, privacy breaches or competitive disadvantages.”
So, what alternatives does Tcherchian recommend?
- Implement an automated and secure email retention policy that ensures both compliance with regulations and accessibility.
- Opt for a secure email archiving solution.
- Delete unnecessary emails.
Why is all of this necessary?Tcherchian summarizes it best:
“In short, these steps will ensure you don’t have confidential emails lingering around in your inbox ready to be exposed to a data breach or taking [up] space. An email archiving solution will move old emails out of your inbox and into a secure vault where they can be sorted, locked up securely and help you follow policies.”
So, are you ready to spring clean your emails and implement these effective email security tips? Great. But our experts still have more email security best practices to share….
8. Invest in Multi-Layered Protection and Encryption
Relying on one-dimensional email security protections is no longer enough to protect your business, data, and customers from advanced cyber threats. 37% of cyber security professionals interviewed by Mimecast reported that Microsoft 365’s security protections failed to stop malware attacks. In 33% of cases, the same tools didn’t identify spam or phishing emails.
Not even cutting-edge solutions, such as passwordless logins, are entirely foolproof when used alone. This is why many IT and cybersecurity experts are calling for multi-layered defenses — think email server and message encryption, sender authentication, email scanning, etc.
This approach covers a broader spectrum of threat vectors to protect emails in transit and at rest (i.e., in your inbox or saved on a secure vault).
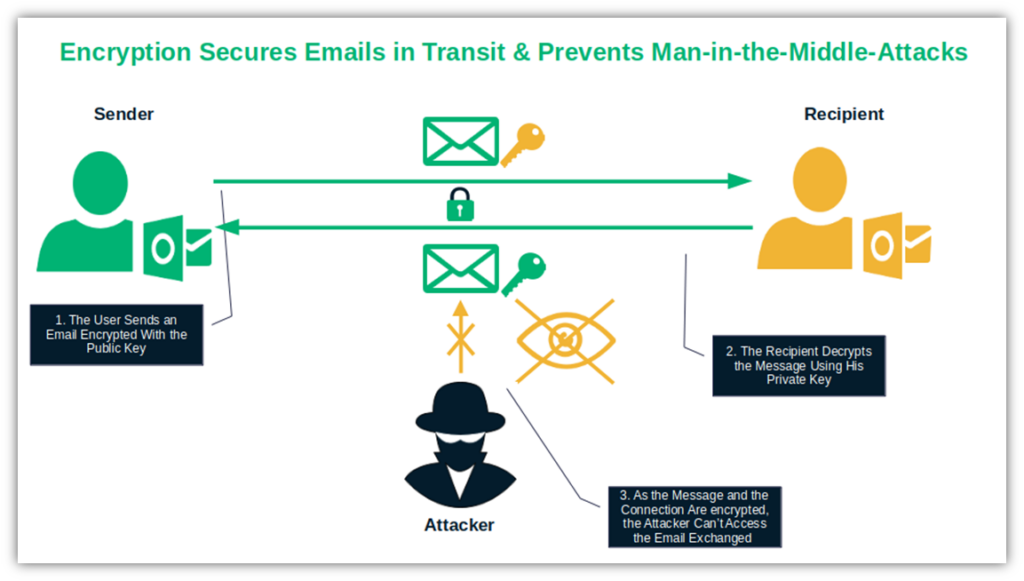
“[…] one of the most critical elements in email security is multi-layered protection. It is no longer good to have simply basic spam filters or antivirus.
Other vital advice is that encryption should be regularly used coherently, both for emails at rest and in-transit. Encryption of email means that, in case an attacker intercepts your email, it will not be able to read its content without the proper key.”
The best of it? You can enable email encryption through two means:
- Using an SSL/TLS certificate on your email server, and
- Digitally signing and encrypting your messages using an email signing certificate.
Rafay Baloch, cyber security expert, white-hat hacker, and CEO and Founder of REDSECLABS, echoes these sentiments and emphasizes the importance of two-factor authentication (2FA):
“Make sure to activate two factor authentication (2FA) at all times. It serves as a security barrier that can significantly hinder hackers’ attempts to infiltrate your system. Stay vigilant against phishing attacks — cybercriminals have become adept at creating looking emails[,] so it’s crucial to verify sender details and steer clear of any links.”
Baloch also recommends:
- Encrypting your emails to protect them from snooping and tampering,
- Keeping your software up to date to shield it from attacks, and
- Safeguarding your accounts with strong passwords stored in a password manager.
At the end of the day, Cristescu says:
“Email might be your preferred communication channel, but it’s also cybercriminals’ favorite playground, with phishing, spoofing, and ransomware making regular appearances. To keep your emails safe, you need a multi-layered defense.”
9. Be Proactive and Have a Zero Trust Approach With All Emails
Georgiev says that effective email security requires a proactive mindset. Simply put, it’s time to get out of reaction mode and start working on prevention.
Baloch reinforces that stance with a real-life example:
“Ensuring the security of emails has become increasingly crucial due to the changing strategies employed by cybercriminals nowadays. This year[,] in 2024[,] witnessed a zero day exploit aimed at email platforms. The perpetrators exploited vulnerabilities in used email applications to infiltrate systems without authorization. This breach is one example among many that have managed to circumvent security protocols[,] hence highlighting the importance of being proactive in safeguarding against such threats.”
Raju Vegesna, Chief Evangelist at Zoho Corporation, says that implementing an email zero trust policy can be a good place to start:
“[…] Implementing the principles of Zero Trust security strategies is also important, especially as threats continue to evolve. A “Trust No Email” approach and strict verification processes can greatly reduce the risk of breaches. It is important organizations reassess their email security frameworks regularly and use highly secured mail platforms that offer security features to protect data and accounts, including code analyzer tools and scanners to manage vulnerabilities.”
Zero trust is also one of the email security best practices echoed by Georgiev:.
“[…] One of the best practices I always recommend is implementing a zero-trust approach to all incoming emails. It’s best to assume that every email is a potential threat until it’s been verified. This way, you’re less likely to inadvertently trust malicious content.”
Are you looking for more ways to proactively boost your email security? Implement continuous threat exposure management (CTEM). It works for SMBs too.
10. Educate Your Peers
It’s no secret that businesses and consumers still love communicating via email. Radicati estimates that the total number of emails sent per day, in 2024 should reach over 376 billion by the end of 2025. But with 17.8 million phishing emails detected by Darktrace in the first half of 2024, and 62% of those passing DMARC checks, it makes sense why Cristescu emphasizes the importance of security awareness training. It’s all about helping employees recognize email-based threats:
“[…] even the best tech can’t save the day if your team isn’t in on the[ir] game. People are still the weakest link, so regular, engaging (and maybe even fun) security training is key. Teach your employees to spot those sneaky phishing emails, and you’ll cut your risk dramatically. When it comes to email security, a well-trained workforce is just as important as the tech tools you use.”
Kalvo is on the same page, emphasizing that training should be provided on a continuous basis:
“Phishing remains one of the most widespread vectors of attack, and regular training helps staff recognize and avoid these threats, significantly reducing the risk of human error compromising the security of your network.”
But how do you make training engaging? Georgiev suggests integrating simulations and awareness campaigns: “Training employees to recognize phishing attempts is also really important. Regular simulations and awareness campaigns can significantly reduce the likelihood of falling victim to sophisticated phishing attacks.”
As part of their training, Vegesna encourages businesses to teach users how to identify malicious email attachments and email headers:
“Email hacking and fraud are often caused by vulnerabilities in email attachments and email headers. To combat this, organizations should focus on identifying and understanding the different types of email threats through targeted training and awareness campaigns.”
Yes, employee training is a big issue. Let’s not forget that Verizon’s 2024 Data Breach Investigations Report (DBIR) revealed that 68% of breaches are caused by human-related factors such as employee negligence and mistakes. Add to this the popularity of remote working and you get a ticking bomb ready to explode.
You still don’t think it’s a big deal? Let’s look at the data. More than one in five respondents to the 2023 Lookout Global State of Mobile Phishing survey admitted that if they were the victim of a phishing attack while working from home on a Friday, they would continue working as if nothing happened. One in 10 (9%) said they’d report the incident only after the weekend, by which time a lot of damage can be done.
Follow our experts’ advice and create a robust cyber security training plan (as described in our free SMB cyber security plan template). This approach is also suggested in the recently updated NIST Cyber Security Framework (CSF) 2.0.
Let’s Meet the Experts
Before wrapping up this list of email security best practices and tips, we would like to thank one by one, the 10 email security “Jedi Masters” who agreed to share their wise words with us. Here, they’re listed in alphabetical order by last name:
- Rafay Baloch — Cyber security expert, white-hat hacker, and CEO and Founder of REDSECLABS.
- Vlad Cristescu — Cyber security expert and Head of Cybersecurity at ZeroBounce.
- Deyan Georgiev — Cybersecurity expert at RapidSeedbox.
- Jacob Kalvo — Tech and cyber security expert and co-founder & CEO at Live Proxies.
- Michael Lazin — Freelance security engineer.
- Simon Lee — CEO of Glance and tech guru with over 20 years of experience in the IT industry.
- Brian Pontarelli — CEO of FusionAuth and an engineer at heart.
- Steve Tcherchian — CISO and Chief Product Officer at XYPRO.
- Raju Vegesna — Chief Evangelist at Zoho Corporation.
- Uwe Weißbach — Founder of Tortuga Webspace Security GmbH and IT security consultant.
Final Thoughts About Email Security Best Practices & Tips
Nowadays, the email threat environment is evolving fast. It’s time to start assuming that every message and attachment can be potentially malicious. Put to good use what you’ve just learned and adopt advanced email security measures. Implementing these email security best practices and tips will elevate your email security posture and help you prevent most threats from reaching your users’ and customers’ inboxes.





















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security