What Is Asymmetric Encryption & How Does It Work?
Your ultimate guide to understanding asymmetric encryption — what it does, how it works, and its strengths and disadvantages
What is asymmetric encryption? How does asymmetric encryption work? These two questions are becoming common as the world is getting more digitized and paperless. But when everything is stored on computers, data privacy becomes a big concern. Hackers can steal stored data from your devices, emails, cloud platforms, and USB drive, or when you transfer it from one place to another via the internet.
One of the best ways to protect the data is to encrypt it. And this is where asymmetric key encryption — or what’s also known as public key encryption — comes into play. In this article, we’ll cover what asymmetric key encryption is and answer your question “how does asymmetric encryption work?” in layman’s terms. Later on, we will also take a look at the strengths and weaknesses of this type of encryption.
What Is Encryption?
Before we can answer the question “what is asymmetric encryption?” we first need to quickly cover what encryption is in general.
In the most basic sense, encryption means using “fancy math” and a set of instructions (algorithms) to disguise and protect data. These algorithms scramble plaintext data into an incomprehensible text known as ciphertext, which looks like gibberish without the use of a special key that decrypts it. This means once the data is encrypted using a cryptographic algorithm, you can’t interpret it or guess the original content of the data from the ciphertext. So, your data stays secure from unintended, prying eyes.
Let’s consider the following example to see how encryption works in a general sense:

In this example, you can see how the data changes from plaintext to ciphertext and back to plaintext through the use of encryption algorithms and decryption keys. The keys can either be identical (symmetric) or unique (asymmetric).
When we talk about encryption, it’s much like a lock on a door. To operate the lock, you need a key. This means only people who hold the key can unlock the door and gain access to whatever it’s protecting. In the digital world, a key can come in many forms — a password, code, PIN, or a complex string of computer-generated characters.
An Overview of the Two Types of Encryption
There are two main types of encryption:
1) Symmetric encryption: This type of encryption is reciprocal, meaning that the same key is used to encrypt and decrypt data. This is great for large batches of data but has issues in terms of key distribution and management.
2) Asymmetric encryption: This type of encryption uses two separate keys for encryption and decryption — a public key and a private key. We’ll cover asymmetric key encryption in more detail momentarily.
For the purpose of this article, we’re going to focus solely on asymmetric encryption. Be sure to check back over the coming weeks for another article that will focus on symmetric encryption. We do, however, have an article already that will help you differentiate asymmetric encryption vs symmetric encryption in the meantime.
Now, let’s talk about what you’re really here for…
What Is Asymmetric Encryption? A Definition and Explanation
Asymmetric encryption is a type of encryption that uses two separates yet mathematically related keys to encrypt and decrypt data. The public key encrypts data while its corresponding private key decrypts it. This is why it’s also known as public key encryption, public key cryptography, and asymmetric key encryption.
The public key is open to everyone. Anyone can access it and encrypt data with it. However, once encrypted, that data can only be unlocked by using the corresponding private key. As you can imagine, the private key must be kept secret to keep it from becoming compromised. So, only the authorized person, server, machine, or instrument has access to the private key.
What Does Asymmetric Encryption Do?
Asymmetric encryption is a way for you to verify third parties that you’ve never met via public channels that are insecure. Unlike traditional (symmetric) encryption methods, which rely on one key to encrypt and decrypt data, asymmetric key encryption uses two separate keys to perform these functions.
This is why public key encryption is considered a critical element in the foundation of internet security. Public key infrastructure (PKI), a framework of policies, processes and technologies that make secure third-party communications over the internet possible. To do this, it relies on both asymmetric and symmetric encryption.
Asymmetric encryption methods are what you use to:
- Authenticate parties,
- Verify data integrity, and
- Exchange symmetric keys.
Symmetric encryption is what you use to handle the bulk of data encryption.
What you may not realize is that you’re actually using public key encryption right now! Do you see the security padlock icon in your browser or the HTTPS in the website URL? Both of those things indicate you’ve connected to a website that uses SSL/TLS certificates and the secure TLS protocol. What this does is use asymmetric key encryption to verify the identity of the server and to create symmetric session keys. (Once this is done, your browser and the web server switch to using symmetric encryption for the rest of the session.)
So, as you can see, asymmetric encryption is complementary to symmetric encryption and is what makes it possible to use over the internet.
Four Main Characteristics of Asymmetric Encryption
1. Asymmetric Encryption Is Designed for Securing Data & Key Exchanges in Public Channels
In a nutshell, the purpose of asymmetric key encryption is to serve as a way to securely encrypt data in public channels while also offering authentication and data integrity. Because it doesn’t require the exchange of keys, there isn’t a key distribution issue that you’d otherwise have with symmetric encryption.
2. Asymmetric Encryption Keys Are Large
Asymmetric public and private keys are unique and large strings of random numbers. For example, there are millions of websites using SSL/TLS certificates, and yet, each website has a different set of public and private keys. For keys to be strong and secure, however, they must be generated with high entropy (randomness). Each key has to be random and unpredictable enough that it would take modern supercomputers thousands of years to guess.
Let’s consider the following examples of asymmetric public and private keys:
-----BEGIN PUBLIC KEY-----
MIIBITANBgkqhkiG9w0BAQEFAAOCAQ4AMIIBCQKCAQBukNqMp3/zrntpyRhCwYxe
9IU3yS+SJskcIyNDs0pEXjWlctfSNEwmeEKG3944dsBTNdkb6GSF6EoaUe5CGXFA
y/eTmFjjx/qRoiOqPMUmMwHu0SZX6YsMQGM9dfuFBaNQwd6XyWufscOOnKPF5EkD
5rLiSNEqQEnoUvJb1LHiv/E36vi6cNc5uCImZ4vgNIHwtKfkn1Y+tv/EMZ1dZyXw
NN7577WdzH6ng4DMf5JWzUfkFIHqA2fcSGaWTXdoQFt6DnbqaO5c2kXFju5R50Vq
wl+7S46L4TYFcMNDeGW6iAFds+SMADG486X/CRBTtF4x59NU3vNoGhplLRLtyC4N
AgMBAAE=
-----END PUBLIC KEY----------BEGIN RSA PRIVATE KEY-----
MIIEoQIBAAKCAQBukNqMp3/zrntpyRhCwYxe9IU3yS+SJskcIyNDs0pEXjWlctfS
NEwmeEKG3944dsBTNdkb6GSF6EoaUe5CGXFAy/eTmFjjx/qRoiOqPMUmMwHu0SZX
6YsMQGM9dfuFBaNQwd6XyWufscOOnKPF5EkD5rLiSNEqQEnoUvJb1LHiv/E36vi6
cNc5uCImZ4vgNIHwtKfkn1Y+tv/EMZ1dZyXwNN7577WdzH6ng4DMf5JWzUfkFIHq
A2fcSGaWTXdoQFt6DnbqaO5c2kXFju5R50Vqwl+7S46L4TYFcMNDeGW6iAFds+SM
ADG486X/CRBTtF4x59NU3vNoGhplLRLtyC4NAgMBAAECggEALFprcZUX3PcXht4m
n1DpMIZCkphgPu7UKjdmRBg+KKLqPk6NiUN1cNE5TsWrbVcl27t0Np/JA3alk11e
iKGQLwAjds/ciLOGLrmuOPJb2/EGS3kXOpjzMJz7soILvdb/Jrw+wQEJ7WvwGNt5
Tz8+kxQOmnu/fIWBoHL1yiTOnzj8rOrJfGjwCWe4skeiTNVXoJ3oTyUp8vLlkeBb
YVOKaHtRVzE4qre6Jy0LelIu8OScpVBz6U9RW8p84eRuH28k6VVAMVd7ruSH0gLu
vcXjXnt6eLRka3Ww4KwA9ATD0oT0270FqebKmorvBv+DmWEjTTkSMfJz2wYN5Dcj
6lg1+QKBgQC6KDBR31573gU9SiilNFGaKL0qB1NbLnj2TL+964LB/bv+25AUKdcH
jJaE41kZWmxonLbxJI4ACTZd/9vXpAPOe1Wwp3r3kEyQsyARYFD7Pdai0DhsS9Mj
Y/hSL0i1cxE6EXY60cXzW4rrI1r7Nd6VCUlGpsOLVfaFR3xByA9JgwKBgQCYDF16
ornljNE8NMG6ojrtpL2pPqNuw4qMrqNOzne90w/ALK6pdTOQFToyRZoQfdVqY9jK
u0LceC6E37w7pX4UwE1zrmprWpBUWnvJhSnDcXcDtVqipqERQ5KPu3/eeyStd5L4
PfPbEWID4+6i9uC0ZQwBU3G41tGaWiaZ3NNlLwKBgEjgIspqX1qud+6ecXr7GFb5
S9SAOamgb8o8EXQQFohLBKWo3qaGGp/h8arkNaUvOPFbKGMOpGhvMtFpsG6izrqu
ncUiS4lO/CpJdWxYAFvawYPLb8s1g9p+8F98E0K1YTESVO6B4LR8Sc3zcVKWrCQ8
FmuKLVMGvBNBAOvfndxxAoGAWebFxuM8g2vVs4GGIrIVobnMoqt0uuNHopMH4GrY
Bhcrsvc4dt3jlQfYFy1sQOAGNhe/cW9zwyQUbWBUzfe2KtLheMriBYPQ3u95Tdg8
r2EBe+HZK17W0XxgxjeZDZVGRIL1FW6cJyWKDL7StOzARCmTBZ2vGhl6aYdwV31o
SOUCgYAwKJgVwTlhelBVl07w8BkqKjG+snnHMV3F36qmQ4+GCBBGaeNLU6ceBTvx
Cg3wZUiQJnDwpB3LCs47gLO2uXjKh7V452hACGIudYNa8Q/hHoHWeRE6mi7Y0QZp
zUKrZqp9pi/oZviMqDX88W06B12C8qFiUltFmhfPLJ9NJ3+ftg==
-----END RSA PRIVATE KEY-----3. Public Key Encryption Algorithms Are Strong
The popular algorithms for asymmetric encryption and key exchanges are Diffie-Hellman, RSA, ECDSA, ElGamal, and DSA. Although it is not a strict rule, most of the time,asymmetric encryption uses long keys that are 1024 bits, 2048 bits, or more. In general, the longer the key size, more secure the encryption.
For example, if the keys are generated with 2048-bit encryption, there are 22048 possible combinations. It would take modern supercomputers thousands of years to go through so many combinations find the corresponding private key of a public key. In short, you can’t guess the private key from the public key, especially when keys are long.
4. Asymmetric Encryption Is a Resource-Hogging Process
Those massive keys are resource-intensive and that means encryption takes longer to accomplish. In other words, because the key sizes are larger and two separate keys are involved, the encryption and decryption process become slower.
As such, asymmetric encryption is most suitable for encrypting small chunks of data due to its latency and processing requirements. If you use it for large blocks of data, it will give more burden to your servers. Sometimes, it’s used to initially establish secure communication channels, which can they be used to facilitate symmetric encryption to exchange data.
How Does Asymmetric Encryption Work? Let’s Explore This Concept with An Example
Before moving on, let’s better understand asymmetric encryption with a hypothetical example.
Imagine you want to protect a precious jewelry box that you’re sending in the mail to your significant other. To keep it secure in transit, you use a special lock that needs two number combinations. One number can lock the box (the number which you have) and the other number combination can unlock it (which your recipient has).
First, you put the items you wish to protect inside the box. Then you lock the box with a specific number combination before placing it in the mail. Once it arrives, your significant other uses her number combination to unlock the box and access its contents. Because she never shares that number with anyone and keeps it to herself, it means that no one else can use it.
Now, let’s apply this concept to understanding how asymmetric encryption works within the realm of public key infrastructure.
All the data you send via the internet is in plaintext. This means that anyone who gets access to it can read and interpret it. Now, of course, you can encrypt the data using a private key. Once the data has been converted into ciphertext, you can’t decrypt it using the same key. The ciphertext can be decrypted only with the corresponding private key. In general, the sender must have access to the public key, and the recipient must have its corresponding private key.

How Public Key Encryption Helps You Protect Your Business & Data
Let’s take an example of how asymmetric key encryption works in real life.
Digital Signatures Ensure Data Integrity
A digital signature is a mathematical algorithm that’s useful for ensuring the authenticity or integrity of documents, emails, or other types of data. What it does it make the recipient of a digitally signed document or email aware of any tampering or unauthorized modifications that may have been made. Digital signatures rely on asymmetric encryption and a cryptographic function known as hashing.
We’ll speak more to the specifics of digital signatures and hashing a little later. But for now, just know that asymmetric encryption is used for enabling digital signatures in:
SSL/TLS Certificates Secure Your Website
When a user tries to open your website on the browser (your web client), the browser initiates an SSL/TLS handshake process. This handshake helps to authenticate the server to your client via asymmetric encryption by sending its SSL/TLS certificate and public key. The browser then generates a pre-master secret, encrypts it using the server’s certificate public key, and sends it back to the server. The server then decrypts it with its corresponding private key. Together, the two parties then generate the master secret (a shared secret) and identical session keys.
The session keys are symmetric and are what the client and server use for all data exchanges for that particular session. No intruder can decrypt or guess the session key while it is in transit between the browser and the server. This helps to protect your data from being intercepted and read in man-in-the-middle attacks (also known as MitM attacks). So, the process starts out with asymmetric encryption and changes to symmetric encryption for the bulk of the data exchange.
Personal Authentication Certificates Offer Client Authentication & Email Security
A personal authentication certificate, which is also known as a client certificate, authenticates users within an organizational setup. Using these types of certificates enable you to restrict access to sensitive data or systems to only select individuals. Companies install these certs on end user devices as a means of access control and passwordless authentication. Employees can access those resources only when they log in from the office device that has the certificate.
Some resources, email clients, and websites (such as intranet sites, development and testing sites, or even the admin pages of the public-facing sites) are intended for only employees to use. And it’s always a good practice to restrict outsiders’ access to these web pages. That’s where a personal authentication certificate and asymmetric encryption come in handy.
The Advantages & Disadvantages of Asymmetric Encryption
In this section, we’ll highlight some of the pros and cons of asymmetric key encryption with comparison to symmetric encryption. But if you want a detailed comparison, please refer to this article: Difference between symmetric and asymmetric encryption.
Four Advantages of Asymmetric Encryption
1. It’s More Secure Than Symmetric Encryption
Because it involves the use of two related but distinct keys, asymmetric cryptography is more secure than its symmetric counterpart. This is, in part, because asymmetric encryption uses longer keys (1028 bits, 2048 bit, 4096 bit, etc.), whereas symmetric encryption uses shorter keys (128 bits, 256 bits, etc.)
2. It’s Useful When More Endpoints Are Involved
In symmetric encryption, only one key is shared by all endpoints. This means the onus of its success is dependent upon the secrecy of that key. When a large number of endpoints share the same key, the chances of exposure increases.
But in asymmetric encryption, the private key is stored with only the authorized recipient. When one endpoint is holding the private key instead of multiple, the chances of compromise reduces dramatically. That’s why asymmetric key encryption works best when a large number of endpoints are involved.
3. Makes Key Distribution Easy
In asymmetric encryption, you can distribute the public key to a large number of endpoints because you don’t have to worry about its security.
Whereas in the symmetric encryption, you must distribute the key very cautiously. When there are millions of servers and devices involved, the key distribution becomes very challenging in symmetric encryption, and the chances of compromise increases.
4. Makes Digital Signatures Possible
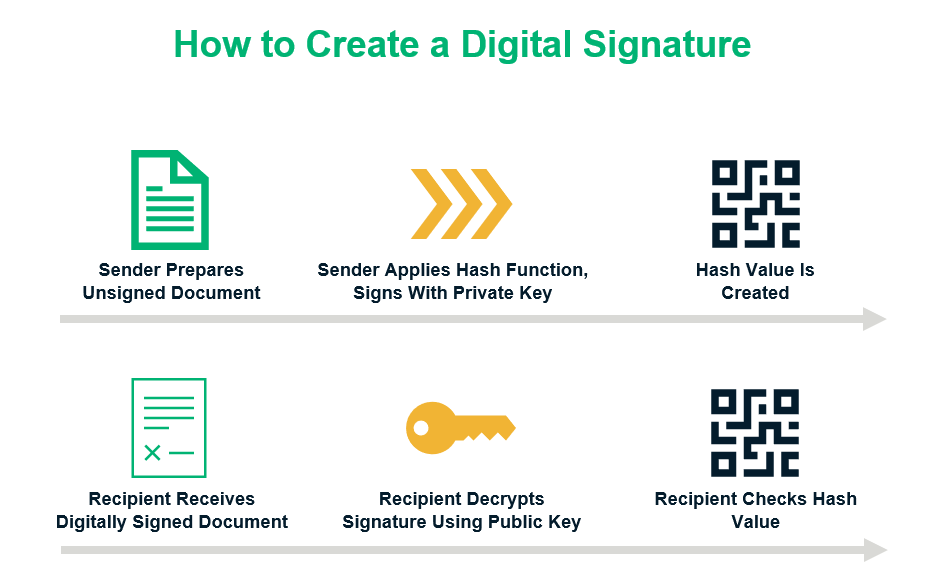
Asymmetric encryption is integral to the entire concept of digital signatures and how they work. When people talk about digitally signing a document, what they mean is that they’re actually applying a hash (a fixed-length piece of data that serves as a one-way cryptographic function) to it that serves as a check-sum. Basically, this helps the recipient know whether the document has been modified or altered since it was signed originally. Digital signatures use asymmetric key encryption to make this happen.
Here, the sender applies a hash as a check-sum and by signing that hash with their private key to encrypt it. The recipient can decrypt the digital signature and perform the same function to check the hash value using the sender’s public key.
Two Disadvantages of Asymmetric Encryption
1. Slower Speed
Because the keys are longer and the server needs to calculate two different keys for encryption and decryption, it becomes a time-consuming process. It also uses more complex algorithms. These are a couple of the reasons why asymmetric key encryption is slower than symmetric encryption.
2. It’s Too Bulky to Be Used at Scale
Because of the two separate long encryption keys, it places an immense burden on the server to go through the encryption and decryption process. You can’t use asymmetric encryption where there is a huge quantity of data involved; otherwise, the servers get exhausted and become slow.
This is why, for example, asymmetric key encryption is used initially in the SSL/TLS handshake process but then it switches over to symmetric encryption for the data exchange that will take place between a user’s browser and a website during their session.
Wrapping Up on Asymmetric Encryption
Asymmetric encryption and its algorithms aren’t perfect, but they’re still incredibly effective at helping us to establish secure communications with third parties via public channels. And that’s why some types of certificates use a hybrid approach in which they use both the types of encryption simultaneously. For example, in the SSL/TLS certificate, all the data transmission is done using symmetric encryption. But to transmit the symmetric key, asymmetric encryption is used.
In conclusion, we just want to say that asymmetric encryption is perfect for transmitting small chunks of data to a large number of endpoints. It is the main ingredient of digital signatures and way more secure than symmetric encryption.














 (77 votes, average: 4.44 out of 5)
(77 votes, average: 4.44 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security