A Brief Overview of the Metasploit Framework
Metasploit Framework is an open-source platform that’s useful for detecting vulnerabilities and creating tools that enhance an organization’s network security. Let’s look at an overview of the Metasploit Framework and what it entails
When we think of how to make software and systems more secure, something that comes to mind (aside from PKI) is a phrase by a notable American engineer and author:
“More than the act of testing, the act of designing tests is one of the best bug preventers known. The thinking that must be done to create a useful test can discover and eliminate bugs before they are coded — indeed, test-design thinking can discover and eliminate bugs at every stage in the creation of software, from conception to specification, to design, coding, and the rest.”
— Boris Beizer, Software Testing Techniques
If you’re involved with developing and maintaining the security of your organization’s software and networks, you’ll understand the importance of reliable penetration tools like Netsparker, Wireshark, and Metasploit. These tools enable you to test your software for exploitable vulnerabilities and play a vital role in the ongoing war against cybercriminals.
This article will focus on one of the most popular open source penetration testing tools — Metasploit Framework. We’ll look at some features, commands, and briefly explore how to use Metasploit Framework.
What Is the Metasploit Framework? A Look at Metasploit
Metasploit, or what’s often called the Metasploit Framework (MSF), is a powerful open source penetration testing platform that’s used by hackers and defenders alike. It’s free for anybody to use and aids in vulnerability and exploit investigations, testing, and tool creation. It’s got a multitude of libraries, modules and tools you can use to assess the security and exploitability of your organization’s networks and report on them. This way, you can find and test vulnerabilities so you can prioritize and mitigate them before bad guys can use them to their advantage.
An exploit is a code or program designed to take advantage of a vulnerability in software or a network. Developers and security experts use exploits to detect flaws or vulnerabilities in their software before its release. Networks also need to be checked for possible flaws or vulnerabilities as they can provide an open door for cybercriminals.
Security professionals and white-hat hackers carry out penetration tests (pen tests) to identify vulnerabilities in software and networks. They do this with the permission of the target organization they’re trying to penetrate, often using testing tools that provide automated vulnerability detection, making testing much easier than using manual techniques.
Metasploit Framework vs Metasploit Pro
Metasploit is a collaborative effort between the open source community and cybersecurity experts Rapid7. It’s used to carry out vulnerability analysis, security assessments, and to improve security awareness. There are two services available:
- Metasploit Framework — This is the free, basic open source version of the framework that’s available free of charge. It offers limited capabilities and no automated features. Rapid7.com lists this platform as being ideal for developers and security researchers who don’t need the same in-depth functionalities and features as security practitioners and penetration testers.
- Metasploit Pro — This commercial service provides a wider range of services and features, including network discovery, automated operations, and web app testing for the OWASP top 10 vulnerabilities. This platform is geared for pentesters and IT security teams.
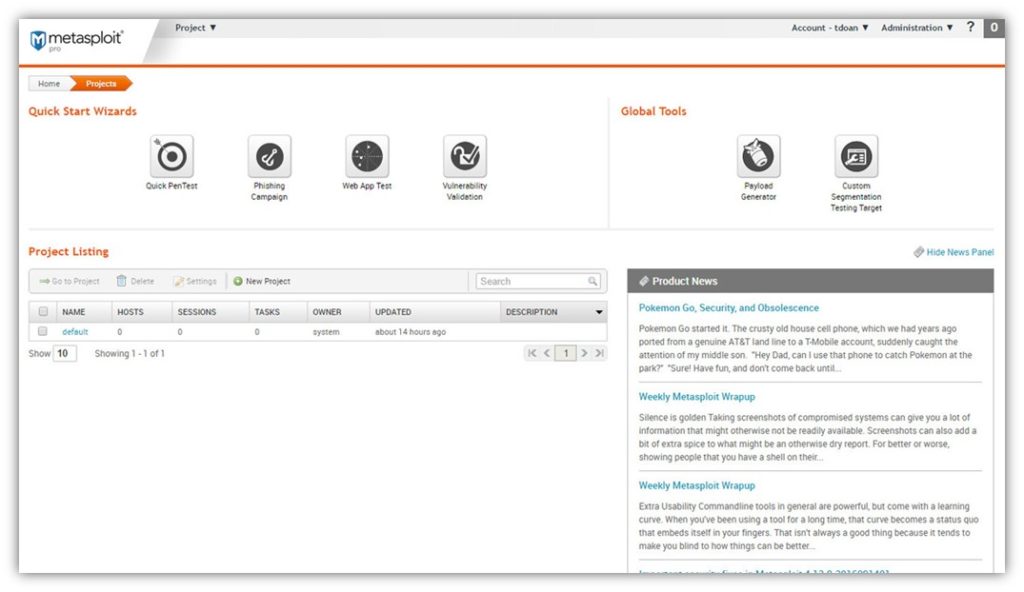
Often, when people are talking about Metasploit or Metasploit Framework, they’re typically meaning the Metasploit Pro version. It’s kind of like how people often use the terms “SSL certificate” and “TLS certificate” interchangeably — technically, they’re two separate things, but they essentially help you achieve the same thing in the end (i.e., secure your website’s data in transit).
For the sake of accuracy, we have to, at least, ensure that you understand that Metasploit Framework and Metasploit Pro are two separate products — the former is the “basic” version and the Pro version has all the bells and whistles.
Why Using a Penetration Tool Like Metasploit Framework Matters
Metasploit Framework helps programmers detect potential vulnerabilities in their program before it is used online. If a defective program is used, the bad guys would be able to break into it using the vulnerability, resulting in a network or data breach. Any glitch in the network or software can also be discovered with Metasploit penetration testing.
Once you identify these gaps in your cyber defenses, you can prioritize mitigation of these vulnerabilities before any bad guys beat you to the punch. What consequences can you face if you don’t take steps to mitigate vulnerabilities before a bad guy finds and uses them? Consider the following:
- IBM Security reported that when the initial vector of a data breach is a third-party software vulnerability, it costs an average of $4.33 million per breach. These cases constitute 14% of the total data breaches in 2021.
- If your software has an undetected vulnerability that results in a data breach, you’ll face some serious consequences that include:
- non-compliance issues, penalties & fines,
- lost relationships and revenue
- reputational harm and professional embarrassment).
No organizations are safe from cybercriminals. Even an institution like the Red Cross, which aims to work for the betterment of humanity, can fall prey to data breaches due to exploited, unpatched vulnerabilities.
What Are the Features of Metasploit Framework?
The Metasploit Framework includes hundreds of tools and modules for a wide array of penetration testing and development applications. Let’s quickly explore the basic features:
A Basic Command Line Interface
Users interact with MSF via the commandline interface. Once Metasploit Framework is installed, you can open the msfconsole to input commands and quickly access the full range of tools, libraries, modules, and document resources.
Network Data Scanning Capabilities
Metasploit Framework’s scanning tool scans the network to identify the operating systems running on it, maps them to IP addresses, and identifies the open ports and services on those systems.
The Metasploit Framework allows you to download and save the results of a network data scan. You can then compare scans from different projects or compare the data from the same project before and after patching. You can also download scan results to Metasploit Framework from other scanners, or integrate data from other scanners. Metasploit also allows you to export reports to other scanners for a detailed comparison.
Support for Manual Exploitation
Manual exploitation means choosing and configuring an exploit rather than using an automated program to do the work. With a manual exploit, you choose the appropriate exploit to target a particular vulnerability. Metasploit Framework allows you to take matters into your own hands by facilitating manual exploits.
If you want to use automation for this purpose, you’d likely have to look at the Metasploit Pro tool instead. The Metasploit Framework (free) platform doesn’t offer the automation features you’ll find in the pro version.
Manual Credential Brute Force Capabilities
In a brute force attack, a cybercriminal uses trial and error to crack passwords or other credentials. They systematically try guessing different username-password combinations until they find a match. They can then use this login information for malicious purposes, such as stealing data, transferring money, or committing identity theft.
Brute force attacks are extremely common, so it’s crucial to conduct penetration testing of your network, web apps, and other resources to determine whether they’re vulnerable to this technique. Metasploit Framework has a tool to test your network against brute force attacks, helping you to analyze security risks and form policies to prevent them.
What Modules Does MSF Include?
MSF has a huge number of tools and modules to help you carry out tests on your software and networks. Rapid7’s website lists the five overarching module categories (listed in alphabetical order) as the following:
- Auxiliary — These modules provide a slew of tools (scanners, “fuzzers,” etc.) that you can use for detecting specific information about vulnerabilities and active services. Basically, they do many arbitrary actions that aren’t exploits in and of themselves.
- Exploit — This group of modules should speak for itself. They’re all about exploiting vulnerabilities and executing payloads.
- Post-Exploitation — These modules help you take your exploit tactics a step further to gain additional intel and insights about the exploited system.
- NOP — NOP generator modules are for facilitating benign instructions that help you bypass security detection systems.
- Payload — This set of modules enables you to execute commands (carry out specific actions) during the exploitation process. These are the often-malicious codes you always have to be on the lookout for.
An Example of Running a Scan Using Metasploit Framework
So, what does it look like when you decide to put one of Metasploit Framework’s scanning tools to the test? I asked a colleague to help me demonstrate how Metasploit Framework works using a couple of auxiliary scanning tools. In this case, she’ll check to see whether a test website has expired SSL/TLS certificates installed on it:
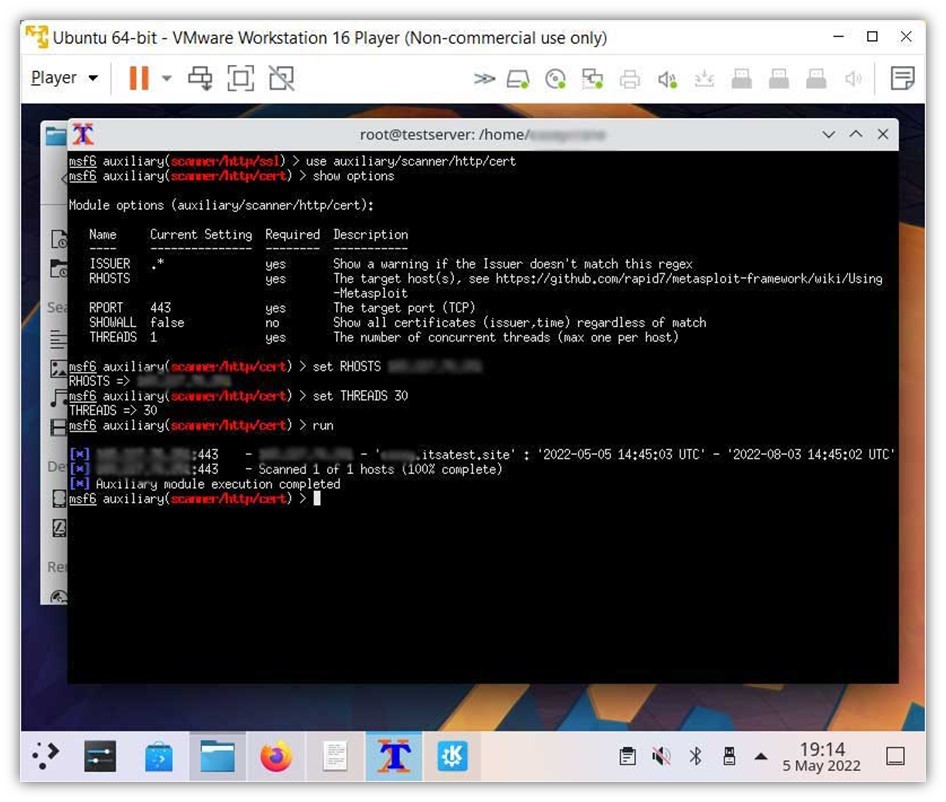
In the screenshot above, she used commands to display information relating to the target website’s SSL/TSL certificate (what site the certificate was issued to, when it was issued and when it will expire). The commands she used to display this information are as follows:
use auxiliary/scanner/http/cert
show options
set RHOSTS [target IP address]
set THREADs 30
runTaking things a step further, she queries to see whether any additional SSL/TLS certificate information is available using the use auxiliary/scanner/http/ssl module:
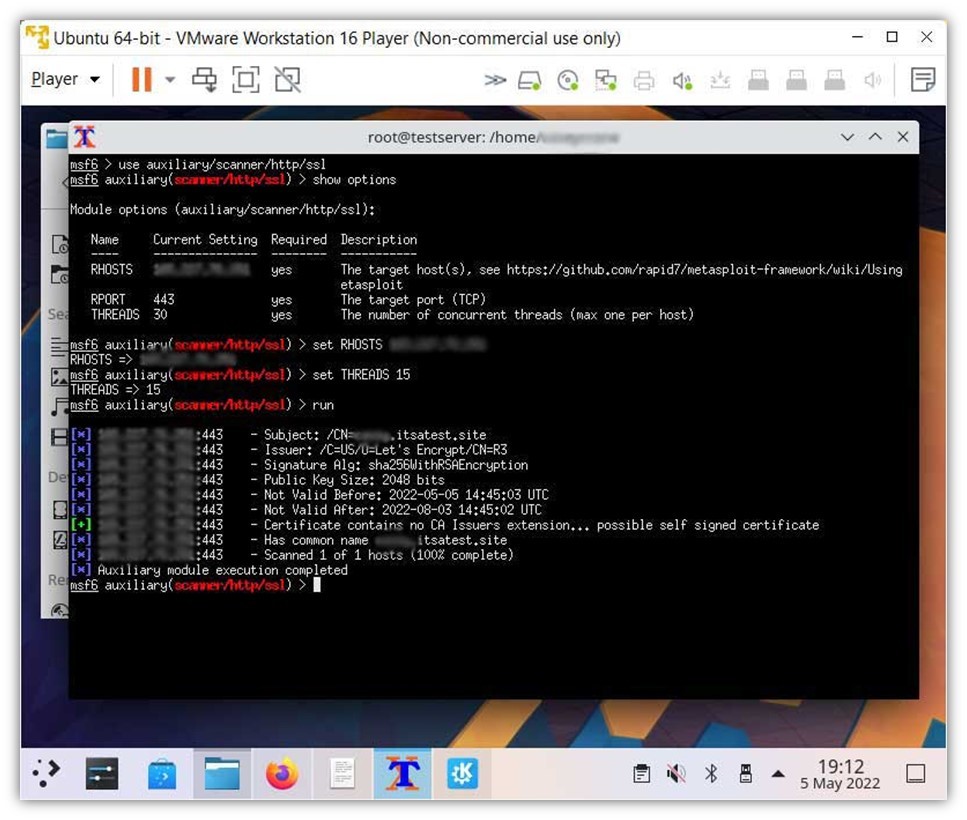
In this case, msfconsole displays information relating to:
- What domain the certificate is issued to
- What CA issued the certificate
- Which algorithms were used to create the digital signature
- What size public key the certificate uses
- The certificate’s issuance and expiration dates
- Whether the certificate is publicly trusted (in this case, it’s likely a self-signed certificate)
What Systems Support Metasploit Framework
Because the Metasploit framework is open source, it works with many of the leading browsers and operating systems:
Browsers
- Google Chrome (latest)
- Microsoft Edge (latest)
- Mozilla Firefox (latest)
Operating Systems
- Microsoft Windows (7 SP1+, 8.1, and 10)
- Microsoft Windows Server (2008 R2, 2012 R2, 2016, and 2019)
- Red Hat Enterprise Linux Server (5.10, 6.5, 7.1 and 8 or later)
- Ubuntu Linux (14.04 LTS, 16.04 LTS, and 18.04 LTS)
A Brief History of the Metasploit Framework
Metasploit began as a collection of exploits and tools and was initially written in Perl with some components in C, assembler, and Python. It had open source and commercial purpose licenses under GPLv2 and Perl Artistic.
Today, MSF is completely written in Ruby and supports a wide variety of application programming interfaces (APIs). It now has its own license, which aims to:
- Allow Metasploit Framework to remain open source
- Allow modules and plugin developers to choose their own licensing terms
- Prevent MSF from being bundled or sold commercially by third parties
- Make third-party patches available to everybody
- Provide legal support to the contributors
Final Thoughts on Metasploit Framework
Pentesting tools like Metasploit Framework help organizations detect any vulnerabilities present in the software or network. This, in turn, reduces the chances of cyber attacks considerably. Just like we test if the cake is cooked properly by inserting a toothpick inside, programmers test their codes by throwing known exploits at it. If the exploit works, the vulnerabilities will be exposed. Then, they can patch these vulnerabilities before releasing their software to the world.
Needless to say, penetration testing is an important (but often overlooked) step in protecting the network security of any organization.




















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security