Demystifying PKI Technology: An Essential Guide for IT Security Professionals
Learn everything you need to know about PKI technology in IT security that enables organizations to establish trust in a digital world where the physical verification of identities is impossible
When you open a website, make an online payment, or binge your favorite series on Netflix, PKI technology is the hidden force that makes these connections secure. Public key infrastructure (PKI) is the unsung hero that makes it possible to authenticate devices and individuals and protect the integrity of data online from unauthorized modifications. It’s behind every secure connection, communication, and code.
But what is PKI technology, exactly? And what’s going on in the background of PKI technology that makes it magic? In this ultimate guide, you’ll find everything you should know about PKI technology but are too afraid to ask.
Editor’s Note: This article is the first in a three-part series that dives into the details of PKI technology. This series explores the roles of PKI technology in IT security, provides examples of PKI uses and applications that small and mid-size businesses can enjoy, and looks at how PKI technology works.
Don't make the same mistakes
Yahoo, Equifax, Home Depot,
LinkedIn, and Ericsson did!
Get our free 15-point checklist and
avoid the same costly pitfalls.
Contact details collected on InfoSec Insights may be used to send you requested information, blog update notices, and for marketing purposes. Learn more...
What Is PKI Technology?
“PKI technology” is a bit of a misnomer. In a technical sense, it comprises a set of policies, standards, hardware, and software used to create, manage, distribute, store, and revoke digital certificates (more on that momentarily). In a more basic sense, it’s what makes secure, authenticated communication possible over insecure networks.
Does it sound familiar somehow? Yup, PKI IT is the digital version of a passport system where the authorities that issue, renew, or revoke physical passports follow specific processes and rules.
Just like how a passport confirms your identity and enables you to prove your identity when traveling abroad, PKI asserts people, services, and devices’ digital identities and facilitates secure data transmissions over the internet.
5 Key Elements of PKI Technology
Let’s explore five fundamental PKI parts that enable you to protect data, manage encryption, and secure communications. But first, you must understand the three main goals of PKI technology in data and IT security:
- Keep the data exchanged between two entities over the internet private.
- Verify that one or both parties are who they claim to be.
- Assure the data arrives as intended (i.e., unaltered).
To be able to do so, PKI technology counts on a few little helpers (i.e., components). Let’s break down the five most fundamental elements of PKI technology.
1. Certification Authorities (CAs)
Roles in PKI technology: CAs form the backbone of the trust hierarchy (i.e., the “chain of trust”) that’s used to issue and revoke X.509 digital certificates.
Certification authorities are the digital version of the government authorities issuing your passport. A CA, such as Sectigo, is a publicly trusted entity that issues publicly trusted digital certificates to individuals and organizations after conducting a thorough vetting process.
These trusted entities are responsible for maintaining “trust hierarchies” that digital certificates for websites, users, software and document signing, and many other use cases all chain back to. Different CAs (i.e., root, intermediate, and issuing CAs) serve specific roles based on their place in the trust hierarchy, as illustrated below:
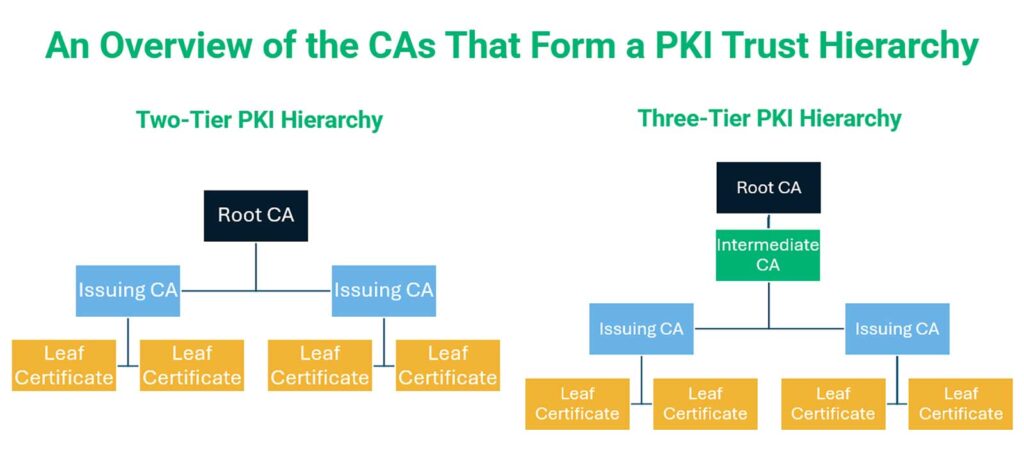
However, it’s important to note that different types of CAs (public vs private CA) can issue publicly trusted certificates for use on the internet or private networks, respectively.
- Public CAs or public PKI. These organizations are carefully selected. Each must satisfy rigid guidelines set by the CA/Browser Forum (CA/B Forum or CABF), an independent organization of representatives from key browsers, operating systems, and mobile device manufacturers. Private PKIs do not have to adhere to CABF server certificate baseline requirements (although doing so is often considered a best practice).
- Private CAs for private PKI. Organizations can create and manage these entities internally using their staff and resources, or rely on a third-party PKI-as-a-service provider. For example, Active Directory Certificate Service (AD CS) enables companies to issue digital certificates exclusively for internal use. Bear with me on this point. We’ll speak more about it later in this article.
Take Your Existing Microsoft CA to the Next Level with Sectigo Private PKI
Sectigo Private PKI is a managed PKI service that complements your Microsoft CA and expands it to protect the non-Windows devices on your networks.
It works with Sectigo Certificate Manager to simplify and streamline certificate deployment and management across all devices and applications within your ecosystem.
2. Digital Certificates
Roles in PKI technology: Enable secure communication and link the identity of an organization or individual to a public-private key pair.
A PKI certificate (i.e., X.509 certificate) is a digital file confirming you are who you’re supposed to be. It’s issued by a trusted third party that confirms the accuracy of the information displayed on the certificate.
Not all certificates are created equal, though. Depending on the level of validation, they can be more or less trusted. Here are a few examples:
- Domain validation (DV) SSL/TLS certificate. This validation level offers the lowest amount of trust. Virtually anyone can get it, including cybercriminals — all that’s required is to have control of the domain listed in the certificate details.
- Organization validation (OV) SSL/TLS certificate. This certificate offers a higher level of trust, as the CA must confirm that the website is legitimately owned by a specific organization. It’s ideal for organizations with a limited budget that don’t want to compromise on security and want to facilitate trust.
- Extended validation (EV) SSL/TLS certificate. Used by banks and renowned brands, EV certificates offer the highest level of trust. Before issuing it, the CA follows a rigid validation and identity verification process to ensure that the organization requesting it is legitimate and that the organizational details included in the certificate are accurate.
Different Types of PKI Certificates Serve Different Roles in PKI IT Security
PKI technology relies on several types of PKI certificates, such as:
- Secure socket layer/transport layer security (SSL/TLS) certificates: These certificates secure websites and web applications.
- Secure/multipurpose internet mail extensions (S/MIME) certificates: S/MIME certificates cryptographically sign, encrypt, and authenticate emails.
- Code signing certificates: These certificates enable organizations to sign software, code, scripts, containers, and drivers.
- Client authentication certificates: These email signing certificates, which also function as personal authentication certificates, authenticate users to applications, databases, and other systems.
- Device certificates: Organizations often use these certificates to authenticate autonomous IoT devices and secure their network connections.
We’ll learn more about their purposes in a minute. For now, it’s essential to know that, despite their different names and purposes, all these certificates typically include the same information, such as:
- Owner’s validated digital identity information,
- A copy of the public key, and
- The CA’s digital signature.
3. Cryptographic Key Pairs
Roles in PKI technology: Cryptographic key pairs encrypt and decrypt information, enabling organizations to securely communicate via insecure networks.
Key Pairs in Private Key Cryptography (Symmetric Encryption)
This encryption method uses a single shared private key to encrypt and decrypt data. Because this sensitive key serves both roles, it must be securely stored and managed to avoid compromise. As such, both parties (i.e., the sender and recipient) must figure out a way to securely share the private key data before using it to exchange sensitive messages.
Historically, two parties used to meet up face to face to exchange the key so they could first verify the other’s identity. But this approach is no longer feasible on its own in a world of online communications over an insecure network (i.e., the internet). If an attacker gets their hands on that private key, they can use it to decrypt your messages. So, what’s the solution? This is where using a public-private key pair comes into play.
Key Pairs in Public Key Cryptography (Asymmetric Encryption)
This approach uses a public key in addition to the private key to securely exchange data in insecure channels. The two keys are mathematically related but are still unique. In public key cryptography, only the public key is shared, meaning the private key remains secret. This helps to protect it from being compromised by bad guys.
Sounds great, right? But as with most things in life, there’s a catch: asymmetric encryption is resource-intensive and isn’t great for use at scale. This is why asymmetric and symmetric encryption both play a role in the SSL/TLS handshake (more on that momentarily), which servers and clients use to authenticate and establish secure website connections.
- Asymmetric encryption is initially used to authenticate one or both parties and to exchange key data.
- Symmetric encryption (which requires less computational overhead) is utilized for the session.
4. Secure Key Storage
Roles in PKI technology: Hardware security modules (HSMs), secure tokens, and cloud-based key vaults enable organizations to securely store and manage their cryptographic keys.
In January 2023, GitHub reported that attackers stole three code signing certificates and keys. The certificates were quickly revoked. However, this incident put GitHub and its customers at risk of attack.
A few months later, the CA/B Forum mandated that all publicly trusted code signing certificates’ keys must be generated and stored on secure hardware (e.g., a FIPS 140-2 Level 2-compliant USB token, a physical HSM, or a cloud-based HSM).
No matter which type of certificate you use, secure hardware such as HSMs are a fundamental pillar for the security of PKI technology as they provide strong protection against cybercriminals. Think about it: Stealing a USB key or a physical HSM appliance in a data center is much more difficult for an attacker than stealing a private key stored on a laptop or a database connected to the internet.
5. Certificate Revocation Mechanisms (i.e., CRLs and OCSP)
Roles in PKI technology: These revocation mechanisms help to identify stolen and/or otherwise compromised certificates and invalidate them ahead of their assigned expiration dates.
Have you ever seen this error message while browsing the internet?
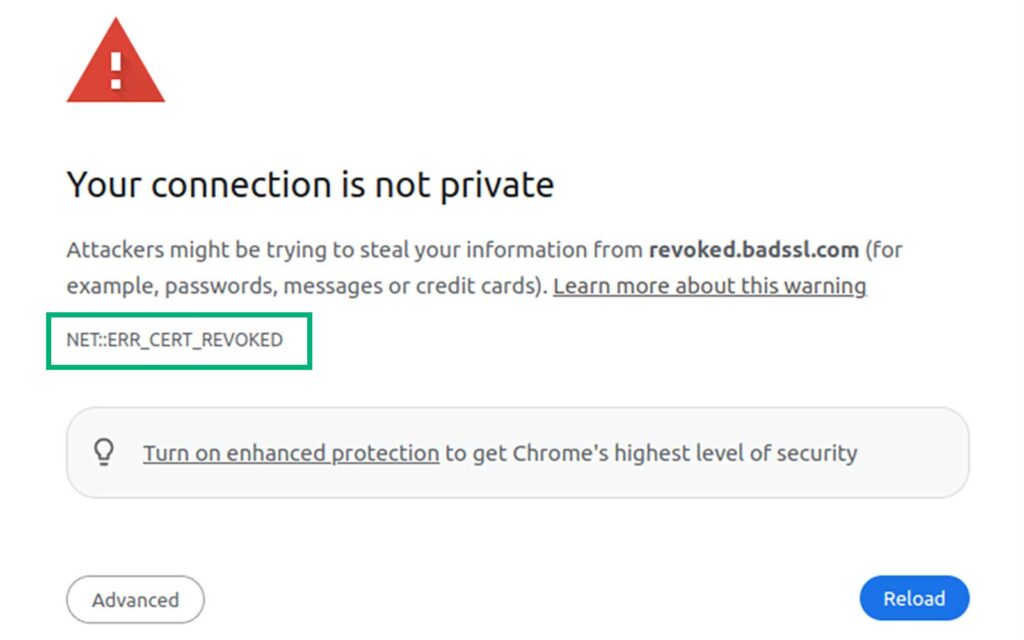
The message above is an example of what you see when a website you’re visiting uses a certificate that has been revoked. When you visit a website, your browser verifies its SSL/TLS certificate validity. To do so, the browser can use different methods:
- The online certificate status protocol (OCSP). The client sends a request to the OCSP responder about the revocation status of a specific certificate and gets a response in nearly real time.
- The certificate revocation lists (CRLs). In this case, the browser sends a request to the CRL distribution point, downloads the latest pre-configured list of all revoked certificates, and checks if the website’s certificate serial number is on the revocation list.
Cool huh? They’re two different processes with pros and cons to each that ultimately share the same goal: alerting the client about whether a website is using a revoked certificate. This prevents users from interacting with potentially dangerous websites (e.g., phishing or phony) and you, as a website owner, from data breach consequences (e.g., legal action, fines).
OK, now that you’ve familiarized yourself with PKI technology key elements, let’s see how they work together.
How Does PKI Technology Work?
In a nutshell, the way PKI IT security works boils down to three salient points:
- Authentication: PKI enables one or both parties to authenticate via insecure channels.
- Security: PKI uses cryptography to encrypt and decrypt data to provide privacy and prevent unauthorized access.
- Integrity assurance: PKI uses cryptographic functions to provide a way to check whether data has been modified or altered since it was digitally signed.
For example, when a user visits your website, their client (browser) and the server engage in a “TLS handshake.” This process determines how the two parties will communicate securely (i.e., using combinations of cryptographic algorithms and functions). Here’s a quick overview of the process:
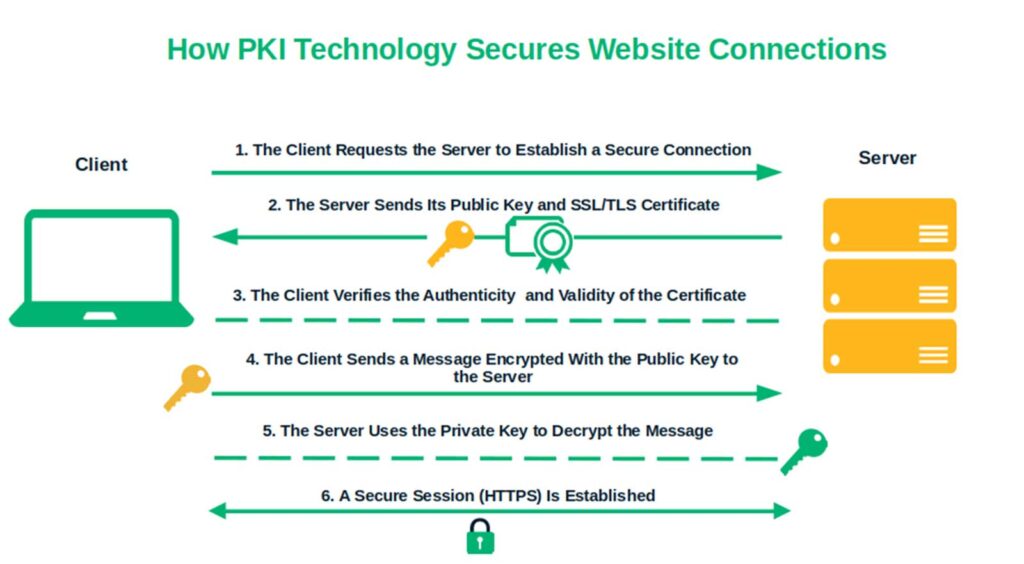
If you want to know more about it and get into the nitty-gritty of the process, stay tuned for my next two articles, which will describe the ins and outs of how PKI technology works and how small businesses and mid-size organizations can use it to improve their security.
5 Examples of Where You Can Use PKI Technology Within Your Organization
So, where can you, as an IT professional, use this wonder of technology to make your organization more secure and trustworthy?
- PKI IT security for websites. Installing an SSL/TLS certificate on your website protects your data and transactions against prying eyes. Thanks to strong encryption, when a customer enters their credit card details to pay for a website order, the information is scrambled into “gobbledygook.” Thus, even if attackers do manage to intercept the data, they’re unable to do anything with it because they lack the requisite private key that’s needed to decrypt it.
- PKI IT security for email security. When it comes to securing emails, PKI technology is essential. You can use SSL/TLS certificates to create a secure channel that protects your data in transit and S/MIME certificates to digitally sign and encrypt the message data for added security.
- PKI technology that secures your software and code. Protect your apps and code against tampering with a code signing certificate. Signing your code ensures that a user’s operating system or client can verify whether a software application has been modified by a malicious third party since it was signed and can prevent the potentially compromised software from installing or running.
- PKI IT security for your documents. Give users a reason to trust your documents. A digital document signing certificate lets you prove that the Microsoft Office document you signed has really been made by you. On top of it, the use of cryptographic hashing to create the code signing digital signature prevents unauthorized alterations from going unnoticed.
- PKI IT security for your IoT devices. Authenticate and secure your IoT devices with a device certificate. One single certificate provides your device with a unique digital identity that authenticates the IoT without the need for a password. It also enables the use of cryptographic algorithms and functions that protect confidential information and the integrity of IoT devices’ data. It’s time to say goodbye to phishing and brute-force attacks.
Want to learn more about these and other specific PKI uses with examples geared for small and mid-size businesses? Check out our other article on PKI use cases to learn more.
PKI Technology: Advantages
By facilitating authentication and ensuring data privacy and integrity, PKI technology offers many advantages for organizations and their customers:
- Trust from your customers and partners. PKI technology helps you boost trust with important parties through digital certificates, identity validation, and encryption. Online transactions are safeguarded, and the risk of attacks is reduced.
- Stronger compliance. Implementing PKI technology and standards helps your organization avoid running afoul of regulatory and noncompliance issues. This is key considering that a violation of even the “less severe” General Data Protection Regulation (GDPR) could result in a fine of up €10 million (i.e., $11.25 million USD) or 2% of your organization’s annual revenue.
- Greater scalability. Public key infrastructure and PKI technology enable organizations to take a more centralized approach to securing their digital assets, devices, and users. This is particularly true for organizations that implement certificate automation to manage their PKI assets.
- Enhanced security. By incorporating PKI IT security into your operations, your organization becomes a more challenging target for cybercriminals who want to make a quick buck.
Take Your Security to the Next Level with Private PKI
While using public PKI technology and certificates is great for protecting external-facing resources, it’s crucial that you don’t ignore your organization’s internal security needs. A private PKI allows you to operate an internally trusted CA that gives you greater control of your IT ecosystem and all of the devices, users, and applications within it.
Do you want to implement an internal PKI within your organization? Excellent! Sectigo Private PKI can help you do precisely that. This intuitive managed PKI platform eliminates many of the burdens associated with running an internal CA.
Whether you’re looking to create a new private CA or want to enhance your existing one, Sectigo Private PKI will help you streamline the process and get back to focusing on other critical responsibilities.
Final Words About Demystifying PKI Technology: An Essential Guide for IT Security Professionals
PKI technology is at the base of a secure digital world. It protects sensitive data, code, and communications while authenticating parties and identities. Now that you know PKI down to the tiniest detail, you’re ready to experiment with it firsthand.
Don’t forget, though: PKI IT security only works if your certificates and keys are safe and sound. So, keep the cybercriminals away from your organization’s emails, passwords, and data with a robust PKI program and pair it with certificate management software like Sectigo Certificate Manager, which integrates with dozens of technologies and platforms, including key vaults to keep your secrets secure. Multiple layers of security are always better than one.






















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security