How Does PKI Work? A Look at the Inner Workings of Public Key Infrastructure
You enjoy the benefits of PKI every day, but have you ever wondered what goes on behind the scenes? Learn how public key infrastructure works to ensure data security and trust for individuals, devices, and organizations.
Just before the last Black Friday, the IKEA operator in several Eastern European countries suffered a ransomware attack. Total loss: $22.8 million. This is just one of the looming threats that public key infrastructure (PKI) helps prevent from happening to your organization.
But how does PKI work?
In our previous articles, we’ve learned what PKI is. We’ve explored its fundamental components and practical uses. Today, we’ll take it a step further by peeking behind the curtain to understand how public key infrastructure works to protect your organization’s data from the bad guys.
Editor’s Note: This post is the third and final article in a three-part series that dives into the details of PKI technology. This series explores the roles of PKI technology in IT security, what PKI uses and applications small and mid-size businesses can enjoy, and how PKI technology works from a technical perspective.
What Is PKI? Public Key Infrastructure Explained in 60 Seconds
PKI is the “secret sauce” of internet security. It’s what makes secure data and communications over the internet possible.
- From a practical standpoint: PKI is what makes “HTTPS” appear in users’ browser address bars and helps prevent “not secure” messages from barring prospective customers’ access to your website.
- From a technical standpoint: PKI is a set of protocols, hardware, and software based on cryptographic key pairs and digital certificates that authenticate parties and ensure secure, unaltered communications in the digital world.
A Quick Recap of What It Does for Organizations Globally
From online payments to email exchanges and even software downloads, PKI:
- prevents sensitive or confidential data from ending up in the wrong hands or being altered in transit.
- helps organizations achieve compliance with various data privacy and security regulations.
- minimizes the risk of data breaches, fines, legal expenses, and other things that pose risks to your organization’s reputation.
How Does PKI Work? An Overview
The way PKI works is by using trusted certification authority’s (CA’s) issued digital certificates to establish a “chain of trust” (more on that momentarily) between two communicating parties (e.g., users, services, or devices). This public key cryptography-based digital trust enables one or both parties to authenticate and encrypt the channel used to exchange data — all while protecting the integrity of the data itself.
Yup, PKI works in a nutshell by facilitating the following:
- Authenticity: PKI utilizes X.509 digital certificates issued via a PKI certificate hierarchy that “chains” back to a trusted entity (i.e., a trusted root CA).
- Confidentiality: PKI employs two cryptographic processes — encryption and decryption — to protect the privacy of your most sensitive data in transit. From a website security perspective, this enables you to ensure that only the intended party can access it in plaintext form.
- Integrity: PKI employs digital signatures that allow recipients to verify whether a file is unaltered or has been tampered with since it was signed.
In a traditional connection, PKI enables a web server to prove its identity to a connecting client as part of the TLS handshake. (We’ll speak more about that a little later.) However, when the client uses a personal authentication certificate, PKI enables it to authenticate as well in a process known as mutual authentication.
Of course, this is a simplified overview of PKI. Let’s answer the question “how does PKI work?” by going through its key concepts step by step.
Don’t have time to go through all of the steps in detail? Get an overview of all the PKI basics in 180 seconds.
How Public Key Infrastructure Works (Step #1): Certificate Issuing
As a certificate requestor, you must generate a public-private key pair as part of your certificate signing request (CSR). You’ll keep the private key to yourself (store it securely!) and send your public key to a trusted certificate authority (CA) with your request for a digital certificate. Which type of digital certificate? The answer depends on your specific needs.
Certificate Types
Organizations are spoiled with options. There are several types of certificates, each of which protects data in different situations. Here are a few quick examples of PKI certificates you’ll commonly find used by small and mid-size businesses:
- Secure socket layer/transport layer security (SSL/TLS) certificate. Go for it if you want to secure information exchanged between your website and the client. SSL/TLS certificates are available in different variants: single-domain, multi-domain, wildcard, and multi-domain wildcard. Don’t forget to select your preferred validation level: domain validation, organization validation (OV), or extended validation (EV).
- Secure/multipurpose internet mail extensions (S/MIME) certificate. Pick this email signing certificate to sign and encrypt your emails, ensure message integrity, or authenticate users and devices without the need for traditional ID and password combinations. That is why this certificate is also referred to as a personal authentication certificate or client authentication certificate.
- Code signing certificate. If you’re a developer or a publisher, this is the certificate for you. It enables you to confirm your identity as a software developer or publisher and prove that your product hasn’t been modified without authorization. It comes in two varieties: standard validation (SV) and extended validation (EV).
- Document signing certificate. This certificate is ideal when you want to prove that your PDF invoice or other document is original and hasn’t been tampered with. You can also use it to sign several file types, including Microsoft Office documents.
The Certificate’s Validation Process
To answer a question like “how does PKI work?” you first need to understand validation and its role in trusted digital identities. For this example, we’ll assume you request an EV SSL/TLS certificate for your business’s website.
Since you requested the highest level of identity assurance, the CA verifies your organization following a more in-depth vetting process. This process may take slightly longer than usual, but it’s well worth it. In exchange, your website will get the ultimate level of trust. Once the validation is completed, the CA issues a certificate that includes the public key and your organization’s information.
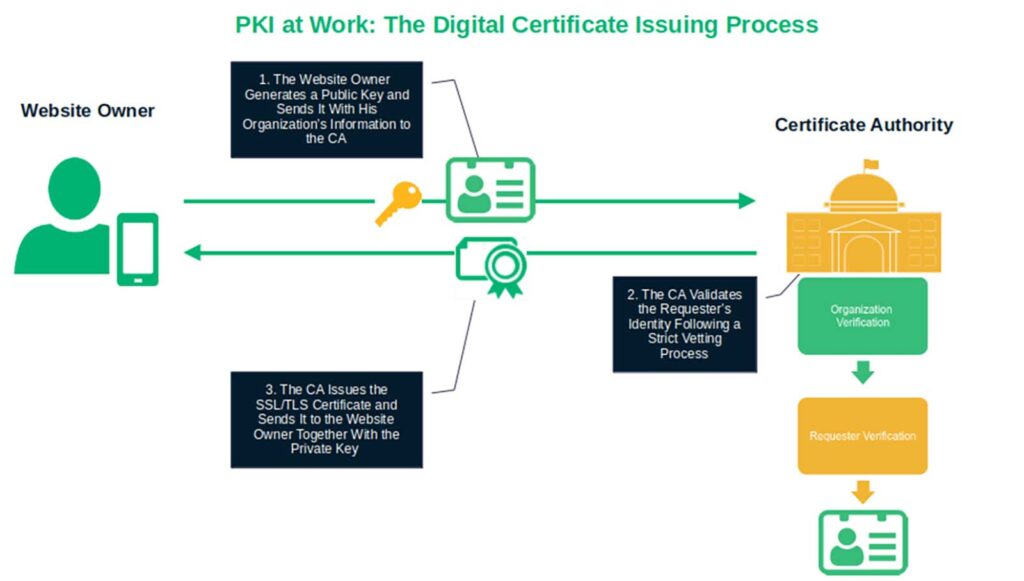
How Public Key Infrastructure Works (Step #2): Authentication
After you’ve received and installed the certificate on your web server, you’re essentially good to go. As soon as a user visits your website, the client initiates what’s known as the TLS handshake, a process that relies heavily on PKI.
The TLS Handshake
This process enables one or both parties (the latter in the case of mutual TLS authentication) to authenticate and exchange information about which cryptographic ciphers they support. Afterward, the server picks the algorithm to use for the secure communication session.
In a traditional TLS handshake, when the user’s client attempts to establish a connection to your website:
- Your web server sends its SSL/TLS certificate and public key to the client.
- After verifying the issuing CA’s digital signature on the certificate, the client sends a message encrypted with the server’s public key.
- When the recipient server decrypts it using its private key, it means that the client is communicating with the right partner (your legitimate website).
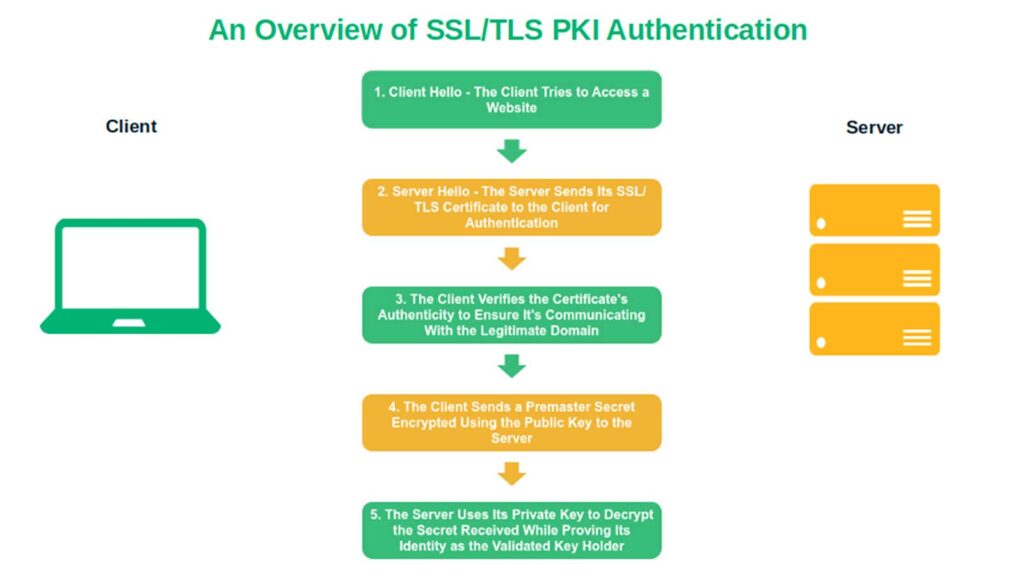
The Chain of Trust
Before moving on to the next step in answering how PKI works, let’s quickly clarify what a chain of trust is and how PKI works with it. A chain of trust is a set of digital certificates that link your SSL/TLS certificate back to the CA that issued it, much like how your genealogical tree links you to your ancestors. It’s this origination method that PKI uses to enable the client to verify whether your server’s identity is legitimate.
This set usually includes three certificates:
- The root certificate. Owned by the CA and saved in a “trust store.”
- The issuing (or intermediate) certificate(s). One or both of these certificates act as a buffer between the root and your domain’s leaf certificate. (This is shown in the left half of the illustration below.) However, some PKI trust chains have more than one subordinate CA — in these cases, they’ll have an intermediate CA that sits between the root and issuing CAs (as shown in the right half of the following illustration).
- The server (leaf) certificate. That’s the SSL/TLS certificate the CA sent you.

So, how does PKI work with the chain of trust to promote confidence in your website? Remember when we said that the server sends the SSL/TLS certificate and its public key to the client? Here’s where the chain of trust comes in.
The client chains the SSL/TLS certificate back to the root, passing through the intermediate, just as if it were following an imaginary “Ariadne’s thread”:
- If the certificate can successfully be traced back to the root, your website is displayed.
- If it can’t be traced back, the browser shows a warning message like the one below.
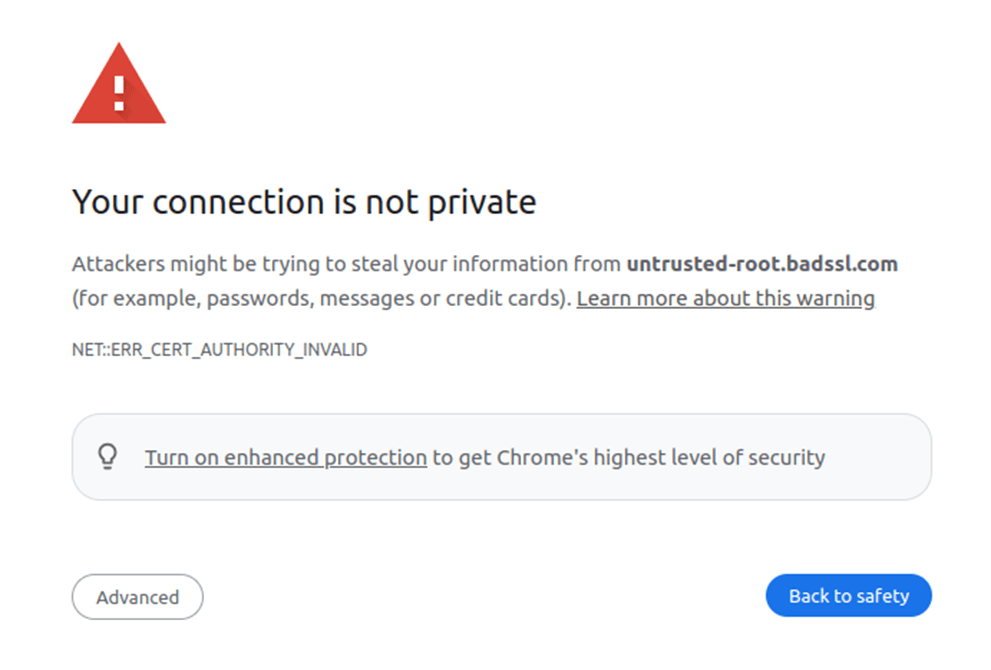
How Public Key Infrastructure Works (Step #3): Encryption
After successful authentication, in our example, PKI creates a secure (encrypted) communication channel between the user’s browser (i.e., client) and your server. That’s how PKI works to protect your customers’ and organization’s data in transit (e.g., credit card information, passwords, and social security numbers) from prying eyes.
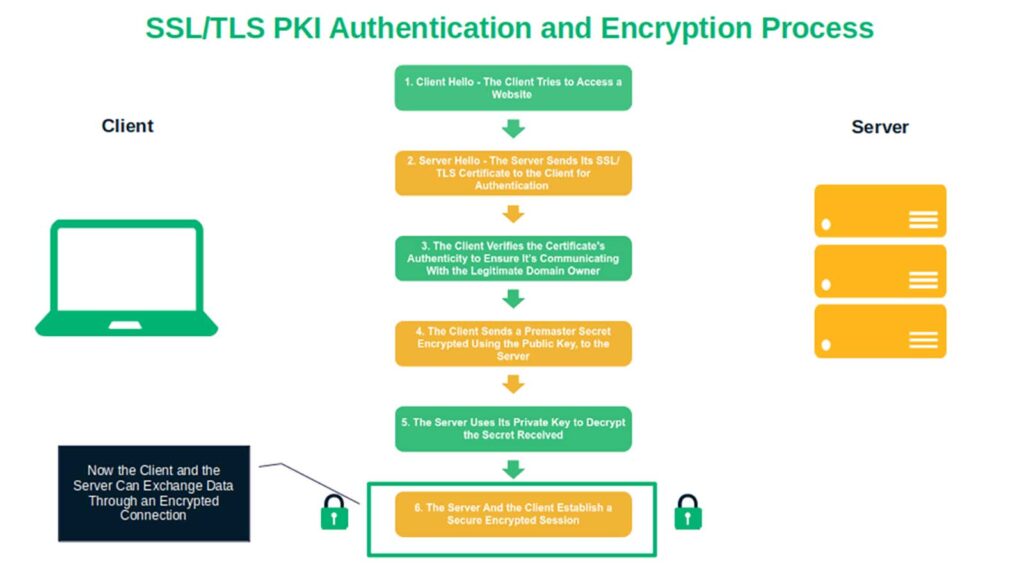
In general, PKI utilizes a mix of asymmetric and symmetric encryption:
- Asymmetric encryption enables the secure exchange of data over an insecure network using a public-private key pair. In a nutshell, the data is encrypted with a public key and decrypted with a private key, scrambling data into gibberish nonsense that only the owner of the corresponding private key can decrypt. The advantage? The transferred key-related data is protected against man-in-the-middle attacks.
- Symmetric encryption, which requires less computational overhead and is better at scale for web servers, is then used for the rest of the session. This method of cryptography relies on both parties using the same shared cryptographic key to encrypt and decrypt data. But enabling both parties to have the same key means that the key-related values that generate the key must be shared securely first via a secure channel (i.e., by using an asymmetrically encrypted channel).
With SSL/TLS, you get the best of both worlds: the enhanced security of asymmetric encryption initially paired with the speed and performance of symmetric encryption for the rest of the session.
Hold on. All of these things occur in the background, unbeknownst to site visitors and other prospective customers. So, how can these individuals know that the connection is secure? By seeing the HTTPS indication at the beginning of the URL (and a padlock near the browser’s web address bar in some clients, such as Firefox).
That’s how public key infrastructure works to secure data in transit. But PKI can do much more for your business. And this is what we’re going to explore next, as our backstage trip hasn’t come to an end yet. There are still a few things to explore before we go back to the digital world’s stage. So, keep on reading.
How Does PKI Work to Protect Your Organization? 8 Practical Examples
Now that we understand how PKI works from a technical point of view, it’s time to discover a few of the ways that public key infrastructure works to help secure your organization’s communications and sensitive data in a more practical sense:
- Secures your point-of-sale (POS) devices’ data in transit.
- Authenticates your network’s IoT devices and protects the integrity of their data in transit.
- Protects physical access to your organization’s premises via PKI-based authentication smartcards.
- Shields cloud-based services and communications from MitM attacks and data leaks via insecure connections.
- Authenticates the software components listed in your software bill of materials (SBOM).
- Secure communication between microservices and containers.
- Protect access to machines with secure shell (SSH) passwordless authentication.
- Enables the more secure mutual authentication (mTLS) for APIs, devices, apps, and services.
Find even more practical examples of how PKI works to pave the way toward zero-trust security in our dedicated article on PKI uses and applications.
PKI Needs a Proper Key and Certificate Management to Be Effective
You’ve just learned how PKI works to facilitate data confidentiality, integrity, and authenticity and how it keeps your communications safe over insecure networks. In many ways, public key infrastructure is the MVP of internet security.
However, there’s a catch: PKI can’t work its magic without robust key and certificate management. Managing keys and keeping them secure is a big deal for PKI. It would be like asking a magician to do his tricks without his hat and wand.
Therefore:
- Purchase your digital certificates only from reputable CAs and resellers such as SectigoStore.com. It’ll guarantee you a secure chain of trust and rock-solid digital certificates.
- Store your private keys securely. All code signing certificates’ private keys must be generated and stored on FIPS 140-2 Level 2-compliant hardware, such as a USB token or an HSM. Apply the same security criteria to the other keys.
- Manage your certificates properly.Software like the Sectigo Certificate Manager automates certificate renewals and management. It speeds up certificate revocation and allows you to implement policies that adapt to each situation.
Follow these tips, and PKI will work like a charm.
Final Thoughts About a Look at the Inner Workings of Public Key Infrastructure
Here ends our grand tour of looking behind the scenes of how PKI works. We hope this article answered your questions so that you’ll never again have to wonder, “How does public key infrastructure work?”
Now, it’s your turn. Use X.509 digital certificates to secure your organization, systems, and customers with PKI. In times when AI-powered attacks increase the chances of breaches, PKI can help businesses of all sizes secure their assets and protect customers’ privacy while offering a robust authentication system.





















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security