OWASP Mobile Top 10 Vulnerabilities & Mitigation Strategies
According to Statista there are 3.5 billion smartphone users — that means a lot of people who could become victims of insecure mobile apps
The OWASP Mobile Top 10 list is a great resource for app developers who want to create secure apps. That’s because many mobile apps are inherently vulnerable to security risks. Let’s think about some of the attacks on mobile apps that have occurred in the past few years. There was the WhatsApp Pegasus spyware that enabled attackers to control victims’ devices. Another was also the attack on the Pokémon Go app, where users could reverse-engineer the app to catch more Pokémon.
Many other apps and organizations, such as Tinder and MediaTek, have fallen victim to mobile security attacks. But what makes them so vulnerable? Mobile apps have a greater attack surface than web apps since the apps can be downloaded from public stores, and the code can be inspected. Combine that with that the amount of user data they can collect, and we’re left with very attractive targets for cybercriminals.
The OWASP mobile top 10 vulnerabilities list the most common security flaws found on mobile devices. But what is included on the OWASP mobile security list of vulnerabilities?
OWASP Mobile Top 10 Vulnerabilities
Based upon survey and feedback collected from the worldwide community, the Open Web Application Security Project foundation gave us the OWASP mobile security risks for the first time in 2011. After that, they released new lists in 2014 and 2016 — the latter being the latest and most current OWASP mobile top 10 list.
While there’s one exact carry-over from the 2014 top 10 mobile risks list, the 2016 top 10 mobile risks list is mainly different in terms of the categories break down. For example, in the 2016 list, one of the items from the 2014 list was removed and two new risks were added. They also split some categories in half to address them separately.
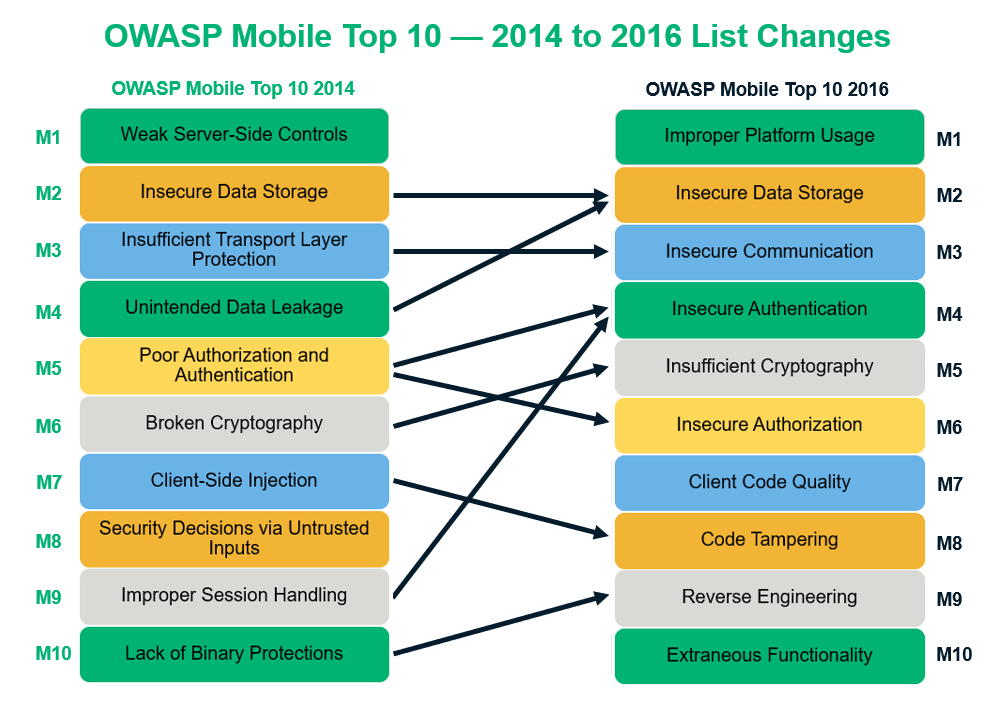
With this in mind, let’s explore the 10 mobile risks that made the final cut in 2016 and look at the ways you can remediate these risks.
M1. Improper Platform Usage

The latest OWASP mobile top 10 list ranks improper platform usage as the leading mobile security vulnerability. Whether you’re an Android user or an iOS customer, each of these platforms are expected to adhere to certain developmental guidelines for security purposes. However, apps may unintentionally violate these published guidelines, best practices, or goof up in their implementation process. That is what this first mobile security risk talks about.
This threat refers to the misuse of any platform feature of the Android or iOS operating system or failure to incorporate platform security controls. This includes issues concerning improper use of security controls and platform features that are a part of the mobile operating system, such as:
- Misuse of the iOS Touch ID feature, which can result in unauthorized access to the device.
- Incorrect use of the iOS Keychain for instance by storing session keys in the app local storage,
- Requesting excessive or wrong platform permissions,
- Android intents (used to request an action from another app component) that are marked public may reveal sensitive information or permit unauthorized execution.
OWASP Mobile Top 10 Remediation Measures for This Vulnerability:
This OWASP mobile security risk is something that you must address on the server side of things. Alongside following platform development guidelines, using secure coding practices and applying the right configuration settings on the server-side helps to minimize risks. Additional mitigation strategies to reduce platforms from being used improperly include the following:
- Restricting apps from communicating with each other, limit access, implement restrictive file permissions, etc.
- Applying the most restrictive protection class for iOS keychains and adopt best practices to avoid weak implementation of any controls.
M2. Insecure Data Storage
Next on the OWASP mobile top 10 list is insecure data storage. Your mobile device may get lost or stolen and land in the hands of an adversary. Or a piece of malware, acting on the attacker’s behalf, may execute on the device, and the attacker might be able to exploit vulnerabilities that leak personal information and gain access to sensitive data.
While it isn’t always feasible to have apps that don’t store data, it is crucial to store that data securely in a place that won’t be accessible to another app or an individual. Jailbreaking or rooting a mobile device is sufficient to dodge encryption protection, and dev teams must never assume that attackers won’t have access to filesystems if they’re easily accessible.
OWASP Mobile Top 10 Remediation Measures for This Vulnerability:
Threat model the app to understand what information assets are processed by the application and how the APIs handle the data. Doing this helps you to:
- Assess whether encryption is applied effectively and how the encryption keys are protected.
- Implement technologies to harden the code against tampering by using obfuscation, protection against buffer overflows and so on,
- Avoid storing/caching data where feasible, and
- Deploy sound authentication and authorization checks.
M3. Insecure Communication
Insecure communication ranks third in 2016 OWASP mobile top 10 list. If the data travels unencrypted in cleartext, anyone monitoring the network can capture and read all the information being sent over the wire.
Mobile apps commonly exchange data in a client-server model, and it must be transmitted over the device’s carrier network and the internet securely. The traffic can be intercepted by proxies, cell towers, or an adversary compromises your Wi-Fi or installs malware on your device. So, what can you do it mitigate vulnerabilities associated with these types of data exchanges?
OWASP Mobile Top 10 Remediation Measures for This Vulnerability:
To avoid data from being stolen as it travels across the network, rely on industry-standard encryption protocols and other general best practices.
- Deploy SSL/TLS certificates from trusted certificate authorities (CA) to secure all communication channels.
- Alert users if an invalid SSL/TLS certificate is detected or if the certificate chain verification process fails.
M4. Insecure Authentication
Insecure authentication comes next on the OWASP mobile security vulnerabilities list. Before granting access, mobile apps need to verify the identity of the user. An authentication bypass is often executed by leveraging existing vulnerabilities, such as improper validation of service requests done by the mobile app’s backend server. Mobile apps need to verify and maintain user identity, especially during the transmission of confidential data such as financial information.
OWASP Mobile Top 10 Remediation Measures for This Vulnerability:
Weaknesses in the authentication mechanism for mobile apps can be exploited by an attacker. Capitalizing on those weaknesses allows them to bypass password requirements or gain additional permissions leading to data theft and other damages.
So, what can you do to stop it?
- Avoid local authentication methods. Instead, shift this responsibility to the server-side and download application data only after a successful authentication.
- Refrain from using vulnerable authentication methods (such as device identity), don’t store passwords locally, implement multi-factor authentication (MFA), disallow using all four-digit PIN as passwords where feasible, etc.
M5. Insufficient Cryptography
There are two situations in which a system’s cryptography may get compromised to reveal sensitive data:
- The underlying algorithm used for encryption and decryption might be weak, or
- The cryptographic process itself has implementation flaws.
Broken cryptography in mobile apps can be the result of one of several factors. This list of potential causes includes:
- Bypassing built-in code encryption algorithms,
- Improperly managing your digital keys, and
- Using custom or deprecated encryption protocols.
OWASP Mobile Top 10 Remediation Measures for This Vulnerability:
Insufficient cryptographic controls can lead to the unauthorized retrieval of sensitive data (such as personal information about the user) from the device.
- Apply strong cryptographic standards as recommended by the National Institute of Standards and Technology (NIST).
- Avoid storing any sensitive data on the device whenever possible
M6. Insecure Authorization
Not all users are created equal! Some users may be regular users, while others may require additional permissions and privileges, such as admin users. Poor authorization schemes fail to verify not who the user is but whether the user is sanctioned to access the resources they’re requesting. Failure to properly enforce identity as well as the permissions given to the users allow hackers to log in as legitimate users and perform privilege escalation attacks.
OWASP Mobile Top 10 Remediation Measures for This Vulnerability
The impact of insecure authorization is similar to insecure authentication. They both may lead to data theft, reputational damage, and even noncompliance fines and penalties.
- Ensure that for each request, backend processes verify that incoming identifiers associated with an identity match up and actually belong to the identity.
- Validate the roles and permissions of an authenticated user using the information on backend systems and not based upon the information supplied by the mobile device.
M7. Client Code Quality
This category on the list of OWASP mobile security risks is a bit of a catch-all for mobile client issues relating to faulty code implementations.
An attacker may pass crafted inputs to function calls made within an app in an attempt to execute them or observe the application’s behavior. It may lead to degradation of performance, increased memory usage, etc. Note that the mistakes in code need to be fixed in a localized way since they arise on the mobile client and are different from server-side coding errors. There could be code-level mistakes in mobile apps that may lead to issues such as:
- Format-string vulnerabilities,
- Buffer overflows,
- Integration with insecure third-party libraries,
- Remote code execution
Several apps rely on third-party libraries to build their applications, which often contain bugs and are not well tested. These issues are outside the control of the app developer since they don’t own the code. More often than not with code-level bugs, the solution is to rewrite some of the code running on the device. But what else can you do?
OWASP Mobile Top 10 Remediation Measures for This Vulnerability:
Poor code quality issues may lead to remote code execution and other vulnerabilities and issues that we’ve already mentioned. Thankfully, there are a few things you can do to help mitigate these issues:
- Test for buffer overflows, memory leaks, etc. using automated tools, rely on source code reviews, and write code that’s easy to understand and well documented.
- Use consistent coding patterns across the organization.
M8. Code Tampering
App stores sometimes contain tampered versions of mobile apps. An example of a modified app is where a hacker modifies the app’s binary to include malicious content, install a backdoor, etc. Attackers can re-sign these counterfeit apps and publish the modified version onto third-party app stores. They can also deliver them to a victim directly via a phishing attack to trick them into downloading the app.
OWASP Mobile Top 10 Remediation Measures for This Vulnerability:
Tampering with the code can lead to revenue loss, identity theft, reputational and other damages.
- The app must be able to identify any code integrity violation (if additional code has been added or modified) and react suitably to it at runtime. Using something like a code signing certificate could help to let users know about the code alterations.
- Implement anti-tamper techniques that prevent illicit apps from executing via implementation of checksums, digital signatures, code hardening, and other validation methods.
M9. Reverse Engineering
Attackers may reverse engineer the app and decompile it to perform some code analysis. This is particularly dangerous since the attacker can understand, inspect, and modify the code to include harmful functionality or transmit undesired advertisements. Once they understand how the app operates, they can modify it using tools such as IDA Pro, Hopper, and other binary inspection tools. Once they get the app to behave in the desired way, they can recompile and run the app.
OWASP Mobile Top 10 Remediation Measures for This Vulnerability:
In order to prevent reverse engineering, the attacker must be unable to de-obfuscate the code using tools like IDA Pro and Hopper.
M10. Extraneous Functionality
Sometimes developers may unintentionally leave backdoors or additional functionalities in mobile apps that aren’t apparent to end users via the interface. These products may get released into the production environment with a feature not intended to be made available, creating security risks.
These weaknesses can typically be exploited by hackers from their systems directly without requiring any participation from regular users. They may examine configuration files, analyze the binary, etc. to discover functionalities in the back-end system that cybercriminals can leverage to perform an attack.
OWASP Mobile Top 10 Remediation Measures for This Vulnerability:
One of the most effective ways to prevent these types of mobile app vulnerabilities is to perform manual secure code review. What this does is allow you to:
- Examine the mobile app’s configuration settings to detect any hidden switches.
- Ensure that the logs don’t hold exceedingly descriptive statements about backend systems.
Wrapping Up
The OWASP mobile security vulnerabilities list serves as a starting point for organizations, developers, security professionals, and users who’re just beginning to address their mobile security risks. It comes with definitions for each of the vulnerabilities discussed, example attack scenarios, prevention controls, and recommended mitigation strategies.
But remember, tackling the OWASP mobile security vulnerabilities is only be the bare minimum. Be sure to go above and beyond to ensure your mobile apps are as secure as possible.





















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security