What Is WPA2 & How Do I Improve WPA2 Security?
More than 68% of users rely on this WPA2 Wi-Fi encryption technology, the Wireless Geographic Logging Engine (WiGLE) shares. Here’s what to know about WPA2 security for your personal and enterprise wireless networks…
For a lot of us, the internet is omnipresent. Wireless security may skip our radar while connecting to the public Wi-Fi at coffee shops or the airport to update our social media or reply to emails. However, connecting over insecure links or networks is a security hazard that could lead to potential data loss, leaked account credentials, and a litany of other concerns. This is why using the right Wi-Fi security measures is critical. But to do that, you need to know the difference between different wireless encryption standards, including WPA2.
So, what’s the difference between the Wi-Fi at a coffee shop and the one we use in our home or office networks? Let’s break it down!
How Wi-Fi Works & Why You Need to Secure Your Connections
Wi-Fi, the wireless network technology that allows devices to interface with the internet, communicates using radio waves. It’s based on the Institute of Electronics and Electrical Engineers’ standard IEEE 802.11. However, this technology is highly susceptible to hacking since weaknesses have been discovered in the protocols upon which they’re based.
Consider the kind of transactions that occur over the internet via both home and business networks. You could be making online purchases from your home that requires you to enter payment information. At work, you might be accessing sensitive customer data for certain projects. As you can see, both of these networks carry sensitive information that needs to be safeguarded from unauthorized access. This typically involves the use of encryption processes and technologies.
The need for wireless security arises to prevent any illegal access to maintain data confidentiality and prevent prohibited users from eating away on the connection bandwidth. Unauthorized users can wreak havoc on a network using various means, starting from eavesdropping on the connection to spreading malware across the network. Hackers also can employ a technique called wardriving, where they drive around the city mapping Wi-Fi access points in search of unsecured networks that they can exploit or use to carry out nefarious activities.
WPA2 & Other Types of Wireless Encryption Standards Definitions & Explanations
Let’s look at the different options you can use to secure your networks and the encryption standards that make wireless security possible. As you can see from this timeline, there have actually been several types of wireless security standards that have been in use over the past 20 or so years.
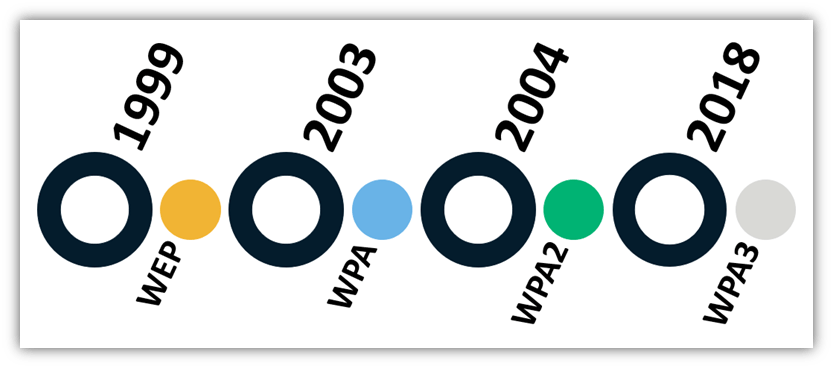
Wired Equivalency Privacy (WEP)
WEP was formally introduced as a Wi-Fi security benchmark in 1999. However, it was part of the original IEEE 80.11 standard ratified in 1997. The idea was to provide a similar level of data confidentiality as wired networks, although that goal wasn’t realized. That’s because WEP uses RC4, a stream cipher with multiple vulnerabilities, as its encryption algorithm.
You see, RC4 relies on an initialization vector to prevent the same plaintext data from generating the same WEP encrypted data. However, the initialization vector is transmitted in plaintext, and by studying enough packets using the same WEP key, an attacker can mathematically derive this key.
As a result, WEP is the most insecure out of all the encryption standards. WEP offers two modes of authentication:
- Open — Here, the WEP key is not needed. But if specified, it will be used to encrypt traffic.
- Shared — This means that the wireless access points and wireless clients are manually configured with the same key beforehand.
Wi-Fi Protected Access (WPA)
Wi-Fi protected access, created in 2003, is an improvement over WEP. That’s because it provides enhanced security in terms of key handling and a more efficient user authorization process. WPA was introduced to enhance security for insecure WEP networks without requiring any additional hardware. It relies on the temporal key integrity protocol (TKIP) for encryption, which dynamically modifies the keys used. TKIP incorporates key mixing functions that increase the key complexity and make it more difficult for attackers to decode.
WPA also incorporates a message integrity check nicknamed “Michael.” Although safer than the CRC-32 checksum used for similar integrity checks in WEP, it still has its weaknesses.
This brings us to our next type of wireless encryption standard: WPA2.
Wi-Fi Protected Access 2 (WPA2)
WPA2, launched in 2004, is the upgraded version of WPA and is based on the robust security network (RSN) mechanism. WPA2 operates on two modes — personal (pre-shared key or PSK) mode or enterprise (EAP/Radius) mode. As the name suggests, the first is designed for home use while the enterprise mode is typically deployed in a corporate environment. Both of these modes rely on AES-CCMP, a combination of counter mode with CBC-MAC message integrity method and AES block cipher for encryption. This makes it more difficult for attackers listening in on the network to spot patterns.
Pre-Shared Key or Personal Mode (WPA2-PSK)
WPA2 personal uses a shared passphrase for access and is not recommended for a corporate environment. It is usually deployed in home networks where the passphrase is defined in the access point (router), and client devices need to enter the same passphrase to connect to the wireless network. The encryption passphrase is stored on the individual endpoint devices and can easily be recovered. Additionally, every time an employee leaves the organization, or if the passphrase is somehow disclosed, it’ll have to be changed individually on all access points and connecting devices.
Enterprise Mode (EAP)
The enterprise PA2 has multiple options for Extensible Authentication Protocol (EAP) – password-based authentication, certificate-based EAP, etc. Note that EAP in and of itself is an authentication framework and can be implemented by adopting various EAP types.
While WPA2 is a step up from WEP, it’s still vulnerable to key reinstallation attacks (KRACK). KRACK exploits a weakness in WPA2’s four-way handshake. An attacker may pose as a clone network and force the victim to connect to the malicious network. This enables the hacker to decrypt a small piece of data that may be aggregated to crack the encryption key. However, client devices can be patched, and it is still more secure than WEP or WPA.
This brings us to the next link in the Wi-Fi encryption standards evolution.
Wi-Fi Protected Access 3 (WPA3)
WPA3 is now considered the mandatory certification for Wi-Fi CERTIFIED™ devices, according to the Wi-Fi Alliance. But what is WPA3 and what makes it different than its WPA2 and WPA predecessors? WPA3 aims to improve some major shortcomings of WPA2 (such as its susceptibility to passphrase brute-force attacks, key reinstallation attacks, etc.). This enables it to provide better security for personal and open networks as well as security enhancements for business networks.
A key benefit ofWPA3 is that it provides resilience to brute force attacks even for weak or short passwords. It replaces the WPA2-PSK with WPA3 Simultaneous Authentication of Equals (SAE), a secure password-authenticated key exchange method. WPA3-SAE does not transmit the password hash in clear and limits the number of guesses an attacker can make. Yet, last year researchers discovered several security flaws (downgrade attacks, side-channel attacks, etc.) in the dragonfly handshake used in WPA3 (that replaced the four-way handshake used in WPA2).
Wi-Fi Alliance has released patches for these vulnerabilities. But given the frequency of Wi-Fi standards failing with KRACK (in the case of WPA2) and dragonblood, relying solely on them may not be the smartest choice for securing our networks.
5 Tips on Ways to Improve WPA2 Security
Many users continue to use WPA2 personal in their home or small business network to access the internet. Here are some pointers you can use to keep your communication secure:
- Keep your devices patched and up to date. Update the operating system on all client devices on the network for boosting WPA2 security. This ensures that the latest patches against known vulnerabilities (like KRACK) have been installed.
- Use strong and unique passwords with a greater password length. Increase complexity by using special characters, numbers, uppercase, and lowercase letters.
- Ensure that no default credentials are used on any of the access points (such as admin credentials on a router).
- Enter the IP address to access router settings using a web browser. Under firmware settings, routinely check for any available updates pending installation on your router. Additionally, consider replacing your router once manufacturers stop supporting it and the product is discontinued. Modern Wi-Fi systems such as Google Wifi have a feature for installing automatic updates.
- Disable remote access to your router. To ensure that your router settings cannot be tampered with over a wireless connection, disable access over Wi-Fi so that changes can only be made by plugging in via an ethernet cable.
Besides the above-mentioned tips, using a virtual private network (VPN) or adopting security best practices such as browsing over secured HTTPS connections can provide an additional layer of security.







![The TLS Handshake Explained [A Layman’s Guide]](https://sectigostore.com/blog/wp-content/uploads/2023/01/tls-handshake-feature-150x150.jpg)






 (7 votes, average: 4.43 out of 5)
(7 votes, average: 4.43 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security