7 WordPress Security Vulnerabilities & How to Fix Them
According to BuiltWith, 44% of websites using content management systems use WordPress. With this in mind, we’ve got your all-in-one WordPress vulnerability guide with security tips, helpful tools and links to important resources…
When we talk about a WordPress vulnerability, what we mean is any security loophole or weakness in your WordPress (WP) website or the CMS platform itself. Cybercriminals can exploit these WP vulnerabilities to:
- Execute various cyber attacks.
- Steal data that they can use or sell.
- Spread malware.
- Bypass authentication mechanisms.
- Make unauthorized website changes and transactions.
- Take down your website.
Hackers use WordPress security vulnerabilities as entry points to hack your website. If hackers steal and misuse your users’ personal and financial information, you might face legal consequences, too. Hence, it’s essential for you to find every WordPress vulnerability you can and fix them as soon as possible.
People can find common vulnerabilities and exposures from the public domain, too. For example, MITRE maintains a list of CVEs, including many of the latest WordPress security vulnerabilities.
In this article, we’ll cover the seven most common WordPress security vulnerabilities and what you can do to fix them.
7 WordPress Security Vulnerabilities & How to Fix Them
Some of these fixes are easy to apply, while others require basic programming knowledge. We have also linked the required resource pages and plugins, so it becomes easier for you to implement the tips.
WordPress Vulnerability 1: Vulnerable Login Fields
As we mentioned earlier, a “WP vulnerability” means any weak component of the WordPress platform (as well as plugins, themes, insecure accounts or databases, etc.) that attackers take advantage of to gain unauthorized access to your website. One of such vulnerable area is the login page fields. Hackers have some techniques which they apply on login fields to bypass the authentication mechanism.
Once they successfully log in to your (admin) account, it becomes easy for them to install malware, post inappropriate content, or steal other users’ data. That’s why an unprotected login field is one of the major WP vulnerabilities.
WP Solution 1. Limit Login Attempts
One method to address this issue is to install plugins (there are many types out there such as Limit Login Attempts, Loginizer, and WPS Limit Login). By default, all WordPress sites allow users to input their user IDs and passwords for an unlimited number of times until they find out the right combination of credentials.
Although this feature makes logging in easier for users who aren’t good with memorizing their passwords, hackers use it as one of those WordPress security vulnerabilities they can exploit by deploying a brute-force attack. In this attack, a hacker applies a bot to continually input login credentials to the login fields. This allows the attacker to keep applying a pre-guessed database of seemingly limitless user IDs and passwords automatically until it makes a successful login attempt.
The best way to prevent brute force attacks is by limiting the number of logins attempts a user can make in a specific period. After the pre-decided number of failed login attempts (generally between three and five), the system temporarily blocks the user/IP address.
WP Solution 2. Force Strong Passwords
Install plugins like Password Policy Manager or Force Strong Passwords to make sure all your users, employees, coauthors, etc. create strong passwords (having one uppercase, one lowercase, one digit, and one special character).
WP Solution 3. Two-Factor Authentication
Passwords can be stolen, guessed, or vulnerable to brute force attacks. To combat this, you can install two-factor authentication (2FA) tool/plugins like Google Authenticator, Two-Factor Authentication, or WP 2FA to enable one additional layer of security. With 2FA, along with password, you need to provide a unique one-time password (OTP), secret code, or PIN that’s sent on your mobile phone or email address. After enabling 2FA, your login page would look something like this:
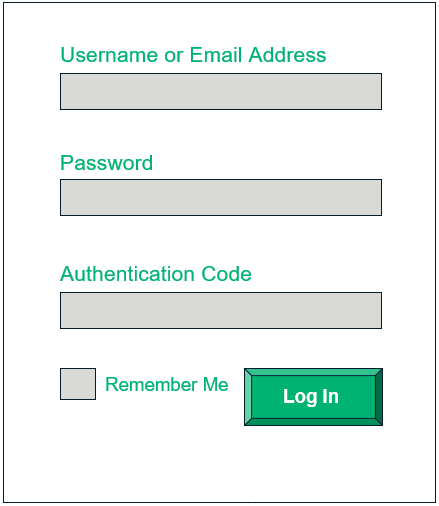
WP Solution 4. Unique User IDs
If you’re using generic user IDs like “admin” or your own name, change it immediately create something unique. Generic and common user IDs are exploitable via brute force attacks.
WordPress Vulnerability 2: Unchanged URLs and File Names
Another WordPress security vulnerability that users often overlook is using the default structure for URLs, file names, and storage locations. By using the default names and locations, you’re making it easier for attackers to find important pages and files to hack them. You should manually change these paths and file names to fix this vulnerability.
WP Solution 1. Change Default URL Path for Admin Page
WordPress uses the following URLs as the default admin page links:
- www.yourdomain.com/wp-login.php, and
- www.yourdomain.com/wp-admin.
Anybody can reach the admin login page easily and use bots to activate the brute force attack. But if your admin URL is unique, only the person having the exact URL can access your login page.
Be creative and change your admin page URL to something unique. For example: www.yoursite.com/pinkbird.php or www.yoursite.com/nationalpark.
WP Solution 2. Change the Default Database Table Name
By default, the table name in your WordPress database has wp- prefix. All your login credentials, user info, transaction details, audit logs, and other important types of data are stored in these tables. That’s why it’s common for hackers to target these types of databases. Attackers use bots to search and break into your WordPress database.
Follow this guide to change the prefix with some unique name: Instruction for changing table prefix in WordPress
WP Solution 3. Change the Location of Your Wp-config.php File
Your wp-config.php file stores information about your website’s important settings, configurations, WordPress authentication keys, and databases. Wp-config.php file is, by default, stored in the root directory and can be accessible to a hacker. Move the wp-config.php file to any other folder above the root directory that’s not a subdirectory of your public_html or WWW folder.
For additional information and instructions, check out this article on how to change the location of the wp-config file.
WordPress Vulnerability 3: A Lack of Data Transmission Encryption
When your users submit any data to your website (name, email address, password, payment card details, tax-related information, etc.), that data transmits in plain text. This means that when data exchanges between a user’s browser and your web server, a hacker can intercept the insecure communication channel and read the data. Basically, your website will be vulnerable to man-in-the-middle (MitM) attacks.
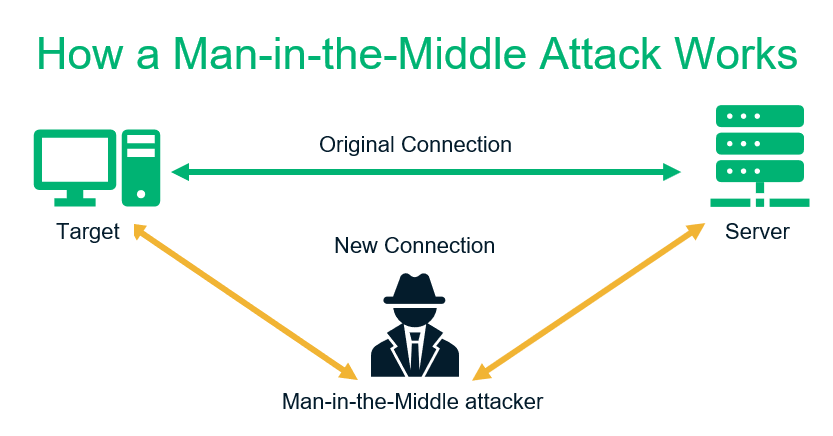
They can use this data to carry out ransomware attacks, financial fraud, or identity theft. That’s why unencrypted data communication channels are considered another WordPress vulnerability.
To address this issue, install an SSL/TLS certificate on your website. This enables you to encrypt the data in transit between your users’ browsers and your web server using asymmetric encryption. There are free and commercial certificates available, but it’s generally better to choose paid SSL certificates over free ones. This is because commercial SSL certificates come with warranties and customer support and can be as inexpensive as costing less than $10/year.
You can install these certificates easily in your cPanel. There are different plugins available, too, that you can use (such as the Really Simple SSL plugin).
WordPress Vulnerability 4: Lack of Firewalls, Malware & Vulnerability Scanners
Cybersecurity is an ongoing process. If your website is not constantly monitored and protected by a malware scanner and firewall, you might not be aware of a cyber attack or malware attack until it’s too late. Hence, an unprotected website is considered a major WordPress vulnerability.
Security scanners and firewalls monitor your website 24/7, detect and remove the malware, block suspicious IPs, and prevent the cyberattack in the initial stage only to cease further damage.
Be sure to install any WP security scanners and firewalls from trusted companies and websites only. You can also use a website scanner like Sectigo’s HackerProof Trust Mark, which scans your website every day for vulnerabilities and gives you tips for ways to remediate them.
WordPress Vulnerability 5: Outdated WordPress Components
Hackers, developers and bug hunters (ethical hackers, aka white hat hackers) alike are always trying to find WordPress security vulnerabilities in the codes. The difference between them is what they do once they find them. The latter two want to find them so that they can be fixed, and so that developers can deploy a patched version that remediates the bug. (Hackers want to exploit it.)
Information about some of the known WP vulnerabilities is released in the public domain, too. The WordPress Vulnerability Database (wpvuldb.com) is one place you can look to learn about the latest WordPress vulnerabilities. Some other resources include the MITRE CVE list we mentioned earlier as well as the National Institute of Standards and Technology (NIST).
Because some of the major WP vulnerabilities are easy to find the internet, hackers seek out websites using older, unpatched versions of WordPress to exploit their security vulnerabilities. Hence, why it’s crucial to keep an eye on updates and install the patched versions as soon as they’re available.
WordPress Vulnerability 6: WordPress Plugin Vulnerabilities
Wpvulndb.com reports observing a total of 21,785 vulnerabilities in their database — out of those, 3,882 (i.e., 17.8%) are WordPress plugin vulnerabilities.
WordPress is an open-source platform, so anyone can make plugins for it and publish it there. Some plugin makers might be amateur developers or might not be very strict about plugin security. That results in poorly coded plugins with weak security postures. But even well-known plugins suffer from security vulnerabilities due to human errors.
For example, MalCare reports the following well-known plugins have been exploited or patched so far in 2020:
- File Manager (WordFence reports that this exploit affected 700,000 WordPress users),
- The Duplicator,
- ThemeGrill Demo Importer,
- Profile Builder,
- Flexible Checkout Fields,
- ThemeREX Addons,
- Async JavaScript,
- Modern Events Calendar Lite, and
- 10Web Map Builder for Google Maps.
Want to learn more about a specific WordPress plugin vulnerability.? Check out this database to view an impressive list of WP plugin vulnerabilities.
How to Fix Plugin-Related Issues
Plugins have direct control over some parts of your website. So, instead of putting hard work in finding vulnerabilities in your entire website, hackers just need to exploit only one plugin you are using to get inside your website and hack it! That’s why hackers are always in search of WordPress plugin vulnerabilities.
You, as a user, can’t fix the plugin’s bugs. That’s the plugin developer’s job. But you can do these following these things.
WP Solution 1: Install Trusted Plugins
It is a good practice to install plugins from reputable companies or developers. Check the user reviews before installing them to ensure that you’re not creating new problems for yourself.
WP Solution 2: Report Security Bugs Immediately:
Some of the most common WordPress security vulnerabilities stem from plugin issues and bugs. This is why it’s imperative to report them whenever you come across these types of issues. The sooner a developer can identify bugs and fix them, the safer your (and other websites) will be.
So, if you install a plugin and notice anything unusual, like the following examples, be sure to report them to the developer:
- New form fields appear that you didn’t add,
- Form responses change automatically in your database,
- Form responses show codes or unusual links
WP Solution 3: Update Plugins Regularly
Most plugin developers are quick in fixing security bugs and publishing patched versions of their plugins. Make sure you install updated plugins as soon as the new versions come to market.
When people are using freemium plugins, they might not get access to the plugins’ updated versions unless they pay for it. Because of this, jackers know that people using free plugins generally may not have the updated versions. So, attackers just find the popular freemium plugins and search for free users to hack their websites.
When you decide to use a freemium plugin, keep in mind that sooner or later, you are going to “pay for it” — either by buying access the updates or by becoming a victim when a criminal exploits a vulnerability you didn’t apply a patch for!
WordPress Vulnerability 7: Unprotected Input Fields
Hackers can insert payloads in any types of input fields such as contact and subscription forms, login fields, comments, or even in your site’s search bar. The payload can execute cross-site scripting (XSS) or SQL injections. Sometimes attackers insert the unsolicited advertisements and malicious hyperlinks in the comments sections of websites.
In XSS attacks, hackers insert scripts anywhere on the web page, but more commonly in the input fields. When users click on such fields, malware gets downloaded in the user’s computer, they are redirected to a spammy website, or the data they have provided is stolen by the hackers.
With SQL injections, hackers write malicious code in web applications and forms’ input forms to take advantage of vulnerabilities that exist within them. This allows cybercriminals to bypass websites’ authentication mechanisms, exfiltrate their sensitive data, or even hijack their entire databases via ransomware attacks.
These are some methods you can use to secure your input fields.
- Minimize User Input: Have scroll-downs, calendars, and checklists to reduce the fields where users need to write down information in free form. For example, for date of birth, instead of making users write down the data manually, have a calendar from which they need to select the DOB.
- Validate/Whitelist Data: Validating means making sure the data provided by users are in the same format as it should be. For example, the name field should accept only letters (not digits or special characters). The phone number field’s answer must be in an xxx-xxx-xxxx format and accept only digits in it. Learn more about validation codes and implementation.
- Thoroughly Sanitize Inputs: This is the second step after validation in which the WordPress scans all the input data and removes the malicious codes before it enters into the database. Check out this guide from WordPress for how to sanitize your inputs.
- Block Spammy Content from Comments: Install plugins like Akismet, CleanTalk, or Antispam Bee to detect and remove spammy and malicious comments.
- Update, Update, Update: As covered in the previous point, regularly update all your WordPress components (WordPress version, themes, plugins, and applications).
- Use Web Application Firewalls and Other Protections: Security software (such as IDS/IPS) and firewalls can detect the vulnerabilities in input forms and scan input data. These are integral tools that no WordPress website — or any website for that matter — should go without.
Final Words on WordPress Security Vulnerabilities
According to BuiltWith, out of all the websites using content management systems (CMSs), 44% of websites use WordPress. Each month, 70 million new posts are published on WordPress. No doubt, when a platform is remarkably popular among the entire tech community and all sizes of businesses, it’s going to attract hackers and cybercriminals, too. These attackers are always hunting of WP vulnerabilities in the main WordPress software, plugins, themes, or applications.
In reality, your website will never be 100% WordPress vulnerability–free. Cybersecurity is an ongoing and evolving process, which means that you need to keep a constant eye on your website’s overall security. It’s about making yourself as tough a target as possible for cybercriminals.
By following the above-mentioned tips, you can at least fix the well-known WordPress security vulnerabilities and enable your website to flex a robust security posture.

















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security