Exploit vs Vulnerability: What’s the Difference?
We’ll take an in-depth look at the difference between vulnerabilities and exploits, why they matter, and how you can use that knowledge to keep your website safe
Ever wonder how a hacker actually hacks? Or are you tired of unrealistic movies that are full of endless lines of code and keyboard clacking without any explanation? Seeing as you most likely googled something along the lines of “exploit vs vulnerability” or “vulnerability vs exploit” to get here, then the answer to those questions is yes.
Exploring what vulnerabilities and exploits are, the differences between them, and how they’re useful to hackers is an excellent way to learn more about how hackers think. More importantly, it can help you better protect yourself and your organization against them.
So, let’s compare and break down an exploit vs a vulnerability to get a better idea of what they are and how they differ.
Exploit vs Vulnerability: A Quick Take
In a nutshell, a vulnerability is a weakness or opening for hackers to find a way into a website, a system that connects to a website, operating systems, web applications, software, networks, and other IT systems. An exploit is a specific code or attack technique that uses a vulnerability to carry out an attack or gain unauthorized access. The vulnerability is the opening and the exploit is something that uses that opening to execute an attack.
The names are, indeed, apt as hackers look for vulnerabilities to exploit. However, it should be noted that not all vulnerabilities are exploitable. Whether it’s due to a lack of abilities on the hacker’s end or supplemental security tools making it difficult for the hacker to exploit the vulnerability, not all vulnerabilities will be exploited. In fact, a 2019 study shows that out of 76,000 vulnerabilities the researchers discovered between 2009 and 2018, only 5.5% had been exploited in the wild.
That’s the quick answer. Now, let’s look at the topic of exploit vs vulnerability more in depth.
Exploit vs Vulnerability: A Deeper Dive
To understand vulnerabilities and exploits, you first need to understand a hacker. Hackers are usually looking to do one of three things:
- Receive some type of short-term or long-term financial, social or political gain;
- Wreak havoc for personal satisfaction; or
- Both of these reasons.
A hacker’s mindset and methods are very similar to those used by a home burglar. They often scout their target (to some extent), search for a vulnerability and exploit it. For example, a burglar will look for an unlocked window (vulnerability) and then wait until you are away to enter it (how they exploit it) without your permission. Then from there, they are most likely looking to steal valuable things but there are also intruders who just want to vandalize (like a hacker will do with a website at times).
So, here’s another way to differentiate exploit vs vulnerability. The big difference between a vulnerability and an exploit is that a vulnerability is a hacker finds an opening in your cyber defenses. An exploit is what occurs if and when they actually take advantage of the vulnerability without your permission. It’s the difference between finding an unguarded entrance to a fort and actually charging through it. But let’s take a few moments to explore each of these terms a little more in depth.
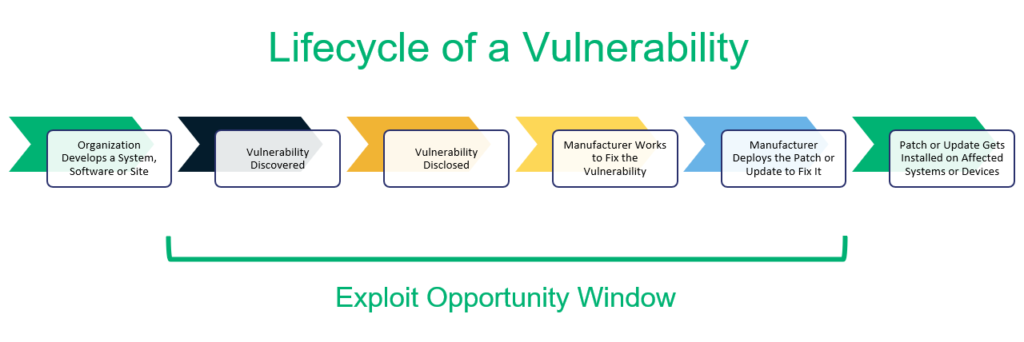
What Are Vulnerabilities?
As mentioned, a vulnerability is a weak point or channel that hackers could use to find a way into your website, operating system, applications, network, or other IT-related systems. (A vulnerability isn’t actually the attack or exploit itself.) Vulnerabilities could be a weakness that exists in your software code. And users can even create some vulnerabilities without even realizing it.
For example, outdated or legacy software or system that you haven’t updated yet could be the target of a hacker. Another example of a vulnerability is when a user creates a weak password or reuses a password that gets compromised in a breach. A vulnerability can also be created by a cyber attack, such as a phishing email with a link that tricks or manipulates you into downloading files containing malicious software or code.
How the vulnerability is created doesn’t change the fact that there is a weakness that hackers could potentially exploit. As for what we mean when say “exploited,” see our next section…
What Is an Exploit?
As mentioned, an exploit is the use of a specific code or technique that takes advantage of a vulnerability that exists in a target’s IT systems or software. Essentially, a hacker will exploit the vulnerability in a way that gets them unauthorized access to the system. Exploits need vulnerabilities to exist, which is why preventing vulnerabilities is so important.
Looking for vulnerabilities manually would be a laborious way of hacking, which is why hackers use automated tools to attack vulnerabilities at mass scale. For many hackers, exploiting vulnerabilities is very much a numbers game. If a hacker discovers an outdated piece of software in a CMS, they may use an automation tool to crawl thousands of sites that use that CMS looking for the vulnerability so they can collect mass amounts of data, typically from many small websites.
Knowing the difference between vulnerabilities and exploits is the first step in knowing how to protect yourself.
Zero Day Vulnerabilities and Exploits
So, what happens if there is a vulnerability that you’ve discovered within your own application but haven’t patched yet? Or what if a cybercriminal has created malware or another way to exploit your application that no one has seen before? Each of these two examples is known as a zero day vulnerability and a zero day exploit, respectively.
A zero day vulnerability is an exploit that you may or may not know about but haven’t yet had time to address. There are organizations and websites such MITRE, NIST and vuldb.com that maintain lists of known critical vulnerabilities and exposures. Once a patch is released for the vulnerability, however, it’s no longer considered a zero day vulnerability.
A zero day exploit is when a cybercriminal uses an unpatched or unknown vulnerability to their advantage. They can do this by creating new malware that they create or by using phishing techniques to direct users to infected websites. “Zero day” attacks are particularly dangerous because they capitalize on unknown or unpatched issues that have yet to be fixed. They’re also typically undetectable because traditional antivirus and anti-malware software aren’t looking for them.
Examples of Vulnerabilities and Exploits
So, now that you know what vulnerabilities and exploits are, you’ll probably want a few more examples that you might come across. Here a few examples of how a hacker might use a vulnerability and exploit:
Example 1
Vulnerability: You did not update your WordPress plugin, which has a code error.
Exploit: A hacker uses the vulnerability to launch a SQL injection attack.
Example 2
Vulnerability: A web admin has a weak password that lacks complexity and doesn’t meet NIST passwords standards. (See NIST SP 800-63B Authentication and Lifecycle Management, section 5.1.1.) Some general password creation best practices include using long passwords that include a combination of uppercase and lowercase characters, and at least one special character and number.
Exploit: A hacker uses a “cracker tool” to crack the password and now controls your website. It should be noted should how accessible these “cracker tools” are. There are literally top 10 lists that rank password cracking tools that range from ones that assists with brute force attacks to tools that can crack LM and NTLM hashes!
Example 3
Vulnerability: A website has an area that allows users to upload unvalidated files with no filters or limits.
Exploit: A hacker uploads a file that contains executable code and now has access to your website source code and database credentials (basically controlling your website).
The CIA Triad: What It Is & Why You Should Use It
So, now that you know the difference between a vulnerability and an exploit, you might be semi-worried that someone is going to use them against you. Don’t worry (or even be semi-worried) — we got you covered. Let’s start with the CIA triad, or what’s sometimes called the AIC triad. This model provides a great starting place for responding to information security threats.
No matter which you prefer to call it, the triad is a helpful and accurate way to remember the three cornerstones of a good cybersecurity program:
- Confidentiality — Keep your data/info — such as HR documentation, customer info, and passwords — confidential and protected from unauthorized access.
- Integrity — Maintain the integrity of your data assets to avoid hackers modifying, eliminating or controlling them in any way.
- Availability — Your data and systems should always be available to those who have legitimate access. Don’t let hackers block users from your website or systems, or allow anyone to take them out entirely.
Pro Tips for Dealing with Vulnerabilities and Exploits
As mentioned, the CIA triad is an excellent barometer for what cybersecurity methods and protocols you should implement. So, when you are attempting to prevent vulnerabilities from becoming a thing, it’s important to look for methods and protocols that align with the CIA triad and can help you avoid being the victim of a hacker.
Here a few tips and suggestions that we think can help:
Get an SSL/TLS Certificate
Make sure your entire website is using the secure HTTPS protocol. This is imperative for ensuring that your site exchanges data via a secure, encrypted channel. Do this by installing an SSL/TLS certificate via your web hosting control panel. After that, update your CMS to use HTTPS URLs and then set your HTTP URLS to point to their secure HTTPS counterparts (using 301 redirects).
Use End-to-End Encryption
Cybercriminals love to target email because it’s a common way for companies to communicate and share information internally. Unfortunately, many organizations choose to share sensitive information via email, and this can leave that data vulnerable to cybercriminals.
By using an email signing certificate, you can encrypt the email message and attachments (using asymmetric encryption) before you hit the end button. This means that no matter whether your email sends through secure or insecure channels, your data is secure from prying eyes because only your recipient will be able to open the email using their private key.
Have a Strong & Unique Password (For Everything)

Nothing makes life easy for hackers like a weak password. Use a long password (like 12-20 characters long) with numbers, capital letters, lowercase letters and special characters. Also, use a new password that isn’t similar to anything you use on other accounts. By using a unique password for every account you use, even if your password for one account gets compromised in a data breach, all of your passwords are still secure.
Implement Access Controls
As a web admin, it’s important to control your CMS user accounts. There are two ways to do this.
- Limit access to a need-only basis. So, if you have a writer that publishes blogs on your website, they don’t need full access to all the capabilities found in the backend of your CMS. That way, if a hacker is able to obtain their login information, their capabilities are limited as well.
- Delete inactive accounts. If there’s no longer the need for an account, it’s important to delete it. The idea here is to eliminate any unnecessary channels hackers can use to get into your website.
Update Your Software, Hardware, and Plugins
This may be the most important tip of the bunch. It’s vital you keep your software updated as outdated software is a very common vulnerability hackers will exploit. Generally, you will need to ensure your CMS and CMS add-ons (themes, plugins, etc.) are updated while holding your web host accountable to maintain updates for your operating system and server software.
Review and Test Your Code
Reviewing and testing your code for weaknesses is a critical component of the project lifecycle when creating new sites and applications. This process should include a secure code review. Don’t skip or skimp on this crucial step as doing so may result in data breaches or cyber attacks that you could have otherwise prevented.
Perform Vulnerability Assessments
A vulnerability assessment is the act of finding, measuring, and categorizing vulnerabilities in your website, computers and other systems. Using automated tools, such as a vulnerability scanner, is a popular way to attack this task.
If you go the vulnerability scanner route, I suggest looking for a vulnerability scanner that keeps an updated database of known vulnerabilities, one that is specific to the CMS you use and one that scans for implementation vulnerabilities. There are also website scanners like Sectigo’s HackerProof Trust Mark, which scans your website daily and provides recommendations for how to remediate them.
Use Penetration Testing
Pentesting is basically simulating a cyberattack to see if any vulnerabilities exist and if/how they can be exploited. Having this ability allows you to not only list what vulnerabilities exist but measure what methods cybercriminals could use to exploit the vulnerabilities. This extra layer of knowledge will make patching vulnerabilities more accurate and efficient.
Put a Web Application Firewall (WAF) in Place
A WAF is longtime best practice in the world of websites. It’s essentially a defense that sits between your website and users. For small businesses, I recommend a cloud-based WAF. It allows for both convenience and customizability. WAFs are all about what rules you set to detect and fight off attacks (and how you evolve the rules over time as well).
With a cloud-based WAF, the CDN/WAF company will manage and update the rules for you, but you will have the option to add your own rules as well.
Conclusion on the Topic of Vulnerabilities and Exploits (TL;DR)
I hope that this article provides you with greater insights about exploits vs vulnerabilities! To quickly recap for those of you who want to skim to understand an exploit vs a vulnerability:
- A vulnerability is a weakness or gap in your defenses that could be exploited. Vulnerabilities can exist in everything from websites and servers to operating systems and software.
- An exploit is when a cybercriminal takes advantage of a vulnerability to gain unauthorized access.
- Not all vulnerabilities get exploited — but when they do, the resulting damages can be immense.
- Frequently rolling out updates and patches is essential to the cybersecurity of your website and organization as a whole.
- There are many ways to prevent and patch vulnerabilities. The key is to find a routine and process that incorporates a variety of tactics (like the ones mentioned above) to ensure your site, software, network and other IT-related systems are as safe and secure as they can be.
Understanding what the differences are between vulnerabilities and exploits is critical to helping you address them before they become security issues. And now that you know more about them, make sure to implement these best practices to make your organization a tougher and less vulnerable target. Good luck!














 (9 votes, average: 4.56 out of 5)
(9 votes, average: 4.56 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security