The Pros and Cons of Passwordless Authentication
There’s a lot of hype about passwordless authentication these days. But is passwordless security something that’s worth investing your money in and basing your cybersecurity on? Let’s find out!
There are many pros and cons of passwordless authentication solutions and security processes (which we’ll go over shortly). By now, we can assume that you already have a basic idea of what passwordless authentication is from our previous article: What is Passwordless Authentication?
As the name suggests, passwordless authentication, or password-free authentication, doesn’t require users to input passwords to complete the verification process. Instead, they need to provide another form of evidence that authenticates their identity, such as:
- A one-time password (OTP),
- Secret PIN,
- SMS- or app-generated codes,
- PKI-based (public key infrastructure) personal authentication certificates, or
- Biometrics to complete the authentication process.
Hackers can steal or guess the passwords using brute force attacks. They can also buy lists of breached passwords on the dark web or acquire them using malware. If you’re a business owner, you can deploy passwordless authentication tools on your websites, applications, software, and office devices to strengthen the security posture and provide a convenient login experience to your customers and employees.
But before implementing passwordless technology, you should be aware of its advantages and disadvantages. In this article, we’ll cover the pros and cons of passwordless authentication with regard to cost, security, and user experience.
Advantages of Passwordless Authentication
Let’s explore in detail what kind of benefits passwordless authentication provides.
1. Passwordless Authentication Improves User Experience
NordPass reports that the average user has 70-80 passwords. As you can imagine, it’s really difficult for an average person to create a challenging password, let alone memorize 80 unique passwords. With passwordless authentication, users no longer need to brainstorm to set and memorize strong passwords. There are no more password memorizations needed at all!
So, how does this help your business? Some users may abandon their shopping carts or your website because they’re required to log in but don’t remember their passwords. Resetting the password adds another layer of complexity, which people generally detest. But you still need to make sure their accounts are secure, right?
Passwordless authentication provides users with a convenient, stress-free experience. They just need to input their user ID or phone number to receive a new one-time password or PIN (OTP), link, or generated token code. Sometimes, a biometric (such as their fingerprint, face, or retinal scan) is enough for the authentication via some password authentication mobile apps, which is quicker and even more convenient.
2. You Don’t Need to Worry About Password Theft
With passwordless authentication, you, as a website owner or employer, don’t need to worry about password theft or data breaches that result from password compromises because passwords are no longer part of the equation. For public-facing websites, OTPs and “magic links” provide greater security than many passwords.
With traditional password-based logins, if a customer claims that an unauthorized transaction has taken place through their account on your website, there will be four types of parties involved:
- The customer,
- One or more banks,
- The court, and
- Your website.
If the perpetrators gain access to the customer’s account with a leaked or stolen password, you will be part of the entire investigation and legal process, even if there is no mistake on your part.
But with passwordless authentication, the use of a breached, leaked, or stolen password is no longer an issue. Here’s a quick video from Microsoft that explains how some types of passwordless authentication work:
Although passwordless authentication is not foolproof, it’s still often more secure than traditional password-based authentication methods alone.
3. Passwordless Authentication Solutions Protect Against Brute-Force Attacks
Passwordless authentication helps to protect websites from becoming victims of brute force attacks. A brute force attack is, essentially, a method of password guessing via trial and error. To better understand this point, you first need to understand how brute force attacks work.
In a brute-force attack, a hacker applies a malicious script to a website’s login field. The script inputs random passwords (often pulled from the hacker’s database of pre-guessed user IDs and passwords) one-by-one until it finds matching password and username combinations.
To protect websites from brute force attacks, web admins generally enable the limited login attempt option. This feature freezes the user ID or IP address associated with the login attempt for a set time (such as after three to five failed login attempts). But there are some techniques attackers use to bypass the “limit login attempt” feature.
Password Spraying
Attackers apply a single password against multiple user IDs. For example, they apply the most commonly used password, “123456,” for millions of user IDs. They then move down the list, trying other commonly used passwords, repeating the process until they find another matching set of insecure credentials. Then another… and another… and the cycle goes on until they achieve their goals.
Brute-Force Attacks via Botnets
A botnet refers to a group of malware-infected devices (bots) that execute various cybercrimes based on a hacker’s (botmaster) commands. In a botnet brute force attack, the bots receive a list of websites (or IP addresses) and some pairs of usernames and passwords (generally less than three) from the botmaster for each IP address. The bots try to authenticate the given set of credentials on the designated IP.
The success of brute-force attacks depends upon finding the right combination of user IDs and passwords. But when you use passwordless authentication, none of the brute force attack methods can work. Since passwordless authentication generates a unique OTP, link, or PIN, or if it relies upon biometrics, it makes it challenging for attackers to steal, replicate, or fake.
But just how broadly can botnets strike? Well, back in 2019, a botnet named GoldBrute attacked more than 1.5 million Windows servers globally that were running remote desktop protocol.
4. Passwordless Authentication Strengthens Your Organization’s Cyber Security Posture
If an employee’s password gets leaked (depending on what accounts those compromised credentials can access), the attacker can:
- Gain access to the company’s network (and other devices connected to it),
- Access email accounts to view and/or send messages,
- Access confidential files and data,
- Carry out financial fraud,
- Eavesdrop on internal communications,
- Post offensive messages from the company’s social media profile to ruin its reputation,
- Leak trade secrets, or
- Cause general havoc.
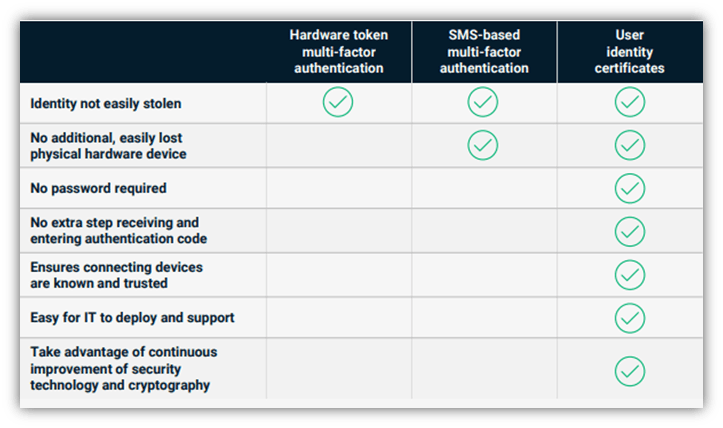
But when you employ robust passwordless authentication solutions like PKI client certificates with hardware tokens, you can be assured that only legitimate employees access the confidential accounts and hardware resources (laptops, PCs, cellphones).
PKI Certificate Client-Based Authentication (User Identity/Email Signing Certificates)
So, let’s talk about user identity certificates (certificate-based authentication) for a few moments. This authentication method relies on public key infrastructure — the foundation of secure communications on the internet — and the use of digital certificates to authenticate users to servers. No passwords, OTPs, PINs or anything else are necessary. You simply replace these secrets with digital certificates on employees’ devices and use them to authenticate users automatically.
(Note: Here at SectigoStore.com, we generally call these client authentication/user identity certificates “email signing certificates” because you can also use them to sign and encrypt email communications. However, they’re capable of more than just that since they can authenticate users for other purposes.)
Of course, if you want to make this even more secure, pair your user identity/email signing certificate with a trusted platform module (TPM). (Which, by the way, come equipped with new Windows 10 devices. Check out this article from HowtoGeek.com to see if your device has a TPM chip installed.)
Sectigo’s Senior Fellow Tim Callan says that you’ve got yourself a passwordless authentication method that’s more secure than passwords combined with phone-based MFA.
5. Passwordless Security Helps to Reduce Cost in Long Run
Passwordless authentication solutions tend to reduce overall security costs over time. A company doesn’t need to spend money on password storage, management, and resets. It frees up the IT department’s time as they no longer require setting password policies and have to focus on compliance with password storage laws and regulations. They don’t need to be constantly trying to detect and prevent password leaks.
Plus, the tech support team doesn’t need to assist in resetting forgotten passwords. Data from HYPR‘s 2019 password survey shows that 78% of respondents had to reset their passwords from the prior 90 days because they forgot them. But how much does each password reset request cost? Okta reports that a single password reset costs companies an average of $70. According to the University of Birmingham, it costs them £150 per password reset and a whopping 30,000 hours of lost productivity per year!
Disadvantages of Passwordless Authentication
Now that we know all the great upsides of passwordless security, let’s explore the downside of certain types of passwordless authentication.
1. Can’t Protect Users in the Event of Device Theft or SIM Swapping
If someone steals your mobile device or you lose it, you’re in trouble. An attacker who gets their hands on your device can use it to intercept all OTPs, PINs, and magic links that are generated on the apps or sent over email or SMS text messages. In password-based authentication, the perpetrator can’t log in to the apps unless they know the password. So, if someone steals or otherwise gains access to the user’s device, the passwordless authentication may be riskier than the traditional password-based authentication.
Let’s consider a SIM swapping attack as an example. SIM swapping takes place when someone tricks or manipulates a mobile service provider (carrier) into transferring your SIM card to them. This often involves the cybercriminal:
- Pretending to be you,
- Falsely claiming that you’ve lost your SIM card, and
- Procuring a replacement SIM card for the same mobile number (transferring your number to their device).
If successful, the perpetrator can use their SIM card access to intercept all of your SMS messages and access all of the apps that rely on that SMS-based OTP authentication.
2. Biometrics Aren’t Foolproof
Hackers can deceive passwordless security technology by showing images or videos of the original user, using machine learning to create morphed images of the intended target, or using sound from the audio recordings or videos for voice cloning. There are even ways to bypass fingerprint locks!
In terms of what technology can do, we’re living in incredible times. But it can also be downright scary when it falls into the wrong hands. For example, here’s an example of how far voice cloning technology has come (which could be used to fake voice ID-based authentication methods):
3. Users Are Hesitant About Trusting Passwordless Technology
The concept of computer passwords was introduced at MIT in the 1960s and has become fundamental to authentication and security over the years. Most of us have set the autofill (auto-login) password functionality for our email accounts, applications, and websites. Some people use password managers to set up and manage tons of complex passwords without the hassle of having to remember them.
As you can imagine, these shortcuts make the authentication process easy and convenient. But they’re also less familiar than traditional password-based security, which can be scary. And since some passwordless authentication methods require users to supply a new OTP or PIN every time we use it, it makes some people resistant to this change.
In an organizational setup, auto-fill passwords provide ease to employees when they have to access a large number of applications, resources, and software every day. However, if employees have to authenticate themselves by providing OTPs or scanning their biometrics every time they need to access something, it can quickly become an annoyance.
4. Cost of Implementation Can Be High (Depending on the Solution)
As with any technology, investing in new passwordless software and hardware infrastructure can be cost-prohibitive, especially if you have a large customer base and many employees. A single hardware security key USB token, on the cheap side, costs around $20 but can range upwards of $500. The software/applications that enable OTP/magic link facilities on your website generally costs $25 per month to $1,000 per month (depending on the service provider and how frequently it’s used). And if employees lose their hardware device, token, card, etc., the company needs to replace those tools. This can be more expensive than simply resetting the passwords in some cases.
Of course, there are some free software programs and apps available for passwordless authentication. But do you want to trust the security of your business’s data to just any free app? Now, that’s not to say all free apps are bad. Some of Microsoft‘s passwordless technologies are free, for example. But, again, you need to provide training to the development team to teach them how to implement and troubleshoot passwordless authentication on your website and applications.
With PKI certificate-based authentication, you don’t have to both with all the “extras.” Simply replace your employees’ passwords with the certificates, implement touchless authentication, and issue your certificates automatically as part of your certificate management process. Using a certificate manager to manage these and all of your other PKI digital certificates (SSL/TLS, code signing certificates, etc.) makes the process even simpler.
5. Passwordless Authentication Doesn’t Protect Against Certain Types of Malware
Some malwares which are specially designed for spyware attacks can take screenshots and record everything that appears on the device screen. Hence, if you have enabled OTP based passwordless authentication, the spyware can intercept the OTP.
Another dangerous type of cyber attack against passwordless authentication is known as a man-in-the-browser (MitB) attack. Here, the attacker inserts a special trojan into the web browser. This trojan not only intercepts all the data shared (including your OTPs, PINs, and other information), but it also changes the appearance of the browser, website, form fields, login fields, and responses received from websites. And to make matters worse, it can also delete all transaction entries.
Note: These disadvantages are applicable to only some specific passwordless methods, not all of them. For example, suppose you are using a PKI-based passwordless authentication to replace passwords for Wi-Fi, web/cloud applications, VPNs, Windows login. In that case, you don’t have to face most of the disadvantages mentioned above. It uses a public and private key pair. This is great because the private key never leaves the client, it can’t be stolen so long as you store it on a TPM, and it’s virtually impossible to guess.
All of this is to say that while one-time passwords and authenticator apps can be vulnerable to different types of malware (such as screen-reading malware), certificate-based authentication is malware-resistant so long as you use a TPM.
To learn more about PKI passwordless authentication, be sure to check out Sectigo’s eBook “Using PKI to Replace Passwords for Identity and Access.”
Wrapping Up on Passwordless Authentication
If you’re an employer concerned about the cybersecurity of your organization, applications, and website, passwordless technology is a solution you may want to consider. By deploying passwordless authentication, you’re providing greater security and convenience to your customers and employees (depending on how you deploy it). However, it’s important to remember that not all passwordless authentication methods are equal as some leave you more (or less) secure than others.
When you implement passwordless authentication using PKI client certificates (i.e., email signing certificates), you’re creating a strong security posture for your organization. And the extra benefit is that this method often is often more cost-effective than other passwordless authentication methods overall.














 (67 votes, average: 4.72 out of 5)
(67 votes, average: 4.72 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security