What Is a Computer Exploit and How Does It Work?
Would you sleep peacefully if your child monitoring app was leaking the location of your child? Probably not. The security flaws found in the Canopy app are the perfect example of vulnerabilities leading to worrying exploits. But what is a computer exploit, and how does it work?
Computer exploits are threats to both your organization and your customers when it comes to data security. Exploits are opportunities for cybercriminals to gain unauthorized access to your systems and data. But before we go into this topic more in depth, consider the following startling statistics.
The Ponemon Institute reports that in 2020:
- 51% of respondents said exploits and malware had evaded their intrusion detection systems,
- 49% said their antivirus solutions had been fooled, and
- 57% of the organizations polled worry that their remote workers are targets that bad actors can use to exploit vulnerabilities in their systems.
So, two important questions arise: what is a computer exploit? And how does it work? And what can you do to protect your organization against computer exploits?
What Is a Computer Exploit? Computer Exploits Explained
An exploit can be defined as an attack on an IT system or device that takes advantage of a hardware or software vulnerability. A vulnerability is a weakness of some kind — but we’ll speak more to the difference between a vulnerability and an exploit momentarily. But first, let’s consider a simple analogy of a car to help you better understand the concept of exploits better.
Imagine your car is in the parking lot at Target. As long as its doors are locked, it is generally considered safe. It’s not impossible to steal a locked car, but a thief will have to put in great effort to steal it. However, the story would be completely different if you had left a window slightly open.
The window is the vulnerability through which the thief can break into your car and steal it. But how would a thief enter through a slightly open window? Well, former car thief Steve Fuller told ABC News how he can pry open a window if he can stick his fingers through the gap.
Let’s compare this example to a computer exploit. If you have a vulnerability (the open window) in your software, hardware, application, or even your network, a bad actor can use their fingers (an exploit) to enter your system (your car) through that vulnerability.
What Is the Difference Between a Vulnerability and an Exploit?
Is there a difference between a vulnerability and an exploit? Yes, there is. Basically, a vulnerability is a flaw in your software or hardware that a criminal could use. This could be something as simple as having outdated software on your device.
You might not be aware that the flaw in your computer system is present, but cybercriminals could be. In fact, many cybercriminals run scans to locate devices, websites, and other assets that have specific vulnerabilities.
An exploit is a tool that helps a cybercriminal leverage this vulnerability to get into your system. An exploit can be designed to work on a particular vulnerability or on multiple vulnerabilities at once. It can also be customized to detect and use vulnerabilities in the system. Referring back to the car theft analogy, the open window represents the vulnerability and the bad guy sticking his fingers through it is the exploit.
How Does a Computer Exploit Affect Your Business?
If you own a small or medium business, you might wonder how computer exploits or exploit kits (which we’ll talk about later) could harm you or your business. Well, a business organization has many devices connected to its network. While this is helpful to the business owner, it also proves to be their biggest disadvantage as cybercriminals can launch attacks using any of them.
The impact of computer exploits on a small business can be listed as follows:
- Data collected and stored can be stolen and used maliciously
- Monetary losses can occur due to downtime and loss of business
- Reputation losses can occur as your reputation takes a beating
- Devices and equipment linked to the devices can become damaged or inoperable
Now that we know what an exploit is and why it’s so devastating for businesses, let’s dive into exploring how computer exploits work.
How Does a Computer Exploit Work?
Computer exploits are commonly introduced to a victim’s device through phishing emails, malicious applications, social engineering, or spear phishing. Once you fall for such emails, cybercriminals might be able to run the exploit program on your device. This exploit program is a way to crack your device security and gain entry, making way for the “real” (i.e., more devastating) malware. The rest of the work — or rather, the damage — is done by the malware.
However, for cybercriminals to be able to hack into your IT system, it needs to have a vulnerability. Without a vulnerability, it is almost impossible to hack your systems. As soon as the developers find out about a vulnerability, they release updates or patches to cover it. Developers also pay a bounty to users who discover dangerous flaws in their products. For instance, an Indian woman was paid $30,000 for finding a bug in the Microsoft Azure cloud system.
Many developers offer “bug bounties” to researchers and users who discover and report vulnerabilities and exploits. There are many legitimate hacker conferences and competitions to discover exploits in popular programs. One such competition is Pwn2Own by Zero Day Initiative. Thousands of dollars are paid in different categories of hacking various well-known products. These types of competitions encourage the hackers to work for the betterment of the software community as a whole and the safety of consumers.
By participating in legitimate competitions, the hackers can be encouraged to participate in white hat hacking rather than turning towards black hat hacking.
Black Hat vs White Hat Hackers Use Exploits — They Just Do So in Different Ways
Simply put, a white hat hacker is a person who hacks the software or the security systems of an organization to find the vulnerabilities in them. They are paid by the developers or the organization to improve the security. On the other hand, a black hat hacker works against the organization, hacking with malicious intent. So, the core difference between the white hat hacker and the black hat hacker boils down to intent and permission.
A white hat hacker will notify the company when they find a vulnerability so that it can be patched. In many cases, they’re even hired by the company to find vulnerabilities and exploits within their systems (i.e., they have the company’s permission). Conversely, black hat hackers aren’t authorized or given permission by companies to access their systems. Furthermore, black hat hackers don’t advertise or let anybody know of their exploits for the simple reason that the developers will patch the vulnerability as soon as they know about it. When the developers patch the vulnerability, the exploit becomes useless to the hackers.
A black hat hacker is a hacker who breaches the security and enters the IT systems of victims with malicious intent. Their destructive intentions make them criminals as opposed to the more ethical white hat hackers whose penetration testing and work aim to strengthen the organization’s security.
Once an exploit is discovered, it is added to the Common Vulnerabilities and Exposures (CVE) list. SonicWall 2021 Cyber Threat Report provides a list of the top eight of 18,353 CVEs published in 2020. Many of the top eight exploits affected multiple products.
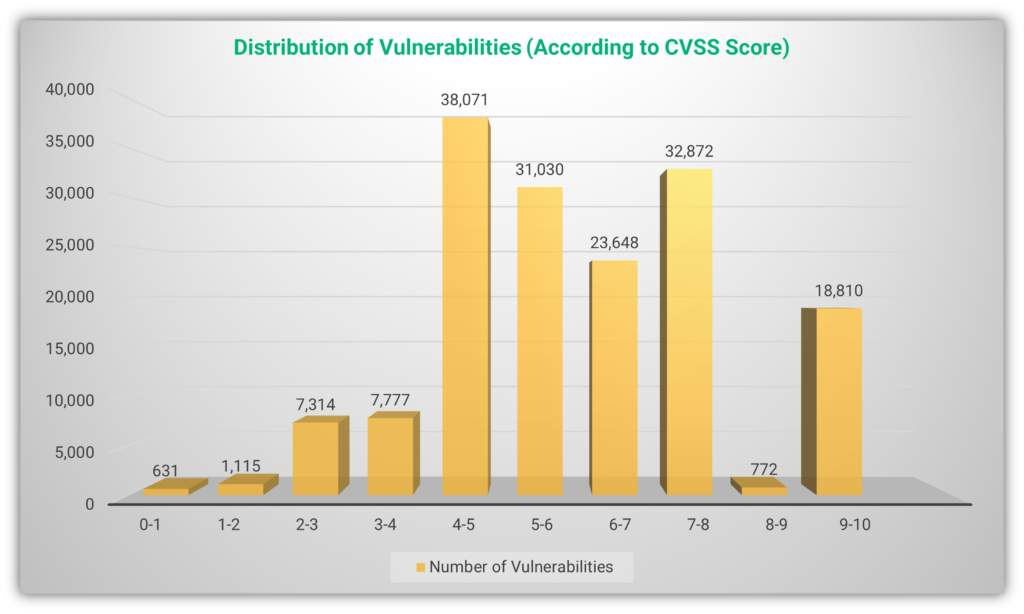
Currently, 11.60% of CVE vulnerabilities (18847 CVEs) have a common vulnerability scoring system (CVSS) score of 9-10. Higher score denotes increased risk. So, the scores suggest 18,847 (11.60%) of the vulnerabilities have highest level of risk. The following figure shows the figures from cvedetails.com as of Oct. 20, 2021:
What Are the Different Types of Computer Exploits?
So now we are clear that computer exploits are the tools with which hackers enter your computer devices to take advantage of a vulnerability. Exploits can be categorized according to the vulnerabilities they target. Let’s discuss briefly different types of exploits and some preventive measures for each:
Hardware Exploits
A hardware exploit is a term used when the cybercriminal uses a vulnerability in physical hardware components to gain unauthorized access to a system.
Vulnerabilities in hardware can lead to breached security and, ultimately, dire consequences. Many people think that cybersecurity has nothing to do with hardware; however, some hardware issues can lead to cyberattacks.
Hardware-based cyber attacks take advantage of the complexity of the integrated circuits (IC) and microelectronics to gain access to a user’s device without their knowledge or consent. Suppose a cybercriminal manages to change a small section of ICs during the manufacturing process. In that case, it might go unnoticed for years, and the criminal will get access to the devices of users installing that piece of hardware.
Additionally, users don’t often upgrade their hardware, which leaves them susceptible to attack.
How to Prevent Hardware-Based Attacks
- Upgrade your hardware regularly
- Ensure a dust-free environment for hardware
- Perform regular maintenance and upkeep of your hardware
- Don’t use outdated devices
- Restrict access to your hardware
Firmware Exploits
Another type of computer exploit that goes hand-in-hand with hardware exploits relates to firmware. A firmware exploit occurs when a cybercriminal takes advantage of a vulnerability that exists within an electronic component’s pre-installed software. Examples of firmware include control systems on washing machines, programmable thermometers, and computer firmware like BIOS, and run-time abstraction service (RTAS) on IBM computers.
In a firmware exploit, a cybercriminal uses malicious code to exploit a vulnerability within the firmware. This code can either create a backdoor in the system or uses a remote desktop protocol (RDP) to spy on the victim. The criminal might be able to set up a command-and-control (C&C) server to snoop and manage the victim’s device from a different physical location.
In short, a firmware exploit can cause as much harm as hardware exploit or a software exploit. The Ukrainian Power Gride Attack is an example of how an attack on firmware can affect an enterprise or a country as a whole.
Unfortunately, the industry still has to update a lot on the firmware security front. As we are discovering new vulnerabilities in the firmware, the manufacturers are introducing the updated software. However, we have a long way to go.
Software Exploits
A software exploit is an exploit that takes advantage of a vulnerability found in the software installed on the systems of the victim. For example, your device could be running on outdated software that has a known vulnerability. Even if the manufacturer released a patch, if you don’t take the time to apply the update, then an attacker can exploit that vulnerability to gain unauthorized access to your system and data.
Overall, there are seven stages of software development:
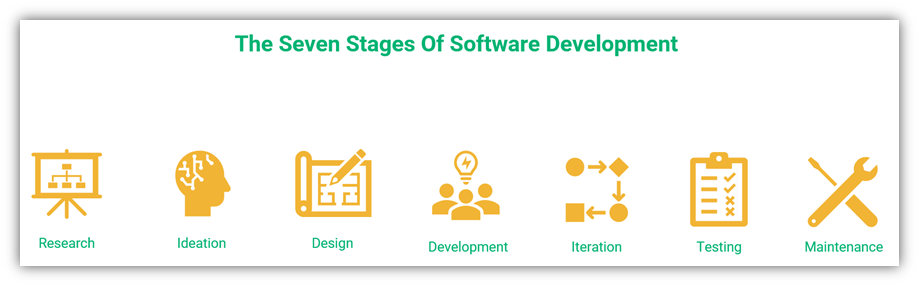
If there are any problems at any of the stages, cybercriminals might exploit them for their own benefit. From a basic design flaw to insufficient testing, from lack of sufficient auditing to poor follow-up maintenance, every mistake can lead to the creation of vulnerabilities. Obviously, doing everything by the book doesn’t guarantee 100% secure software, but following a comprehensive checking process can reduce the chances of an exploit.
How to Prevent Software-Based Attacks
Software vulnerabilities are not the responsibility of developers alone. Users also have to take responsibility for fending off attackers.
- Update your software regularly
- Use only licensed versions of software
- Limit the use of software to the personnel who need it
- Introduce appropriate security measures for logging in to any software
- Develop and communicate procedures to report issues
- Keep yourself updated on the latest attacks
- Delete unused and obsolete software
- Set up a system to revoke privileges from software not used for a certain period of time
Network Exploits
A network exploit uses a vulnerability in the network of the victim to breach their security. This includes vulnerability on any layer of the network, including physical, data link, transport, or internet.
EdgeScan reported that there was a 40% rise in remote desktop (RDP) and secure shell (SSH) exposure, probably resulting from increased remote working due to COVID-19. Organizations could make several errors while establishing and maintaining an internet network, leading to vulnerabilities. Criminals can then exploit insecure network architecture to deploy malware.
How to Prevent Network Attacks
Organizations should focus on the security of their own website by having an SSL/TLS certificate. An SSL/TLS certificate can not only show the legitimacy of your business but also helps to enable secure communications between a website and a user’s client. Without an SSL certificate, the website will be vulnerable to exploits from cybercriminals. The data in transit is up for grabs if it’s not protected by an SSL/TLS certificate.
- Secure networks with strong password policies and ensure they are discoverable by authorized people only
- Use a different network for guests
- Build a zero-trust organizational structure
- Keep records of employees’ activity on the network
- Secure your sites with SSL/TLS certificate
- Train employees to use healthy network habits
Personnel Exploits
When cybercriminals make use of vulnerabilities created by the employees of an organization, or they target the employees to phish sensitive data, the exploit is said to be personnel-based. Verizon reports that 44% of data breaches in small organizations were due to internal actors. The breaches were not only the result of espionage but also due to sheer negligence. Sometimes the ‘oops’ moments of employees cost almost as much to the organization as employee espionage.
Let’s quickly explore three of the risks:
- Having insufficiently trained employees performing technical jobs increases your attack surface. Non-technical employees might not recognize vulnerabilities in software/hardware even if they see it. They may also not be aware of the latest exploits in the market and may not be ready against zero day exploits. These users are less likely to follow cybersecurity best practices and may fall for phishing scams.
- Employees making minor misconfigurations can cause big problems. Poor cyber security planning and implementation processes can result in big issues for organizations.Implement cyber security policies and procedures that spells out what employees should — and should not do — regarding company devices and BYOD devices that connect to your network. Even a small slip-up can open up the doors for a cyber attack or data breach.
- Unhappy or manipulated employees can misuse their access. A disgruntled employee might work with a malicious outsider to get back at their employers, and manipulated or blackmailed employees might wind up doing the same for different reasons. The end result is that they can pass on sensitive information or might actually share the vulnerabilities in the system that external threats can use.
How to Prevent Personnel Exploits
- Conduct employee training sessions regularly
- Employ appropriately trained people to work jobs that require handling sensitive data
- Document procedures for employees to follow
- Implement strict access and use policies
- Address employee grievances on a regular basis
- Compensate employees at market levels
- Restrict access to sensitive systems and data to only those who need it for specific tasks
Organizational Exploits
In addition to personnel and faulty IT systems, organizations might become victims to computer exploits if they don’t follow some of the basic principles of cyber security. Some of these principles are as follows:
- Set up the most secure IT system you can afford
- Employ people to operate those systems well
- Set out rules for protecting the systems and mandate your employees to follow them
- Form concrete plans for cyber security and follow them exactly
- Perform regular internal and external audits to find vulnerabilities in your system
If the organization follows these security rules, it will reduce the chances of computer exploits and malware attacks.
EternalBlue: An Example of a Real-World Exploit and Its Role in Cyber Security:
StatCounter reports that as of September 2021, 75.4% of desktop computers use Microsoft Windows. Now, if Windows had a vulnerability and someone developed an exploit for it, these devices would be vulnerable to attack. This is exactly what happened when the National Security Agency (NSA) developed a hacking tool called EternalBlue that used a vulnerability in legacy Windows operating systems.
EternalBlue exploited the server message block (SMB) protocol of Microsoft’s legacy systems. Microsoft released a security patch for the vulnerability in March 2017 but, unfortunately, a hacker group called the Shadow Brokers leaked it to the world soon after in April. Despite the fact that Microsoft had released the patch for the vulnerability, many users didn’t update it in time and faced the consequences. The following exploits took advantage of EternalBlue:
WannaCry
WannaCry attacked users on May 12, 2017. It is considered one of the most intimidating exploits of all time. Microsoft released an emergency patch for previously unsupported operating systems (OS) the very next day, but some users still didn’t update their OS due to neglect, lack of knowledge, or procrastination.
WannaCry was ransomware that used EternalBlue exploit to creep into user devices. The criminals demanded ransom in Bitcoins. Security experts from the U.S. and U.K. think that WananCry originated from North Korea, and the attack is said to have affected more than 200,000 devices in 150 countries. It is considered particularly damaging as it included a transport mechanism that enabled it to spread automatically. The total damage was caused by WannaCry is not determined but is estimated to be between millions to billions of dollars.
NotPetya
The interestingly named NotPetya has many similarities to a previous piece of ransomware named Petya. Petya and NotPetya encrypted the victim’s hard drive, restricting their access until the ransom was paid. However, unlike Petya, NotPetya didn’t decrypt files upon the payment of the ransom.
NotPetya was a state-sponsored Russian cyber attack deployed to hurt Ukraine in 2017. However, it got out of hand and victimized large corporations worldwide, including Russian state oil company Rosneft. NotPetya caused estimated damage of billions of dollars, affecting numerous countries, including the U.S., U.K., Ghana, Russia, and of course Ukraine. The U.S. government formally called the attack “reckless and indiscriminate.”
BadRabbit
BadRabbit ransomware preyed mostly on devices in Russia, Germany, and Ukraine, and manually used a ransomware dropper from a single server. The attack began on the morning of Oct. 24 2017, and by late evening the dropper server went down. During its course, it affected about 200 devices.
BadRabbit encrypted the victims’ files using RSA 2048 and AES 128 CBC protocols. It was found that the victims were redirected to a malware site from a legitimate news website. Thereafter, a fake Adobe Flash Player was used to deploy the code of the malware.
What Are Exploit Kits?
Over the years, we’ve seen a steady rise in malware attacks that make us ask, “are so many people suddenly mastering the evil skill of developing malware?” Well, no. Not everybody who launches malware attacks actually developed the malware themselves. Oftentimes, cybercriminals make use of “crimeware,” including malware-as-a-service (MaaS) and exploit kits. So, what are exploit kits?
Exploit kits are tools that contain multiple exploits. These kits helps the criminal launch cyberattacks without having to go to the effort of programming individual malware and exploits. They can readily buy exploit kits from the dark web to launch attacks. This has led to an increase in cyber attacks all over the world. Recently, PurpleFox malware, a type of malware that infects Windows systems, was discovered as being distributed through exploit kits.
Depending on the services provided, the going rates that criminals charge for exploit kits vary on the dark web. Some exploit kits can not only install exploit and malware on the device but can also look for vulnerability in the software and provide the appropriate type of exploit. Once inside, the exploit kit might also launch a remote access tool (RAT), which gives the attacker remote access to your system.
The monetization of malware-as-a-service can be linked to the release of the Blackhole exploit kit back in 2010. Very much like software-as-a-service, Blackhole provided a ready-made kit to deal with every stage of an exploit attack in one place. The Russian distributors also offered customization of the kit to meet specific requirements of the users.
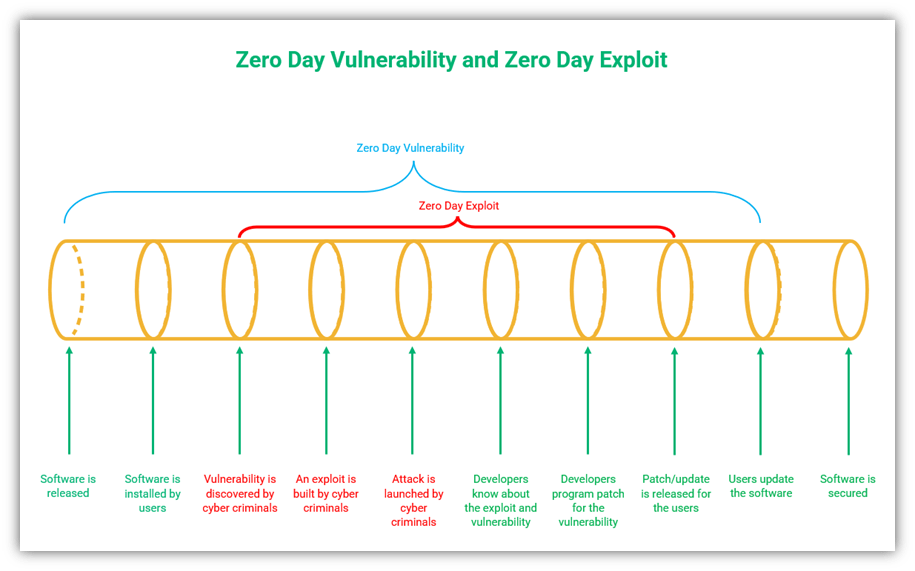
What Are Zero Day Exploits?
A zero day exploit is every developer’s worst nightmare. This is a vulnerability in your computer program that’s unknown to your organization —you can’t fix problems you don’t know exist, right?
Developers issue patches and updates to address flaws and other vulnerabilities they discover in their software (or that researchers and white hats report to them). However, there are times when researchers and cybercriminals discover the vulnerabilities before the developers. It’s good when researchers find them because they’re on your side and want companies to take care of the issues before they become problems. But it’s horrible when cybercriminals discover them first because they exploit the vulnerabilities to launch attacks, taking everybody by surprise.
A cyberattack launched using an unknown or undisclosed vulnerability is called a zero day attack. These types of attacks take advantage of what’s known as a zero day exploit or vulnerability. So far, zero-day.cz reports that this year has seen almost double the number of zero day exploits in nine months than during the whole of 2020.
Zero day exploits are sold for millions of dollars on the dark web if they are not used directly by the people who discover them. In a shocking incident, Accuvant, an American security company, sold an iPhone exploit to a group of mercenaries for $1.3 million. Reuters reports that this hack was ultimately used by the United Arab Emirates (UAE) to launch surveillance and espionage against geopolitical rivals, dissidents, and human rights activists. Another example is a zero day vulnerability in the Virgin Media Super Hub 3 router that exposed the true IP addresses of VPN users, damaging their privacy.
Thankfully, white hats at Google have developed a Google sheet to keep track of the zero day exploits they discover and help fellow experts. The project is dubbed “Project Zero” and its goal is to make using zero day exploits harder for attackers to achieve. The Google team tracks their own security resources along with the zero day exploits they discover in the wild.
Even so, as a business owner, the onus is on you to keep your IT systems secure and updated. Abandoned or obsolete software is often targeted for zero day exploits.
Final Words on What a Computer Exploit Is and How It Works
Computer exploits are programs devised by cybercriminals to take advantage of the vulnerabilities in your IT systems. As much as the software developers try to develop vulnerability-free programs, it is virtually impossible for them to do so. Cybercriminals are also experts in programming, and they find every little vulnerability to exploit and launch malware in your devices and systems.
A business organization provides a large area for exploiting vulnerabilities, and therefore small and medium-sized businesses (SMBs) must be extra vigilant for their cyber security regimen.



















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security