Code signing is the process of getting your code signed digitally by a trusted certificate authority (CA). The CA verifies the identity of the author or publisher who submits the software and assures end-users that his identity has been validated. Although this process is pretty straightforward conceptually, there are some code signing best practices that you can implement to make the process a little smoother and more effective. We’ll jump into some of those code signing best practices for Microsoft in particular shortly.
Before you can start using best practices, though, you first need to have a code signing certificate. If you haven’t already bought a code signing certificate, depending on your requirements and budget, you can purchase one from us at discounted rates. You can get either a standard code signing certificate or an EV (extended validation) code signing certificate that bypasses the Microsoft SmartScreen filter.
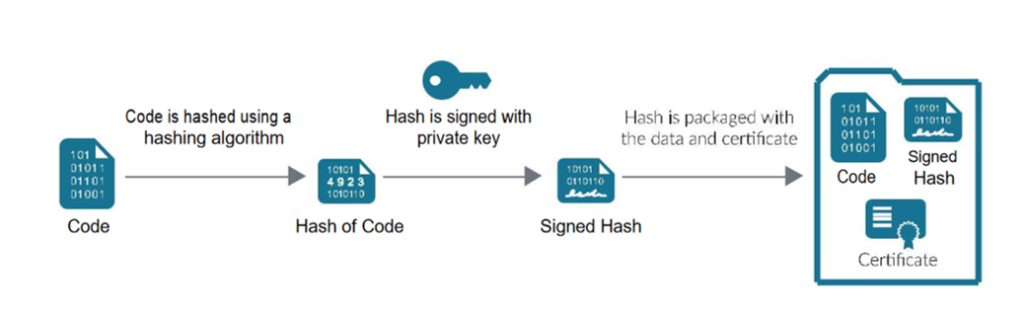
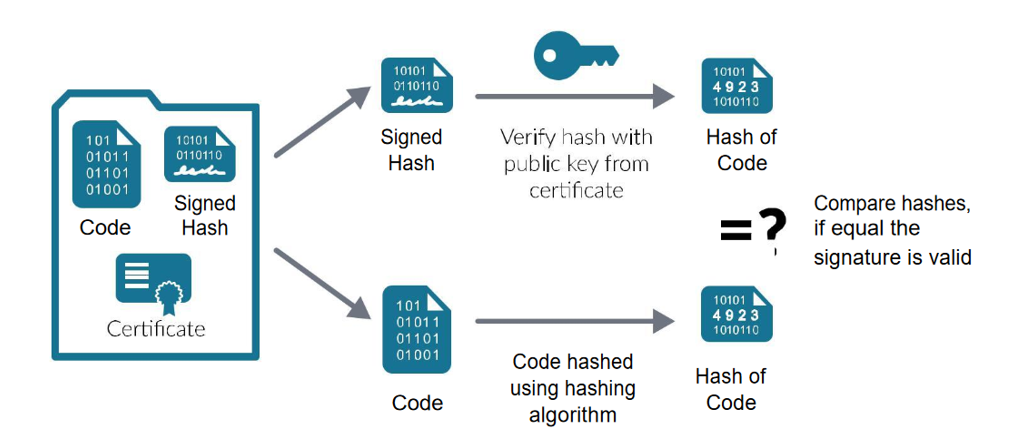
Code Signing Best Practices
Let’s take a look at the code signing best practices outlined by the CA Security Council in its white paper:
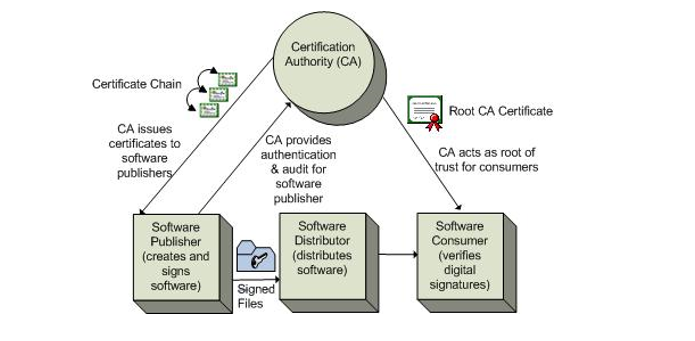
Code Signing Best Practice One: Restrict Access to Private Keys
Only authorized personnel should be granted access to computers with the code signing keys. Proper care to enforce access control using physical security solutions alongside their software counterparts can help to establish strict accountability for the use of private keys.
Code Signing Best Practice Two: Store Private Keys with Cryptographic Hardware Solutions
- As a minimum protection standard, use a Federal Information Processing Standard (FIPS) 140-2 Level 2 certified cryptographic device. These devices do not permit the private key to be exported.
- Using an EV code signing certificate necessitates storing the private key generated in a cryptographic hardware device (smart cards, USB tokens, etc.).
- Physically secure the device in a locked cabinet and ensure that it’s not left lying around, inviting the possibility of theft.
- Ensure that the hardware device holding the private keys is protected with a strong randomly generated password at least 16 characters in length that contains uppercase and lowercase letters, numbers, and special characters.
- Microsoft code signing best practices also recommend the destruction of these private keys either by overwriting the devices or physically destroying them.
Code Signing Best Practice Three: Always Timestamp Your Code
- Timestamping extends the trust beyond the validity period of the code signing certificate. It enables the code to be verified even after the certificate has expired or been revoked. The revocation is dependent on a specific date and signatures issued before the revocation date remain valid.
- Timestamp certificates can be issued up to a maximum validity period of 135 months.
Code Signing Best Practice Four: Note the Difference Between a Test-Signing Certificate and Release-Signing Certificate
- A test signing certificate is used to sign prerelease builds of software and are trusted only within the test environment. The test signing certificate can be self-signed or be signed by an internal CA who is trusted within the internal corporate network.
- A release signing certificate is used to sign the production code that will be shipped to end-users. Users across the globe will trust the root certificate used to sign this publicly released build.
- Set up a separate code signing infrastructure to sign the prerelease code. Test-signing private keys and certificates, therefore, require less stringent security access controls than release signing certificate and keys
Shop for Code Signing Certificates – Save 53%
Save 53% on Sectigo Code Signing Certificates. It ensures software integrity with 2048-bit RSA signature key.
Code Signing Best Practice Five: Authenticate the Code to Be Signed
- Any code submitted for signing needs to be authenticated before it is signed and released.
- According to Microsoft code signing best practices, a streamlined process for submission and approval of code should be implemented to stop unapproved or malicious code from being signed.
- For maintaining audit logs, and for escalation of incident-response cases, keep a record of all code signing activities.
Code Signing Best Practice Six: Scan the Code for Viruses Before Signing
- Code signing verifies the identity of the publisher but not the nature or quality of the code. It merely gives assurance that the software has not been tampered with after the author last signed it.
- Malicious snippets can be introduced, especially when incorporating code from other third-party sources. As a precautionary measure, it’s essential to run virus scans to help improve the security of the released code.
Code Signing Best Practice Seven: Revocation of Compromised Certificates
• If there is a security breach, the issue needs to be reported to the CA. It might necessitate the revocation of the code signing certificate.
• If your code has been timestamped, the revocation date can be set to before the breach occurred. This implies that the code signed before the revocation date has not been impacted.
• If further clean code is released, the revocation will impact this code as well. It can be eliminated by changing keys and certificates to avoid conflicts and distributing the risk with multiple certificates.
OV vs EV Code Signing Certificate
| Features | Sectigo Code Signing | Sectigo EV Code Signing |
|---|---|---|
| Certificate Authority | Sectigo | Sectigo |
| Certificate Type | OV Code Signing | EV Code Signing |
| Validation Type | Organization Validation | Extended Validation |
| Multiple year options | Yes | Yes |
| Encryption strength | 256-Bit SHA-2 | 256-Bit SHA-2 |
| Issuance Time | 1 to 3 Business Days | 1 to 5 Business Days |
| Immediate Reputation with Microsoft’s SmartScreen Filter | No | Yes |
| Two-factor Authentication | No | Yes |
| Microsoft Authenticode Signing | Yes | Yes |
| Android Apps Signing | Yes | Yes |
| Apple OS X Signing | Yes | Yes |
| Java Signing | Yes | Yes |
| Apple OS X Signing | Yes | Yes |
| Microsoft Office VBA Signing | Yes | Yes |
| Adobe Air Signing | Yes | Yes |
| Windows Vista x64 Kernel Mode Signing | Yes | Yes |
| Windows Phone Apps Signing | Yes | Yes |
| Qualcomm Brew App Signing | Yes | Yes |
| Microsoft Office Document Security | Yes | Yes |
| Free Re-issuance | Yes | Yes |
| Support Options | Yes | Yes |
| Refund Policy | 30 Days | 30 Days |
| Lowest Price | From $79/year | From $289.67/year |
| Buy Now | View Product | View Product |

 (4 votes, average: 4.00 out of 5)
(4 votes, average: 4.00 out of 5)