Cybersecurity for Startups: 10 Cybersecurity Tips to Implement Now
In honor of National Cyber Security Awareness Month, here are 10 essential cybersecurity tips for startups to protect your website, devices & data
We all know cybersecurity for startups is crucial, but it often takes a back seat because of budgetary concerns. And that’s pretty obvious because it takes a massive investment to hire cybersecurity consultants and buy sophisticated security tools. This is where having some useful cyber security tips can help. There are things you can do for free (or at a low cost) that will increase your cybersecurity for startups.
In this article, we’ll introduce you to some ready-to-implement tools and techniques that you can deploy in your startup right away. Some cybersecurity tips will need basic programming knowledge. But no worries — we’ll link to some great resources from which you can simply copy-paste codes.
Achieve Cybersecurity for Startups With These 10 Cyber Security Tips
Whether it’s because of budgetary concerns or a lack of personnel or other resources, cybersecurity for startups is a critical function that budding businesses often neglect. That’s why we’re here to help you correct course sooner rather than later.
A couple things that every startup should already be doing is using antivirus and anti-malware software on endpoint devices. However, there are other things that you can do in addition to that to secure your network, devices, website and data.
Each of the following 10 cyber security tips for startups include links to tools, software, applications, plugins, guides and other resources. These are the combination of free, “freemium” and paid (low cost) tools.
1) Install a Malware Scanner & Web App Firewall on Your Website
These scanners continuously monitor your website for cyber attacks and malware insertions. They monitor your website 24/7 and detect, block, and provide guidance about how to remove some of the most critical the cyber threats.
Of course, not all scanners and firewalls are made equally, and that’s why you should choose only a robust and trusted one. For example, Comodo’s cWatch Web is one of the most efficient, yet affordable managed security services for websites and apps in the industry. Its comprehensive security-as-a-service (SaaS) offerings includes website scanning, malware removal, and advanced threat protection via a web application firewall (WAF).
2) Secure Your Website’s Login Fields
This next tip on cybersecurity for startups is something that’s often overlooked. It’s likely that you have a lot of users and stakeholders with accounts on your website. This may include employees, customers, vendors, suppliers, and others as well. Hackers like to exploit vulnerable login fields to bypass the authentication mechanism and enter your website. That’s why you must ensure that your login fields are secure by following these cybersecurity tips for startups.
1. Include Your Login Portal or Fields on HTTPS Sites Only
One of the biggest mistakes people tend to make is hosting their login portal on an insecure page. Whether it’s a standalone login page or a field that’s included on your site’s home page, make sure that you’re using a secure, encrypted connection. By using an insecure HTTP site, any login information or other data you or your customers enter on your website will be vulnerable to hackers.
To avoid this issue, install an SSL/TLS certificate on your website. We’ll talk more about using SSL/TLS certificates later in this article.
2. Force Users to Create Strong Passwords
People tend to make easily guessable and weak passwords. Why? Because it’s easy. And to make matters worse, many people — 66%, according to Google and Harris Poll — are known to reuse passwords across multiple accounts! So, what can you do to ensure that you and your employees are using the strongest passwords? Check out these resources for how to force them to make strong passwords:
For WordPress sites: Use plugins like Password Policy Manager or Force Strong Passwords to ensure users create strong passwords.
Here are some useful and informative resources for enforcing strong passwords on the following platforms:
- Debian, Ubuntu
- Linux
- Web Host Manager (in cPanel)
Also, check out these coding to implement strong password policies using JavaScript.
3. Limit the Number of Login Attempts Allowed
Every year, billions of credentials get exposed via data breach incidents. Riskbasedsecurity.com reports that 8.1 billion records got leaked in the first quarter of 2020 alone. Attackers buy millions of credentials from the dark web (often at little to no cost) to execute brute force attacks. In this type of cyber attack, a hacker uses a bot to auto-fill login fields with a pre-guessed database of user ID and password combinations until it finds a successful combination.
One of the best ways to protect against a brute force attack is to limit the number of login attempts a user can make within a specific period. After the pre-determined number (generally between three and five) of failed login attempts, the system temporarily blocks the user’s IP address for a set time period.
To limit logins through the use of plugins or code, check out the following resources:
- For WordPress sites: Use plugins like Limit Login Attempts, Loginizer,orWPS Limit Login.
- For non-WP sites, use the following resources: Limit login attempts in HTLM and JavaScript and PHP and MySQL.
Here’s another great resource: You can use haveibeenpwned.com to check out whether your (or your employees’) company email accounts have been exposed in any data breach incidents.
4. Implement 2FA/MFA or Passwordless Authentication Solutions
There are some sophisticated cyber-attacks like botnet attacks that can bypass the authentication mechanism even when the limit login attempt feature is active. Plus, attackers use social engineering and phishing attacks to steal users’ credentials.
That’s why you should enable two-factor authentication (2FA) or multi-factor authentication (MFA) in your login fields. The users will receive a one-time password (OTP), secret pin, or a unique link on their registered mobile phone or email address every time they want to login.
You can also use tools such as Google 2-Step, Google Authenticator (plugin for WordPress sites), Twilio, Authy, etc. to enable 2FA/MFA. Read more about the technical components of deploying 2FA on your website.
There are some other passwordless authentication methods, too, such as biometrics, QR codes, and hardware security tokens. It is important to note, however, that while some of these options can be expensive, though not all. For example, client authentication certificates can be cost effective (we’ll speak more to that later in the article).
To learn more about passwordless authentication, check out our article on the topic.
5. Prevent SQL Injections
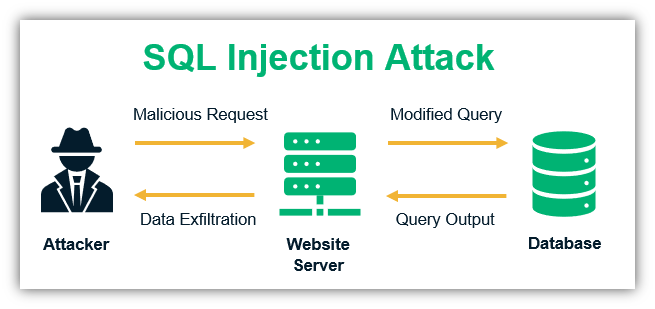
SQL injection attacks are major concern for site owners and admins. In fact, they’re among OWASP’s top 10 vulnerabilities. Hackers install malicious codes in the input fields that help them access your databases. This technique is known as SQL injections. With SQL injections, the hacker can insert the malicious codes in your databases, steal the data or even hijack the database for a ransomware attack. You must restrict the input values on the fields.
To start, use an open-source platform like SQLMap to detect SQL vulnerabilities in the system. Then follow the cybersecurity tips provided in this article that details how to prevent SQL injection attacks.
3) Secure Data and Communications with Encryption
This next item on our list of cybersecurity tips for startups is crucial. All types of data are critical to the success of your business — customer information, proprietary information, trade secrets, etc. The devices such as PCs, laptops, tablets, and cell phones that employees use to do the office work contain all the confidential business information. That’s why you must protect these devices with the use of encryption technology.
Here, we’ll go over how to encrypt files and folders. We’ll also talk about how to protect your data both when it’s at rest and in transit in subsections 4 and 5.
1. How to Lock Files and Folders
Educate your employees to encrypt the essential files and folders. You can use free encryption software like Folder Lock, 7-Zip, VeraCrypt, AxCrypt, DiskCryptor, etc. for this purpose.
You can also use Window’s in-built encryption feature to encrypt files and folders:
- Navigate to the folder/file you want to encrypt.
- Right-click on the item. Click Properties, then click the Advanced button.
- Check Encrypt contents to secure data.
- Click OK, then Apply.
- Windows then asks whether you wish to encrypt the file only, or its parent folder and all the files within it as well. Select the appropriate option and proceed.
2. How to Lock Windows Using BitLocker
- Go to Control Panel.
- Click on BitLocker Drive Encryption.
- Click “Turn on BitLocker” next to the drive (generally C: and D: drive) you want to encrypt.
- Enter a unique password or passphrase and start the encryption process.
Note: You can encrypt the USB drive, too, using BitLocker: Read more on how to encrypt USB drives using BitLocker.
3. How to Encrypt Mac Laptops and Tablets
- Choose Apple menu
- Go to System Preferences
- Click Security & Privacy and then FileVault.
- Click Locked and enter the admin ID and password.
- Click Turn on FileVault
Note: For iPhones, there is no separate encryption option is available. When you set your password or fingerprint lock, your iPhone automatically enables the encryption feature.
4. How to Encrypt Email Communications
The FBI’s Internet Crime Complaint Center (IC3) received nearly 24,000 business email compromise (BEC) complaints with adjusted losses topping $1.7 billion in 2019 alone. Hackers can use phishing emails to pose as one of your company’s employees or executives. They can also intercept email content when the data is in transit or stored on the email client if it’s not encrypted.
The best way to protect your email communications is to install email signing certificates on all your employees’ devices. These certificates, which are also known as personal authentication certificates or PACs, are inexpensive and yet highly valuable from a security point of view. An email signing certificate enables users to attach their digital signature onto their email communications, which can’t be replicated, removed, or otherwise tampered with. Hence, when you send an email that’s signed by an email signing certificate, it assures the recipient that you are who you claim to be.
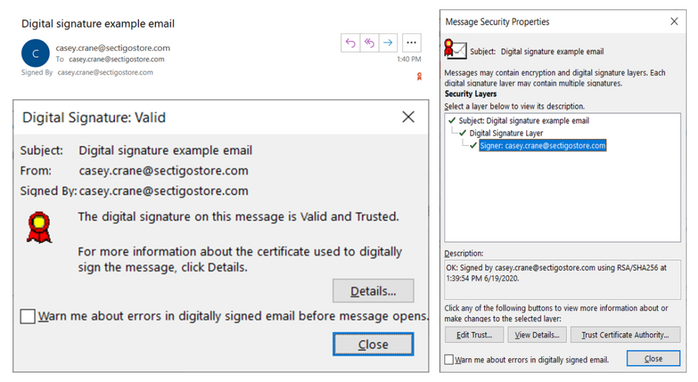
These certificates also enable you to encrypt your email data before sending it. So long as your recipient also has an email signing certificate involved, this process allows you to exchange encrypted emails easily and efficiently. What this does is keep your email content secure and away from prying eyes while the data is “at rest” (sitting) on your organization’s server.
5. Encrypt Data Transmission Between Your Website Visitors and Server
When your customers submit data to your site (such as their names, email addresses, passwords, payment card details, tax-related information, etc.), that data is sent in plaintext. When the data is in transit from the user’s browser to your website’s server, a hacker can break into the weak internet connection and intercept all the data. This is known as a man-in-the-middle attack, and it can cause a lot of problems for you and your customers.
Remember how earlier we talked about installing an SSL/TLS certificate on your website to make it more secure? This certificate enables your customers and other site visitors to connect to your site via a secure, encrypted connection. (You know the “HTTPS” that you sometimes see in your browser’s web address bar? We’re talking about that.) Basically, it encrypts the data in transit using public key encryption.
After installing an SSL/TLS certificate, the browsers will show a padlock sign in front of your domain name, which indicates that your website is secure for data transmissions.
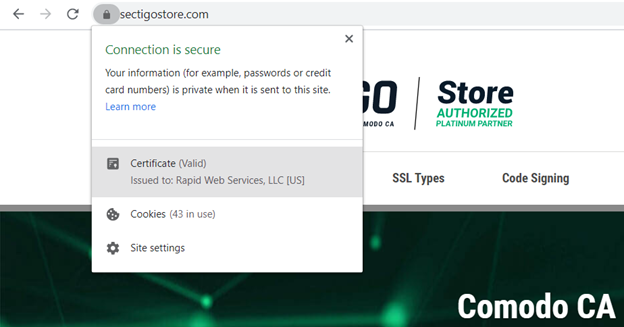
Without an SSL certificate, all the browsers will show a “not secure” sign in front of your domain name in the address bar. As such, it means any data shared via that insecure connection will be vulnerable to hackers who can use that data for ransomware attacks, or to commit financial fraud or identity theft. Either way, this spells bad news for you and for your customers.
4) Enable DNS Filtering to Protect Your Network & Devices
This next cybersecurity for startups tip is a little more technical because it involves the domain name system, or DNS. The DNS is the way through which you access websites on the internet. Every website has a corresponding server IP address, but these numbers are hard to remember — this is why we use domain addresses like domain.com. So, every time you type in a website address (such as SectigoStore.com), your browser uses DNS servers to connect to the site’s corresponding IP address for you automatically.
DNS filtering is a feature that blocks malware-laden, spammy, and phishing websites at the DNS level. As a trickle-down effect, this protects your organization’s network and connected devices. You can do this by creating blocklists or allowlists that will either block or allow the website to load depending on the settings. You can filter by either domain name or IP address.
There are many different commercial and free DNS filtering services out there that you can choose from. For example, you can change the DNS setting using the free solution Quad9, or use paid DNS filtering tools like DNSFilter, WebTitan, or Darklayer GUARD. These solutions providers maintain lists of malicious websites. You can also add websites that you want to block. Some companies use DNS filtering to block social media sites or other sites that can distract employees.
DNS filtering is important because some websites are so dangerous that they automatically download harmful drive-by malware like viruses, ransomware, spyware, the trojan horse onto users’ devices without the users noticing.
Once an employee’s device gets infected with malware, the hacker can:
- Intercept confidential data,
- Monitor all the actions,
- Send phishing emails to others using employees’ corporate email address,
- Steal credentials,
- Corrupt other connected devices to spread malware, and
- Cause many other types of harm or damage.
5) Use Vulnerability Scanners to Identify Gaps in Your Cyber Defenses
A vulnerability scanner simulates cyber attacks on server to find the vulnerabilities in the server, website, applications, plugins and databases, without harming your website.
Vulnerabilities mean bugs or weak areas of a software’s security defenses or code that cybercriminals can exploit. Vulnerability scanners scan your servers, databases and other areas, and detect vulnerabilities to help you stay one step ahead of hackers. This way, you can fix any vulnerabilities before hackers can find and exploit them.
Use software like ThreatRunner, WireShark, or Zed Attack Proxy for vulnerability scanning.
Note: If your website accepts online payments, you must use a PCI approved scanner such as HackerGuardian.
6) Use Passwordless Authentication Methods to Authenticate Employees Remotely
This little-known cybersecurity for startups method is a real gem. If you want to ensure that only your employees have access to your website or network, there’s a way to do that. You can install email signing certificates on all your remote employees’ devices.
But, wait, didn’t we say earlier that email signing certificates were useful for signing and encrypting emails? Yes, they are. However, these certificates also serve another purpose: client authentication. This is why email signing certificates, which are also known as personal authentication certificates (or PACs), are also known as:
- Client certificates,
- Device certificates, and
- User certificates.
What these certificates do is ensure that employees can access the company’s resources only when they log in from devices that have the certificates installed (and the corresponding private key is stored). Hence, even if hackers steal the remote employees’ credentials, they can’t access anything on the company’s server because they wouldn’t have access to the certificate or the private key. (Because the authentication is done via private keys, which is stored on the employee’s official device only and can’t be stolen or guessed easily.)
Using a client certificate for authentication is a passwordless authentication method. When employees try to access company’s locked resources, the server automatically verifies the device through the client certificate. Tim Callan, Senior Fellow at Sectigo, says that using a client authentication certificate in conjunction with a TPM (trusted platform module) actually makes authentication more secure than using phone-based MFA methods.
7) Be Vigilant About Network Security
When we talk about cybersecurity for startups, securing your network is something you should never overlook. You can secure the communication between your users and server with an SSL/TLS certificate, but there are some other loopholes related to the internet, too.
Follow these cybersecurity tips for the best network security practices:
- Block unused internet ports on the router and disable network bridging (so outsiders can’t exploit your internet connection to break into your network).
- Enable encryption on your router to prevent data leakage.
- Disable Wi-Fi protected access (WPA) as it has some known security flaws. Instead, enable WPA2 / WPA3, which uses more secured algorithms like AES for encryption.
- Change the default login credentials and the SSID broadcast name.
8) Maintain Multiple (Current) Copies of Data Backups
Your data is only as good as its backup. If something happens to your website or servers and you don’t have a backup in place, you’ll find yourself in deep water. Data backups are the way to get your business up and running again in the event of a cyber attack or another disaster.
Taking the website’s backup is different than taking backups of your PC or smartphone. There are following precautions you must take while taking your website and databases’ backups.
1) Enable Automated Backups
Don’t rely to your or your employees’ memories when it comes to maintaining current backups. Use a tool or solution that automatically create backups of your website’s files and data on a regular interval and also deletes the old, outdated backups.
2) Store Backups in Multiple Locations (Including a Third-Party Cloud Platform)
While having on-site storage of backups is good, you should never save backups on your public-facing server or your/employees’ local devices. When attackers get into your server, they can access all your data, including the backup copies. This is why you should also store your data backups off-site via a third-party cloud platform like AWS, Google Drive, Dropbox, etc.
Use the 3-2-1 data backup rule as part of your data security strategy. According to this rule (which is more of a strategy):
- Create three copies of your data (one primary copy and two backups),
- Store your copies in at least two types of storage media, and
- Store one of these copies off-site on a trusted and secure third-party cloud platform.
3) Scan the Data Before Taking Backups
Scan all the components and databases with a robust anti-malware scanner before taking backups. This is highly important. Suppose a hacker infects your website with malware and you inadvertently restore the website by using the malware-infected backup. In this kind of situation, your backups won’t be helpful when you actually need them. This is why it’s important to use a solution that regularly scans your website before creating backups.
Recommendation: A backup solution like CodeGuard can simplify this process for you. CodeGuard automatically creates backups, stores them on a trusted third-party platform, and also scans the website for malware before taking the backup. You will also get free space on the reputed cloud platform like AWS.
9) Educate Your Employees About Cyber Security Threats & Best Practices
Next on our list of tips on cybersecurity for startups: Make your employees vigilant and let them know about cyber threats. A small human error, a wrong click, or a wrong download is enough to make your company a cyberattack victim.
Educate Employees About Phishing Attacks
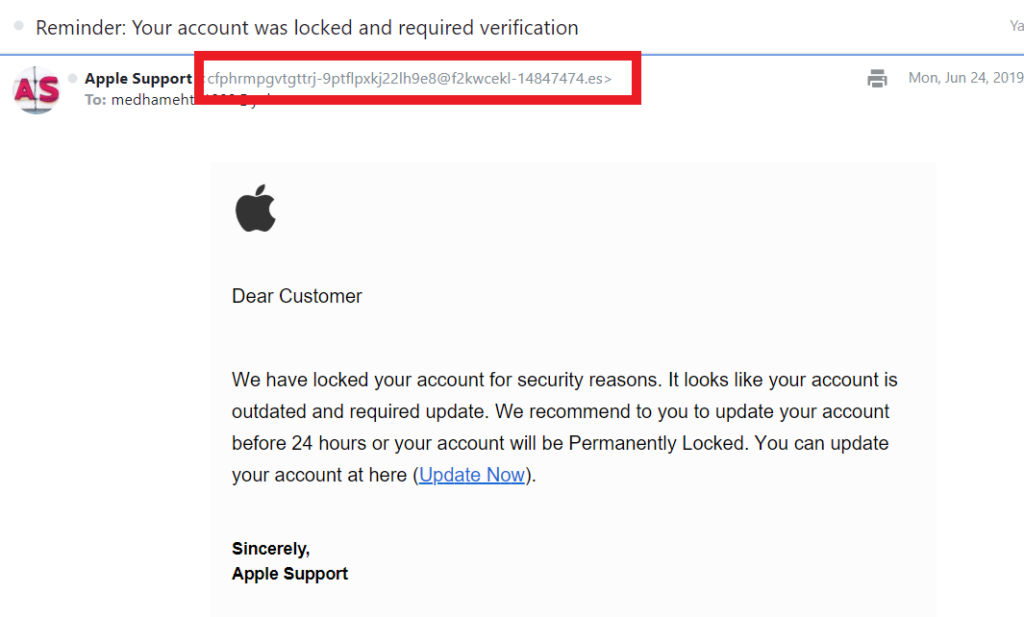
In phishing attacks, attackers disguise themselves as legit companies or people to trick their targets into doing something. This could be anything from giving them their login information to sending sensitive or proprietary information.
Phishing can occur via email, SMS text message scams (smishing), phone calls (vishing), or even through fake websites. To help your organization avoid falling prey to these tactics, teach your employees to recognize the phishing scams and not to share any personal or professional info and download anything.
Check out these resources to learn more about phishing attacks and other related tactics such as:
Make Sure Your Employees Use a VPN
Hackers and advertisers can track you or your employees’ IP addresses and eavesdrop their actions (such as by seeing what sites they commonly visit). From these records, hackers can plan a targeted phishing attacks, social engineering attacks and other types of cybercrimes. By following employees’ online activities, people can also get predict information regarding your confidential suppliers, resources, strategies and much more.
One way to prevent this is to install a VPN on all the employees’ devices and require them to use it. A virtual private network (VPN) is software that hides your real IP address and also encrypts all the online communication. VPN wraps your original IP address under a layer of a new IP address and provides an encrypted tunnel to transmit the data.
Inform Them About Trojan Horses:
A trojan horse (or what’s commonly known as a trojan) is malicious software that looks legitimate. When you download a trojan, it infects your device, steals all your data, and execute dangerous cybercrimes. Use this article to help employees recognize a trojan so that they don’t download it intentionally or inadvertently.
10) Keep Everything Patched and Up to Date
There is a widespread misunderstanding that the updates manufacturers and developers release are there just to tweak appearance and features of the software. Sometimes, people avoid using updated versions because some free applications, plugins and themes providers force the users to update their free version to paid ones to access the updates.
What people with these misconceptions are missing here is that the old versions generally have security flaws that hackers can exploit. The developers fix these flaws by releasing patches and updated versions of their software. Hence it is one of the most important cybersecurity tips to install the new patched versions of plugins, applications, themes, operating systems, and all other technical components as soon as new updates are available.
Final Words on Cybersecurity for Startups
The above cybersecurity tips will help you to avoid some of the pesky cyber attacks and strengthen your startup’s security posture. Even after you follow all the cybersecurity tips for startups, there’s no guarantee that hackers won’t find new techniques to hack your website.
Even the world’s top organizations and enterprises have been the targets of cyber attacks in the past. That’s why you should always take cybersecurity insurance to reduce the damages and recovery costs when something goes wrong. Also, check out this document that help startups to lay out a systematic cybersecurity plan.














 (15 votes, average: 4.73 out of 5)
(15 votes, average: 4.73 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security