How to Prevent Hacking: 15 Proven Tricks to Avoid Hacking
According to Verizon, 45% of data breaches are the result of hacking. Let’s find out how to prevent being hacked as an internet user.
If you are wondering “how to prevent being hacked,” you’ve found the right article! You can, of course, use some security software or tweak the security settings to prevent hacking. But most importantly, you need to recognize the psychological games attackers play to make you take actions that you shouldn’t. This includes everything from sharing your personal or financial information to downloading and installing malware-infected files/software.
In this article, we’ll cover 15 tips to help you understand how to prevent being hacked. We’ll also link to “freemium” tools that you can use to prevent hacking.
15 Tips to Prevent Hacking
You don’t require a lot of technical expertise to prevent hacking. These are some super easy and yet, efficient ways by which you can avoid hacking.
1. Encrypt Files While Storing and Transferring
When you’re sharing any important Microsoft files with anyone or storing them on your device, USB, or cloud platform, always encrypt them. Encryption means using mathematical algorithms to “lock” the data with a cryptographic key. Encryption scrambles plaintext data and makes it incomprehensible to protect it from unintended parties without an authentication key.
So that, even if someone gets access to those files, they can’t open and read them. All Microsoft files (such as Word, Excel, Access, PowerPoint) have this option.
For example, to encrypt a file in Excel:
- Click on File from the upper left corner.
- Select Info.
- Click on Protect Workbook (or Protect Document, Presentation, etc., as per the file type).
- Select Encrypt with Password.
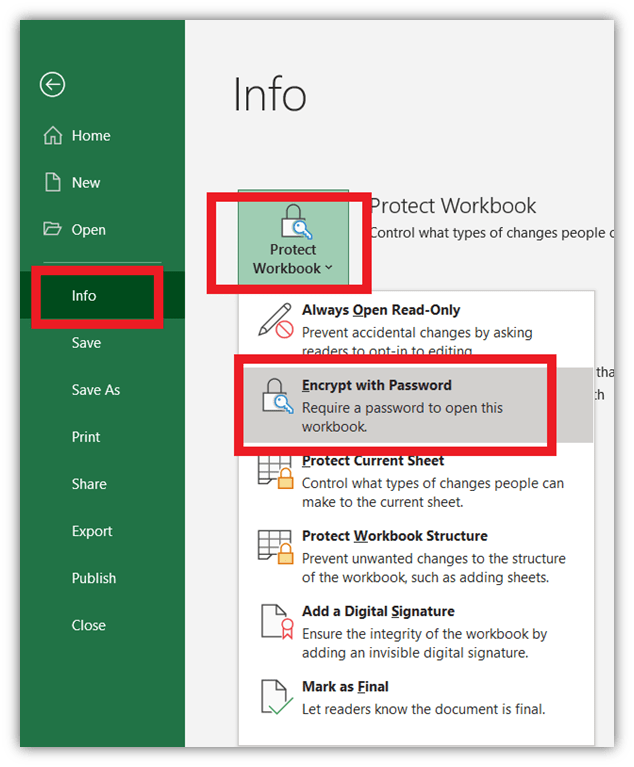
Once you set the password, anyone who wants to access this file would require this password. When you send such a protected file to anyone, be sure to provide the recipient the password via phone, a separate email, or any other communication channel.
Use These Tools to Encrypt Any Other Types of Files/Folders
There are some commercial and “freemium” tools that can help you to enable encryption for any type of files, folders, drives, and documents. Some examples include:
2. Use Browser Extensions to Block Malicious Sites and Harmful Downloads
There are some free browser extensions that maintain a list of malicious and phishing sites and block them. To use them, you’d need to install these extensions (“add-ons” for Firefox) on your browser to keep the attackers at bay and prevent hacking.
These are some well-known free extensions and add-ons:
- Online Security Pro by Comodo
- Anti-Malware Subzero
- AdBlocker
- Malwarebytes Browser Guard
- Avira Browser Safety
- Bitdefender TrafficLight
We have already provided the links here. You just need to click on Add to Chrome or Add to Firefox.
3. Install a Strong Anti-Malware Program
Although this one is pretty obvious, some people still need a gentle reminder to use antivirus and anti-malware programs. These types of security software regularly scan your device and remove dangerous malware. They also alert you when you visit a spammy or malicious website or if you download a corrupted file from the internet.
While choosing an antivirus program, be sure to get it from a reputable company only.
Beware of scareware: If you get a random email or see a popup indicating that your PC is infected, it might be scareware. Scareware is rough antivirus software that can be a virus itself or works as spyware to monitor your actions.
Never click on these links or ads, nor should you install unknown security software. We recommend Comodo Antivirus. It’s a highly reputable brand and offers free and paid versions.
4. Sanitize Your PC Manually
There are some advanced types of malware that a firewall/security software can’t detect. That’s why it is advisable to keep an eye on your device manually to prevent hacking.
Regularly check your C: drive, especially folders like C:/Program File, C:/Program Files (x86), and all the TEMP folders. Also, keep an eye on the Download folder. If you find any unusual items that you haven’t downloaded, perform an internet search to learn about them. Delete the files if they don’t serve any purpose or are linked to malicious activity.
Some malware programs are so stubborn that you won’t be able to delete them with regular deleting steps. The good news is, there are some free file shredder and uninstaller programs that can help you to uninstall such programs. Some of these programs are so efficient that they deep scan your device and delete all the hidden traces like cache and shortcuts.
5. Enable Encryption Using BitLocker for Windows 10
This feature will encrypt your hard drive. If your Windows computer is stolen or you sell it without wiping the memory (note: always wipe the memory first before selling a device!), no one can hack you by stealing data from the hard drive. It also has an encryption facility for the USB drive.
To enable encryption:
- Search BitLocker in the Windows search bar and select Manage BitLocker
- Click on Turn on BitLocker for your C: drive, D: drive, and USB.
- You will need the administrator’s credentials (if not logged in as admin already)
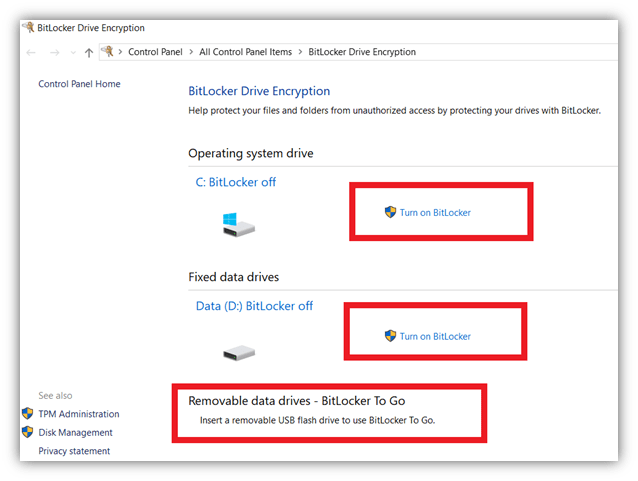
For Mac Users: FileVault provides a similar function as BitLocker. Please follow this resource: Step-by-step guide to enable FileVault.
6. Enable Two-Factor Authentication (2FA)
2FA adds another layer of security along with your traditional passwords. You’ll get a unique one-time password (OTP), secret code, or a magic link on your registered mobile number or email address every time you log in to your account or make a transaction. If any of your bank, credit card companies or any other service providers allow you to enable 2FA, do so immediately!
You can also enable 2FA on the cellphone by installing free third-party apps like:
After installation, you’ll get the option to enable 2FA for all other apps stored on your mobile that support 2FA. Make sure you enable it for eCommerce sites, cloud storage platforms, and financial platforms.
7. Don’t Log in Via Existing Third-Party Platforms
Next on our list for how to prevent hacking: don’t link accounts. When you want to sign into a new platform, you may see an option to sign in using your existing accounts like Facebook, Gmail, LinkedIn, etc. Don’t use these options. Instead, use your email address or phone number or manually complete the login form (don’t be lazy here).
Why? When you sign in/log in using any of these existing accounts, the new app/website can access some information about you stored on such platforms. Such data sharing can be dangerous if the new app/platform owner or employee has malicious intentions. They can steal such data to hack you or sell it in the dark market to other hackers. Even well-known platforms misuse users’ data for creating targeted advertising.
For example, Zoom faced allegations that it shares (or sells) users’ data to Facebook. Zoom admitted that such data leaks happened because it gave users the option of logging in to Zoom via a Facebook software development kit (SDK).
8. Don’t Share Any Information via HTTP Sites
When you open a website, look at the address bar. If you see “Not secure” or an exclamation sign in a round or triangle, it indicates that the site is running on HTTP, which is an insecure protocol. This means that any sensitive data that transmits between your browser and the website’s server remains unencrypted, which makes it easy for hackers to steal your personal and financial information.
So, a good rule of thumb is to only share information with websites that have a padlock symbol in front of their domain names in the address bar. This indicates that the website owner has installed an SSL/TLS certificate, and all the data communicated between your browser and the website’s server remains encrypted.
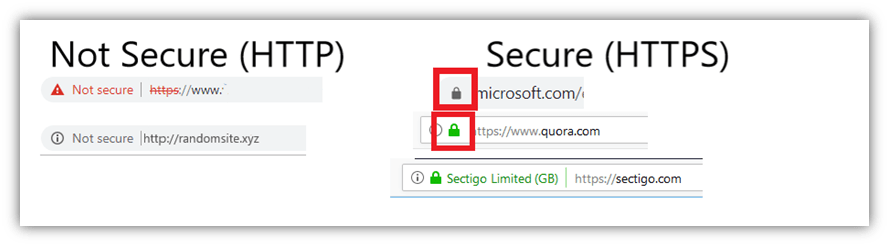
However, just because a site has a padlock sign doesn’t mean it’s safe. A cybercriminal can use a free SSL/TLS certificate on their fake website, too. And then you’re using a secure connection, but you’re still left with the uncertainty of knowing to whom you are connected on the other end.
The solution is to click on the padlock sign and check out the “issued to” field. If the website has installed an extended validated (EV) SSL certificate, you will be able to see its legal name in front of the “issued to” information. You’ll see the company’s name in green color or with a green address bar in some browsers. Most reputable and legitimate companies use EV SSL certificates, which require a rigorous identity verification process.
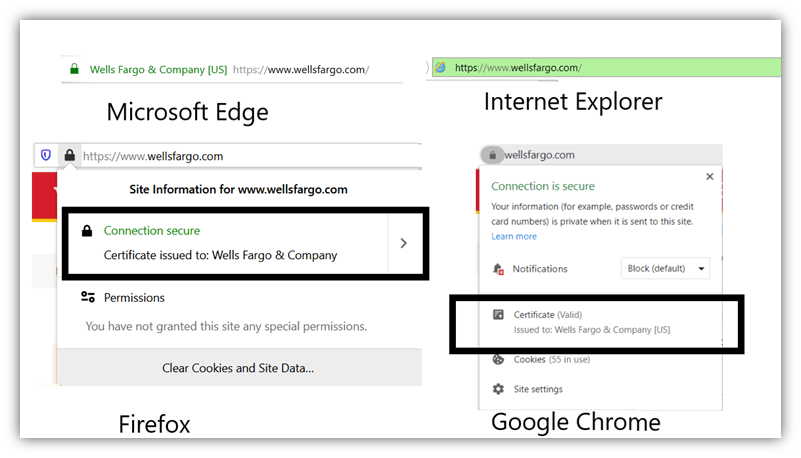
9. Recognize Signs of Fake or Malware-Infected Websites
Okay, so, you’ve have landed on a website and are not sure whether to trust it. You should look for a few specific things when evaluating any website to prevent hacking as a site visitor.
Here are several signs that a website is fake, risky, spammy, malicious, or “phishy”:
- Too many redirects to unknown, irrelevant, or advertising sites.
- Something downloads onto your device automatically (and without your permission).
- Many different “downloads” or “play” buttons for the content.
- You notice multiple screens or popup windows in the background even if you haven’t opened them.
- The site is claiming unrealistic results of any product or offering “too good to be true” deals and discounts.
- There are many spelling and grammatical mistakes on the site.
- The website is trying to create a sense of urgency and urges you to take any immediate steps.
- The site announces that you have won the big prize in the casino, lucky draw, or games in which you haven’t participated. (Sometimes, you will be asked to take part in some easy game, spin the lucky draw wheel, answer easy questions, etc. But keep in mind that no one there to give you a penny for free, let alone big prizes.)
Beware of Cybersquatting Sites
Some people buy domain names that look similar to popular domain names and have just slight variations in the spelling or top-level domains. This is known as cybersquatting or typosquatting, depending on the specific instance.
For example:
- Amzon.com (instead of amazon.com),
- Goggle.com (instead of google.com),
- Dictionery.com (instead of dictionary.com),
- Facebok.com (instead of facebook.com),
- Linkdin.com (instead of linkedin.com), and
- Insiderbusiness.com (instead of businessinsider.com)
So, be careful while typing a domain name in the address bar. When you share your personal or financial information, check the address bar again to make sure you are on the right site.
10. Learn to Recognize Fake vs. Legitimate Software and Applications
When you install software on your device, you permit it to make changes to your device and access data. It is a dangerous step because if the developer has bad intentions or the software contains malware, you’re doomed!
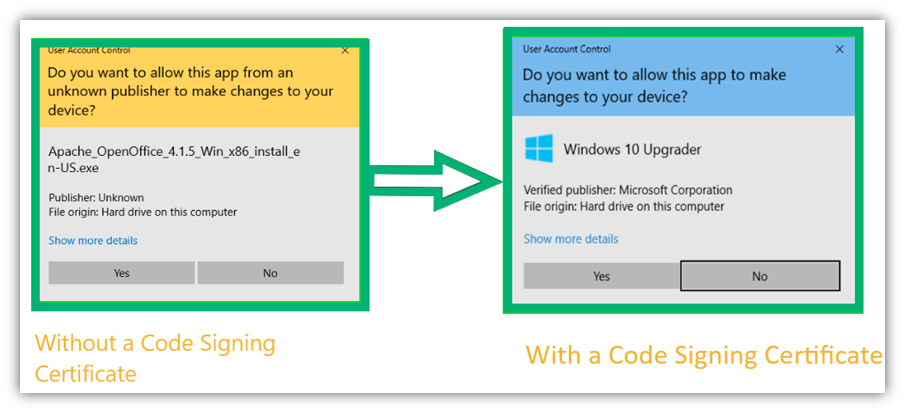
When you’re downloading software, check out the publisher’s name in the security window.
If you see the publisher’s name as Unknown, beware! This indicates that the software’s integrity is not vouched for and protected by a code signing certificate. It also tells you that the developer’s identity hasn’t been verified by a third-party certificate authority (CA). Legitimate developers and publishers use code signing certificates. If you haven’t heard the publisher’s name before, conduct a quick internet search and read the reviews.
11. Recognize Phishing Emails
FireEye reports that one in every 101 emails is malicious! Attackers spread malware via email attachments or redirect you to some infected sites. Some cybercriminals try to manipulate you into sharing personal information psychologically.
Luckily, there are a few things you can look out for that will help you to avoid falling victim to phishing schemes:
1. Carefully check the sender’s email address. If it is unusual or too long, be cautious! Also, if someone is claiming to be an employee of a well-known organization, their email address will have the company’s domain name after “@.” For example, “@apple.com, @amazon.com, @wellsfargo.com, etc. Their messages won’t come from a generic email client like Gmail, Hotmail, Yahoo, AOL, etc.
2. Don’t ignore spelling, punctuation, and grammatical errors. Good companies have strict editorial standards. It’s uncommon for them to send an official email with many errors. So, if you see such errors, be on alert because it’s likely a scam.
3. Is the email trying to provoke any strong emotional response from you? For example, an attacker might want to generate panic in you by sending any fake transaction notice in the hope that you will open the attachment to investigate it. Or they might offer you a great discount on a product/service, hoping that you would click on the link provided in the email in excitement to avail of the deal.
Check out this article: Five real-life examples of phishing email scams
Recognizing a phishing email is the very first and essential step to prevent hacking. If you receive such an email, just delete it. Don’t download anything from it or click any links — and never share your personal information in a reply message! If you think the message is legit, go to the original company’s site to verify the given deal, offer, transection history, donation drive, news, claims, etc.
If the sender is claiming to be someone you know, contact them personally to verify the message before taking any actions suggested in the email.
12. Be Vigilant While Downloading Anything from the Internet
It’s a common practice to spread viruses and other types of malware via:
- Email attachments
- Advertisements (known as malvertisements)
- Fake software, programs, and apps
- Media files like songs, images, videos, and slideshows
- Social media attachments
- SMS/WhatsApp messages
As we mentioned before, if there are too many “downloads” buttons placed in a deceiving manner, it is also a red flag.
The malware-laden emails, advertisements, or popups will try to catch your attention by:
- Showing a sense of urgency.
- Generating a surprise element or curiosity.
- Inciting feelings of curiosity, fear, or panic.
Examples of these types of messages include:
- “Your account has been suspended due to rules violation. Attached is a document for more information about the violation.”
- “Your PC is infected with viruses. Click here to get free scanning.”
- “Your order has been shipped from xyz.com (any well-known ecommerce site). Attached is your transaction receipt.” (When you haven’t placed the order, you may feel curious and tempted to download the attachment to see the transaction details — don’t do this)
- “$5,000 has debited from your bank account today. If you haven’t done this transaction, click on this link or download the transaction receipt.” (If you haven’t made that transaction, before downloading the attachment, make sure email is legit by following tips stated in this article: How to spot fake emails)
If you spot a fake email or website, don’t download anything from it. But even if you trust the email sender or the website, always scan the downloads with a robust antivirus program before downloading. After all, it’s possible that the legitimate organization’s or person’s email account or the site may be compromised.
13. Beware of Phishing SMS Messages
Hackers send SMS phishing (smishing) messages to defraud people. These fake SMS text messages might offer you a free product or a great discount on your favorite brands. They might generate panic by sending messages of a fake financial transaction. Attackers also pretend to be your friends/relatives and ask you to send them money immediately.
Such fake SMS messages generally contain links that redirect users to infected sites or phishing sites. Some links enable automatically download malware onto your mobile device as soon as you click on them. Otherwise, the attacker may try to manipulate you into sharing your personal or financial information in a reply message. In short, they will use the same tactics in SMS text messages as they do in phishing emails.
Some tools make it possible for attackers to send you messages pretending to be someone else. Whenever you receive such a message, don’t click on the link given in the SMS. Rather, go to the original website to confirm the deal’s legitimacy, discount, offer, transaction, etc. Also, call directly to the friend/relative to confirm whether they sent the message. If you suspect a phishing or fake SMS, block the sender ASAP.
14. Don’t Jailbreak Your Devices
People generally jailbreak their phones or other devices to access banned apps, change service providers, or change the phone’s layout and settings.
But jailbreaking (rooting for android) is not a great idea if you want to avoid hacking! When you jailbreak your phone, you unknowingly disable some of the phone manufacturers’ default security features. Plus, when you use jailbreaking tools or software, you’re giving administrator-level powers to app developers whose intentions are unknown. They can not only access all your data but can also make unauthorized changes in the device’s settings.
In short, when you jailbreak your phone, you severely weaken your device’s security posture. Hence, to keep hackers away, refrain from jailbreaking your device.
15. Additional Tips on How to Prevent Being Hacked
Alright, we’re on to the last tip for how to prevent hacking. These are some simple yet important tips to prevent hacking.
- Keep your device, software, operating system, and apps updated with the latest versions.
- Never share your login credentials, one-time passwords (OTP), or other account-related information with anyone.
- Don’t use public Wi-Fi. If you must, use a VPN to prevent anyone from identifying or intercepting your device’s identity and data transmissions.
- Use haveibeenpwned.com to find out whether your password is compromised in any data breach incidents.
- Store your backup on the third-party cloud platform to keep it more secure.
- Regularly run antivirus software checks. If you suddenly started to see ad popups or security warning popups, your device might be infected with adware or a potentially unwanted program (PUP). Scan your device with a robust anti-malware program immediately.
Final Words on How to Prevent Hacking
We all love using the internet but are not aware of its dangers. We have written this article for individuals to help them recognize online threats and avoid hacking. If you’re a business organization that wants to protect your website and customers from getting hacked, have a look at these helpful articles:
- How to Secure a Website in 6 Easy Steps
- Cybersecurity for Startups: 10 Cybersecurity Tips to Implement Now
- What to Do If Your Website Is Hacked














 (39 votes, average: 4.44 out of 5)
(39 votes, average: 4.44 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security