8 Passwordless Login Security Mistakes and How to Avoid Them
Identity Defined Security Alliance (IDSA) reports that nearly 85% of identity stakeholders were directly impacted by identity-related security incidents in 2023. Protect your data and systems by learning eight passwordless login security mistakes and how to avoid them
$5,479,819. This is the average cost organizations spent on data breaches caused by insecure authentication in 2023. It’s enough to easily bankrupt many businesses. To make matters worse, the same Hypr report confirms that authentication-related attacks affected 69% of the firms polled.
Adopting passwordless login solutions can help organizations mitigate the risks associated with traditional password-based access. But, if incorrectly implemented, these solutions can do more harm than good.
As the character Rocky Balboa said in one of his namesake movies: “The world ain’t all sunshine and rainbows.” So, let’s explore the most common passwordless security login mistakes to avoid and a few tips that’ll protect you from most of the digital world’s nasty storms.
7 Passwordless Login Security Mistakes and How to Avoid Them
Passwordless login solutions are a wonderful way to verify your users’ identities without requiring them to type their passwords. This method replaces passwords with more secure alternatives such as:
- Client certificates (i.e., personal authentication certificates),
- Biometrics (e.g., fingerprint, retina scans),
- One-time passwords (OTPs), or
- PINs.
Here’s a quick overview of several of the most common passwordless security mistakes people make and what you can learn from them:
| Passwordless Login Mistakes | Passwordless Login Issue Examples | Solutions |
| 1. Skipping Users and Customers’ Identity Proofing | Not verifying a user’s identity before granting him access to a new app or resetting a password. | Follow NIST digital identity guidelines, use different verification methods, and manage identities correctly. |
| 2. Insecurely Handling Your Certificate’s Private Keys | Storing keys as plain text files, using the same key for multiple servers, sharing keys, and no key rotation. | Use unique keys, rotate them frequently, and store them securely with secure hardware. |
| 3. Opting for Less Secure Authentication Factors | Carelessly using magic links, OTP, SMS, push notifications, and biometrics. | Implement a PKI certificate-based passwordless login solution. |
| 4. Underestimating Cybercriminals and Technology Advancements | Disregarding the dangers of social engineering and generative AI-based attacks. | Opt for reliable biometric devices/software, certificate-based passwordless logins, backup authentication solutions, and have a backup of your key-related data. |
| 5. Not Having a Plan B in Place for “Murphy’s Law” | Lacking protections in case devices are stolen or lost. | Use encryption and remote wipe software, and have a secondary passwordless login solution. |
| 6. Assuming That There Won’t Be Any Technical Issues Once Implemented | Ignoring biometric devices, network connections and software update-related issues. | Frequently test passwordless logins, and have an authentication backup and a remediation plan in place. |
| 7. Neglecting Security Misconfigurations | Overlooking Software misconfigurations and default credentials. | Personalize usernames, passwords, error messages, and settings, and disable unused features. |
| 8. Ignoring Updates and Vulnerabilities | Sticking to legacy or unpatched systems and skipping vulnerability checks. | Keep all systems up to date and patched, and use automated security check tools like SiteLock and HackerGuardian. |
1. Skipping Your User’s Identity Proofing
Of course, you know who your employees are. You’ve personally hired Bob, and you see him nearly every day in the office. So, why should you waste time verifying his identity again before giving him access to a new app?
Because if Bob works from home one day and asks to get access to a new application containing sensitive information, how can you be sure that’s really Bob requesting it and not an attacker? Hint: you can’t unless you verify his identity.
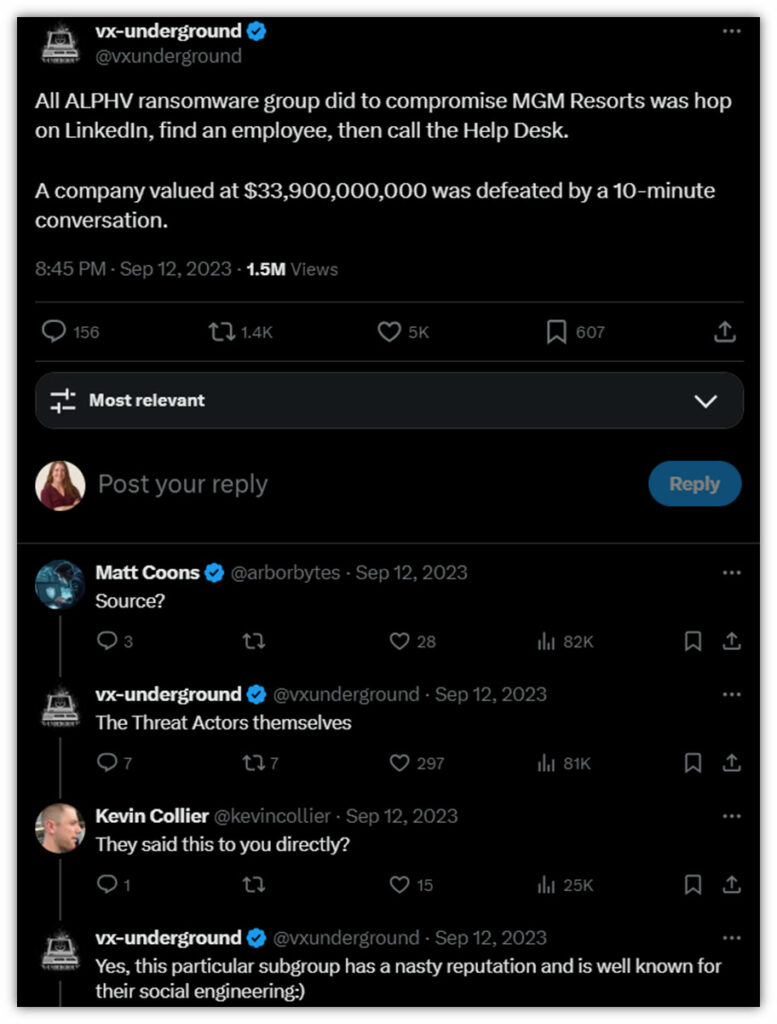
Are we being paranoid? Maybe. But this very concern may have contributed to MGM’s troubles and woes in September 2023. According to VX-Underground, an attacker impersonated an MGM employee to convince the support team to give him the credentials to access the corporate system. MGM reported in its SEC 8K filing that this attack led to:
- A massive data breach.
- $100 million in earnings losses.
- $10 million in one-time remediation-related expenses and legal fees.
3 Solutions to Overcome This Passwordless Login Security Mistake
Become a doubting Thomas and prevent social engineering attacks on new accesses and password resets by:
- Following identity proofing guidelines. Choose among the three security levels described in the National Institute of Standards and Technology (NIST) Digital Identity Guidelines.
- Verifying your user’s identity via a combination of different elements. For instance, combine face-to-face video conferences, location detection, or document verification with behavioral analytics.
- Correctly managing digital identities. Ensure the digital identities of your customers and other users are properly managed, respecting data privacy and security regulations.
2. Insecurely Handling Your Certificate’s Private Keys
Cryptographic private keys and the digital certificate saved on the user’s device are at the basis of public key infrastructure (PKI) certificate-based authentication.
Here, we won’t go into the technical nitty-gritty of how PKI and certificate-based passwordless logins work, but you can get an overview from the graphic below:
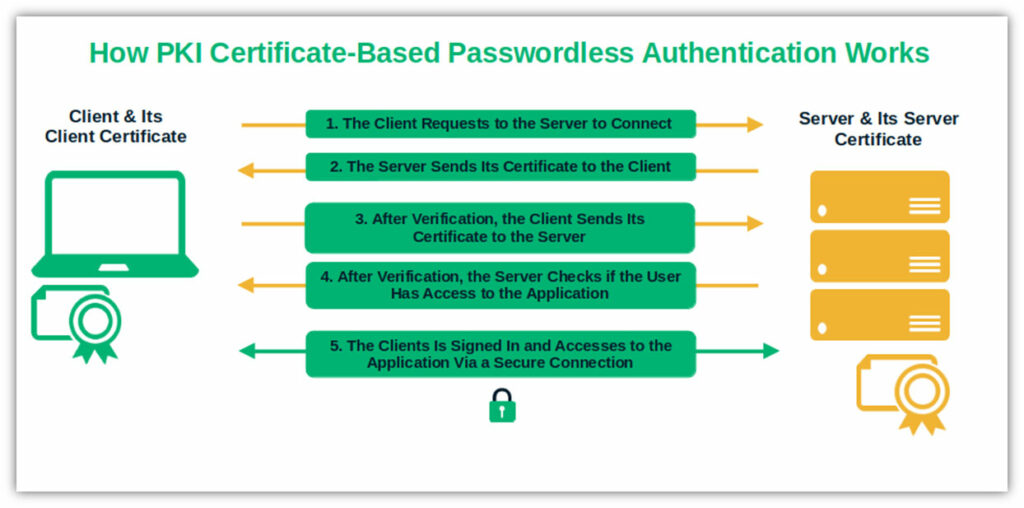
However, the complex validation process and the fact that the private key is never sent to the server makes it one of the most secure passwordless login methods (more on this in a moment). As long as the private key remains private. But what if it doesn’t?
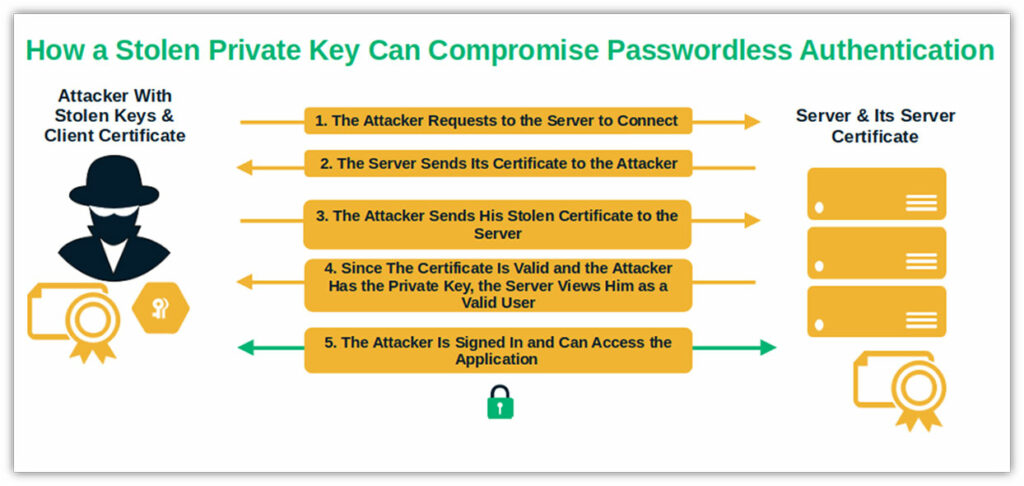
Examples of These Passwordless Security Issues
A stolen private key and mistakes like the ones listed below could spell the end of your passwordless login security.
- Storing keys in plaintext files or on unprotected servers. Private keys are like passwords. They shouldn’t be saved in plaintext or on unprotected servers as anyone can access text files.
- Using the same key for more than one server or service. It can be convenient, but a private key should never act as a passepartout. Imagine if it’s stolen. Jackpot. The bad guy can roam free all over your network and systems undetected.
- Sharing your keys or giving access to them to anyone. SSH passwordless login lets server administrators (and anyone with the same keys, including cybercriminals) access Linux servers without a password. In this case, “sharing is not caring.”
- Avoiding key rotation. 45% of businesses surveyed by Microsoft haven’t rotated their AWS access keys in more than six months. An inexistent or long key rotation period facilitates the attacker’s work and increases the risk of data breaches. Unfortunately, this useful approach is often overlooked and isn’t done as often as it should be.
4 Solutions to These Passwordless Login Security Issues
Prevention is always better than cure. Secure your passwordless logins by doing the following:
- Store all your private keys on hardware security modules (HSMs). This ensures the keys are securely stored while allowing authorized users to access them to perform tasks.
- Use one key for one server/service. This way, if one private key is compromised, the attacker will only get access to that one server or service.
- Minimize the chances of breaches and unauthorized access. You can do this by implementing access controls and limitations regarding your cryptographic keys and other secrets (i.e., the principle of least privilege).
- Frequently rotating private keys. This approach is recommended by the National Institute of Standards and Technology (NIST).
3. Opting for Less Secure Authentication Factors
Client certificates aren’t the only authentication factor for passwordless logins. There is a broad range of other methods that can be used. But not all of them are as secure as they seem. For instance:
Magic Links
You get an email with a unique link that includes a token. When you click on it, the server verifies and saves the token as a cookie on your browser. Abracadabra! You’re now signed in using a magic link.
But what if the email is intercepted through a man-in-the-middle attack? Or if a cybercriminal sends you a phishing email with a phony magic link redirecting you to a malicious website? Malware infection and data breaches are just around the corner.
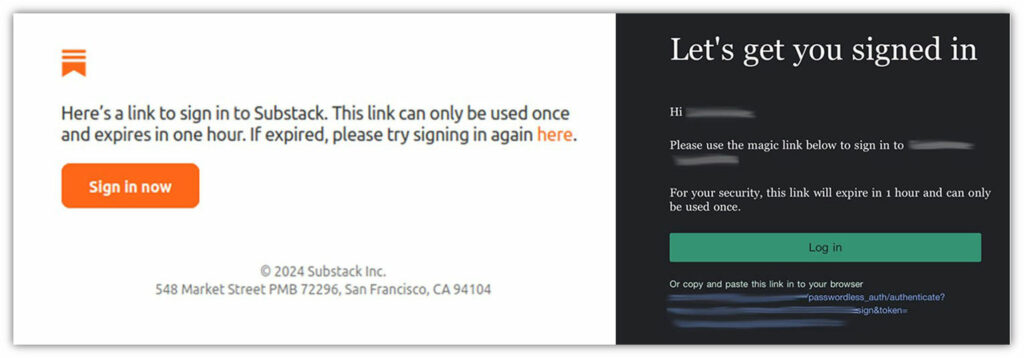
Image caption: Two examples of magic links a colleague and I received via email.
OTP, TOTP, SMS, and PINs
In July 2024, Zimperium warned that over 600 global brands were infected by SMS Stealer, a malicious software that steals one-time passwords (OTPs) sent via text messages. SMSes aren’t encrypted and can be intercepted or spoofed in no time. The video below says it all. Some developers got hold of a time-based OTP (TOTP) and used it to steal a Tesla car (please, don’t do this at home).
Push Notifications
These are those login notifications you get on your authentication app or hardware token asking you to approve or deny access to an app/system with a click. It’s simple, user-friendly, and resistant to phishing (albeit the message can still be intercepted). Your device could be lost or stolen. Furthermore, believe it or not, governments can use push notifications to spy on you.
Biometrics
OK, hopefully, no bad guy would go as far as cutting off your finger or scooping out your eyeball to access your apps. (This isn’t the movies, after all.) Yet, biometrics aren’t exempted from attacks. In the second half of 2023, IProov detected 704% more face swap injection attacks than those recorded in the first half. We’ll dig deeper into this in the next point. For now, let’s see how we can fix this.
Ward Off These Passwordless Login Security Issues With Certificate-Based Authentication
A PKI certificate-based passwordless login solution is your best bet against cutting-edge attacks. The authentication happens automatically without the user’s input. Secrets are replaced by a more secure digital certificate confirming your identity as an individual, issued by a trusted certificate authority (CA) and the user’s private key.
This way, attackers have nothing to phish, spoof, or fake to gain access to your company’s secrets and systems. To set up certificate-based authentication:
- Purchase a personal authentication client certificate from a trusted source. SectigoStore.com provides 24/7 free support, strong 256-bit encryption, and 2048-bit RSA signature key at a bargain price.
- Set up a scalable Sectigo private PKI platform. This will enable you to issue and manage virtually any type of private certificate for any device. The certificates issued are secure as your company acts as a private CA.
- Automate management of your certificates and keys. Sectigo Certificate Manager is an intuitive platform that can help you do that with ease.
4. Underestimating Cybercriminals and Technology Advancements
95% of IT leaders interviewed by Keeper Security reported that cyber attacks are becoming more sophisticated. 51% confirmed their organization suffered an artificial intelligence (AI) attack in 2023.
Nowadays, generative AI can be used by anyone for virtually any purpose. From translations to generating credible videos and pictures, it’s a cheap and fast solution that requires no technical skills. AI also makes generating malicious code, phishing, and social engineering attacks practically child’s play.
Turning a blind eye to these threats will make your passwordless login vulnerable to:
- Sophisticated phishing attacks. A tell-tale sign of phishing messages were grammatical mistakes, poor spelling, and typos. Then ChatGPT came to light. Et voila. Cybercriminals can now use it to generate grammatically correct, believable phishing emails in seconds.
- Voice simulation. Microsoft demonstrated that its new VALL-E text-to-speech AI model can simulate anyone’s voice with only three seconds of audio. Do you think that this is bad? Real-time voice changer software is even worse. These tools let anyone change their voice to sound like someone else in real time and use it for SIM swap attack.
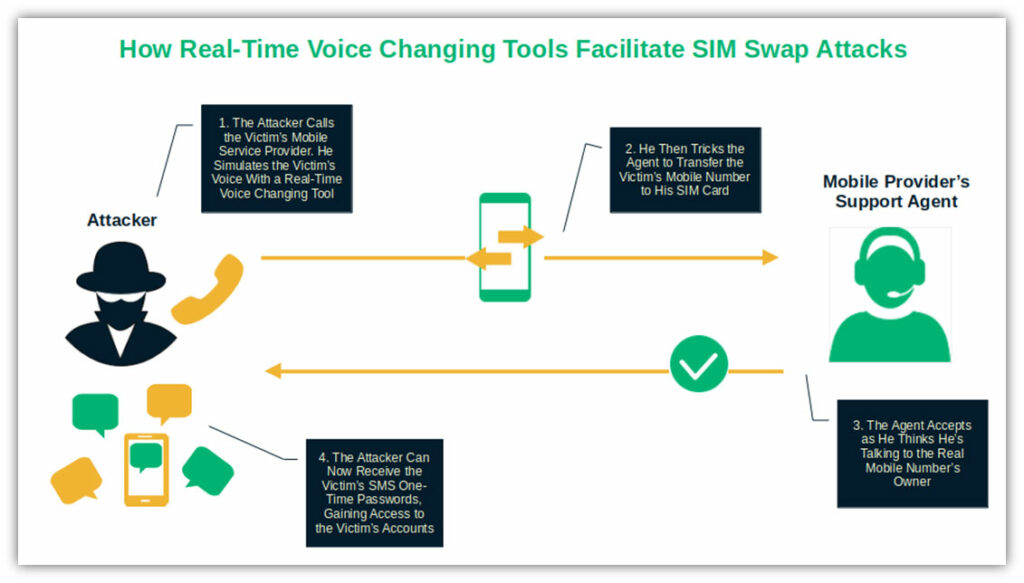
- AI Image and video. Do you like playing with image morphing and AI video-making tools? I’ll tell you a not-so-secret secret: the bad guys like it, too. They often use it to inject manipulated videos into authentication systems (face swap injections). Access granted!
- Vulnerabilities exploitation. A recent study shows that ChatGPT-4 can successfully autonomously exploit 87% of one-day vulnerabilities without too much effort. Yup. ChatGPT never stops surprising us.
3 Ways to Bypass This Passwordless Login Security Issue
Agatha Christie once said, “To every problem, there is a most simple solution.” And she was right.
- Opt for high-quality and reliable biometric devices and software. It’ll enable you to spot and stop even the most advanced attacks.
- Ensure you have one or more backup authentication solutions. This way, if one is compromised or has a vulnerability, your users can switch to another one.
- Leverage the power of digital trust with certificate-based passwordless logins. 91% of IT professionals polled by KeyFactor in 2023 say that strong PKI management is key to protecting organizations from AI threats.
Last but not least, always back up your data.
5. Not Having a Plan B in Place for “Murphy’s Law”
As the saying goes: “Anything that can go wrong will go wrong.” So, what will you do when a device is stolen or hijacked (in case of SIM swapping) or when things simply go wrong?
Once the device is lost or stolen, the attacker who finds it (or steals it) can use it to bypass the passwordless login and get a free ticket to your organization’s network, email, and all your employee’s accounts.
Let’s have a look at some recent statistics.
- In 2023, nearly 52,000 mobile devices were stolen in London alone.
- The United Kingdom’s Ministry of Defense (MOD) confirmed that nearly 400 devices were lost or stolen between November 2022 and November 2023.
6. Assuming There Won’t Be Any Technical Issues Once Implemented
Technical issues or errors could impact the security, performance, or availability of any passwordless logins. This could negatively affect your operations and bottom line, underscoring the importance of taking steps now to prevent these issues. For example:
- Biometric devices could malfunction,
- Network connections could fail, or
- A buggy software update could mess your systems up.
Just look at what happened with the latest Microsoft/CrowdStrike update in July 2024. It crippled over 8.5 million devices worldwide and caused major disruptions. Class actions have been filed by investors and travelers. OK, maybe a sloppy update won’t cause the same level of damage to your passwordless login security solution, but you got the picture.
Dodge This Passwordless Login Security Error by Implementing These 3 Solutions
Mitigate future risks and guarantee 100% login availability to your users by:
- Frequently testing all passwordless login methods and systems used. Monitoring systems will let you immediately spot and fix anomalies and potential issues.
- Running a risk assessment and using the outcome to generate an action plan. The NIST Cybersecurity Framework (NIST CSF 2.0) is an excellent resource full of tips and best practices that can be applied even to small and medium businesses.
- Having backup passwordless login methods in place. This is The Lord of the Rings’s Ruling Ring of passwordless login security: one solution to help you minimize all issues (or, at least, most of them).
7. Neglecting Security Misconfigurations
Passwordless login solutions are like the latest Tesla car: technologically advanced, powerful, and sporting a ton of awesome features. Yes, you can have the best authentication method and technology, but if it is incorrectly configured, it’ll be useless and put you and your whole organization in danger.
In fact, the 2021 OWASP top 10 ranks misconfigurations as the fifth most critical web application security risk. The following can lead to malware infection risks:
- Application and software misconfigurations,
- Using default configuration settings, and
- Sticking to manufacturer authentication credentials.
3 Ways to Prevent These Login Security Errors
Did you know that some manufacturers publish how-to guides explaining how to find their products’ default usernames and passwords? So:
- Change all applications and systems’ default usernames and passwords. Never, ever run with the defaults — doing so is setting yourself up for a headache.
- Personalize your passwordless login settings. Error messages should be concise to avoid information leaking useful information or informing attacks of flaws that can be exploited.
- Disable all unused/unnecessary features, components, and frameworks. It’ll restrict the attack surface.
8. Ignoring Updates and Vulnerabilities
In Q1 2024, 8,697 new common vulnerability exposures (CVEs) were discovered. Over 1,600 more than in Q1 2023. We get it. Testing and installing patches can be boring and time-consuming tasks that aren’t generating profit for your company. But it’s a necessary function that ensures the security and reliability of your software products and services.
Unpatched software and unaddressed vulnerabilities can have disastrous consequences, including:
- Data breaches,
- Reputation damage, and
- Compliance fines and penalties.
And it doesn’t matter if those flaws are old and well known. A 2023 study revealed that 76% of vulnerabilities used today as entry points by attackers were discovered between 2010 and 2019.
3 Tactics to Prevent This Passwordless Login Security Issue From Happening Again
To prevent this passwordless security mistake:
- Promptly install all software updates. Patches and updates are only as good as the speed at which you apply them. As we saw with the WannaCry situation years ago, leaving your systems’ vulnerabilities unpatched puts your devices and data at risk of compromise.
- Regularly test your systems. Proactively identify and fix vulnerabilities through continuous testing and a robust patch management strategy.
- Proactively look for security issues. Check your systems for flaws using automated security check tools like SiteLock and HackerGuardian.
Final Thoughts About 8 Passwordless Login Security Mistakes to Avoid
An error-free implementation of passwordless login solutions will enable your organization to mitigate the risks of using a conventional ID and password. They’ll also improve your applications’ user experience and help you save money in the long term by eliminating time-consuming and costly operations such as password resets.
We hope this article will help you avoid the most common passwordless login security mistakes so that you can fully enjoy the benefits of this technology. Implement it on your websites, applications, software, and devices.





















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security