In the digital world, SSL certificates — client or server — exist to guarantee that we are communicating securely with legitimate entities. These certificates use a trusted third party, aka a certificate authority (CA), to validate the identity of the client to the server or the server to the client, respectively. Whether you know it or not, each of us on the digital platform has made use of these certificates because they afford us a certain level of protection from malicious attacks.
A client certificate is a digital certificate used to assure a remote server that the requester is a legitimate user. While both SSL and client certificates are building blocks of mutual trust, there is a fundamental difference between the two. An SSL certificate validates the server’s identity, whereas a client certificate validates the user’s identity.
So, when talking about a server authentication certificate vs a client authentication certificate, can one be used in place of the other? Are there any differences between the two? To answer these questions, let’s dig into the details of the client certificate vs server certificate!
SSL Server Authentication Vs Client Authentication
SSL server authentication is an SSL certificate issued to the server to validate their identity to the client, while client authentication is an SSL certificate to validate the client’s identity to the server. An SSL server authentication includes the encryption of the communication with the client, and therefore, the client certificate doesn’t involve the encryption of conversation.
Client Certificate vs Server Certificate: Some Useful Terms to Know
Before we can get into the whole server authentication certificate vs. client authentication certificate discussion, we need to take a moment to understand what X.509 digital certificates are.
In simplistic terms, an X.509 certificate is a digital file. It uses a globally accepted standard called X.509 public key infrastructure (PKI) to verify the identity of the certificate holder and map a public key to that specific user, computer, or service. X.509 digital certificates can include SSL/TLS certificates, S/MIME email certificates, code signing certificates, etc.
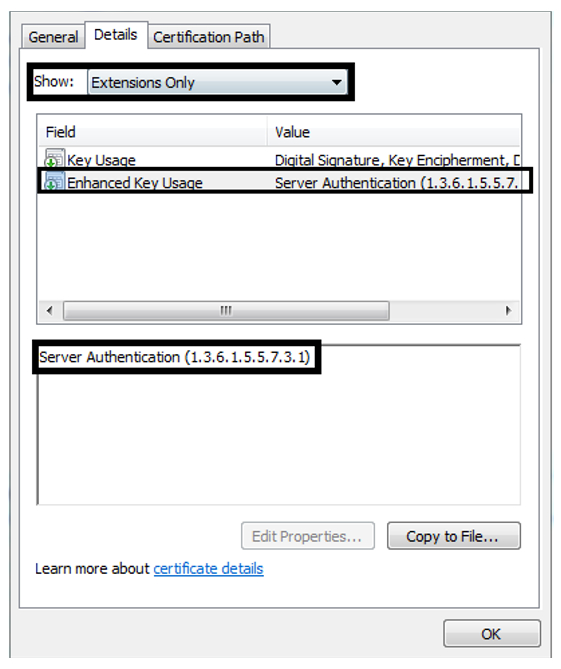
In the X.509 system, extended key usage (EKU) is an attribute that may be included under the optional extensions. It’s used to indicate the purpose of the public key contained in the certificate by listing the roles with the help of object identifiers (OIDs). A certificate authority can use extensions to issue a certificate for a specific purpose.
• anyExtendedKeyUsage (OID 2.5.29.37.0)
• Server Authentication (OID 1.3.6.1.5.5.7.3.1)
• Client Authentication (OID 1.3.6.1.5.5.7.3.2)
• Code Signing (1.3.6.1.5.5.7.3.3)
Secure Unlimited Subdomains with One Wildcard SSL Certificate – Save 50%
Save 50% on Sectigo Wildcard SSL Certificates. It includes unlimited server licenses, reissuances, 256-bit encryption, and more.
Client Certificate vs Server Certificate: The Purpose of Each
What is a Client Certificate?
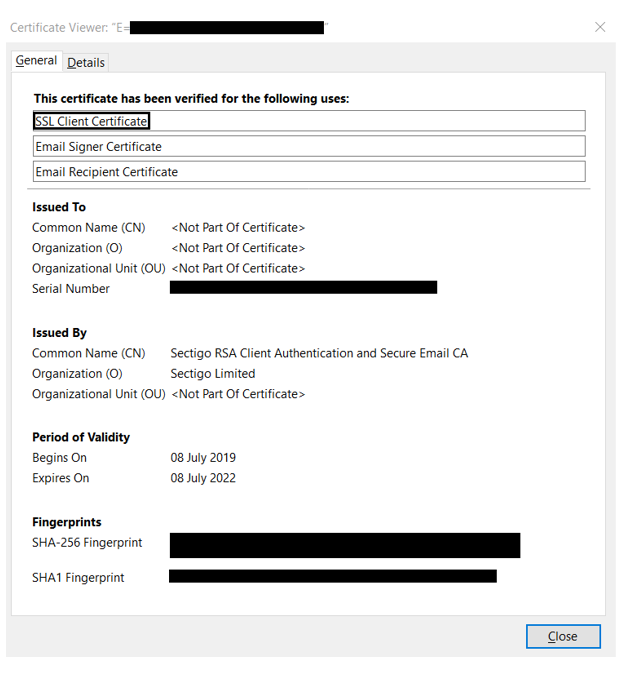
A client certificate is a digital certificate that is used to authenticate the identity of the client/user to the server. A client certificate is to a client what an SSL certificate is to a server. Both client and SSL certificates play a crucial role in creating mutual trust and a secure communication channel between the client and the server.
A client certificate serves as a way for the user to assert their identity to a server. Since passwords are known to be vulnerable to brute force attacks and various other cracking techniques, we rely on the user’s system to authenticate client identity. It does so without requiring any input in the form of a password from the user. Once the client’s (email user, website, etc.) identity is validated, the server knows that it is connecting to the legitimate user and grants access.
Consider a scenario in which you have placed some highly confidential documents on your server that you want to share only with some trusted personnel within your company. You already know that client certificates authenticate users based upon the systems they use. Unless users access the server from a client machine which has permissions, they would be denied access. To add another layer of security, you could combine this with multi-factor authentication to avoid any data breach.

Client Certificates Explained
A client certificate is a digital certificate authenticating the client’s identity to the server while making a request. The client certificate can ensure the server that the request comes from a legitimate user and not from somebody impersonating them. A client certificate becomes crucial when requested sensitive information or access to the information is limited to certain users only.
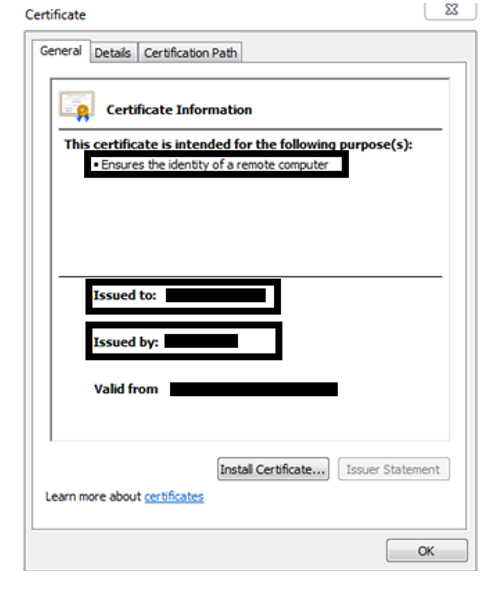
What is a Server Certificates?
Server certificates are what are commonly known as SSL/TLS certificates. An SSL/TLS certificate accomplishes two things:
• First, it verifies and validates the identity of the certificate holder or applicant before authenticating it.
• Second, it establishes an encrypted communication channel and switches the protocol to HTTPS once installed on the server (as a defense against any man in the middle attack).
It also is the most popular type of X.509 certificate. SSL/TLS certificates are issued to hostnames (machine names like ‘ABC-SERVER-02’ or domain names like www.site.com). When we hop on to our computers and type in a website URL, the server certificate ensures that the data flow between our client browser and the domain we’re trying to reach stays secure.
Client Certificate vs Server Certificate: The Difference Between the Two
As you probably know by now, client authentication vs server authentication is different processes. As such, these two types of certificates have very specific purposes, and they cannot be used in place of one another. The table below compares the two certificates, giving a high-level overview of their similarities and differences:
| TL;DR — Comparing a Client vs Server Certificate | |
|---|---|
| Server Certificate | Client Certificates |
| A server certificate is used to authenticate the server’s identity to the client. | A client certificate is used to authenticate the client or user identity to the server. |
| Server certificates perform encryption on data-in-transit to assure data confidentiality. | Client certificate does not encrypt any data, it only serves as a more secure authentication mechanism than passwords. |
| Server certificates are based on PKI. | Client certificates are also based on PKI. |
| OID for server authentication is 1.3.6.1.5.5.7.3.1 | OID for client authentication is 1.3.6.1.5.5.7.3.2 |
| Server certificates have “Issued To” and “Issued By” sections. | Client certificates also have Issued To” and “Issued By” sections. |
| Example: SSL certificates | Example: E-mail client certificates |
